In this video, Karlyn M. Campbell, an Information Technology student, goes through how to set up and secure a wireless network on a laptop. For a wireless network you will need your computer, a wireless router and its CD, and a USB wire. First the video goes through how to set up the router by using its installation CD. This video uses a Belkin router, and so shows the steps the Belkin installation CD takes the user through. The CD also lets the user decide which security settings he or she w...

Watch this video for instructions on making the Yukki Cross Artemis scythe from the anime / manga Vampire Knight.

By using sewing pattern Simplicity 4670, the author of this tutorial video takes you through the steps needed to produce a great shirt collar. First you should attach interfacing to one piece of the shirt collar. Here you will be using fusible interfacing and taking the facing to the shirt collar iron the interfacing to the wrong side of the fabric. Sew a guide line that is 5/8ths of an inch wide along the notched edge of the shirt collar's facing piece. At the dot markings of the collar clip...

When is a knot not a knot? When it's a grip. The knot outlined in this video isn't a knot per se but a way to wrap objects to increase their grip and also to store extra paracord. Specifically, this video demonstrates how to County Comm Micro Widgy Bar, which is a miniature pry bar. It’s made from hardened D9 steel and is around 3? in overall length.

Three hundred people die every year from carbon monoxide poisoning. Don't risk being a part of that statistic.

Shaun Alexander was an amazingly productive NFL running back. In this video, he takes some time to explain for young running backs how to hold the ball properly, protecting it from the defense and potential fumbles. Proper finger positioning and placing the body between opponents and the ball are both crucial elements.

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is to connect to a remote MySQL database securely via SSH tunneling. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a secure connection between a given MySQL database and the DreamCoder for MySQL, take a look!

Babies have no way of communication other than crying. = Touch is one of a baby's most highly developed senses at birth. Holding, caressing and cuddling your infant is crucial to helping her feel safe and secure. There are a number of tips demonstrated in this instructional video to help calm a crying baby. Watch this video child care tutorial and learn how to comfort a baby.

This video demonstrates how to install or replace a dead bolt in your door. Having a dead bolt lock gives you a added sense of security, because it is more secure than just the lock on the door handle.

Botanically, tomatoes are fruits, but an 1893 Supreme Court decision changes that. They were ruled to be considered vegetables, allowing for a higher tax to be placed on imported tomatoes. Seems silly now. Tomatoes are rich in vitamins A, C, and K, as well as lycopene, a cancer-fighter. Enjoy tomatoes throughout the year by canning your summer harvest.

This video shows everything about how to put on a rented tuxedo. When you get your tux, the shoes will be hanging in a bag on the outside of the bag. Inside the bag will be the coat, shirt, vest or cummerbund, tie, pants and studs and links. Socks will be in the inside coat pocket, and the pocket square should be on the outside pocket of the coat. Remove the studs and links from the bag. Leave the collar button alone and start with the next button hole. Put the studs through the holea. Insert...

Here's how to make this Middle Eastern delicacy. You Will Need:

Learn how to make a bike repair stand with this video! Create the legs: 1. Two sets of 8 and 10 inch piece of steel pipe, a 90 degree angle, an end cap and a T pipe are the starting materials. About 0.5 inch diameter pipe is fine for the project.

If your old clothes are of high quality and in good shape, selling them on consignment is an easy way to make cash quickly.

If things are getting a bit stuffy at your desk, don’t fret. A cool breeze is just a USB slot away. Watch this video to learn how to make a USB fan.

Learn how to immobilize an ankle. The ankle is a complex joint, so when an injury occurs, and you can't get help right away, the first thing to do is keep it from moving – you'll prevent any more damage to the surrounding nerves and tissue.

Instead of pushing, pulling, and cursing, why not fix that door that sticks? You Will Need

Learn how to give your daughter a trim and you’ll save big bucks on trips to the hairdresser. Learn how to give a child a haircut, at home. This is a cost effective tip that will help you save money.

In this stage design and construction video series, learn how to build one of those small “portals.” Our expert—a director, actor, and producer himself—will show you tips and techniques for building a small, mobile stage that can be set up anywhere you or your acting troupe decide to give a performance. This step-by-step guide to stage construction includes clips on what tools and materials to use, how to measure and cut the frame, what type of bolts to use for ease of tear down, and how to b...

This is a tutorial showing you how to mod a ps2 slim. This will allow you to play backups as well as Guitar Hero 2 customs. If you want to learn how to make your own copy I might put up a video for that. This tutorial also shows the swap trick in action.

The recent announcement that Facebook will begin inserting advertisements into its VR experience on its Oculus Quest headset has set the VR and augmented reality industry into a frenzy.

