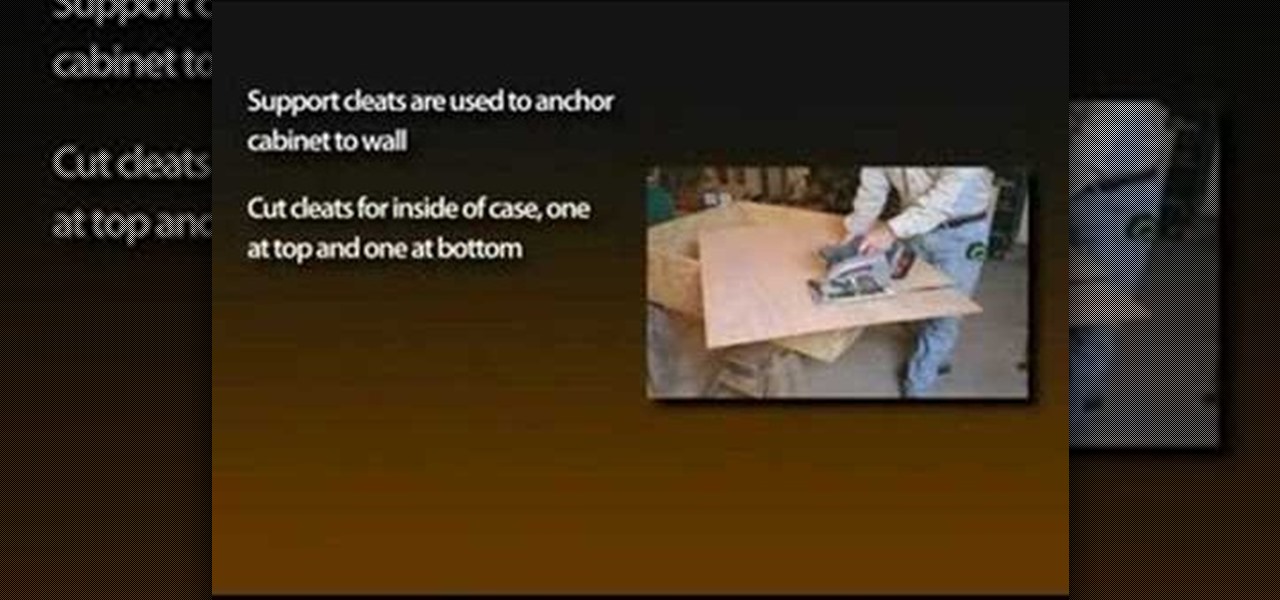
Learn how to install a blade into a jeweler's saw with this two-part video tutorial. Make sure your jewelers saw blade is facing outward and the teeth are pointing down. Run a finger over the blade before inserting it to make sure it is in the right position. Once it is in correctly, tighten the thumb screws at the top and bottom first.

Try these simple fixes to salvage your specs. Learn how to fix your eyeglasses with this helpful guide.

Board up a window for protection against strong storms and hurricanes. Learn how to board up a window.

Add instant elegance to your look by pulling your hair into a classic updo. You Will Need:

One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple maintenance on your automobile, but you may need a few tools. Invest in the basic tools and you'll be prepared for just about any car malfunction you can think of. These tutorials will help get you on your way, as long ...

Any long wrap can secure any size baby leaving your arms free with the basic front wrap demonstrated in this how-to video. Find the middle of your wrap. Place the middle marker in front of your chest. Wrap both lengths around your back and over your shoulder. Lift straps above the head to adjust. Grab your baby. Wrap lengths around the baby's bottom and under each of the legs. Depending on the type of wrap, tie off with a half or double knot. Watch this video infant care tutorial and learn ho...

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Cabinets are usually the most prominent feature of a kitchen and greatly determine the room's overall décor. Peeling paint, nicks and scratches, or a dull, dirty finish can plague older cabinets and really sap the pizzazz out of the living space. On the other hand, a fresh coat of paint can do wonders for cabinets and breathe new life into the kitchen. A repainting project can also save tons of money when compared to full cabinet replacement, which can easily total several thousands of dollar...

