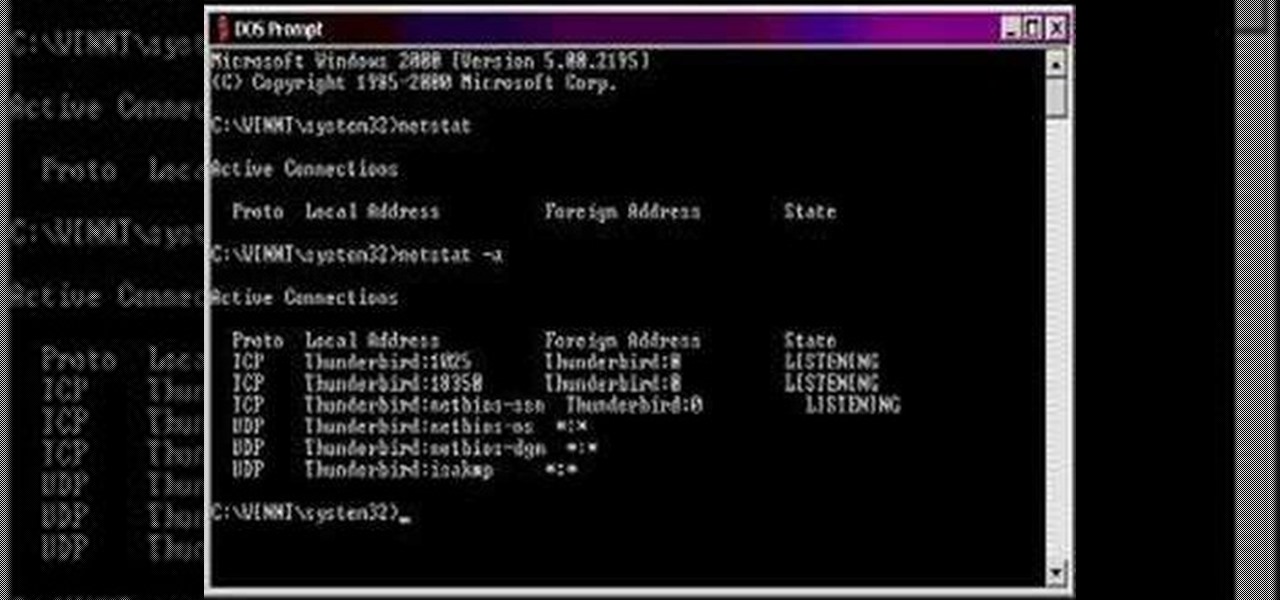
In this how to video, you will learn how to keep your Windows operating system secure by look for and closing open ports. First, you will need to run the program called Net State. Once this is open, type in netstat -a. This will list main connections. Next, type in netstat -an. This will give you the numbers of ports that are open. Some may be used for file sharing and anti-virus programs. If you want it completely secured, you should only have one running. This video shows you how easy it is...

Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 257th installment in their series of digital spreadsheet magic tricks, you'll learn how to text dates to number dates suitable for use in pivot tables (PivotTables).

