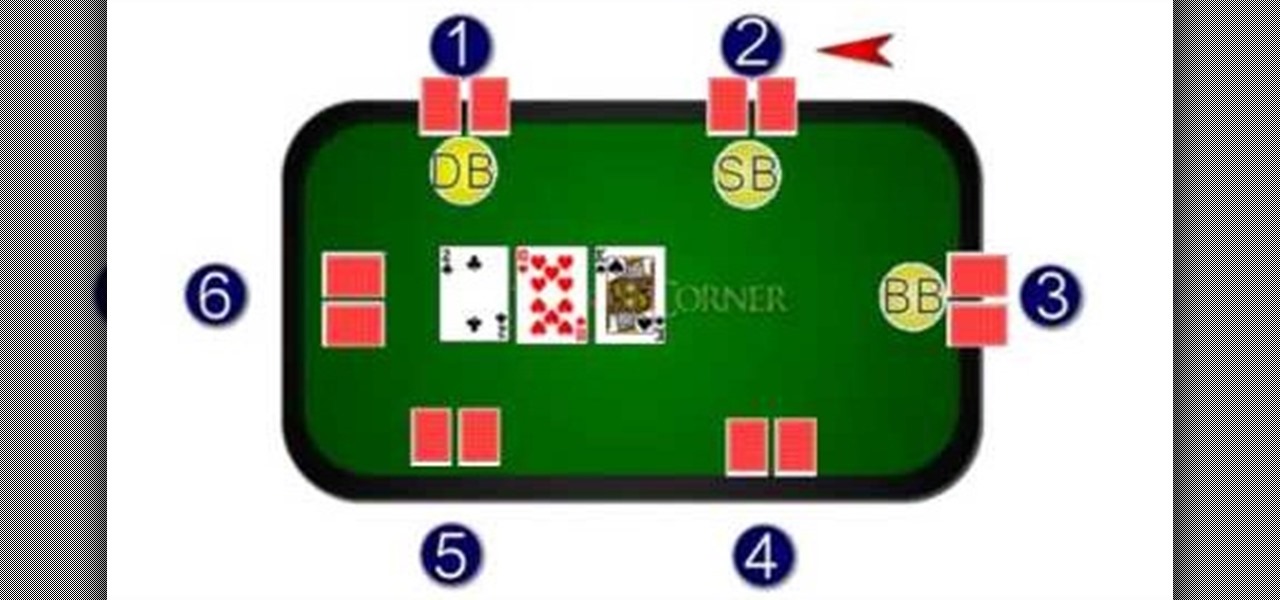
This video is sponsored by My Poker Corner and introduces the novice into how the game "Texas Hold 'em" is played. The complete process of the game from the number of players and their positions such as the Dealer are explained. The Small Blind position and the Big Blind position in the game are forced to place blind bets before they view their cards. Different betting rounds of the game such as "The Flop," "The Turn" and "The River" are explained and how the betting works and the option the ...

One of the best ways to learn the Hebrew alphabet is to use the alphabet song. But this twist on the song incorporates "Twinkle, Twinkle Little Star" in order to better remember the alphabet. "Twinkle, Twinkle Little Star" is the song that most English speakers learn their alphabet to, so why wouldn't it work with the Hebrew "Aleph-Bet"? The Aleph Bet has 22 letters which are all consonants. Get more details here. There are actually three videos here, the first is slow. The second if medium s...

Learn a bar bet trick in which the bet is that you can pull a bill from between two bottles balanced on top of one another.

