Google's new Pixel and Pixel XL flagships are some very powerful smartphones, but as with any high-tech gadget, they're only as capable as the user allows them to be. So if you're a proud new Pixel owner, it's time to bone up on a few new features to help get the most out of your device.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.
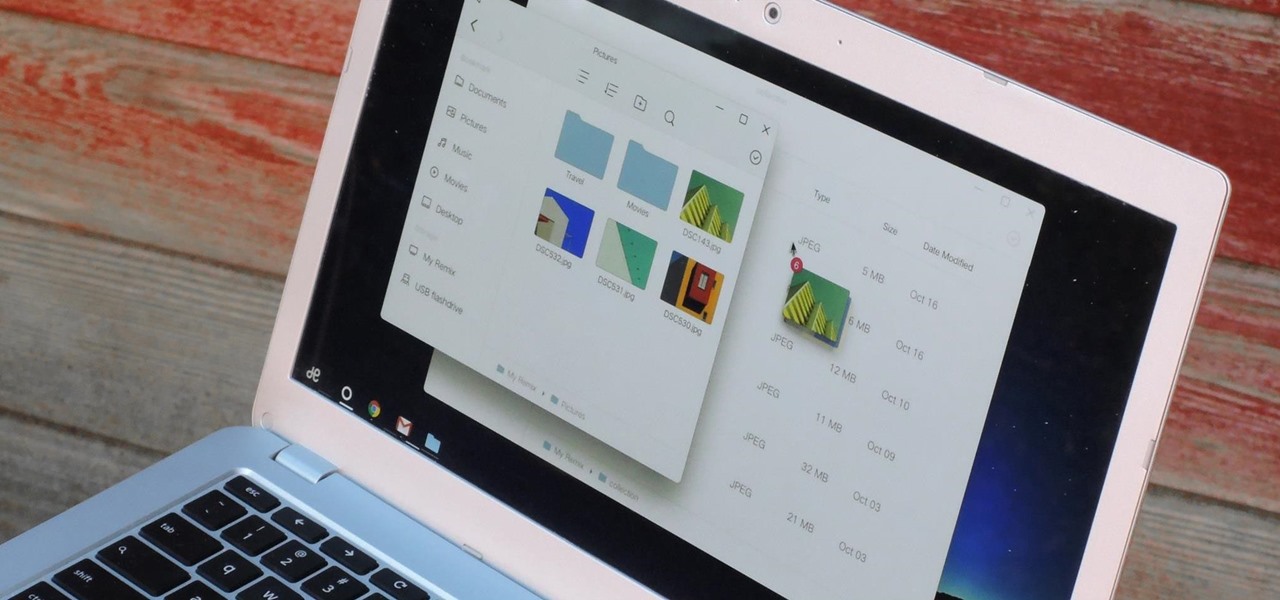
If you read the reviews on Google's Pixel C, you'll notice one big complaint about the tablet/laptop—most reviewers feel that Android simply isn't ready to be used as a desktop OS. The developers at Jide felt the same way, so they set out to make a custom version of Android with proper multitasking support and a UI optimized for the mouse and keyboard.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

I'm often reluctant to use a home screen launcher other than the stock one on my Android. Once you're well acclimated with something, complacency sets in, welcoming change with much resistance. Well, my friends, I have seen the error of my ways...

