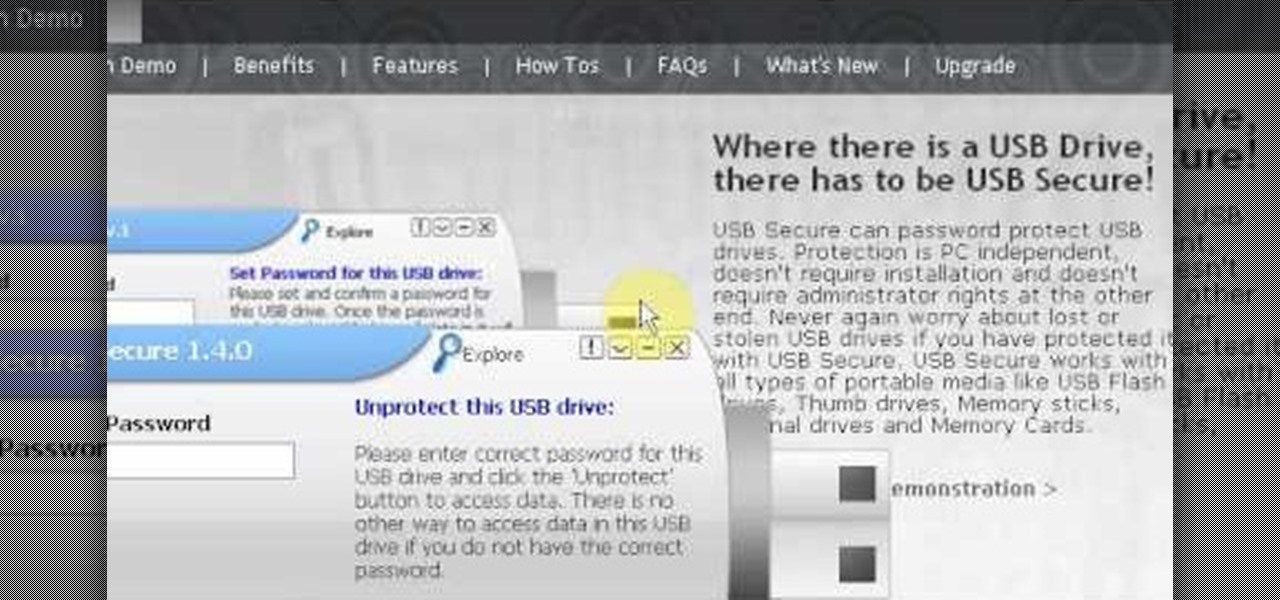
How To: Password protect a USB thumb drive
Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.


Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

Use three tools to create a simple ponytail. Use a hairbrush, a bobby pin, and a bungee band holder for this look. Using a bungee band instead of a standard ponytail holder eliminates some of the issues typically caused by pulling hair through ponytail holders. Start by using a bristled brush to brush the hair to one location on the head. Secure one hook of the bungee band in the ponytail and wrap the tail around the rest of the hair. Wrap it around again, and secure the other bungee band hoo...
Using ASP.NET Secure Services and Applications Services

Need to know how to tie a Bowline with a few ways of securing it? This way shows you how to secure it with a seizing so that it won't accidentally come undone. Included is a little variation of the bowline with a built-in seizing. If you don't have electrical tape to secure the bowline feed the bitter end back through the hole. It also makes it so you don't have a tail line dangling if you're towing something.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

Don’t play Russian roulette when it comes to your wheels. Keep your bike secure with these precautions.

A formal occasion calls for a classic look. You Will Need
Buns and updos are gorgeous hairstyles, with one caveat: If they're not pinned perfectly and securely in place, all your hard work braiding and curling will go to waste as your hair slowly unravels.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

Secure a square knot with tips from this video.

In this tutorial, we learn how to lash a bamboo tripod. First, you will tie a clove hitch by taking one piece of bamboo and wrapping the rope around it, then crossing the two sides of the string together to make a hitch. Next, you will secure the clove hitch around the third piece of bamboo. Now, you will rap all the pieces of bamboo together with the rope. Continue to do this until all the pieces feel secure together. Wrap the rope several times around each of the pieces, then wrap it in the...
Picking a secure password is not only important for protecting your privacy, it's also very easy. Provided, that is, that you know how to go about it. This free video lesson from CNET TV will walk you through the process. For more information, and to get started creating and using high-security passwords yourself, watch this video tutorial.