How to build a high tunnel to protect your plants
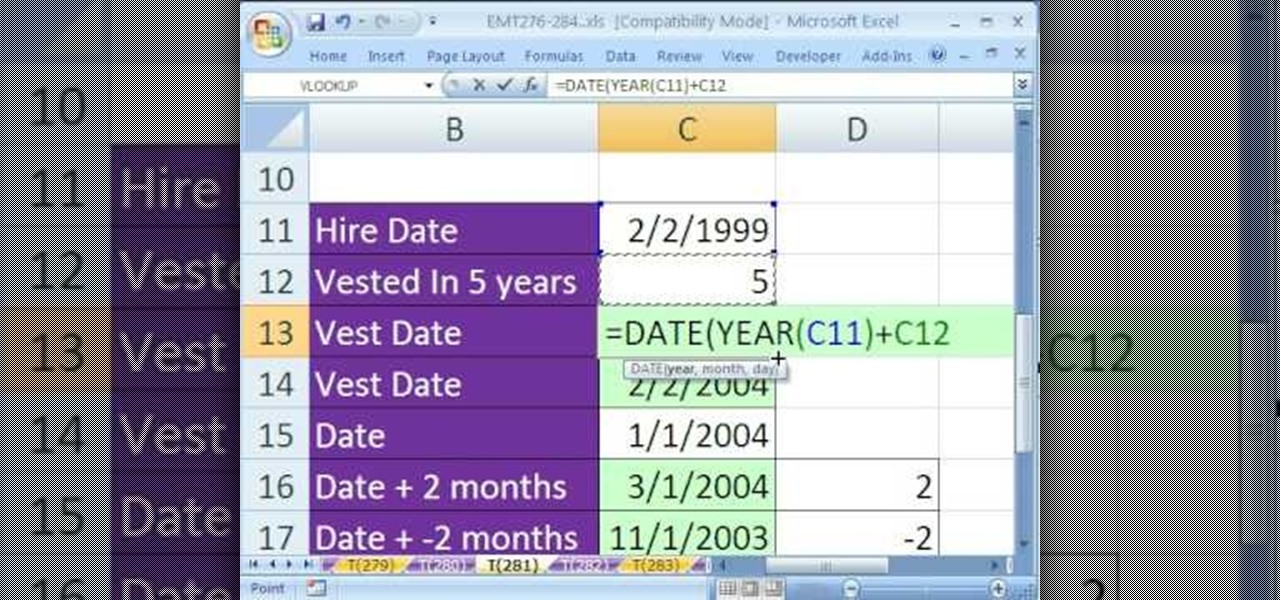
New to Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 269th installment in their series of digital spreadsheet magic tricks, you'll learn how to

This is a video using Swarovski Crystals to make jewelry. This video shows how to make one with a gold bow. You need a pendant with 2 hoops (in this case it is a gold bow), a pendant holder, a crystal, a bill, and pliers. You take the bill and hook the crystal on it. Then you hook the bow on it and secure it using the pliers. You take the pendant holder onto the top of the bow pendant, and press it down to secure it, and you’re finished. You can also make rings, earrings, necklaces, and many ...

This video shows the viewer how to secure crimp beads using both crimping pliers and chain-nose pliers for the purpose of jewelry making. The video uses two millimeter crimp beads, beading wire, and both sets of pliers to demonstrate the technique. To crimp using the crimping pliers, the viewer will utilize both notches of the pliers to crimp the bead onto the wire. In order to crimp using the chain-nose pliers, one must simply flatten the bead onto the wire. Crimping is a good method to secu...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. It's like having a safe built right into your smartphone, and it couldn't be easier to set up.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

If there is anyone who can help you get closer to finding your true love it is Dr. Diana Kirschner. Dr. Kirschner is a love expert, media psychologist and bestselling author. She is the go to psychologist on most talk and reality TV shows and for newspapers and magazines in need of a relationship expert.

Have you met a guy you really like and you want to see him again? Make sure you check out this video, and avoid common mistakes that girls make when they meet guys.

Ramses and Tara from Skills of the Game explain why creating an attention-getting headline is important in online dating, especially on dating sites that emphasize a headline rather than a thumbnail picture. They explain how and why a poor headline can diminish a person’s standing. They give examples of bad headlines, and suggest writing headlines that are either lighthearted or call the reader to action. After giving a few examples of good profile headlines, Tara explains why the most import...

In this video you will learn how to insert the current time and date in MS Word 2007. In order to do that, just follow these easy and quick steps and instructions. The first thing you need to do is to click the Insert tab. Now, you need to select a space where your date and time will be placed. The next step is to click the Date & Time button, and select the format that you want. Click the OK button, and you are done. If you followed the simple steps correctly, then you won't have any problem...

YourTango presents relationship expert Rachel Greenwald, who breaks down why he didn't call you back. She takes us through the process of learning why men do not call women back after first dates. Find out if you are the type of woman who is at risk of not getting a call back, and it begins with "the blahs", a woman who gives the one word answer to standard questions. Next, see if you suffer from iPod repeatability, the Oprah eyes, or how men call it the Park Avenue princess. If you follow th...

Nine out of ten people say they would refuse to date someone who is a bad kisser, while one out of five say they’d date someone unattractive if that person was a great kisser. So let’s get started. You will need a practice partner, fresh breath, and lots of moves. Tip: keep it wet, but not a wash out. Nobody likes to be slobbered on. For men, try holding her face in your hands as you kiss her - women love that!

