As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.
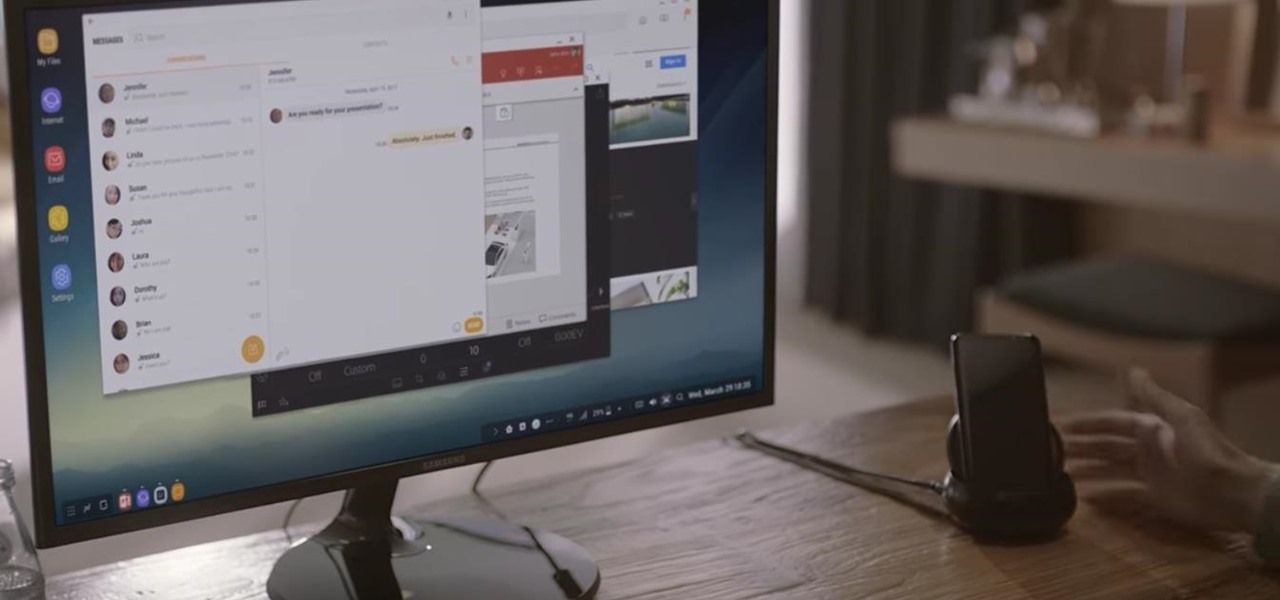
Samsung's new Galaxy S8 can turn into a PC with its DeX dock, but while that may sound like the future of mobile computing on the surface, there are definitely a few issues with the entire setup.

Throughout the summer and fall of 2016, in the sudden whirlwind that was Pokémon GO, it was hard to go anywhere in public without seeing someone attempting to catch Pokémon. Now, thanks to an upcoming platform called Motive.io, from the Vancouver company of the same name, location-driven application development will soon be accessible to everyone.