Kandee, a makeup, artist demonstrates a Gwen Stefani up do that was from an Elle magazine cover. Rub hair paste into your hands and smooth it through your hair. Then section crown to forehead and twist it counterclockwise until it starts curling up. Keep twisting and wrap it around into a tight knot. Use a bobby pin to secure it at the base. Then take another section of hair and repeat. Split the bottom section of hair that is left asymmetrically and twist each of those sections halfway and t...

TrueCrypt is a free application that lets you encrypt designated programs on your Ubuntu system to prevent unwanted access. Provided you select a strong password, intruders will not be able to open your personal files and documents. This instructional video walks you through the process of installing TrueCrypt on your Ubuntu operated machine and demonstrates an example on how to create an encrypted volume within a select partition.

The Clinch Knot is used to secure your fishing line to your fishing lure. In this video, learn how to tie a secure clinch knot, step by step. You can't fish without a sturdy lure, so watch the video and practice until you master the knot on your own. Once you've got it, attach your bait and you are on your way! Happy fishing!

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!
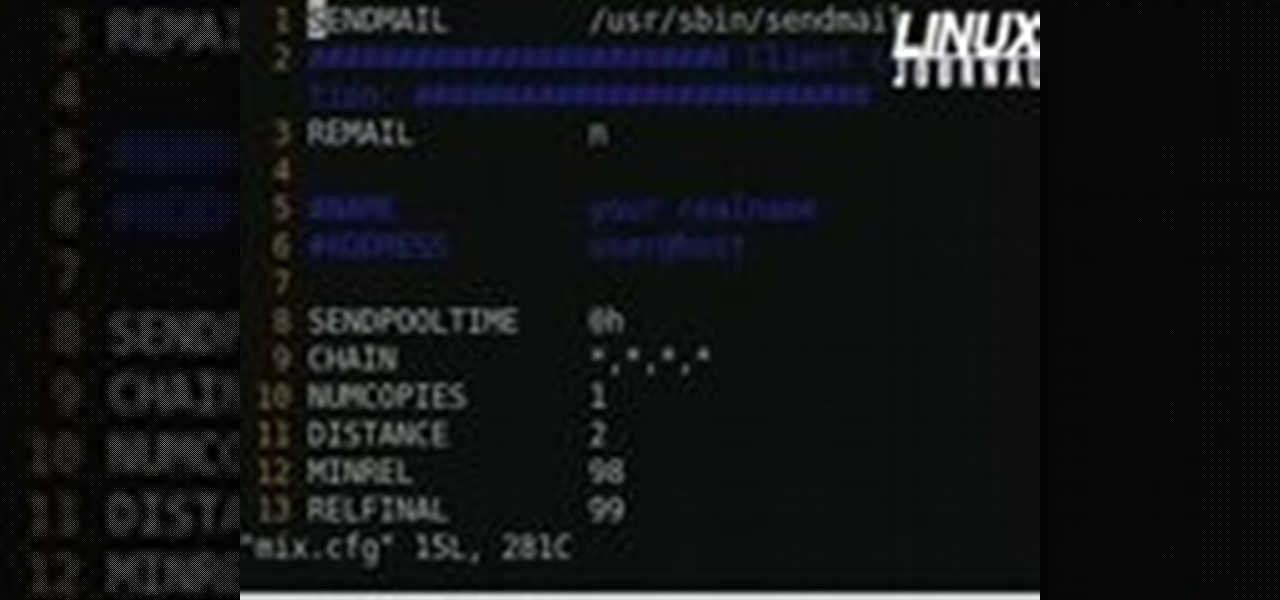
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.
A little precaution can go a long way to securing your online banking experience. Use these tips from Tekzilla.

Video: . This video will show you how to secure your kayak to a J bar roof rack carrier.

If Netflix's $9.99/month has deterred you from signing up for its streaming service, you're probably looking for cheaper alternatives to stream movies and TV shows, like Crackle (free with ads) or Hulu ($7.99/month with some ads). And now there's a new option for you when it comes to movies—Paramount Vault.

Do you like candy corn? Do you like vodka? Well, then this candy corn vodka cocktail will be a huge hit at your Halloween party (at least, with you).

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...