This video will show you how to perform a great bar trick/puzzle/proposition bet called the "Three Knife Scaffold". This trick is super easy, it just takes a bit of know-how. In this tutorial, learn how to place your knives in order to fool your friends and win any bets they might make.
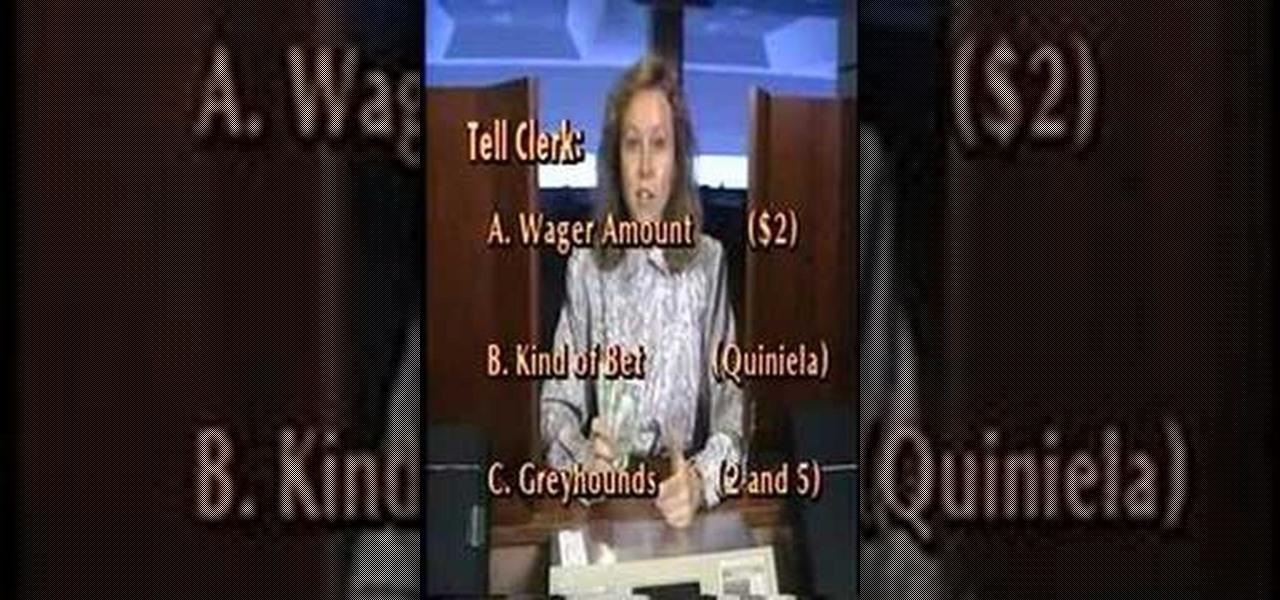
Learn different ways to bet at the greyhound racetrack.

In this two part video, learn how to build a scaffold or a bridge between two glasses that is strong enough to support another glass on top of it.

Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to secure your Gmail account.

Short on cash? Why not trick someone into buying you a free drink if they can't do everything you do. Learn the simple trick to this mirror bet. Watch this video magic tutorial and find out how to do the mirror bet bar trick.

Learn what to play before the first round of betting. Understand how to bet, when to bet, and in what increments to better your position and your hand.

Suckers bets are the easiest way to makes some money. You only need to be able to do something that seems impossible, but is exactly the opposite.

You're about to learn some incredible close-up magic tricks from Close Up Card Tricks that you can perform right away. You don't have to be a professional magician to do these card tricks, and you don't even have to practice them that much!

