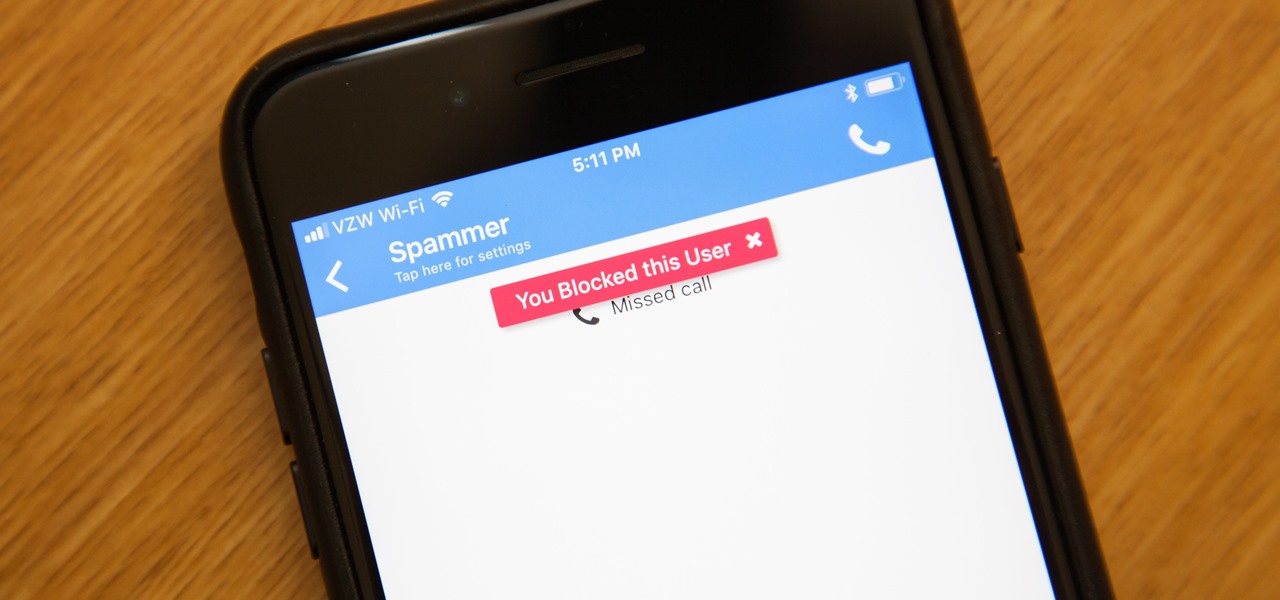
This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

This video shows you how easy it is to use an OSI swinging trailer hitch mount bike rack. Learn how to put bikes on it, secure and lock them.

It's almost as easy as it sounds - just don't forget to secure the cover to the spare tire by the two hooks. This video shows you how to put on a spare tire cover.

The SportRack bike rack lock kit can be easily added to many of the SportRack model racks. It includes two locks, one that secures the bikes to the rack and another that locks the rack to your trailer hitch. It only takes a minute to install and is dead simple to use, as this video demonstrates.

The memories on your devices are precious, even if you don't often get a chance to revisit them. The worst thing in the world is when something happens to your computer or phone, and you end up losing some of those memories because your files weren't backed up or your microSD wasn't fireproof.

With everything the last year has thrown at us, the odds are good that you've had to start working from home, complete with all-new challenges both for you and the technology you use.

The first step to getting your life together? Getting your online security together. After all, security when you're shopping, video calling, and more means more than ever in a digital age when anyone can copy your info or try to pose as you on the web. This Premium Privacy Bundle featuring Zenmate and StartMail will give you a secure VPN and encrypt your emails, all at a bundled price. The security duo is on sale for 60% off for a limited time, which means it's just $44.99 (regularly $113).