Julia, AKA Hairbeauty4you, gives detailed instructions on how to do a quick half up-do with a twist in under 10 minutes. She notes that this style is best for medium to long length hair. Julia starts with straight hair, then sections off the top part and clips temporarily. She then separates another section on either side of the top part- from the ear to the clipped section- and pulls it back into a high pony tail and repeats identically on the other side, securing each with clear rubber band...

This video is provided by "Betty Sell" from AAA travels. In this video she tells about the international travel and also about the important documents to be carried while carrying out an international travel, that is the international driving permit, commonly called as an IDP. It's very important to carry an IDP while traveling overseas because an IDP acts as an important recognizable form of photo identification which helps us to communicate with foreign authorities. To get more information ...

Do you need to lock the door but don't have the keys? This may happen if you are sharing your keys with someone else, staying at a friend's house, or for a variety of other reasons. Check out this video for a sneaky way to secure that door tight without even sticking a key in the lock.

In this video, we learn how to know how often to talk to the girl you're dating. Make sure you aren't texting the girl too much, you want to talk during one point of the day so you have a lot to say. If you're checking in all the time, you are not having a real conversation. Don't rely on the internet to communicate with her because this is very interpersonal. Talk on the phone and in person so you can get a better feel for the person. If you skip a day, it's no big deal, just pick up on wher...

Everybody needs a little dating advice, especially the men… or boys! Alec Greven, the nine-year-old author of "How to Talk to Girls" shares some of his successful tips on talking to girls. And surprisingly enough, this dating information can be applied to all ages. Are you smart enough to take over a girl's heart? See how to talk to girls!

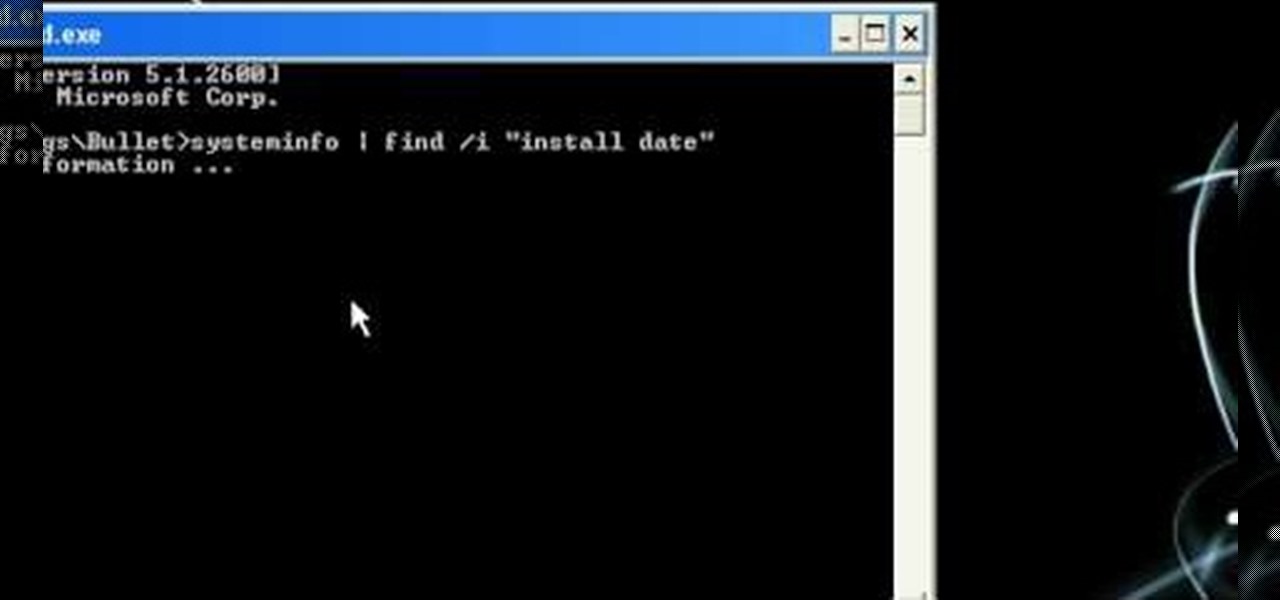
In this video from MegaByteTV we learn how to find your operating system's original install date and time. This is for XP Pro only. To find it, go to the Start menu, then click Run. Once there, type in cmd and click OK. A black box will come up showing that you are in cmd. Then paste the following into the cmd box: systeminfo | find /i "install date" The original install date will then come up on your screen along with the original install time as well on that date. This is a very simple proc...