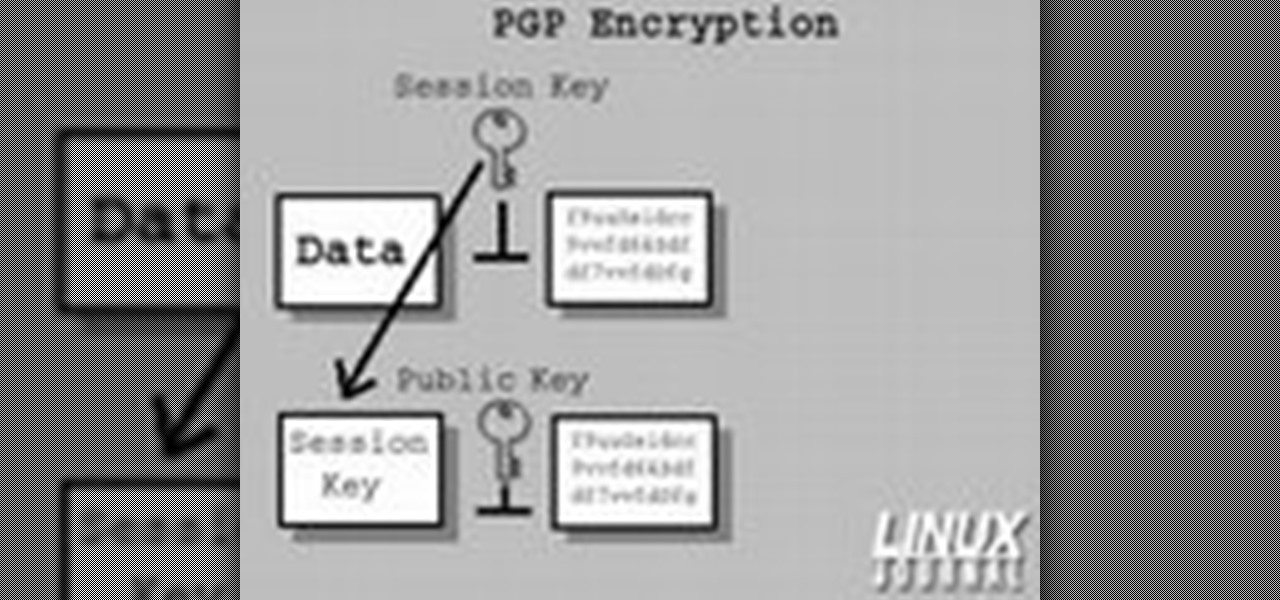
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

In this trick, bet someone that they can't transfer two corks between their hands and separate them without getting stuck. Unless you know the trick, you won't be able to do this. Check out this tutorial and let Scuba show you exactly how to do this funky illusion and win many bets.

If you are looking to win an easy bar bet, check out this video. In it, you will learn how to link two paperclips together using magic and without ever touching the clips!

Ever try your hand at betting on the ponies? It's a hard sport to bet on if you're just starting, and you should know everything you need to before you start, or you're just going to be throwing your money away.

Make someone write something on a note without you watching. Bet that person you have a note in your pocket saying the exact same. Great for Bets. Win Beer.

Wanna know how to get a shot at any bar for just a dollar. Mr. Magicpants gives a wealth of barroom strategy. You gotta botch the first bet. Wager a $1 on a drink. Then lose the bet. The mark gets to drink it. Walk away and he's left paying the bill!

Great bar trick that can win you beers!! This bar trick is great for bets. It’s a funny little coin trick. Do this bar trick as a bet and win beers or use the bar trick to challenge friends. The Bar Trick is easy to learn and the bar trick is very good.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

The scenario: The Super Bowl. The stakes: Humiliation. The results: Incredibly satisfying. Learn how to plot the most humiliating sports bet ever. You will need someone to bet against, your team's jersey, face paint, coasters, a razor, a poker game, and an (optional) bikini wax.

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

In this tutorial, we learn how to simply learn Texas Hold'em. First, you will need a deck of cards dealt out to all the players. After this, the dealer will place cards out on the table, one will be upside down and the others will be face out. Now, it's up to the other players to bet or fold because their cards aren't good enough to win. The players will bet money down if they think their cards will win, then the dealer will place another card face down and another right side up. The last rou...

Looking to impress your gullible friends and win a bar bet? Check out this tutorial if you are!

While this bar trick may not be failsafe, depending on how well you hustle, it can work. You will need a hat, a drink, a straw, and the ability to charm your victims. Watch this video magic tutorial and learn how to win a bar trick bet.

Pour both salt and pepper onto a table, and bet that you can pick up the pepper without touching the salt. This is an easy bet to win, and all you need is a balloon. This can be performed as a magic trick as well. Learn how to manipulate static cling to pick up pepper by watching this video magic trick tutorial.

Learn how to perform this easy cheat in Blackjack, "pinching the bet."

Learn the betting structure of poker. This video is an excellent resource for beginner poker players.

Learn when to fold, check, and bet in Texas Hold'em. This video is an excellent resource for the beginner poker player.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

Cool bet with beer and vodka. Great trick to play on friends and earn money.