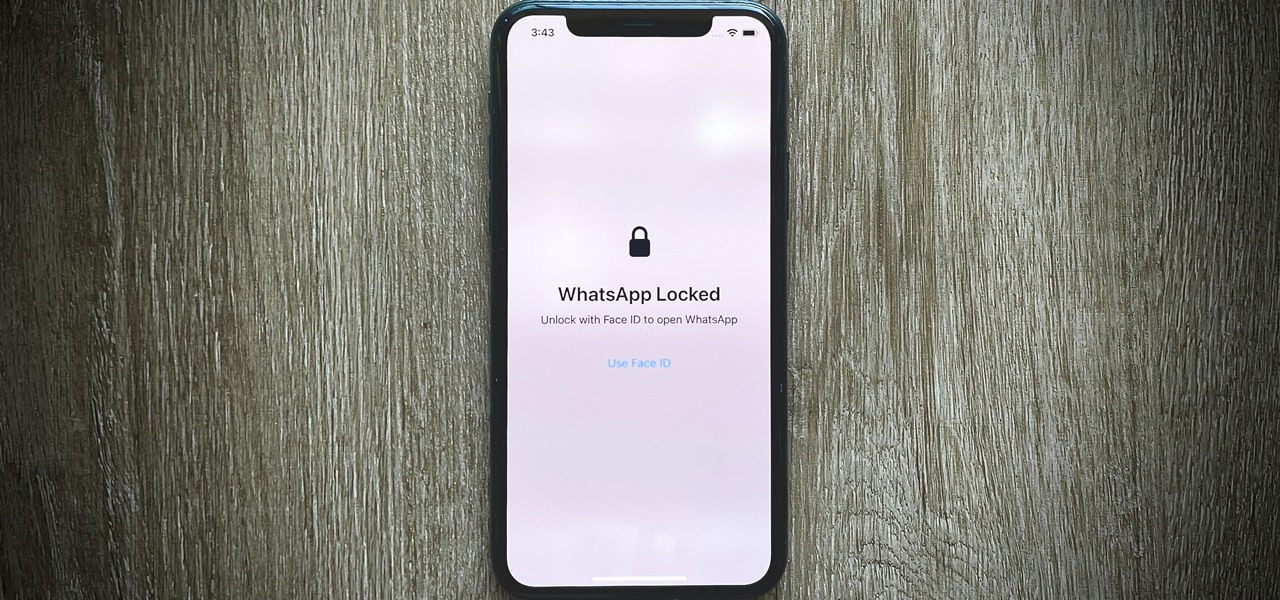
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

They say it is always darkest before the dawn. If that's the case, then perhaps there's a light ahead for Magic Leap after more unfavorable news in the form of executive departures.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

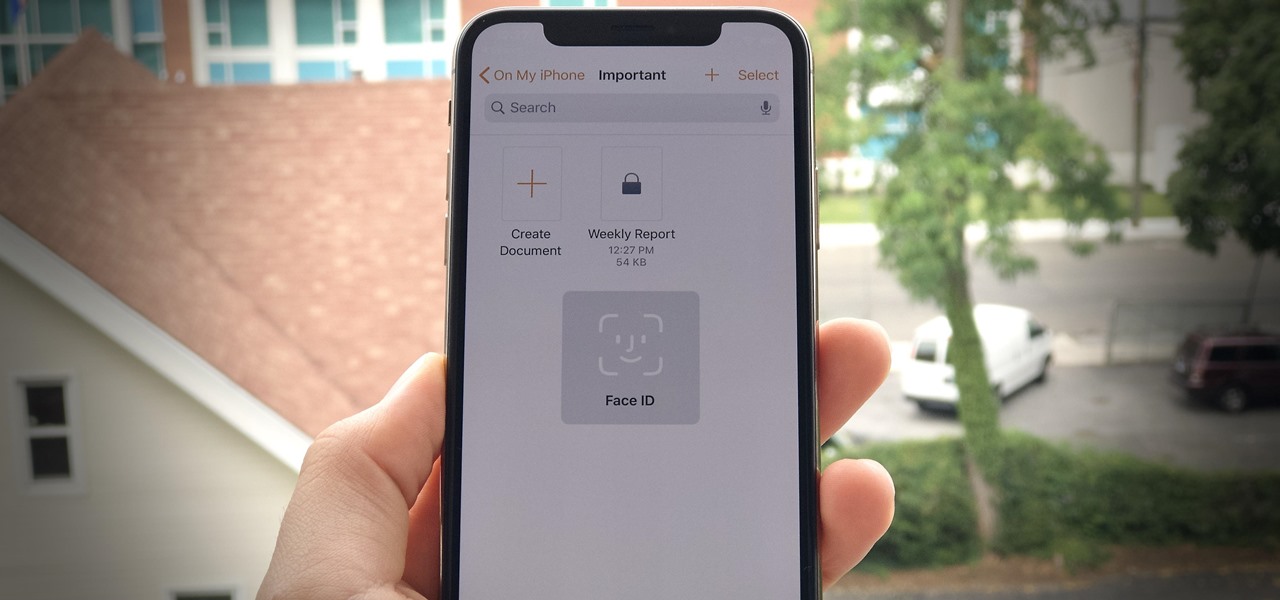
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