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

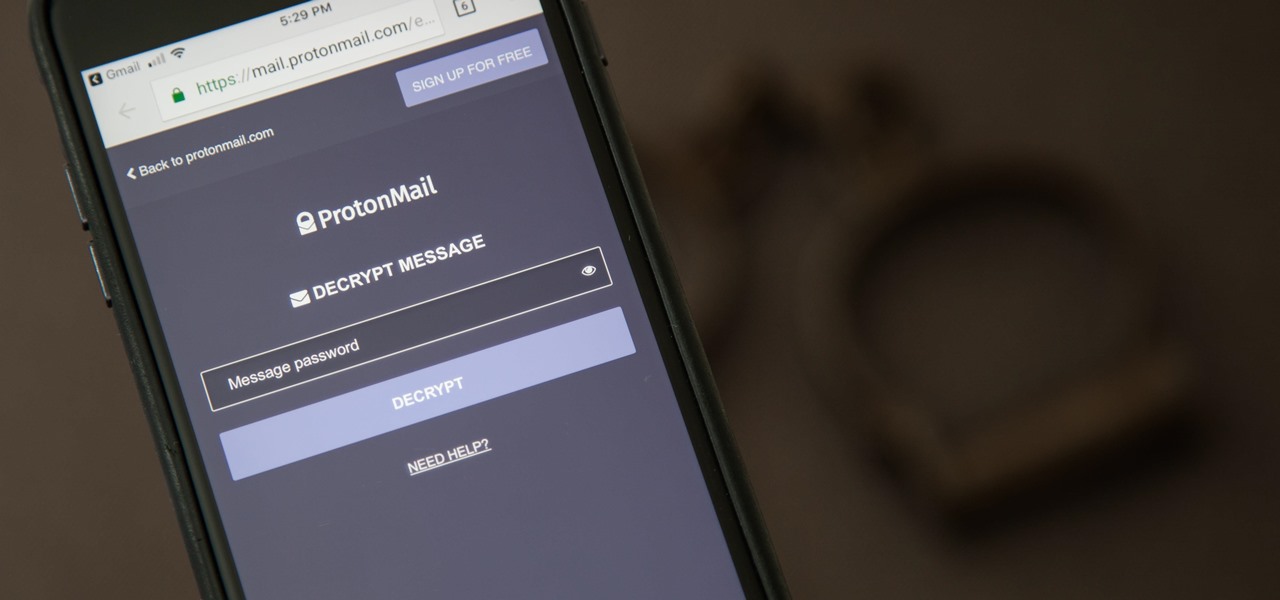
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or extensions to read or reply to the messages.

We'd never turn down a nice big slice of homemade apple pie, but sometimes eating the same selection of all-American desserts (apple pie, brownies, lemon custard pie) gets to be boring.

You don't want anybody to have access to your cell phone. Nobody. Well, instead of the standard unlock mechanism, the one anybody can unlock your cell phone with, the Motorola DROID, and Android enable mobile device, allows you to create your own unlock pattern, secret to anyone else, which wakes it from sleep mode. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up a secure lock on a Motorola DROID cell phone.