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

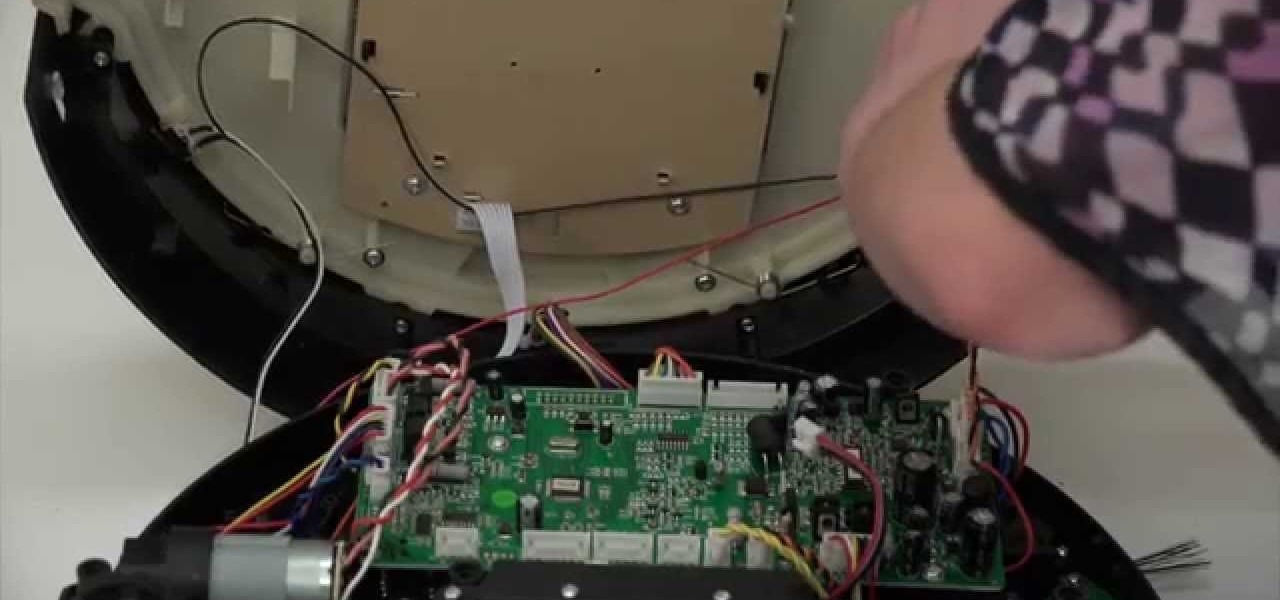
A step-by-step guide to replacing the side brush motor on bObsweep Standard or Pethair. Follow the video or multimedia directions in order to open up bObsweep, remove the main board, replace the side brush motor, then close your vacuum for future use.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