Google's monthly Android security updates are generally welcome—at the very least, they provide a feeling of security that our device is now somewhat safer than it was 30 days ago. Vulnerability patches, slight enhancements to performance, and overall bug fixes are generally included in the monthly OTAs, but as it turns out, they're not always for the better.
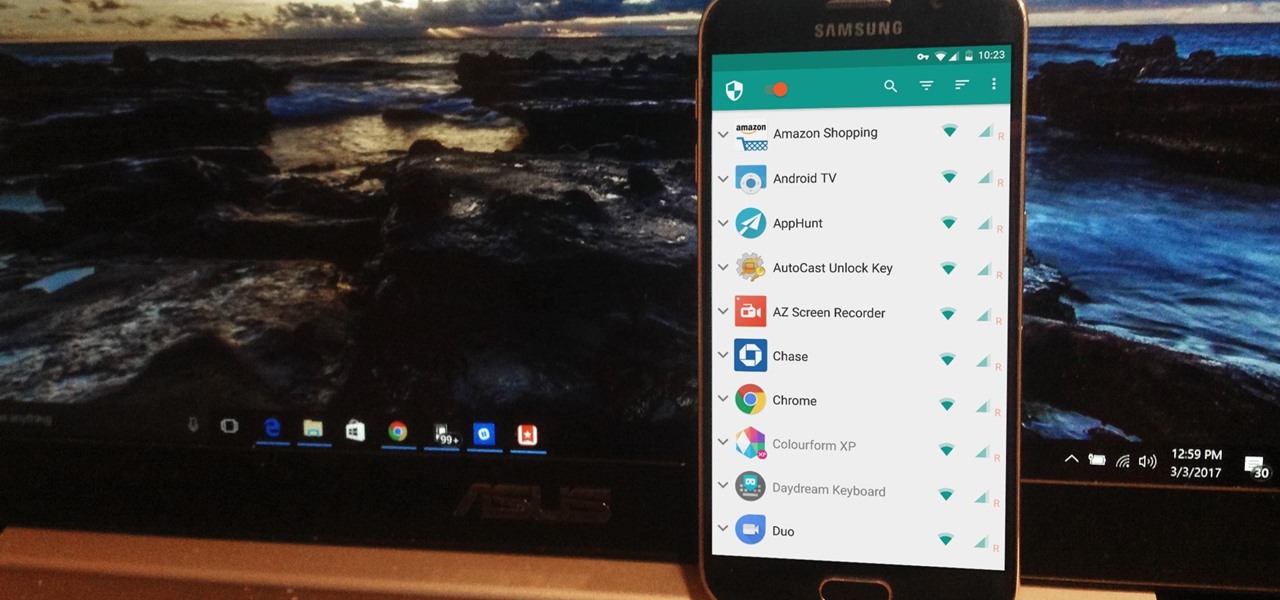
NetGuard is a well-established app known for its highly secure firewall, which blocks unwanted web activity from individual apps that can take up both precious bandwidth and battery life. Not quite as well known, however, is the fact there's a second official version of NetGuard that comes with a hidden ad-blocking feature, which can be activated with just a little tinkering in the app's settings menu.
If you're ever in a major accident or have a bout with acute onset health problems, first responders will need to know as much information about you in order to provide proper care. For this reason, paramedics and firemen have been trained to search a subject's cell phone to find ICE (in case of emergency) contacts that know your allergies, blood type, and other vital details.

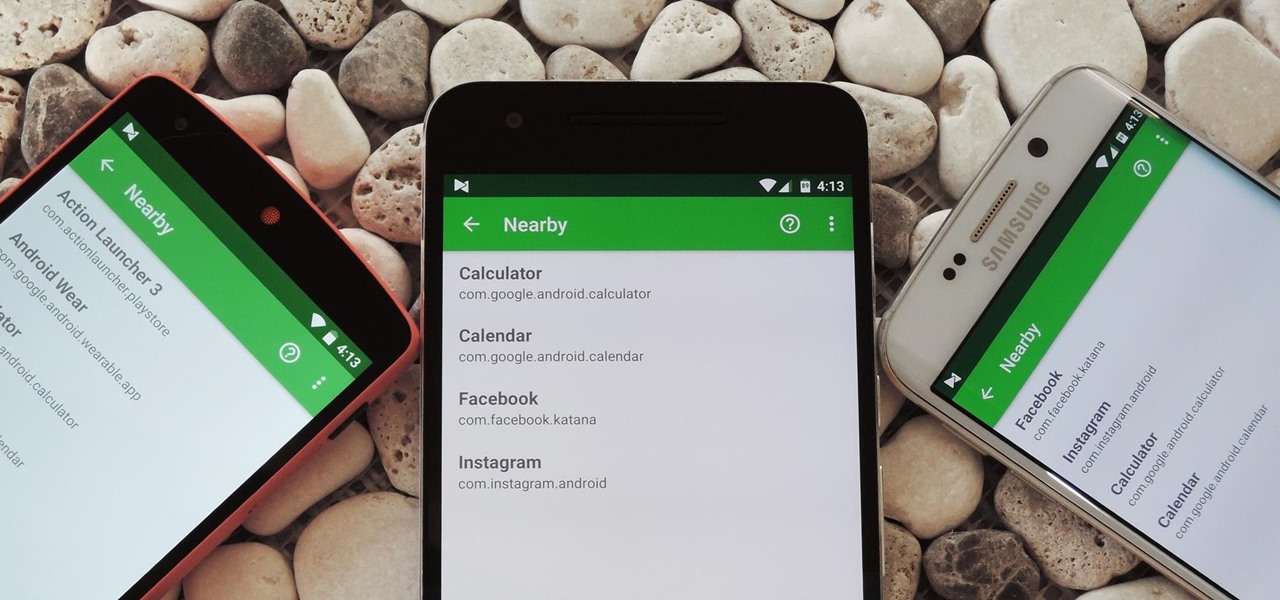
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