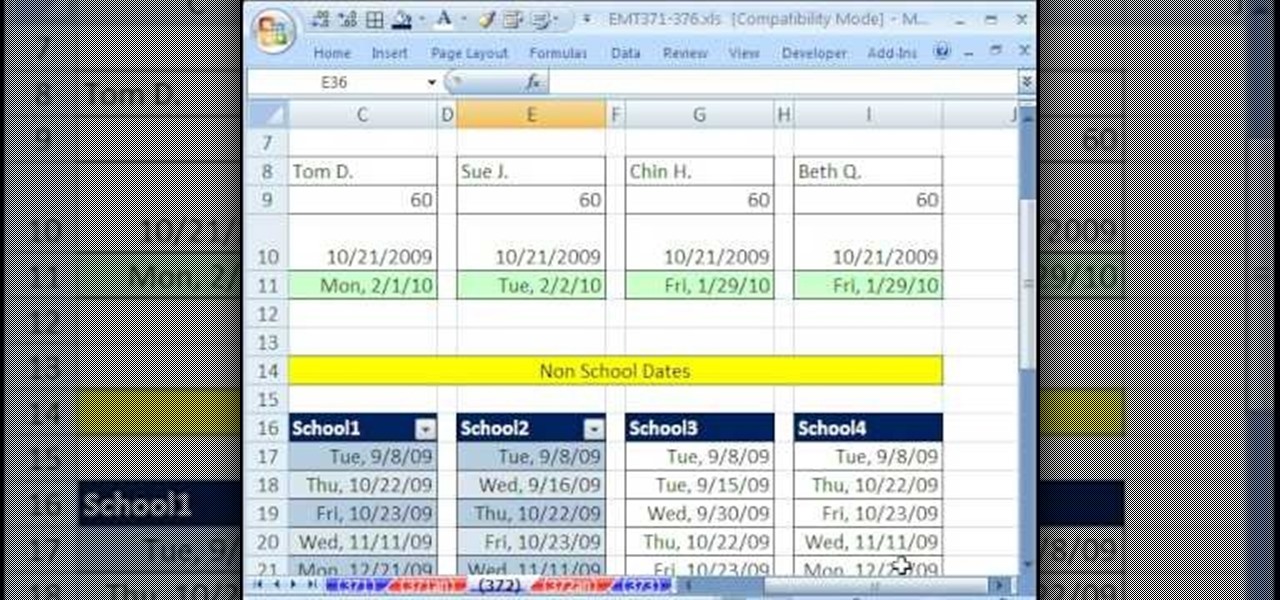
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 372nd installment in their series of digital spreadsheet magic tricks, you'll learn how to find the end date for a specified event with the WORKDAY function given a start date, number of workdays and non-included days.

In order to begin, you will need the following: Three hair tiesBobby pinsHair spray or spray gelRat tail combHair net

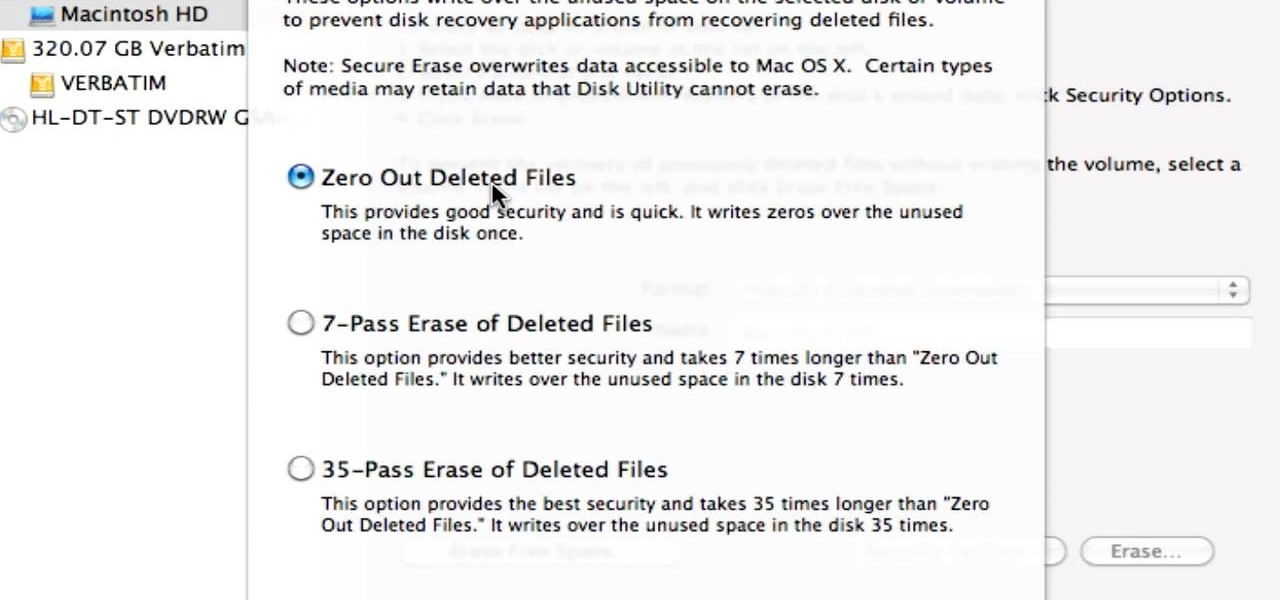
Did you know that even after you've emptied your Mac's trash can, the data still has not been permanently removed from your system? Anyone who knew where to look could easily unearth this data. You can prevent this by using the secure empty trash option on your Mac. Whenever you put something in the trash, instead of pressing delete, go into 'finder' up top and press 'secure empty trash'. What this will do is replace the data that is left behind on your hard drive with random ones and zeros. ...