A tutorial on how to make a paper slingshot gun that shoots. Things you'll need: Bond Paper, Elastic, Scissor and Duct tape. Roll the bond paper half-wise. Secure with duct tape. Get another bond paper and fold it in half. Cut. Roll the cut bond papers length-wise and secure with duct tape. Form a "V" shape using the rolled cut bond papers. Attach to the first rolled bond paper to make a "Y" form. Secure with tape. Attach a rubber band on both ends. secure with tape. Follow these steps and Yo...
Like everyone, you're on Facebook. And, also like everyone, you'd like to control the access your Facebook apps have BEFORE you even install them. Well, you can, with a sweet little Firefox add-on called FB-Secure. Take control of Facebook app privileges before they read your secret diary.
In this clip, you'll learn how to secure a new Microsoft Windows desktop or laptop computer. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started protecting your own new Microsoft Windows PC, take a look.

Pop sensation Katy Perry has a wonderfully unique sense of style and fashion, from her clothes to her makeup to her hairstyles. And this video will show you one of the latter or the three— a great signature curls hairstyle.

If your home has a garage with a fairly standard garage door opener, that garage door is probably the easiest way for a burglar to gain entrance to your house. If you want to secure your home against such breakins, watch this video. It offers tips for securing your garage door so that thieves cannot gain access to your property and your family.

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video expla...
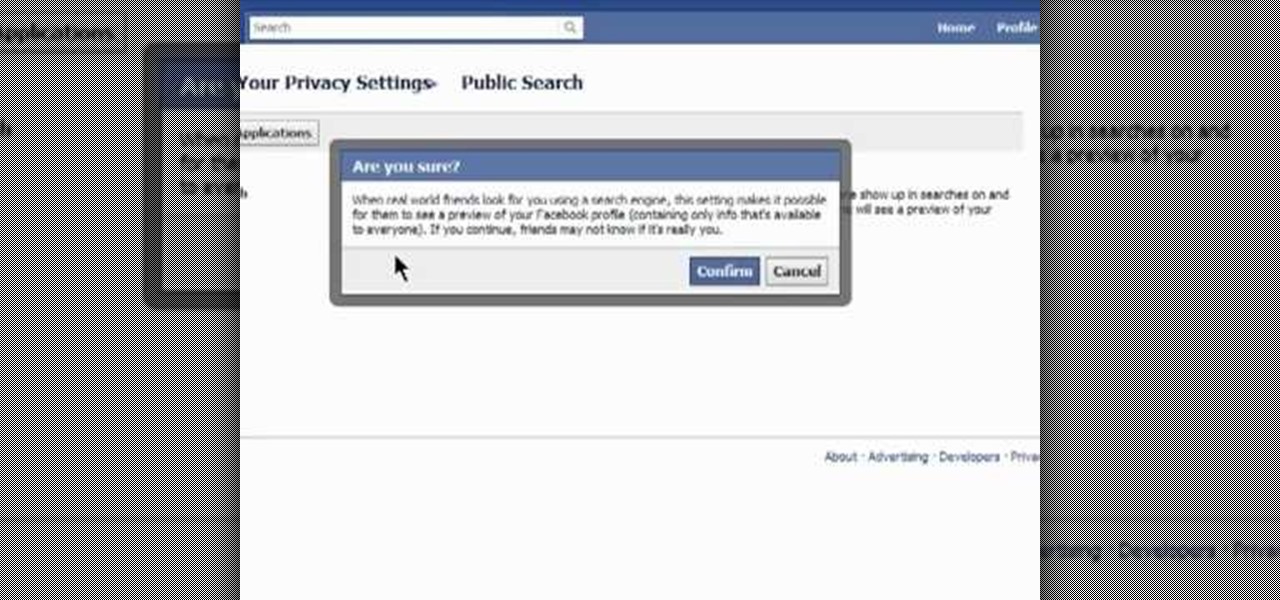
Looking for a guide on how to secure your public Facebook profile? This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