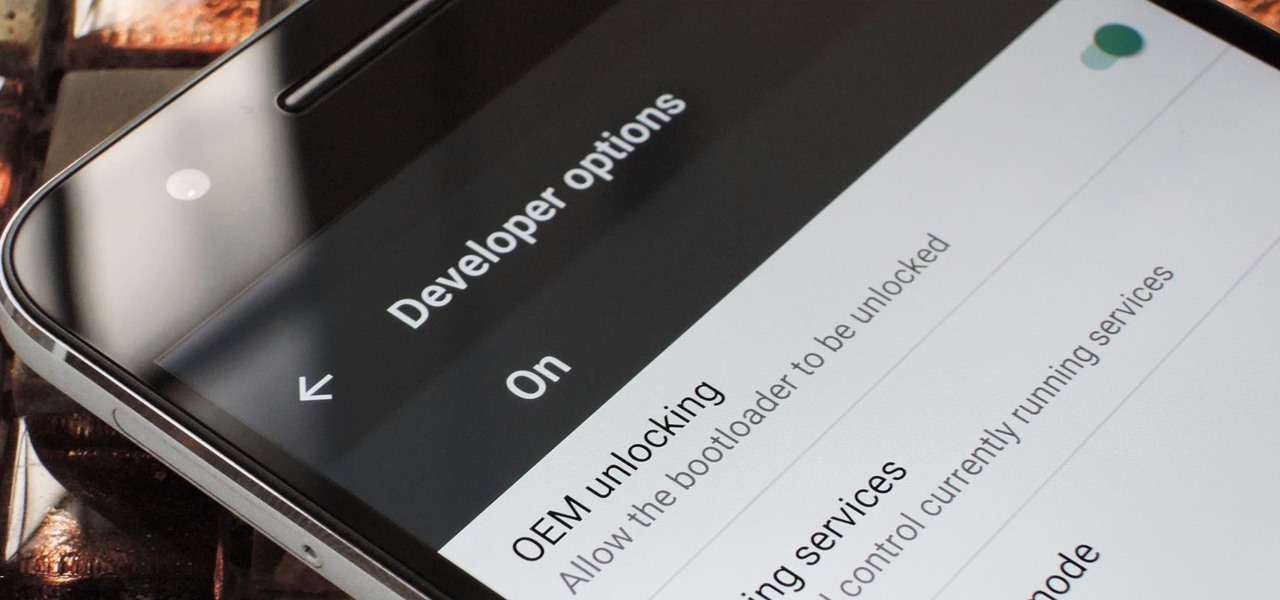
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