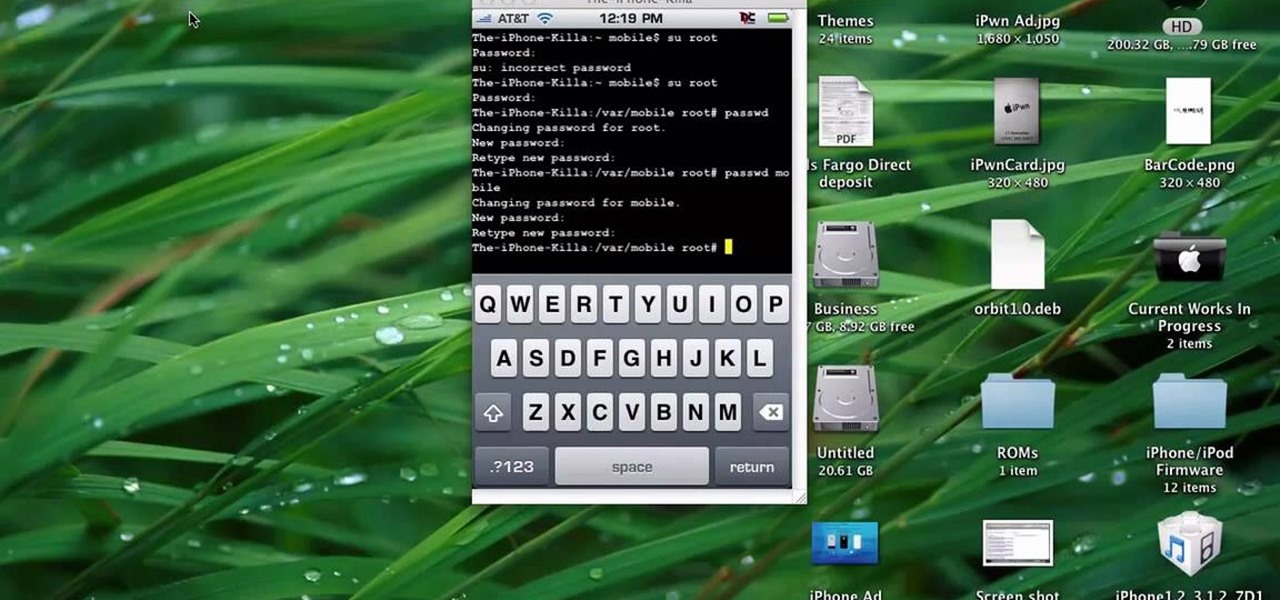
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

First of all, we don't recommend this makeup look for a first date. With super dramatic brown shadow and liquid-lined black cat eyes, you may just look like you're trying too hard. But if you're in a committed relationship, or have been dating for a while, this makeup look is a fierce way to spice things up.

TrueCrypt is a free open-source program for encrypting data and it's excellent for securing hard drives, but it also has the ability to hide a secret operating system inside another operating system. CNET shows you how this "insider secret" operating system is created. This operating system will be impossible to prove to people like the Feds.

