It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

There's a lot of personal information residing on your phone, possibly even more than on your computer, so it's only a matter of time before someone tries to access it.

When you think of nail polish, it's probably almost always in the context of a manicure. I mean, that's what it's made for, right? But there are plenty of other things you can use clear or colored nail polish for besides painting your nails.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.
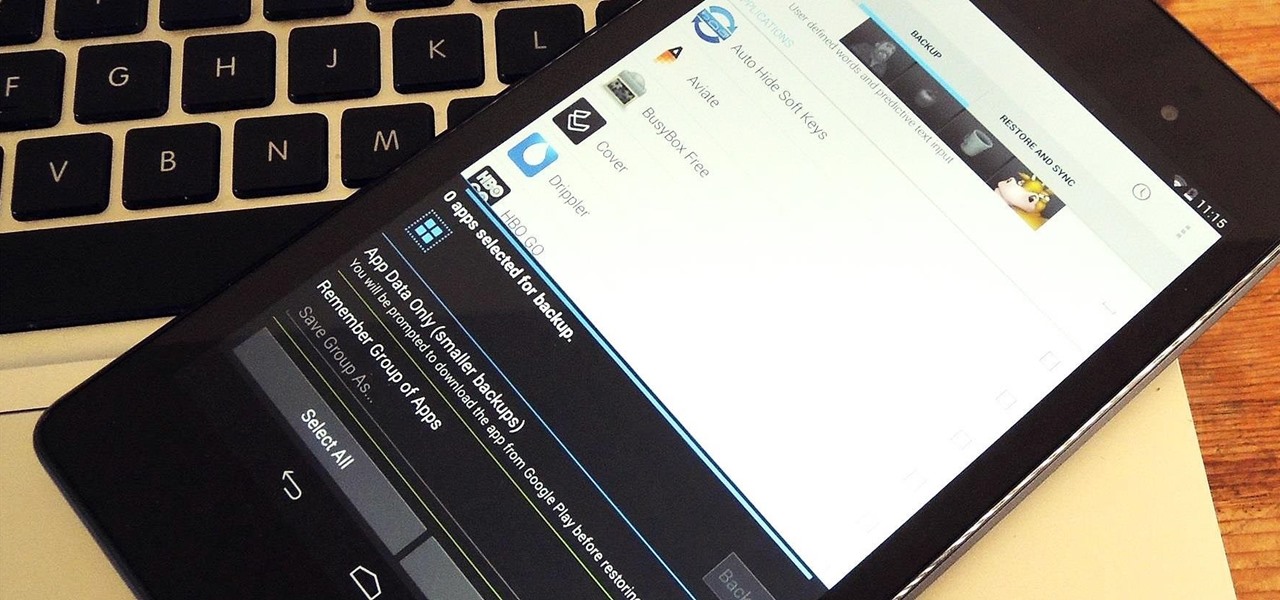
At some point, we all need to back up our device. Maybe it's time to take it in for repairs or maybe you're just cautious and paranoid. Maybe you're trying out a new ROM on your Nexus 7—then you definitely need to back up. The most secure way would be to use a custom recovery like ClockworkMod or TWRP, but if you're not rooted or planning to root, then you'll need an easy alternative.

Video: . Today I bring you my first Christmas themed video!Here there are some DIY ideas to decorate your room for the holiday season. They are really easy and affordable so I hope you like them!

This is about how to make a rabbit become less wary of you and more trustful with you also. I myself have a Dutch that was released by its previous owner, then I rescued it. She never wants to be took out of her cage, but now she doesn't mind as long as I'm gentle and nice.

Most hardcore Android fans loathe carrier or manufacturer additions to the Android operating system. Whether it's bloatware or changes to the user interface, many enthusiasts prefer the clean look of stock Android.

Walking into a bar or crowded dinner party can be intimidating. Being surrounded by a bunch of people you're unfamiliar with or trying to impress the smokeshow at the bar is no easy task...for most of us.

If you've had the pleasure of owning both an iOS and Android device, you may have noticed one subtle difference on each one's PIN unlock screen. Android's lock screen requires you to press "OK" after entering the PIN, whereas iOS's simply unlocks the screen right after the last digit.

Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

Nearly two years ago, Peter Chou, CEO of HTC, confirmed that the company would no longer be locking bootloaders. Whether or not they've actually lived up to this claim is debatable. Any phone bought from a wireless carrier comes locked. Only the new HTC One Developer Edition ships with an unlocked bootloader, and it does not have any carrier add-on software installed.

A single movie download can consume a good ten percent of the storage on your Nexus 7 tablet, unless you went all crazy and opted for the 32GB model. Even then you're bound to run out of space fast, especially if you're like me and have tons of media files you want readily accessible on your tablet.

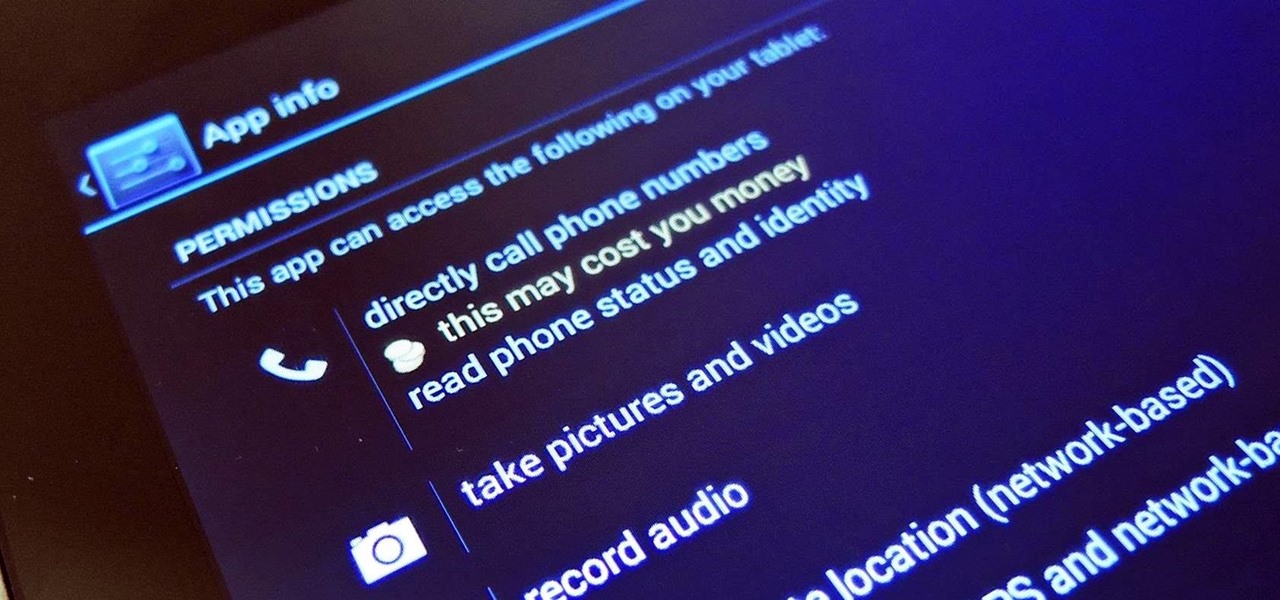
We go to such great lengths to secure our smartphones. We put passwords on our lock screens, encrypt our data, and install anti-theft programs, but it's never enough—someone, somewhere, will find a way around any protective measure you use, no matter how sophisticated.