With the growing popularity of cordless power tools, it's extremely easy these days to accumulate a lot of portable tools, and when you add in quality corded tools, such as circular saws, routers, planers and air nailers, you can end up with a pretty hefty investment. These same tools are the first to “walk away” in a theft. Left lying around a shop or garage, they can also be somewhat dangerous for youngsters. A locking cabinet not only provides a secure place, but protects the tools as well...

Arrange your flowers in a bowl with these easy tips. Learn how to cut, secure, and add decorations to a bowl flower arrangement in this free video series from a professional florist.

Home cooks know firsthand what it takes to make delicious and amazing food for friends and family. One of the most effective ingredients to making foods as delicious as possible is herbs.

Losing your important data can be more painful than losing the hardware the data was stored on. Precious memories, files you don't often access but always want to have, there's so much you store on impermanent devices that you can't live without. Backing up your information to a secure, cloud-based location is the best way to stave off disaster here. Polar Backup Unlimited Cloud Backup Storage will give you an unlimited amount of cloud storage while making the process super easy.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

The wait is finally over. Apple just released iOS 13.2 for iPhone, the latest update to this year's iOS 13 release. The update contains a slew of exciting new features, such as Deep Fusion for 2019 iPhones, a suite of new emojis, the long-awaited Announce Messages with Siri, among many, many others.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

On Sunday, Microsoft did what everyone expected the company to do by unveiling the long awaited HoloLens 2.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

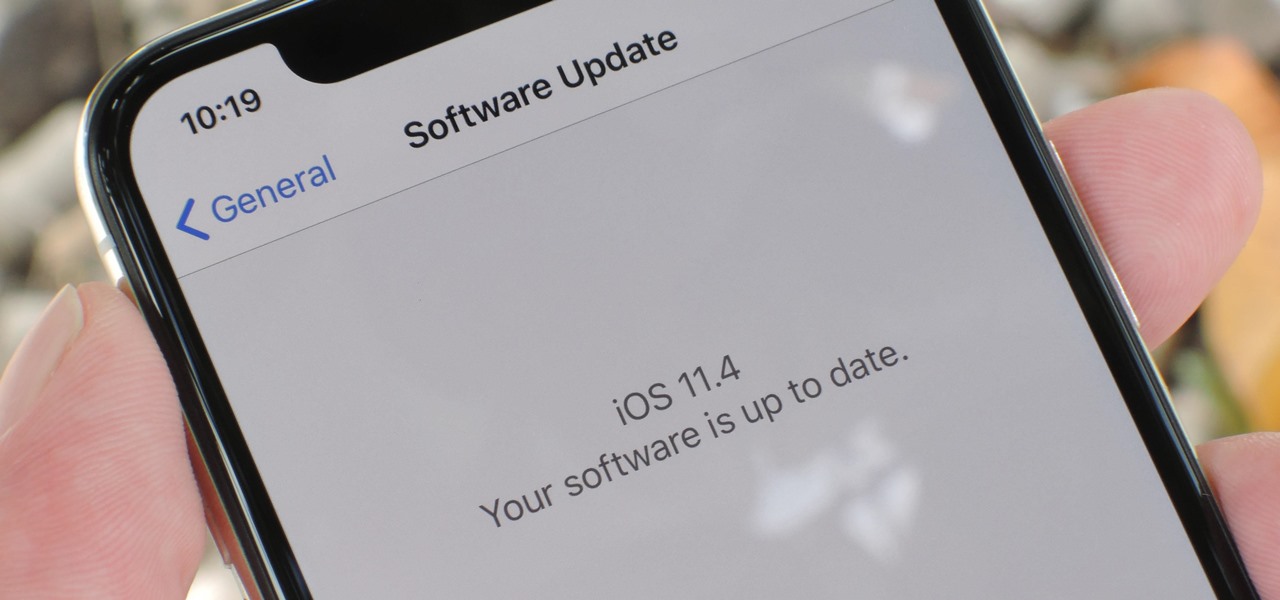
Talk about rapid-fire. Apple released the sixth beta for iOS 11.4 on Thursday, May 17. The update comes just three days after the release of iOS 11.4 beta 5, indicating that Apple is readily approaching the official release of the software. Apple has not issued an official iOS update since 11.3.1, which found its way to users over three weeks ago.