Android has a built-in browser called WebView that any app can use, which makes it easy for developers to display webpages without actually having to build an internet browser into their apps. But WebView is a stripped-down, bare bones browser with no ties to Android's default browser, Chrome, so none of your synced data like bookmarks, passwords, and history is available when an app is using WebView to display a page.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

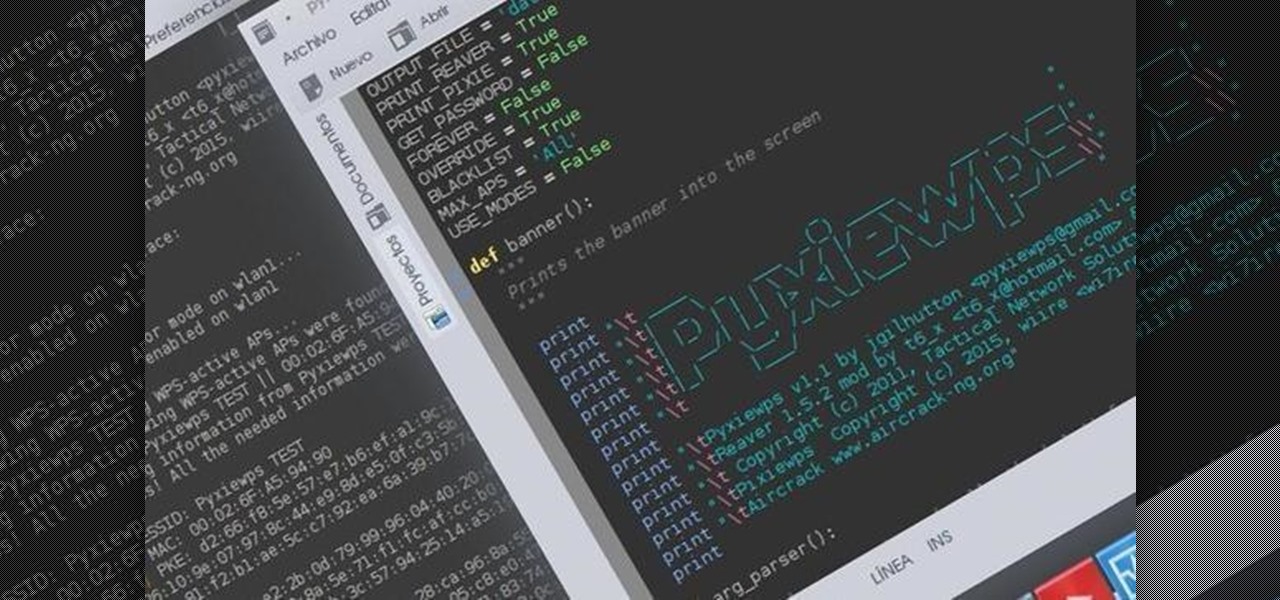
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

The increased sophistication of smartphones and apps have allowed us the luxury to never leave our homes. Everything from coffee to food to dry cleaning can be delivered straight to your door without ever leaving your couch, which can can be a godsend during the winter months when you'd rather not risk leaving your warm bed. But during the summer, you gotta ditch the comforter and go enjoy outdoors.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

Welcome back, friends! Many times, businesses, friends, and family will lock their zip files with a password to keep their files secure. It is reasonable, and understandable. Well, thanks to hackers, there are many ways to get past this wall of security.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

Every bObi robotic vacuum works best with a clean dustbin and brushes. Luckily all of bObi's parts are easy to remove and wash, so you can do so whenever you notice large amounts of debris collected.

Both bObsweep Standard and Pethair models have two bumper sensors inside their covers. Whenever Bob runs into an obstacle, the sensors tell Bob to back away.

I'm a firm believer that a sandwich is the ultimate food. It's filling, but not heavy; it has carbs, protein, veggies, and sauces; and it's easily customizable. Add that all up and you've got the absolutely perfect lunch.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

If you've got a desktop computer, I can almost guarantee that you've got a widescreen monitor set up in landscape mode. It's how just about everyone uses their monitor these days, including myself. Except that it's not always the best way of working.