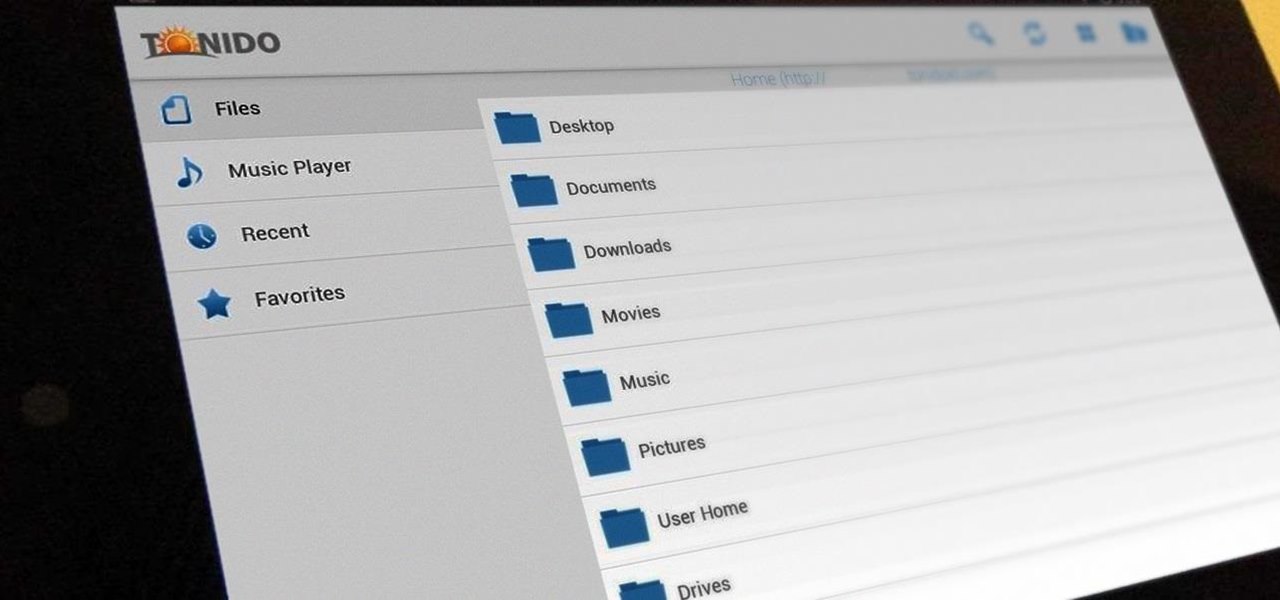
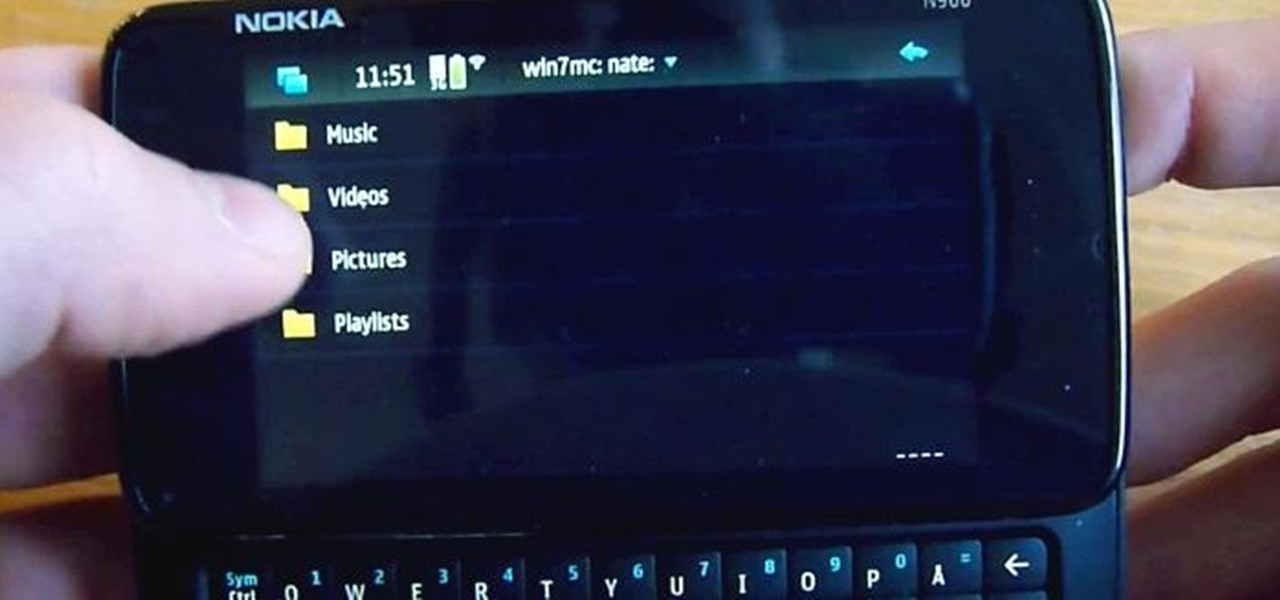
Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