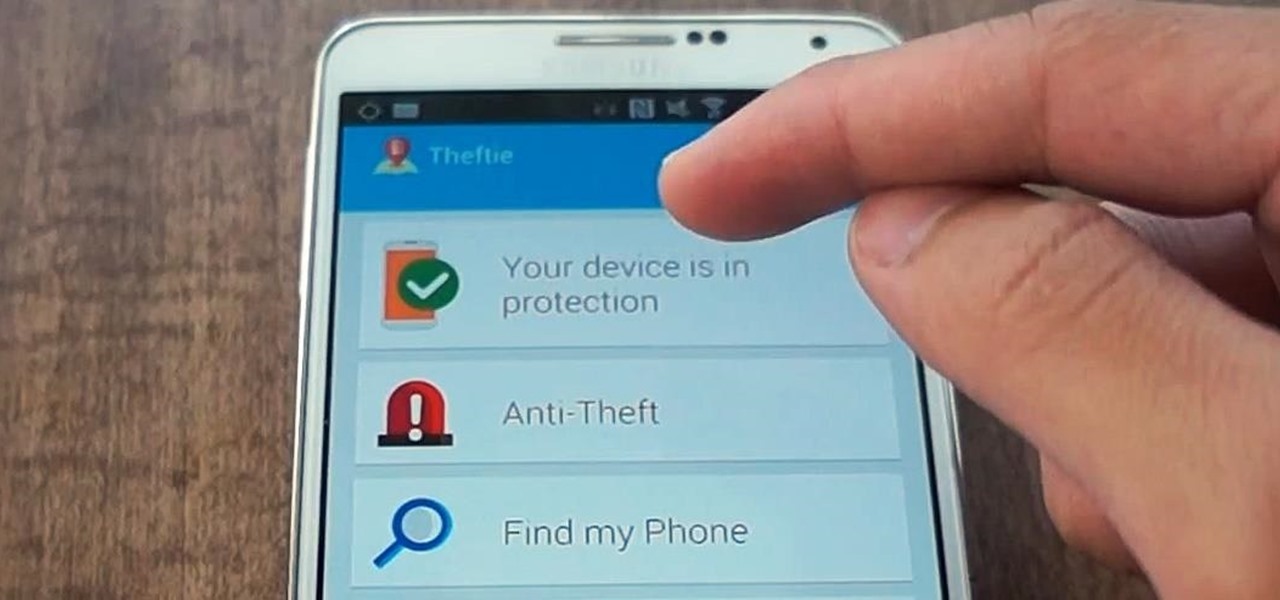
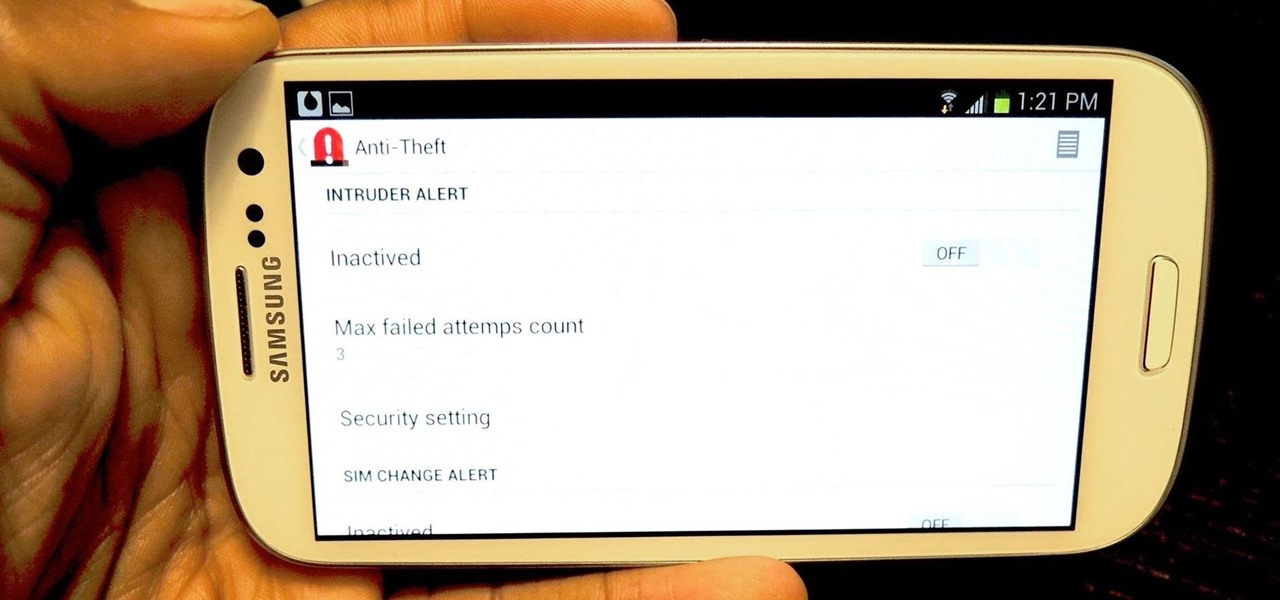
When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!

If you're as bad at locking your Nexus up as I am, you have the "slide" option set for your screen lock. It may not be the most secure option, but it's definitely the easiest way to unlock your device while being able to utilize lock screen widgets.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

Nine times out of ten, when you pick up your Samsung Galaxy Note 2, you already know what app you're going to be using. If you only have Swipe to unlock enabled, finding that app is as easy as swiping and locating the app on your Home screen or in the app drawer.

I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

In this episode of YouTips4U, learn how to do a new style to your hair following the steps outlined here. A fishtail is a variation of a traditional braid and works well for people with thick hair. You will need two hair ties and a ribbon (which is optional). In the first step, bring your hair to one side of your head and tie the ponytail to secure it. Divide pony tail in two equal sections. In the first section take a 1/2-inch to an inch piece and fold it over to the left so that it is in th...

If you're anything like me, the heat of the summer can often be unbearable. Where I live, it often gets as high as 108 degrees Fahrenheit, so anything that cools off is a welcome and amazing thing. Mister fans are especially amazing for cooling off, but they are usually very big and attached to buildings (which currently is way out of the picture for me.)

It takes talent and training to drive a semitrailer. See if you have what it takes to operate one of these rigs on the open road.

There are countless ways in which you can turn your love of tech and coding into a full-fledged career — from developing apps and websites as a freelancer to working in the IT departments of small startups or major tech companies. But one of the best ways that you can put your programming skills to good use is to join the increasingly important world of cybersecurity.

