
YouTube 101: Is YouTube Red Worth It?
When Google announced YouTube Red — a paid monthly subscription service that disables advertising, among other perks — many of us thought "just use an ad blocker." But it isn't really that simple.


When Google announced YouTube Red — a paid monthly subscription service that disables advertising, among other perks — many of us thought "just use an ad blocker." But it isn't really that simple.
There's no debating that the Galaxy S8 and S8+ are top contenders for the most beautifully designed handsets of 2017, but the same can't be said for their TouchWiz interface, which has been met with lukewarm reception at best.

Apple's default browser for iOS, Safari, has a ton of useful features, and there's so many that it's impossible to know everything you can do to browse the web more efficiently. One you may not know about brings the Command + F keyboard shortcut right to your mobile browser so you can search for words or phrases directly on any webpage you're viewing.

The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

Many new parents will tell you how hard it is to name a baby. Some have stories of how they knew what the name of their child would be from before conception, only to change their mind when they were born. Sometimes new babies can go weeks without a name since there is an endless selection to choose from.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.
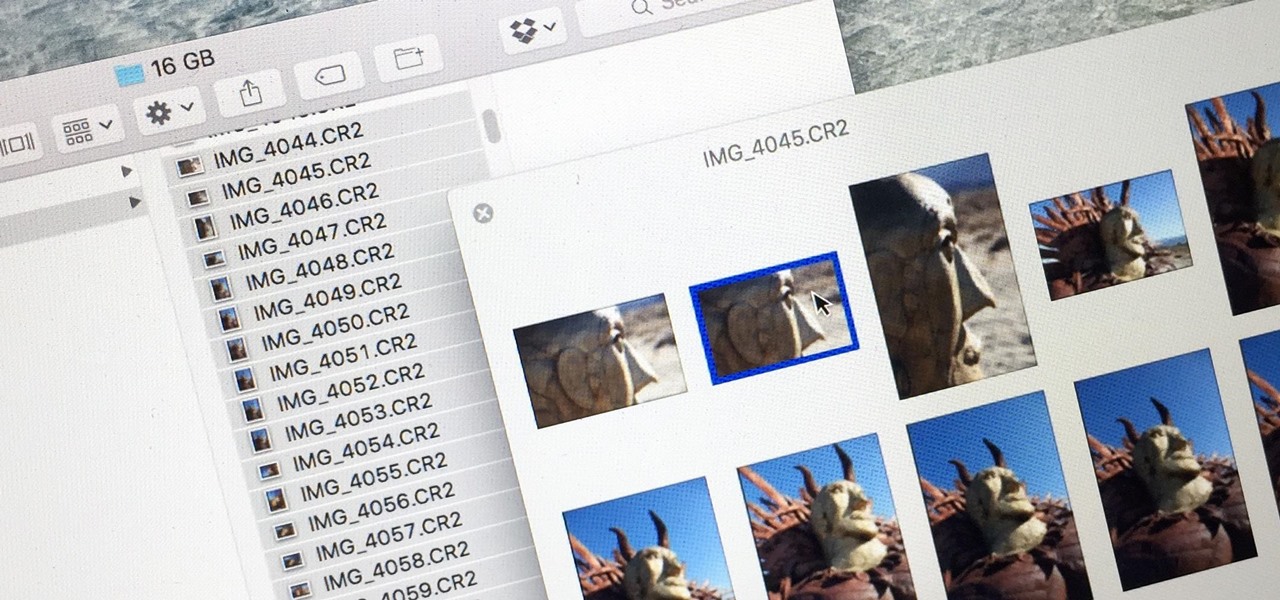
Quick Look, first introduced in 2007, is an instant preview feature on the Mac operating system that lets you view files and folders without opening them up. Just highlight a file, like a picture or text document, then press the spacebar on your keyboard to get a speedy preview of it.
Android Police reported that the upcoming Nexus phones would be getting an exclusive launcher this year, dubbed the "Nexus Launcher." This rumored home screen app was said to feature Google Now integration, a swipe-up app drawer gesture, and a few other finishing touches.