Everybody loves the stars. Well, I certainly do. As a child I'd spend hours outside during summer nights marveling at the seemingly endless amount of sparkling dots spanning the sky. Maybe you have children of your own and want to create a sparkle in their eyes, or in your own. This tutorial will provide a basic method of bringing the stars inside—at least, in part.

Starting April 10th, you'll will be able to book 15-minute appointments online to try on an Apple Watch in person at Apple Stores across the world. With the April 24th release date just around the corner, making an appointment is a great idea for those who are unsure about which color and size to purchase—or if they'll even want one.

If you were around when the Nintendo Wii first launched, you remember how revolutionary the device was at the time. When I first encountered one, I was amazed at the simplicity of its controls, namely the fact that the Wii Remote (aka Wiimote) just felt like such a natural way to play a game.

Beginning with KitKat, I've been used to customizing every aspect of my Android phone, but with the release of Lollipop, there is quite a bit of catching up that developers need to do. Most customization features, like quick settings rearrangement and theme support have already been ported over, but any type of lock screen customization has been noticeably absent.

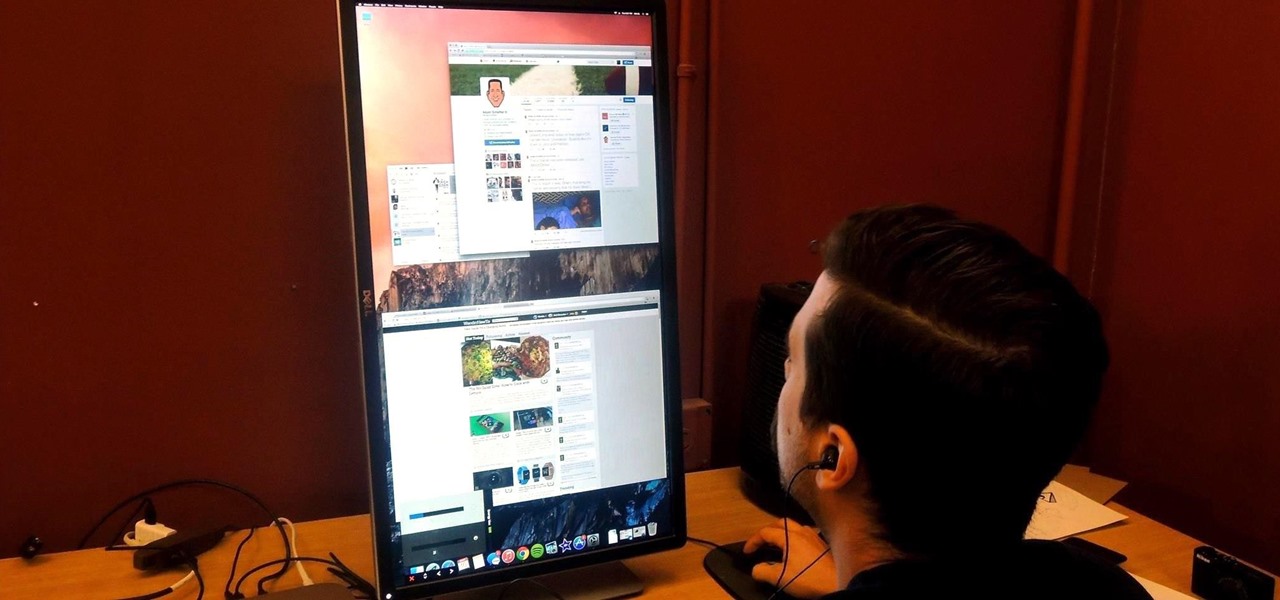
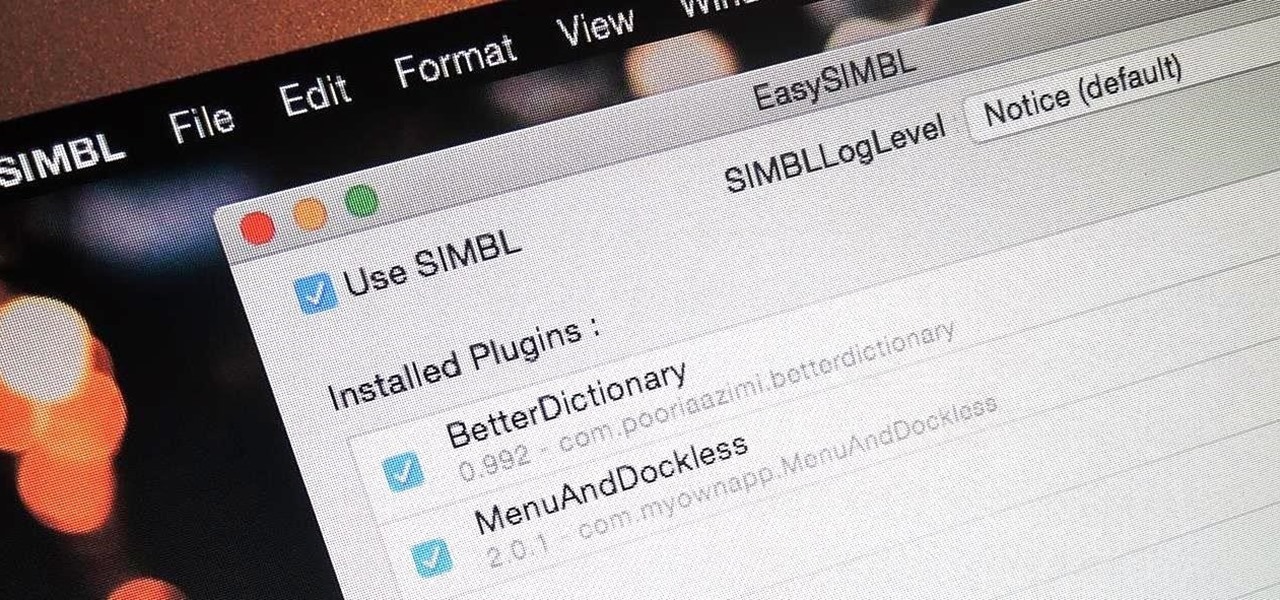
When you buy a Mac, you accept that you're giving up the customization found on Windows or Linux systems for a more fluid and secure machine. This is great for most consumers, but for those of us who'd rather opt for a tailor-made experience, there are always developers that can combine functionality with stability.