It can be extremely frustrating when you've forgotten the pattern you use to lock your smartphone, and even more so if someone has managed to prank you by changing it. Luckily, there's an easy fix if you know the username and password for the Gmail account you used to set up the lock.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

It can be incredibly frustrating to take closeup shots with an iPhone camera—or any smartphone camera for that matter. Even if your phone's camera is top of the line, you'll still get a fuzzy picture if you get to close to your subject.

There's been a lot in the news lately about tracking devices, and it's been pretty much all bad. They can be useful if your car gets stolen, but if you weren't the person who installed it, chances are you don't want it there. Just type "GPS tracking device" into Google and on any given day you'll find an article about someone who got busted by one of these things. Even if you don't have to worry about getting into trouble, you still don't want people following you. Here's how to make sure you...

Did you know that there's a way to start a fire by squishing air? In this project, I'll show you how to build a tool that does exactly that—and I'll give you a sneak peak into the principals of how a diesel engine operates!

Everyone has a junk drawer in their kitchen. It's like an unspoken rule. The junk drawer is full of all the strange bits of what not that accumulates in your home over time. Everything in there is useful, and you never want to throw any of it away for fear that you might need something in there one rainy day.

This video teaches the secrets of making a floral bow or tying a ribbon in simple steps. First take a piece of ribbon, make a loop, twist and hold it. Now make a loop to the side, twist and hold and make another loop to its opposite side. Now make two more loops in the same way and hold it tightly. Secure the loops made in the ribbon by using a wire. Finally pull out the loops to make a floral pattern and finish.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

In this video you will learn how to change out the hard drive to get even more storage capacity from your Sony Playstation 3. The PS3 takes any 2.5 serial ATA hard drive, which is your basic laptop computer hard drive. To switch this out begin by looking at the base of your PS3, here you will see a cover with the label "detach this cover to remove hard drive". Remove this cover with a flat head screwdriver to reveal the hard drive. You will see 3 screws on the hard drive, use a Philips head s...

The warmth of a fire is great while camping or on a cold winter’s night but it can be difficult to get those log roaring. Use materials you have at home to create some easy, fool-proof fire starters that you can use the next time you need to get some logs burning.

Here is a fun afternoon project that will add a little fare to your dogs wardrobe. Instead of buying your next dog collar, try making one out of an old belt. Some say dogs look like their owners and now they can dress like them too.

Love the beauty and fresh fruit of trees but have limited space? Try your hand at dwarfing a tree. You can enjoy all the benefits of a tree without any worry of the tree outgrowing the area or roots damaging side walks and property. Plus, they just look adorable.

Dawn your flannel and grow out your beard, it’s time to do some log cutting. Put good use to unwanted trees or extra lumber by making proper logs. It may seem self explanatory but the correct form will create uniform, crack free logs and keep you with all your fingers.

Show up the other kids at school and bring your teacher a super-sized apple, well, paper-bag apple that is. Great project to do with the family or in the classroom. Create a festive apple using just paper-bag and some newspaper.

A bouquet of fresh roses is wonderful but real roses soon fade and die. Make a rose that will last forever, or at least a lot longer that a freshly cut one. Give your rose to someone special or use it as a decoration.

In this video demonstration you will see the work done on a GM 3.1 Liter V6; your instructor is replacing the cam cover seal. First raise the car into the air, remove the tire wheel assembly and place a jack stand underneath the car or vehicle on the side where you have removed the tire wheel assembly. Now remove the serpentine belt from the engine by using a 3/8ths breaker bar. Place it on the tensioner and lift up while removing the belt from the alternator. Keep lifting the belt out from t...

Vacuum the floor and make sure that the surface is clean and free from anything sticking up out of the floor. This is important so that there are no uneven areas when you start laying the laminate flooring.