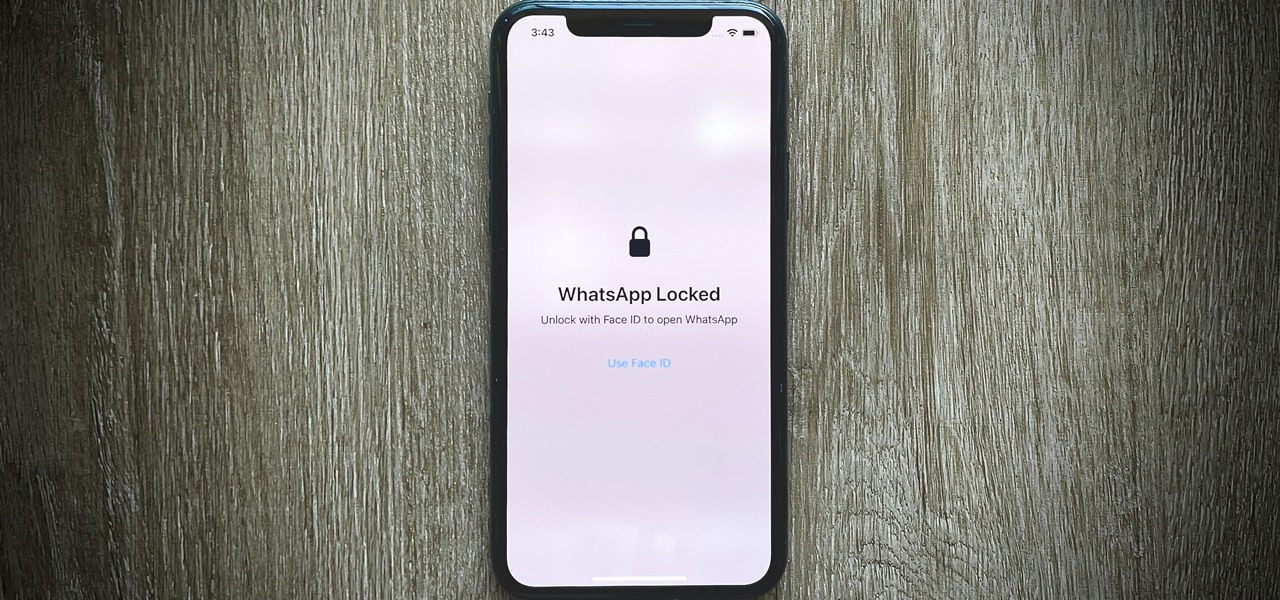
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

With millions of people working from home as a result of the coronavirus outbreak, hacking is on the rise. Nefarious black hats are taking advantage of the fact that workers have been forced to abandon their secure office networks in favor of home wireless connections. And white hats are spending even more time at home trying to be the next great ethical hacker.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

One of the masters of science fiction, Neal Stephenson, may be on staff at Magic Leap, but that doesn't mean he can't take a moment to visit the halls of competitor Microsoft, the maker of the HoloLens.

Lions and tigers and bears are just a few of the animals that Google users can now bring into their physical environments.

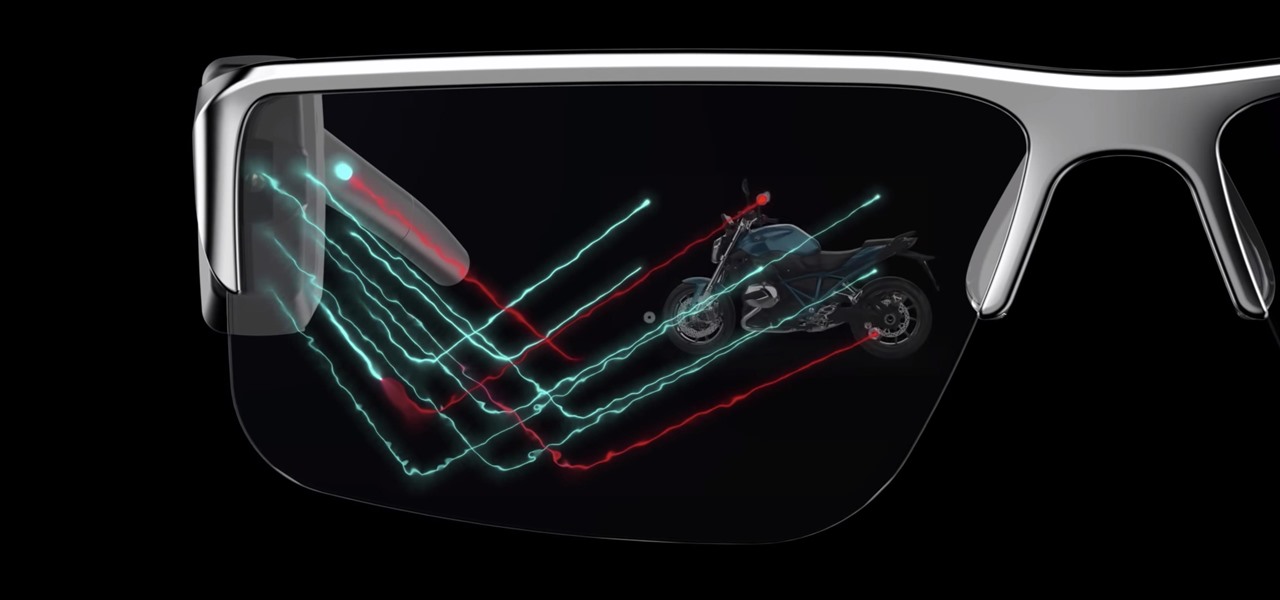
Smartglasses are the future of augmented reality, and Samsung is betting on waveguide maker DigiLens to emerge as a leader in the growing AR wearable industry.