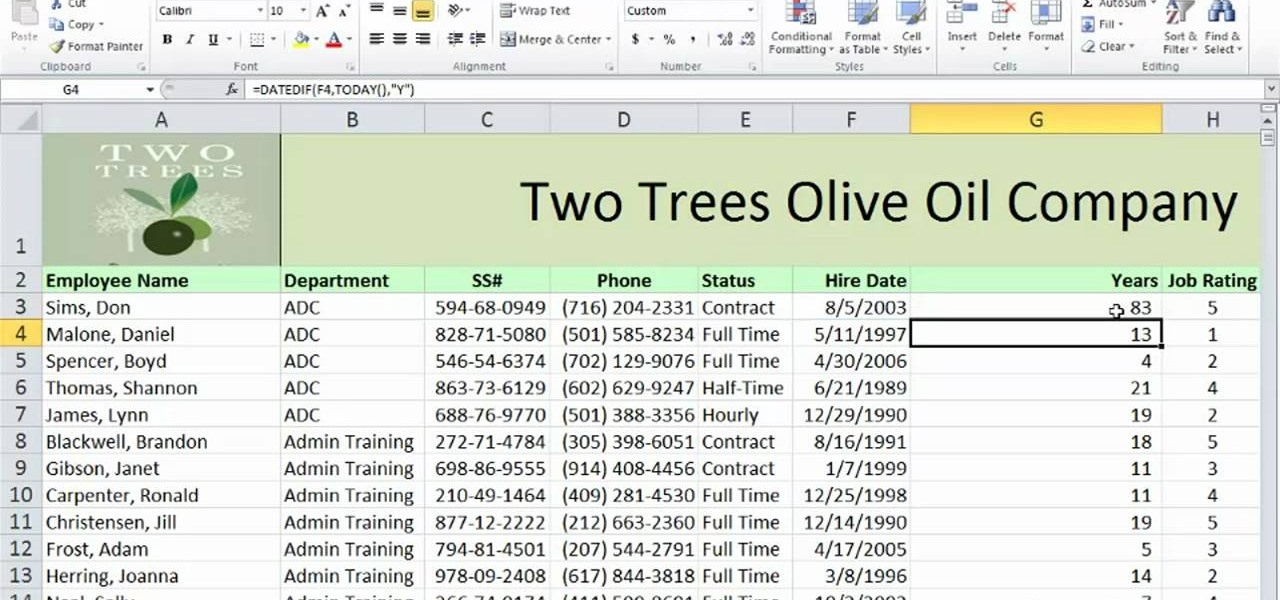
Learn how to find the difference between two dates with MS Excel 2010's DATEDIF function. Whether you're new to Microsoft's popular digital spreadsheet application or a seasoned business professional just looking to better acquaint yourself with the Excel 2010 workflow, you're sure to be well served by this video tutorial. For more information, including step-by-step instructions, take a look.

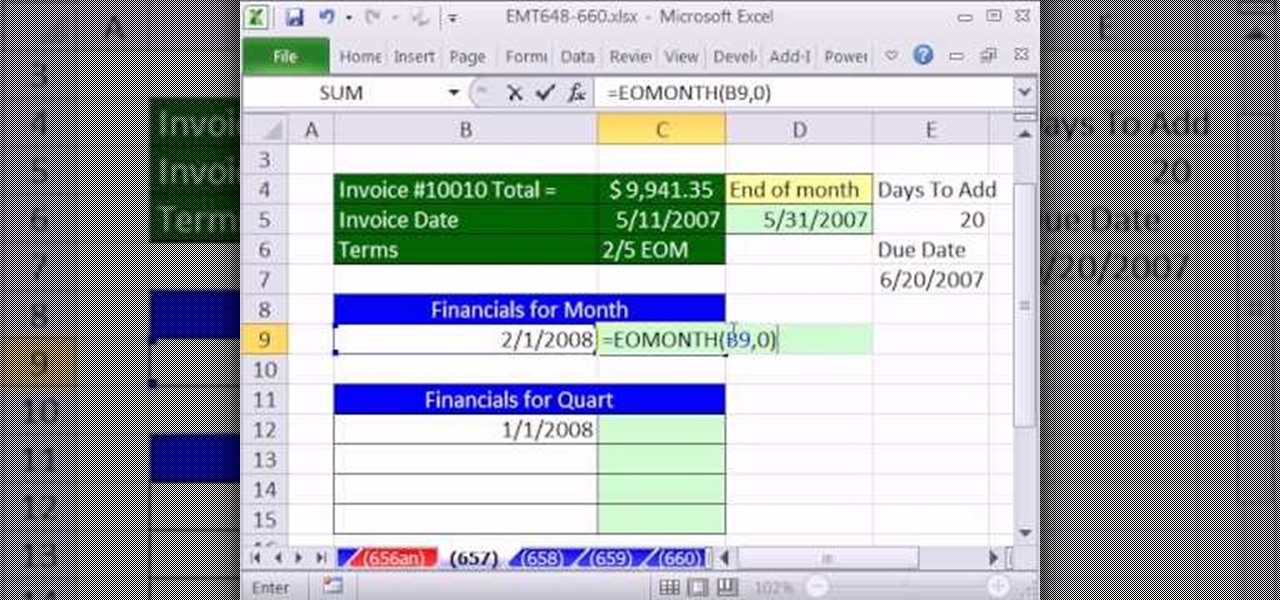
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 657th installment in their series of digital spreadsheet magic tricks, you'll learn see howto calculate Invoice Due Dates & Financial Statement Dates using the EOMONTH function including end of the month and beginning and ending dates for each quarter.