These days, there are Android apps for every budget—forgive me if that sounds like a car commercial, but that's just the way things are in the age of the smartphone and tablet. You've got apps that require monthly subscriptions, paid apps that will run you a $30 one-time installation fee, and even games that start at 99 cents, but quickly skyrocket in price with in-app purchases.
Most of you lot would be aware what WPA/WPA2 is so I won't bang on about the encryption or protocols a great deal. In short WPA and WPA2 both have a maximum of 256bit encrypted with a maximum of 64 characters in the password. The encryption is really only 64bit but x 4 because of the way the authentication functions as a 4 way handshake.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

Coverage for the 88th Academy Awards, aka the Oscars, will air live this Sunday, February 28th at 4 p.m. PT (7 p.m. ET). The ceremony itself, hosted by Chris Rock, is set to begin at 5:30 p.m. PT (8:30 p.m. ET).

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Smartphones have become such a big part of our lives these days that they're now closely associated with our personal identities. No longer is it Ford versus Chevy, rock versus rap, or PC versus Mac—now, you're either an Android person or an iOS person.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

There's been a whole lot going on at this year's Consumer Electronics Show, from the latest in virtual reality gear to televisions that continue to slim down while producing higher quality images.

Hello NullByte! This will be my first How To series.

These days, if you're having friends over, they'll probably ask to log into your Wi-Fi network before asking for a drink. But if you've forgotten your password, it can be quite hard to find, since most devices obscure the characters with asterisks.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

When attempting to gain access to a server, there may come a point when you need to get around file upload restrictions to upload something. If we can find a way to get around the restrictions, then we can upload anything we want to the server, effectively compromising it. That is what we'll be doing here today, so let's get started!

When most people think of "gaming computers," they're probably thinking of Windows-based PCs. They offer a huge variety of devices with better equipped software and hardware for a cheaper price, and there are more available games than there are for OS X-based systems.

If you're having a "Netflix and chill" night, the last thing you want to worry about is finding something to watch—after all, you have better things planned for the night.

While most of your iPhone's features are intuitive or well-covered across the web, there are some features hidden deep within iOS that you probably never even knew about. (These could also apply to an iPad or iPod touch.)

Texting has become the king of communication—gone are the days where everyone called each other. These days, it's down-right weird when someone calls first. Whether it be on a phone or on a computer, SMS and MMS messages are the most common way people keep in contact, so why not make sure your app of choice is the best possible one out there?

Whether you're just getting your first Android, or are already on your fifth annual cycle of picking up the latest flagship, there is always the question of what to do after booting up your device for the first time.