After about 40 days of beta testing, Apple pushed out iOS 11.4.1 to everyone as a stable build on Monday, July 9, exactly one week after the final beta appeared.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

BlackBerry has formally unveiled its latest flagship, the KEY2, during an exclusive event in New York. The Android-powered KEY2 retains its distinctive BlackBerry aesthetics with a physical QWERTY keyboard. Here's all the juicy details regarding Blackberry's followup to the venerable KEYone.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

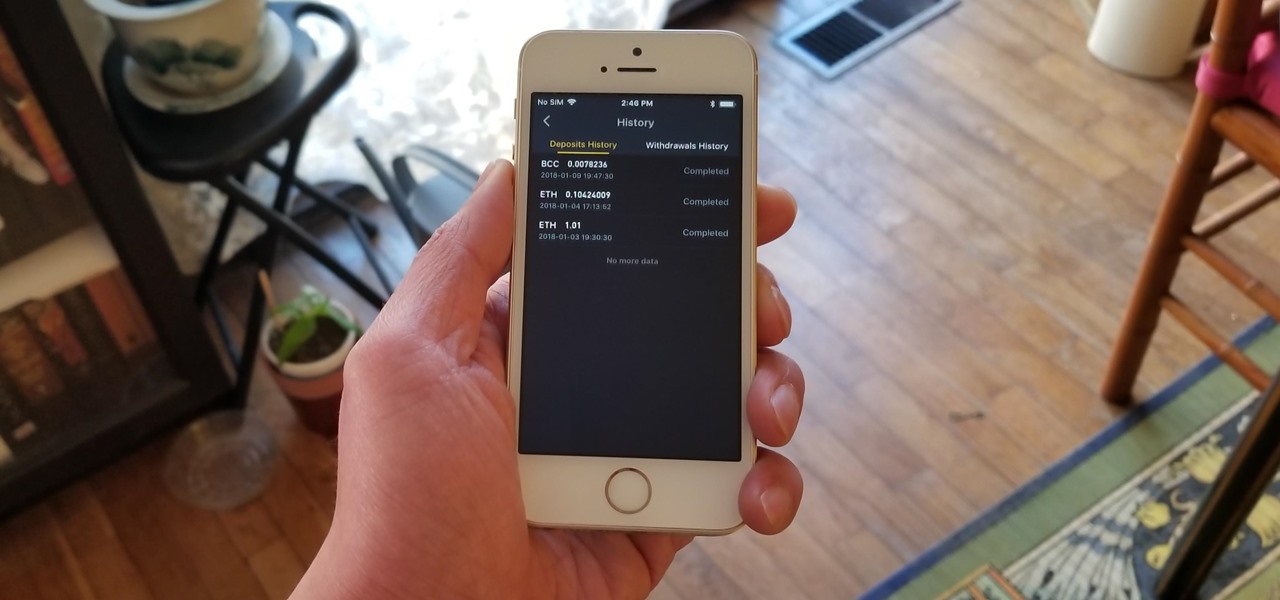
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

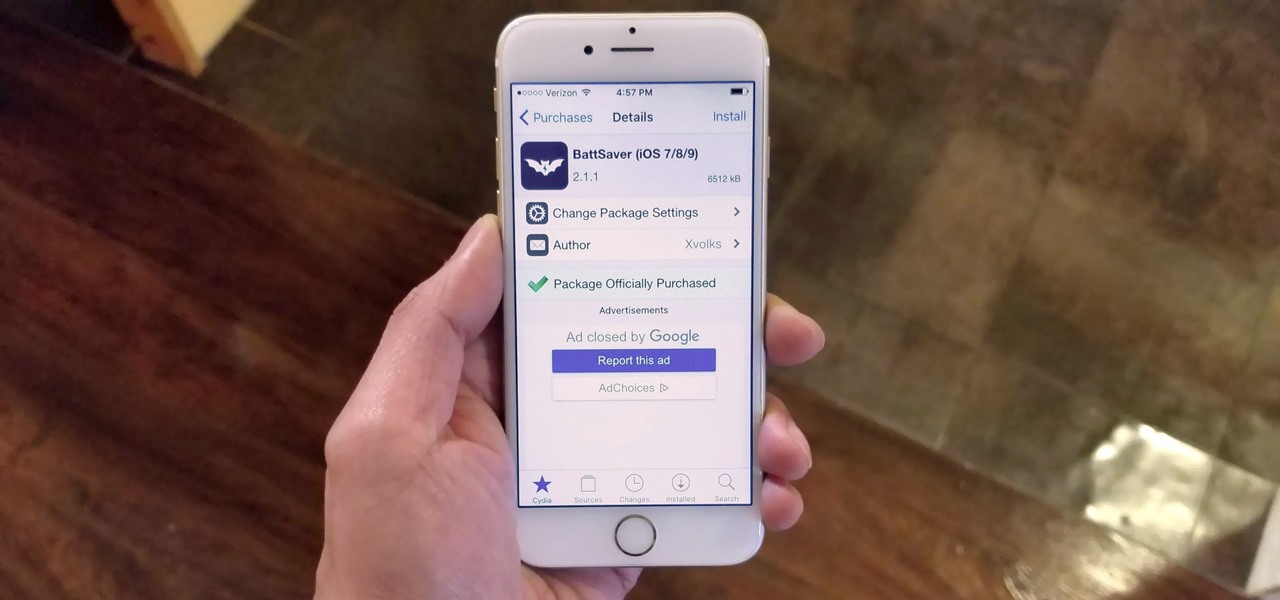
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buying an app in Cydia is simple and relatively safe.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.