Whether you choose to hang an authentic or artificial pine Christmas wreath on your door — or an entirely different type, like ones made of paper waste or even food — chances are you've spent a year or two struggling with how to keep your decor hanging. With one easy to apply, quick to remove trick, you can skip the shiny wreath holder and any further damage to your front door.

You've found the perfect tree — or so you think. As hard as we try to display an ideal tree each year, both plastic and pine can disappoint, especially when you're shopping on the cheap.

Holidays are a time for good food and good drink, but more often than not, we substitute good drink for, well, cheap drink. However, cheap wine doesn't have to be bad.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

Accessing your favorite and most recent contacts on your iPhone is now faster than ever before, thanks to the iOS 8 update. Just double-click your Home button, select your contact above the app switcher menu, then choose how you want to contact them.

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

Most times when you take your smartphone out of your bag, pocket, or purse, you probably know exactly what you're going to do with it. Make a call, send a text, take a selfie, browse viral videos on YouTube, or one of the other many things a smartphone can do nowadays.

Here is a tutorial to show you how you can easily make this much loved Frozen character with Play-Doh. Using some simple techniques and clever tricks, you can make your very own Olaf.

While their merger with Microsoft has lead to a seemingly complete halt of new device development, some Nokia employees are still hard at work to bring new software to the table.