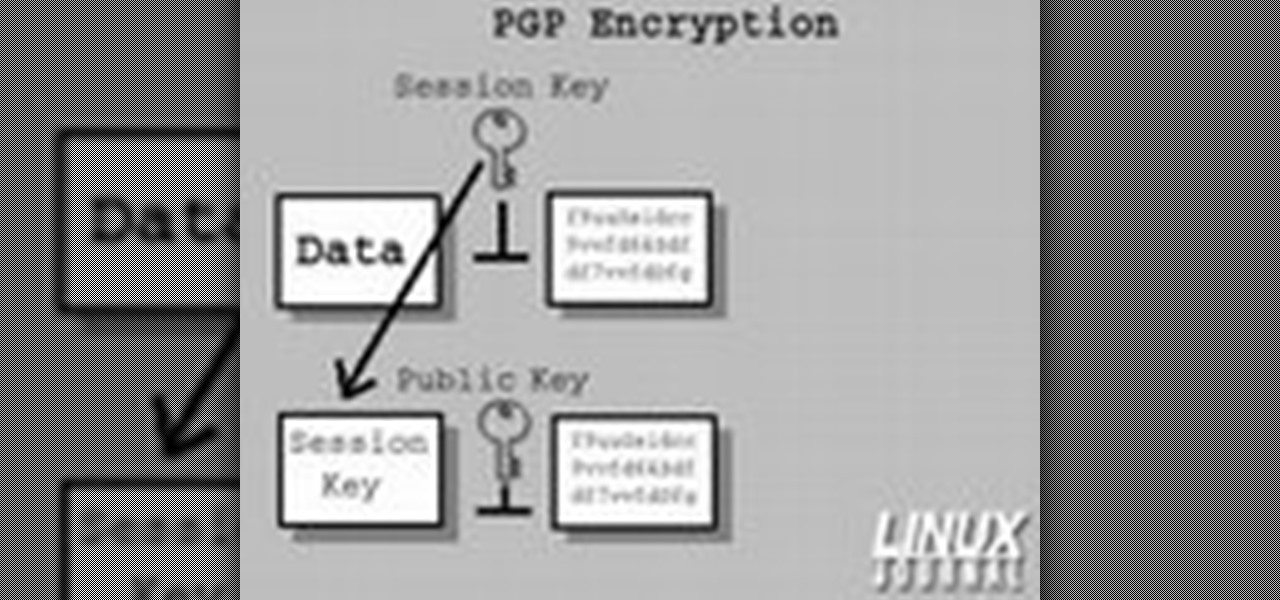
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

TrueCrypt is a free application that lets you encrypt designated programs on your Ubuntu system to prevent unwanted access. Provided you select a strong password, intruders will not be able to open your personal files and documents. This instructional video walks you through the process of installing TrueCrypt on your Ubuntu operated machine and demonstrates an example on how to create an encrypted volume within a select partition.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to secure your Gmail account.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

Celebrites make party hopping look so easy. Flitting around from red carpet event to after party to after after party, they always seem to look so flawless in their pictures. But here's a little secret: They have some help from Hollywood's top hairstylists.

The trucker's hitch is a good, strong knot with many uses. It's ideal for securing a load in a vehicle, and was used that way dating back to the days of wagons hauled by horses. In this video the folks at ITS Tactical teach you how to tie a trucker's hitch, quick and easy.

Things a little quiet on the online dating front? Need some online dating advice from the experts? Maybe you're looking for love with all the wrong adverbs and dating SEO. SEO is short for search engine optimization. Take a little time to soup up your profile and those dates will start a'rolling in with this how to dating video.

Asking someone out on a date can be very intimidating, especially if you do not know them that well or if they are a complete stranger. This guide helps you learn how to confidently ask a stranger out on a date by introducing yourself, finding common ground, learning about the stranger, and then asking them out. Sometime's asking someone out is as easy as initiating a conversation.

You’ve had a great date and now it’s time to say good night; why don’t you seal it with a kiss? You Will Need

Having a date over to your place for the first time is nerve-racking enough without having to worry about your embarrassing roommate. With these easy steps, an uncomfortable situation can be smoothed over. Watch this dating advice video and learn how to bring home a date when you have a roommate.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

After a divorce, it may seem easy to keep your female hunting on the down low and avoid awkwardness by simply registering on sites like eHarmony.com and "dating" people online. But the experience of a first date is one hell we must all go through in our lives.

Have a date and looking to impress? First dates can be nerve racking and totally awkward. Watch this video on how to impress a man on the first date and stay calm.