While it's a more secure platform for messages and calls, Signal's job isn't to prevent unknown users from contacting you, so you run into the same issues you would with a regular phone number. People you know that you don't want to talk to may try to strike up a conversation and you'll still get spam messages. Luckily, it's easy to block these suckers.

The leading platforms enabling augmented reality technology lead our headlines in Market Reality this week.

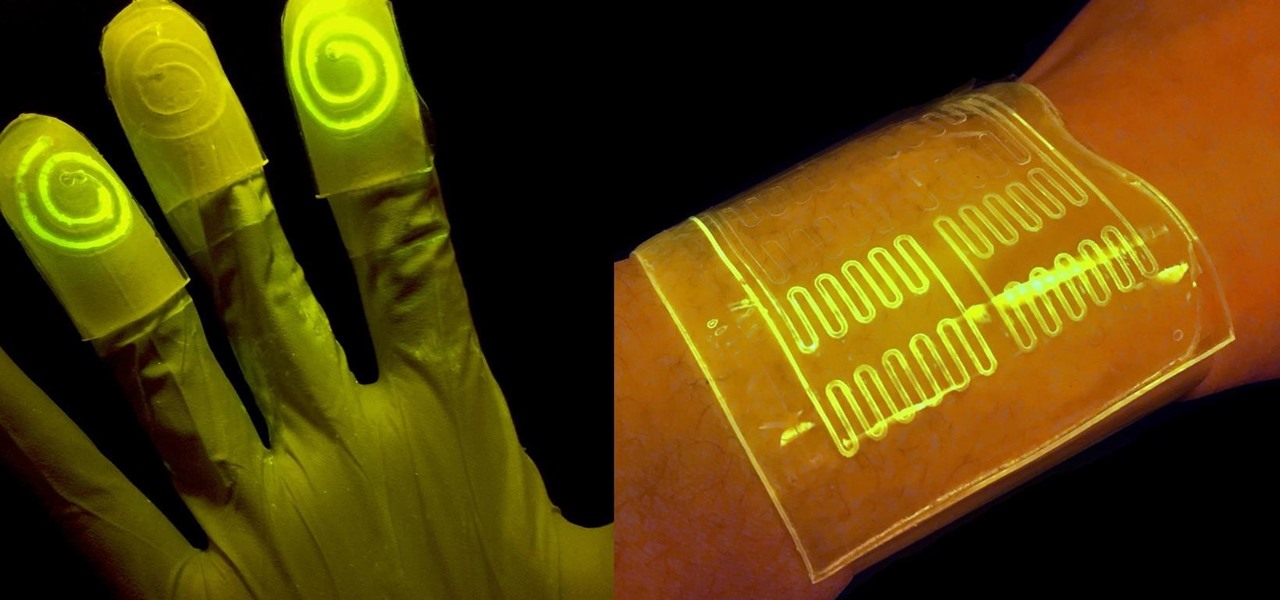
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are becoming a reality as researchers move forward with technology to use living bacteria in cloth to detect pathogens, pollutants, and particulates that endanger our lives.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

Responding to the emergence of Zika in the US, researchers investigated what type of repellent works best to reduce your odds of a mosquito bite from Aedes aegypti, the mosquito species that spreads the Zika virus.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

The story of Helicobacter pylori is a real testament to the tenacity of medical researchers to prove their hypothesis. It took decades before the scientific world would accept that the bacteria H. pylori caused ulcers.