In this tutorial, we learn how to play Texas Hold'Em like a champ. First, you will get two face down cards. After this, there will be a round of betting, followed by the dealer putting down the flop. After this, there is another round of better. Then, the dealer will deal the next card called the turn. Another round of betting occurs, then there is a river dealt by the dealer. Now, you can bet or you can stop playing, depending on what cards you have. After this, if you have the better hand t...

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

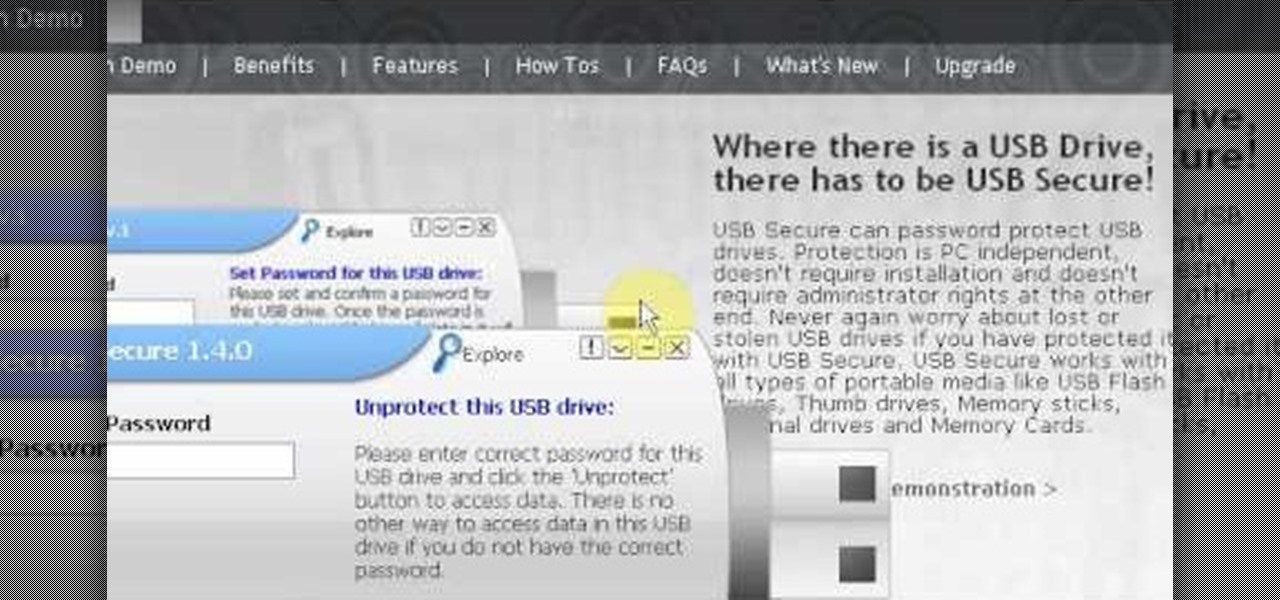
Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

Use three tools to create a simple ponytail. Use a hairbrush, a bobby pin, and a bungee band holder for this look. Using a bungee band instead of a standard ponytail holder eliminates some of the issues typically caused by pulling hair through ponytail holders. Start by using a bristled brush to brush the hair to one location on the head. Secure one hook of the bungee band in the ponytail and wrap the tail around the rest of the hair. Wrap it around again, and secure the other bungee band hoo...

Using ASP.NET Secure Services and Applications Services

Need to know how to tie a Bowline with a few ways of securing it? This way shows you how to secure it with a seizing so that it won't accidentally come undone. Included is a little variation of the bowline with a built-in seizing. If you don't have electrical tape to secure the bowline feed the bitter end back through the hole. It also makes it so you don't have a tail line dangling if you're towing something.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

In this clip, you'll learn how to get started using Secure Computing's Secure Web Protection proxy service. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

Don’t play Russian roulette when it comes to your wheels. Keep your bike secure with these precautions.

A formal occasion calls for a classic look. You Will Need