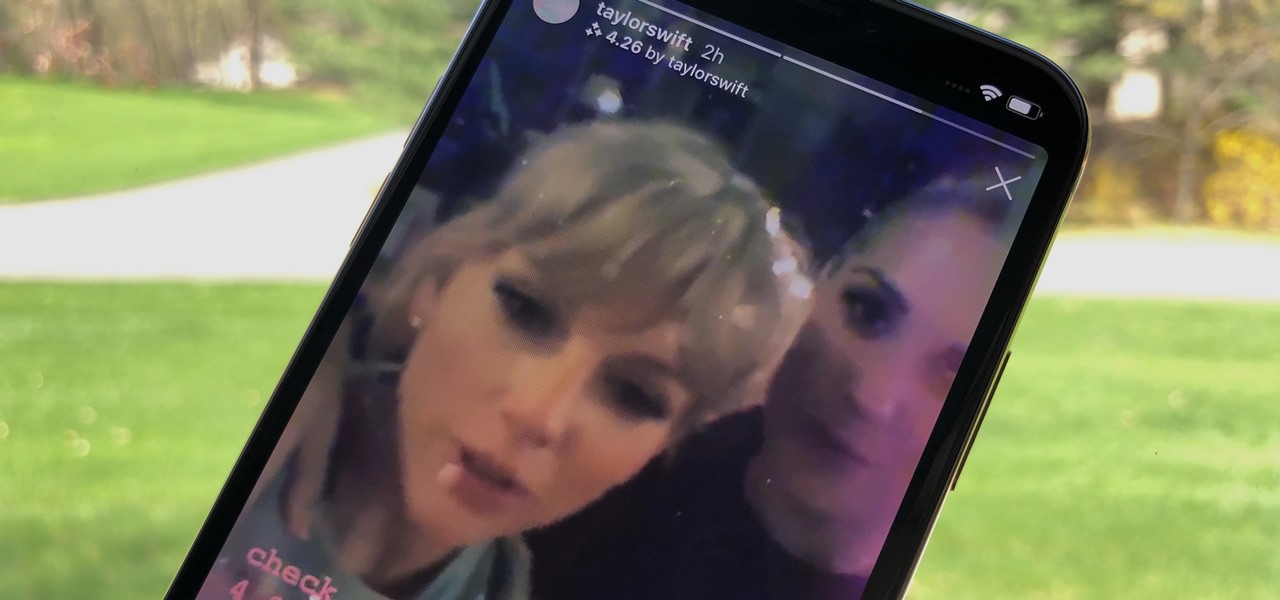
Is there a bigger name in pop music than Taylor Swift right now? Her 116 million followers on Instagram would probably argue, "No." As such, if you're one of these many followers, you might have seen Taylor advertising a new "4.26" filter on her story. Problem is, there's no clear instruction for actually using the filter. That's where we come in.

As one of the leading 3D engines for augmented reality development, a new release of Unity is a significant event that carries the potential to facilitate huge leaps forward in AR content creation.

A week after reducing the base price of its Focals smartglasses by nearly 50 percent, wearables maker North is now reducing its workforce.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

The fortunes of ARKit and ARCore are still in the hands of developers, who have been increasing the number of mobile augmented reality apps on the market, but perhaps not as fast as companies like Apple might have expected. But one new product is looking to literally kickstart mobile AR gaming by introducing a few key components that harness the traditional board game model.

For the first time since its inception, the famously hidden System UI Tuner has to be unlocked in a new way. No longer can you long-press the gear icon (found in Quick Settings) until it spins and reveals the hidden settings option. With Android 9.0 Pie, there's a new workaround to reveal the menu.

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

Google's AI investment arm, Gradient Ventures, has joined a $10.5 million round of funding for Ubiquity6 and its platform for shared augmented reality experiences, just weeks after Google's GV fund backed a competing AR cloud platform.

With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.

Augmented reality software maker 8th Wall has closed a Series A funding round of $8 million in capital to feed the growth of its development platform.

Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

In the wake of reports of slow iPhone X sales and a possible early end to its shelf life, Apple CEO Tim Cook is on a public goodwill tour of sorts, espousing the virtues of Apple AR.