If you're using a VPN app to block ads or secure your Galaxy's internet connection, Samsung has decided you need yet another non-dismissible notification from One UI to tell you about it. Not just a status bar indicator like Bluetooth or Wi-Fi, but a full-size alert that can't be dismissed. The entire time your always-on VPN is running.

The UK has officially exited the European Union, completing the long and tumultuous Brexit story and putting the storied nation once again on its own on the international stage.

While Apple and Google have paved the way for developers to create web-based AR experiences through their respective mobile toolkits, an open source option has entered the space.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.

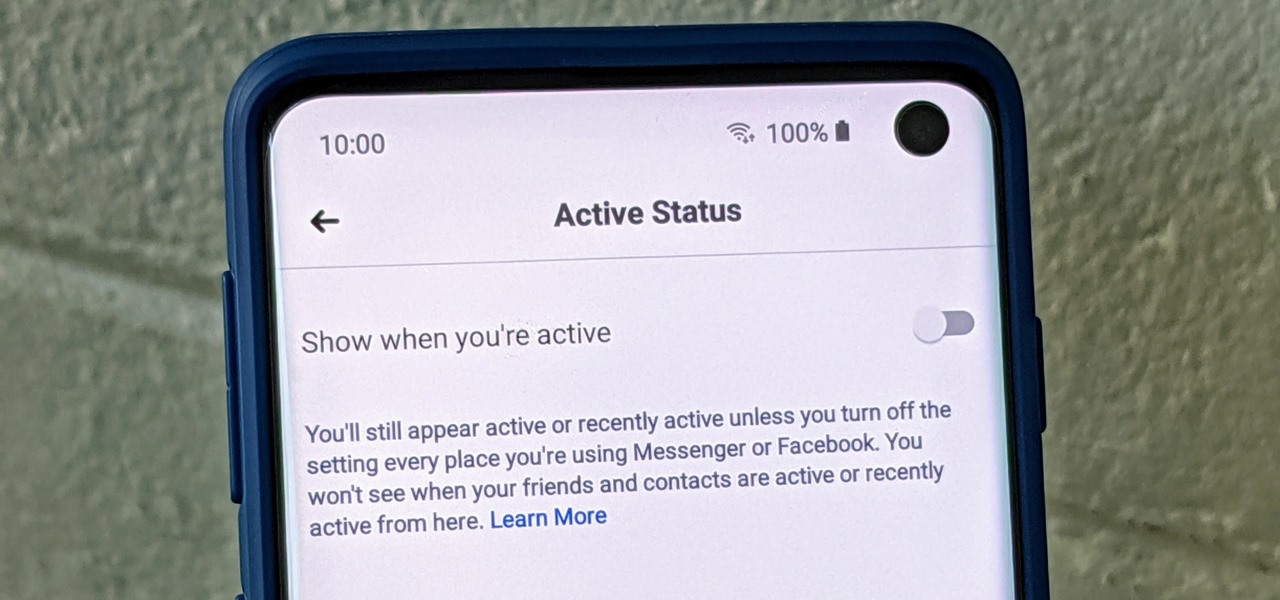
Have you ever wondered how some people know you're online even though you swear you set the Messenger app to hide your active status? No, you're not crazy — it's an issue with two conflicting settings, and there's an easy fix.

After entering into settlement talks with Epic Games over the gaming giant's trademark challenge, Nreal is now ready to open up the floodgates to potential early adopters in the augmented reality space.

Following on the heels of the announcement that ThirdEye's Gen X2 MR glasses began shipping in September, ThirdEye has revealed it has developed an app that helps soldiers aim their weapons during battle situations.

Increasingly, cutting-edge platforms like blockchain technology and augmented reality are overlapping, forging new digital frontiers that promise to change the way we interact with the virtual and the real world.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.

Haptic feedback is one of the iPhone's most underrated features. With Face ID, you'll feel a satisfying tap or two when buying something in the App Store or iTunes, unlocking protected notes, viewing saved passwords in Settings, and the list goes on. For the first time, Apple has added haptic feedback when unlocking your iPhone via Face ID, as well as a way to disable haptic feedback for Face ID entirely.