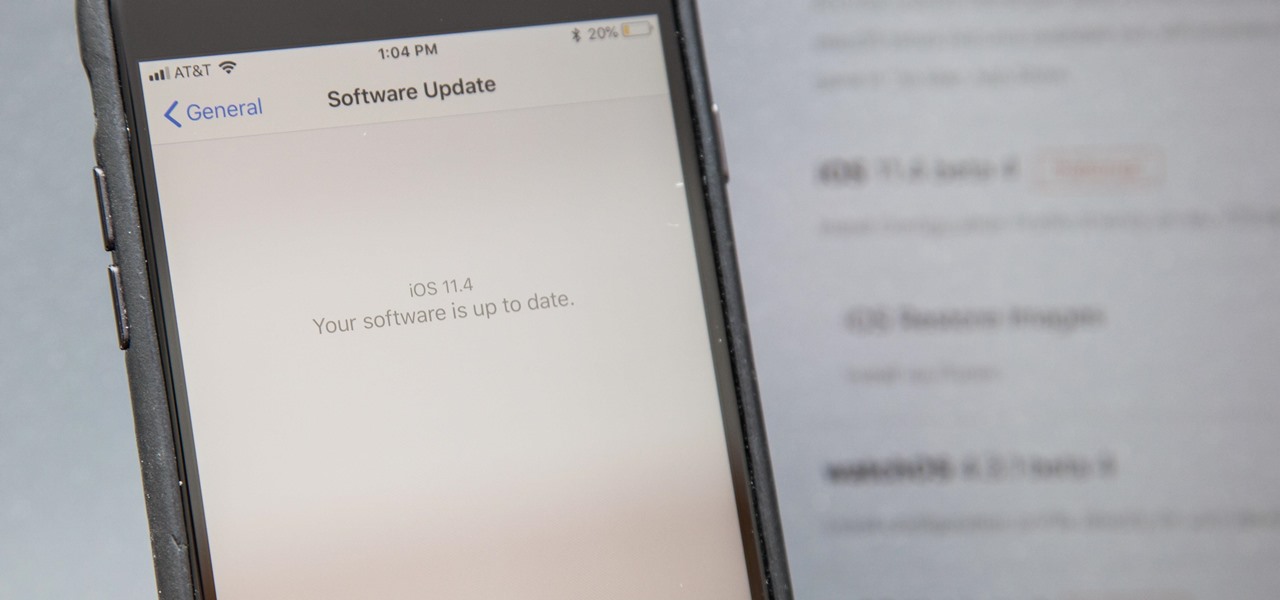
Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

