Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

The augmented reality industry has a bright future built on innovation and growth, but that doesn't mean we can't look back at the close of the year to see what the industry has accomplished from a business perspective.

The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. That's why we set out to find the very best tweaks for OnePlus phones, and to make it easier for you to apply them.

With would-be unicorns Magic Leap and Niantic among its investments, Google is an active investor in augmented reality technology. This week, the search giant experienced both ends of the investment cycle, with an exit via Lyft's acquisition of Blue Vision Labs, and a funding round for Resolution Games.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Apple's Mail app for iOS isn't a bad email client by any means. However, it just doesn't cut it for iPhone users that want a more intelligent and advanced email solution. If you're in the market for an app like that, Spark is absolutely your best bet.

No matter what your holiday preference, you're probably aware that Christmas is now just days away. By now, you've already decked your halls with boughs of holly (either physically or virtually), thanks to our last holiday app roundup.

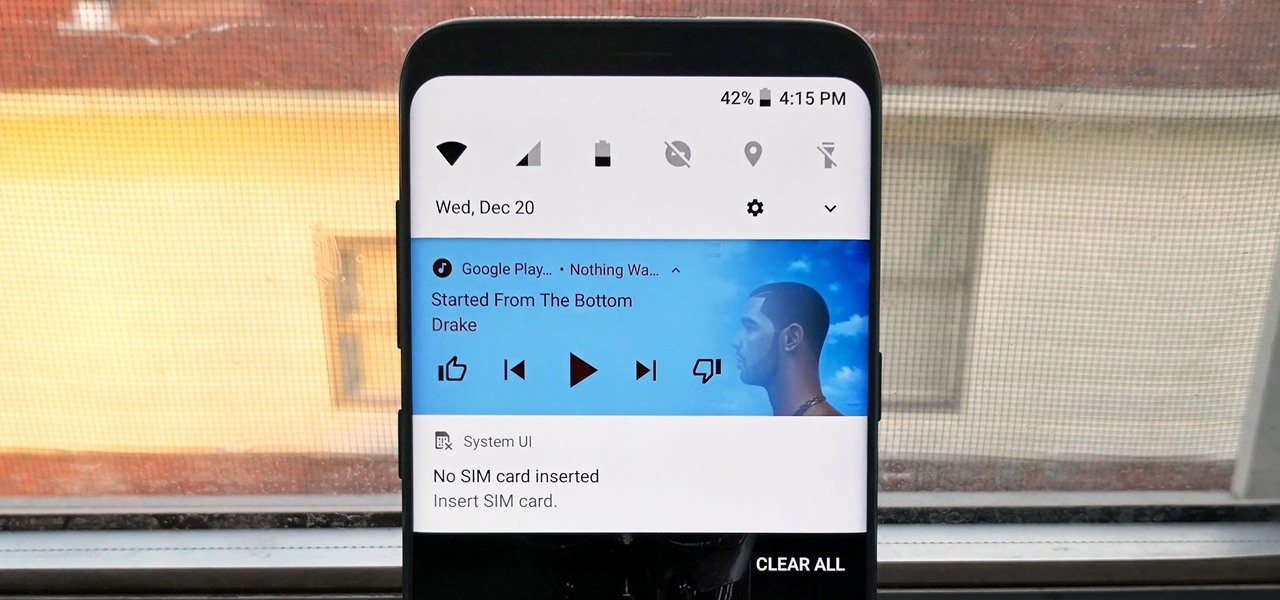
One of the biggest gripes we always hear about is the changes OEMs make to Android's notification shade. Icon styling and home screen layouts can be fixed with custom launchers like Nova and Action, but we're stuck with the tacky Quick Settings theme our phones came with. Today, we no longer have to envy Pixel 2 owners, as a new app will give you that clean stock Android look on any phone.

As the first Animal Crossing game on mobile devices, it's clear that Nintendo had a more social experience in mind for Pocket Camp, and I'm not talking about all the animal friends you can make. You can add other players to your list of human friends, and they're incredibly useful for a wide array of tasks.

Whenever you attend or remotely watch a major Apple event, you're likely to see Phil Schiller, the company's senior vice president of worldwide marketing, unveiling a brand new product on stage. Outside of an official event, Schiller is the second most likely person (after Apple's CEO Tim Cook) you'll find delivering a rare tidbit of new Apple info or perspective to the public.

Augmented reality was recently named the "Mobile Disruptor of the Year" for 2017 by Mobile Marketer, but the technology is showing no signs of slowing down as we head into 2018. In fact, the technology appears to be gaining momentum.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

When Apple announced their ARKit platform in June, they immediately staked the claim to the largest augmented reality hardware platform, with millions of iPhones and iPads compatible with iOS 11 becoming AR devices this fall.

It's not always easy to get to the root of an infection outbreak. Epidemiologists study infected people, contacts, and carefully examine where the infections happened and when. In the case of a 2012 outbreak of pertussis — whooping cough — in Oregon, scientists just published an analysis of how vaccination status affected when a child became infected during the outbreak.

Ford's appointment of Jim Hackett as its new president and CEO reflects how the company is largely pinning its long-term survival hopes on its driverless business. Following his previous role as head of Ford's Smart Mobility division, which overseas Ford's autonomous driving activity, Hackett will help the company take a more self-driving direction as a whole.

Drug-resistant bacteria have made curing some infections challenging, if not nearly impossible. By 2050, it's estimated that 10 million people will be dying annually from infections with antibiotic-resistant organisms.

The noses of kids who live in areas of intense pig farming may harbor antibiotic-resistant bacteria, presumably acquired from the animals, according to a new study by scientists at the Johns Hopkins Bloomberg School of Public Health, UNC Gillings School of Global Public Health, and Statens Serum Institut in Denmark, published in Environmental Health Perspectives.

Every Tuesday, Next Reality will give readers a rundown of the augmented and mixed reality news briefs from the preceding week that we didn't cover already. This way, you'll never miss anything of importance in the Next Reality landscape, and will always know what's going on with new augmented and mixed reality tech and applications.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

Where in the world did it come from? All of a sudden, one day, someone had an infection with flesh-eating bacteria. It captured headlines and worldwide attention because it was such a severe, strange, uncontrollable, and really disgusting condition.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

This is a whole new level of "Paleo," guys. Seriously: there's nothing more primal than a giant hunk of meat cooked in direct flame. Fancy grills and grill masters be damned—this method of cooking your meat is both the past and the future.

Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

If you love quenching your thirst with an ice-cold glass of lemonade but aren't a fan of artificial powder mixes, then this hack is for you. When your next lemonade craving strikes, instead of reaching for a glorified Kool-Aid packet, get an instant sip of summer by using pre-made, frozen lemon cubes to create your favorite drink. And this recipe isn't just easy to make, it's perfect for any number of servings, from single to several, or even a pitcher, if necessary.

A cup of ginger tea with lemon first thing in the morning, a pick-me-up cup of green tea (or matcha) to fight off the afternoon slump and a soothing cup of chamomile tea to help me unwind before bed—I would be lying if I said I weren't a major tea enthusiast.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

I was bored when I found this piece of literature: ==Phrack Inc.==

One of my favorite things about cocktails is that they're so diverse. They can be sweet or savory, filling or refreshing. And they can take advantage of nearly any ingredient imaginable, including egg whites, smoked ice, flavor cubes, and even beer.

Practically every smartphone comes with a built-in camera app, but these apps are generally created by the device's manufacturer. And let's face it, manufacturers are hardware companies first and foremost, so they don't always produce the best software.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.