Check out this how-to video that shows you how to avoid the anxiety of asking out or being asked out so you can enjoy success from smart dating every time. If you have dating anxiety, this is the tutorial to consult! There's no reason to be scared or anxious about dating if you get tips from these two.

Depending on your juggling skills, it can be a dream come true or your worst nightmare. Watch this how-to dating video and learn how to date several women at once. To carry out this delicate project you will need more than one woman, organizational skills, and a silver tongue. Caution dating several women at once can have disastrous consequences.

Dying to try online dating, but worried that the guy that you're digitally winking at is really a cyber stalker? Then watch this Dating Advice how-to video to learn how to date and decode online dating profiles. With this online dating translator you are sure to keep all the cyber stalkers out of the running.

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

This video on typhoon preparedness comes from Andersen Air Force Base in Guam, where typhoons are common. The key to surviving a typhoon or other disaster is preparation. Stock up on enough food and supplies to last your family for about a week. Routinely check expiration dates on food, water and batteries and rotate your stock. Be sure window screens are in place and in good condition in the event the power is off for several days.

This video has a man by the name of Dr. Neder and he has a book by the name, ‘how to be a man in a woman’s world.’ He answers a series of questions. The first question asked is how to get a girl with a boyfriend. The answer this video provides is simply that all girls are looking to date up. Meaning your value and assets, if there is a greater attraction then the girl will end up with you and dump the guy that she is with. Does size matter? The average size of most man is five inches to five ...

In this clip, you'll learn how to get started using Secure Computing's Secure Web Protection proxy service. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

Vanae presents a video about dating a woman who is already married. Monologue to a question presented by a subscriber to her video blog. In her opinion it is not wise or acceptable to date someone who is married or dating already. Reasons to not date a married person and different potential things about what could happen including the block on having a full relationship, the potential karma, and a few other aspects of what this could mean to you.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

In this tutorial I am going to show you how to change some file metadata, this could be very useful if you want to edit or access a file and remove any evidence of your changes.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

Use three tools to create a simple ponytail. Use a hairbrush, a bobby pin, and a bungee band holder for this look. Using a bungee band instead of a standard ponytail holder eliminates some of the issues typically caused by pulling hair through ponytail holders. Start by using a bristled brush to brush the hair to one location on the head. Secure one hook of the bungee band in the ponytail and wrap the tail around the rest of the hair. Wrap it around again, and secure the other bungee band hoo...

Using ASP.NET Secure Services and Applications Services

Need to know how to tie a Bowline with a few ways of securing it? This way shows you how to secure it with a seizing so that it won't accidentally come undone. Included is a little variation of the bowline with a built-in seizing. If you don't have electrical tape to secure the bowline feed the bitter end back through the hole. It also makes it so you don't have a tail line dangling if you're towing something.

Buns and updos are gorgeous hairstyles, with one caveat: If they're not pinned perfectly and securely in place, all your hard work braiding and curling will go to waste as your hair slowly unravels.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

In this video from JenniferCornbleet we learn to make raw food granola with almond milk. Place a nut or seed in a mason jar about halfway. Fill the rest with water. Sit over night. Drain, and you can use right away or store in your refrigerator for up to 3 days. Almond milk is a great cereal milk replacement. To make it combine almonds, water, and a couple of dates to sweeten the milk. You can use a different sweetener of your choice. You can flavor with vanilla extract as well. Blend in a bl...

So, you asked out the girl you like and now you're about to hemmorage because you have no idea how to talk to her on a date. No sweat. The Wing Girls are here to help. In this video, learn how to go about getting a comfortable, flowing and interesting conversation started with a girl on a date.

Once you know what makes a Leo tick, it will be easy to get under his or her skin. Learn how to use astrology advice in dating, by watching this how-to dating video. Pick up tips on making a relationship with a Leo work. Leo's have a healthy self image, so when you date a Leo make sure to admire them.

It is senior year and prom season is approaching, but you don't have a date yet. Then its time to ask someone to the prom ASAP. Don’t freak out. Just watch this how-to dating video and follow these simple steps. Before you know it you'll have a date to prom.

Apple's once flawless mobile operating system has seen its fair share of bugs recently. From Messages and Wi-Fi settings crashing to having your photos and contacts exposed, iOS has been standing on shaky ground for a while now.

For some reason these days, it seems like all the young people want to date old people and vice versa. If you find yourself on the young side of that equation, watch this video for some novel tips on convincing your parents to let you date an older man or woman.