If your pet has recently had surgery or been ill, they may need to wear a medical collar. A medical e-collar or a cone will prevent your pet from chewing or licking an area of their body that they shouldn't be touching. In this video from Dr. Lauren, you will learn where to get an e-collar and how to secure it to their head so that they stay safe and happy.

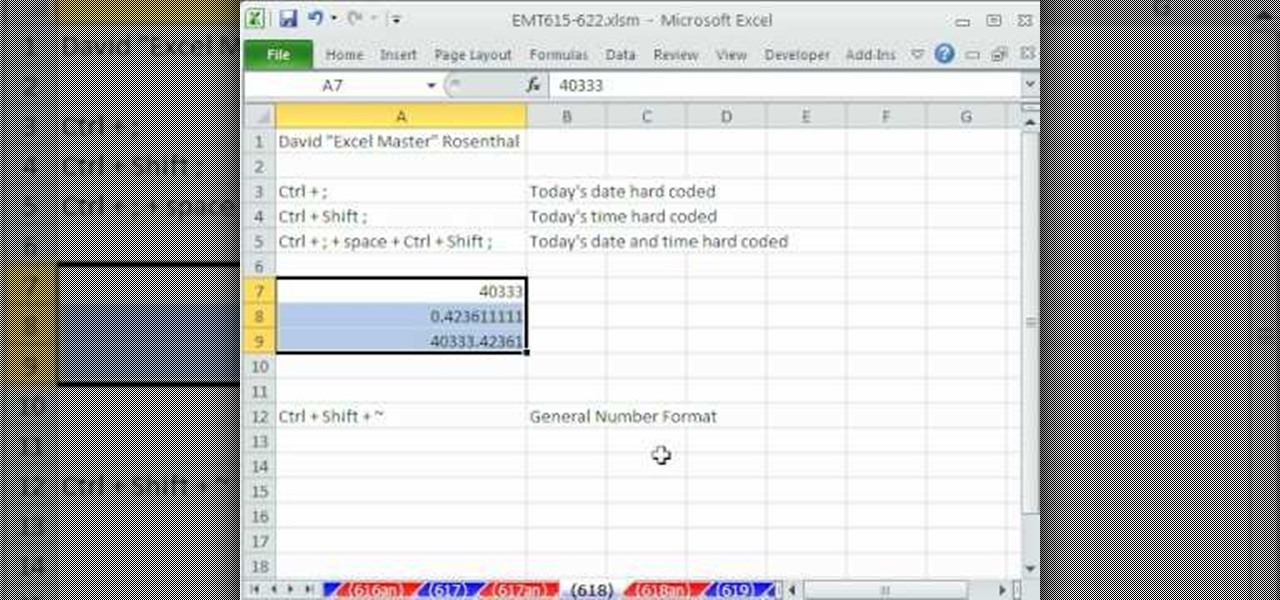
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 618th installment in their series of digital spreadsheet magic tricks, you'll learn about a handy key command that will allow you to enter both today's time and date into a single Excel cell.

Titli Nihaan shows us how to make Date and Walnut Cake. The ingredients are 200 g. of pitted dates cut in half, 100 g crushed walnuts, 100 g of brown sugar, 100 g of white flour, 100 g butter, 1 tsp. baking power, 1/2 tsp. cinnamon, 1/2 tsp. nutmet, 2 tsp. honey and 2 eggs.

In this video tutorial from Get Connected TV, hosts AJ Vickery and Mike Agerbo will show you how to safely move your iPod files to your home pc, for back up purposes, just in case something were to happen to your iTunes account or your iPod is damaged, or music directory accidentally deleted. The program they introduce in this video is called iPod-Rip, and they lead you through the steps necessary to back up your iPod files safely and easily, without damaging or deleting your files.

Sometimes it can be difficult to find information essential to a citation on a webpage, like an author or a date. Here are some steps you can take to make up for this lack of information.