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Microsoft's new voice-enabled virtual assistant, Cortana, is a lot like a blend of Siri's personality and Google Now's predictive capabilities—but the best part is it's baked right into the taskbar in Windows 10.
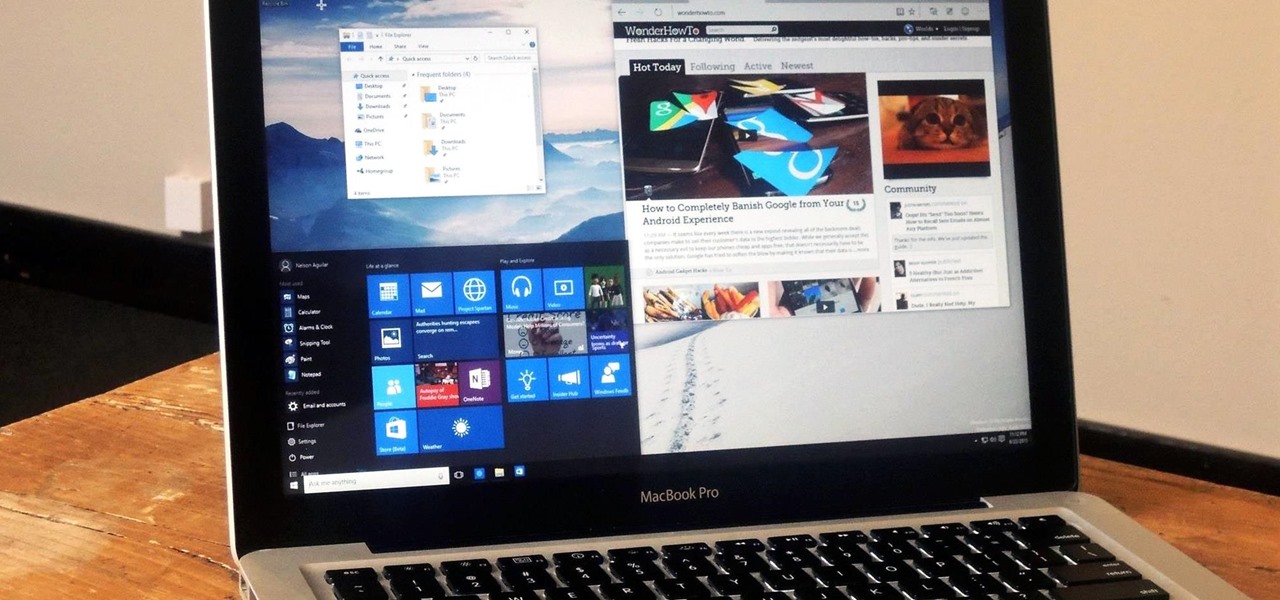
While Windows 10 is still a few weeks away from a public release, that doesn't mean you can't enjoy its brand new features right now. Anyone with an Insider Preview account can install Windows 10 on their computer. And that doesn't just go for those that own a Windows PC—Mac users can get their hands on Windows 10 as well.
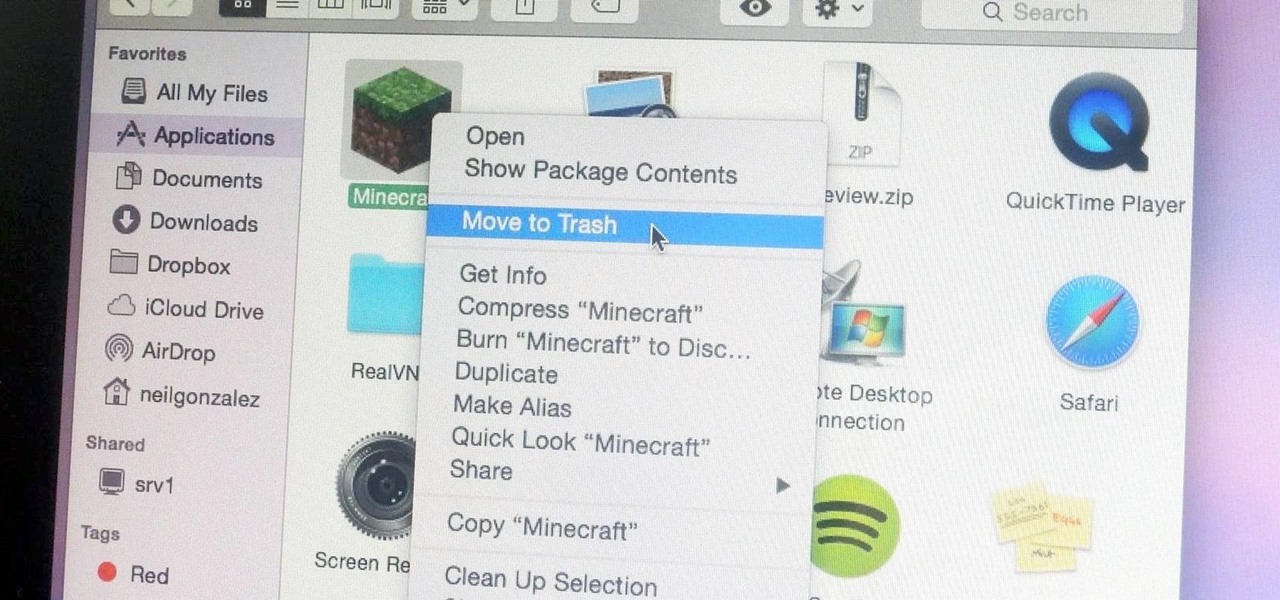
Uninstalling an app on your Mac isn't as straightforward as you would think. When you drag and drop an app into the Trash, then empty it, the main app itself may be gone, but many associated files and folders are left behind. So how do you get rid of them? There are a couple of ways.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new features you need to know about on the new iOS 9 for iPad, iPhone, and iPod touch.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.