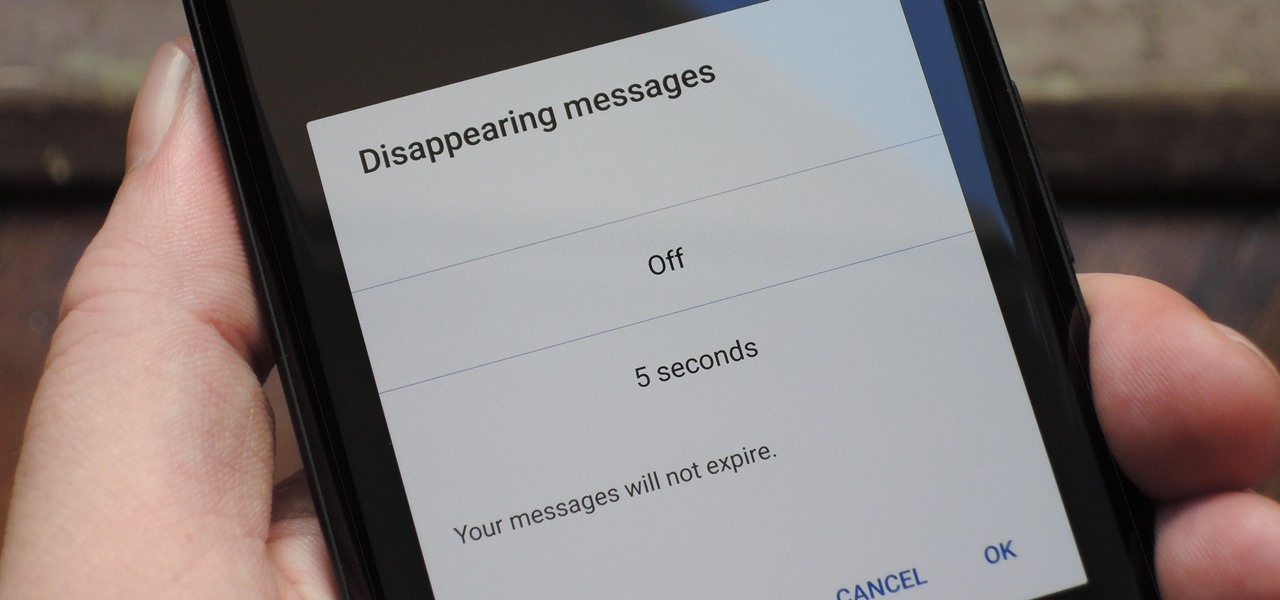
With Signal's class-leading end-to-end encryption, you can be sure your messages will remain secure as they travel to the recipient. However, once the message arrives, its privacy is completely dependent on the receiver, who could share it anywhere if they wanted. To patch this vulnerability, Signal added disappearing messaging.

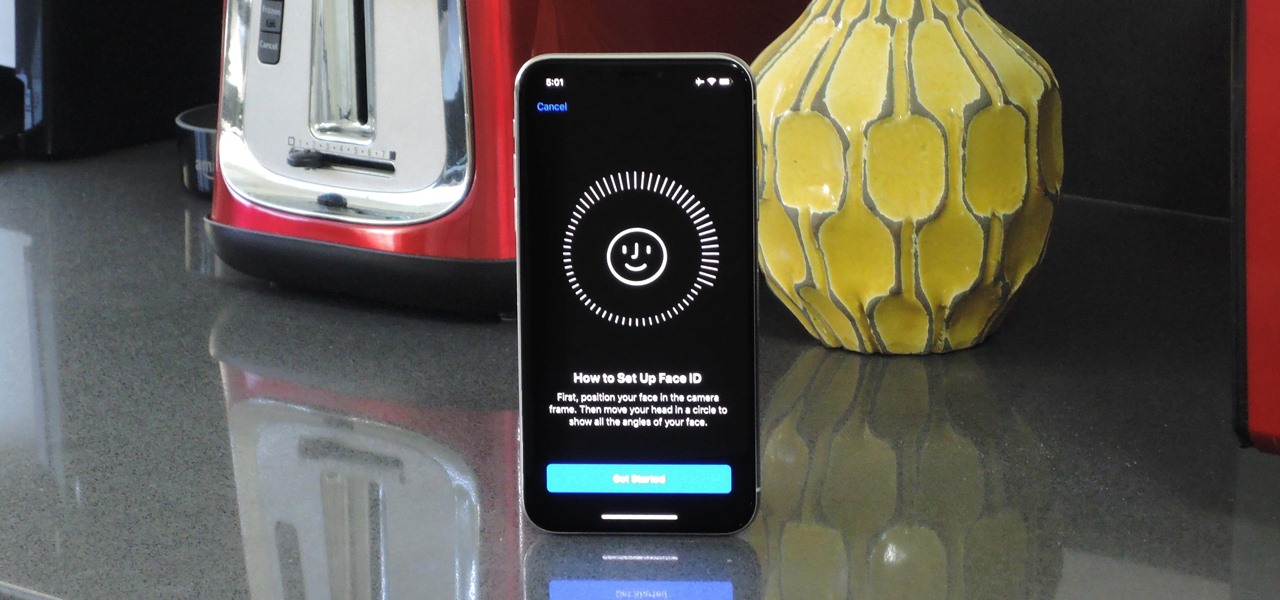
The cutting-edge iPhone X, XS, XS Max, and XR have one-upped their Android competitors when it comes to facial recognition. Apple packed these flagships with an array of front-facing sensors to complement its selfie camera, which allows the new device to more accurately analyze faces, which you need for Face ID, Touch ID's replacement.