In this video, we learn how to wear a beret securely. This is used to keep the beret on your head so it doesn't fly away. To do this, you will need the beret and bobby pins. First, place the beret onto your head and style your hair around it so it looks how you prefer. Next, grab your pins and place then inside the beret holes onto your hair. Use a couple of the pins to make sure the hat and hair are connected and secured tightly. When finished, move the hat slightly to make sure it is secure...
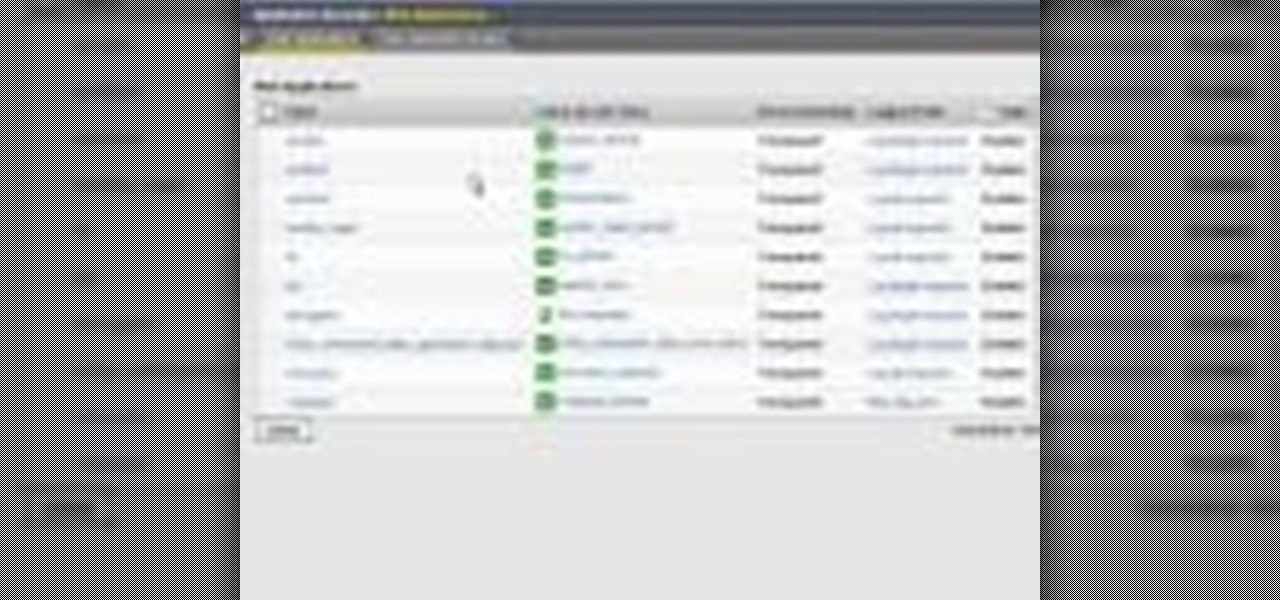
Learn how to create & secure applications with BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

In this video tutorial, viewers learn how to secure a Mac Book Pro. Begin by opening the System Preferences and select Security under Personal. In the General tab, users are able to put on a password when the computer goes to sleep or screen-saver, disable automatic log in and log out after a certain amount of minutes. To set a password, go back to System Preferences and select Accounts under System. Then click on Change Password and input your password. This video will benefit those viewers ...

This video is a tutorial on how to make a baby diaper cake. To begin, you will need to roll all your baby diapers from the waist down and secure them with rubber bands. Your top tier will have 8 diapers, the middle tier will have 19 diapers, and the bottom tier will have 40 diapers. Use rubber bands to secure all your tiers together. Next, glue thick ribbon around the tiers over your rubber bands. Follow up with decorations such as bows and extra ribbons. Use a cake stick to secure the tiers ...

Professional truck driver, Yesterday Irmani, teaches us how to tie a time honored, weight sustaining knot, for transportation purposes.

The Wood Whisperer is Marc J. Spagnuolo, a professional and passionate furniture maker, who also contributes to Fine Woodworking and Popular Woodworking. In this video, Spagnuolo shows us how to build a French cleat storage system. It's a very versatile unit, and gives you plenty of storage space without cluttering up a room.

Vines create the perfect look when grown over a trellis, arbor, or arch. You Will Need

Need to know how to tie a Double Sheet Bend? This is a more secure version of the standard sheet bend, and an excellent way of joining two ropes of equal or different diameter. He's using flex rope, but it's a generally good way of securing two lines together.

Studying to be a nurse? Then one important part of nursing involves making your patient comfortable. This nursing how-to video demonstrates how to attach Foley catheter tubing to the leg to avoid pulling. Our nurse uses a catheter securement device to secure the catheter in place. Follow along and learn how easy it is to use this device to secure the Foley catheter to avoid pulling.
Learn how to secure a web site using the new Membership and Roles features of ASP.NET 2.0. In this ASP.Net video tutorial, the topics include user registration, password recovery, and restricting access to content with roles.

From email to online banking, you never want someone poking around in your personal information. Learn what to avoid when creating passwords, and try these tips to keep your passwords safe and secure.