As more companies begin adopting augmented reality in the workplace, providers like Vuzix reap the benefits.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

This week in Market Reality, we see two companies capitalizing on technologies that contribute to augmented reality platforms. In addition, industry mainstays Vuzix and DAQRI have business news of their own to report.

The Pixel is now rumored to be the next phone up in line to be getting a curved display. ET News just reported that Google is in talks to invest $875 million (KRW 1 trillion) in LG Display to give their next-generation Pixel 2 smartphone some curves around the edges.

The ride-sharing company Lyft has managed to secure $500 million in funding, which will certainly help its ongoing competition with Uber. According to recent reports, the cab firm is currently valued somewhere between $6.9 billion and $7.5 billion, but this still pales in comparison to Uber's estimated $70 billion valuation.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

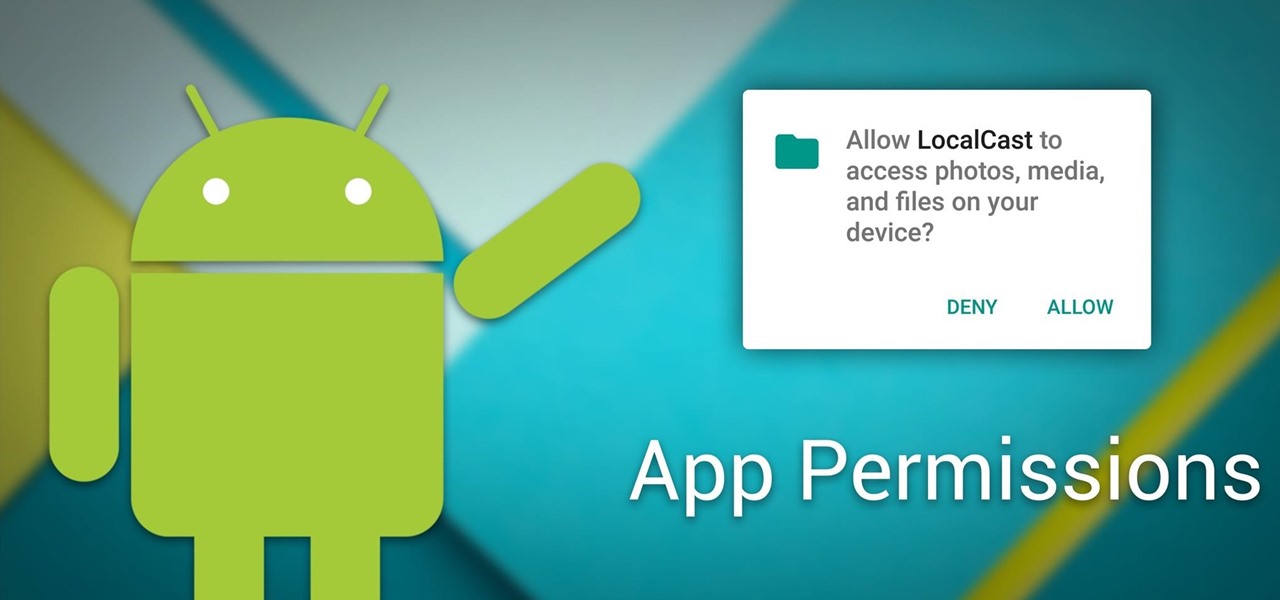
Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.