Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

Jerry Lavender demonstrate how to build confidence in your children. Use secure attachments to provide a stable base for your child. Your child will fee safe to explore the world. Provide structure and predictable environment for your child. This will enable your child to relax. Use a stable routine so that your child knows what to expect during the day. Encourage your child to play with people in their environment. Sports and physical activity raise endorphins and increase happiness. Remembe...

Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to secure your Gmail account.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.
Learn how to use the VBA environment within MS Excel 2007 to create custom macros. Whether you're new to Microsoft's popular spreadsheet application or a seasoned business professional just looking to better acquaint yourself with the unique features of Excel 2007, you're sure to be well served by this video tutorial. For more information, and to get started working within Excel 2007's VBA environment yourself, watch this free video guide.

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

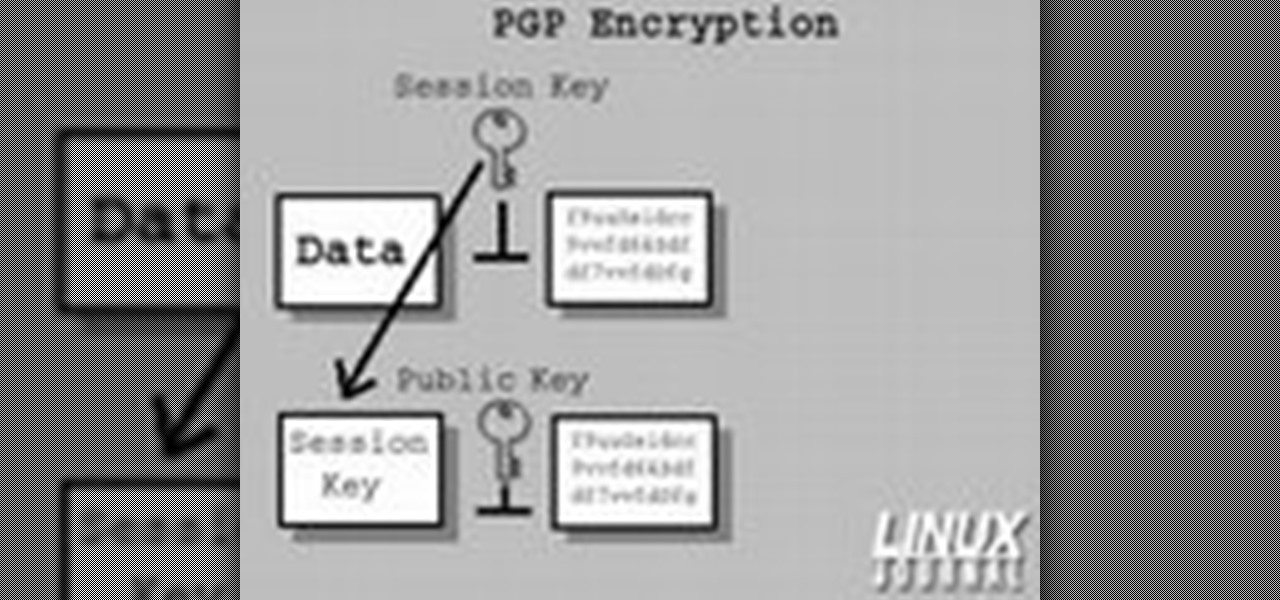
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

This video explains how to solve several problems associated with gardening in arid environments. Rhubarb is a plant that is commonly grown in colder environments. In arid environments, its very important to not over water it, so keep it in a sandy soil with lots of organic compost material. Plants such as the peace lily also need well irrigated soil, so it is important to pot it in an organic potting soil in a location that allows the water to drain away from the pot instead of soaking back ...

Why buy an ant farm? It’s simple and fun to make one from a few items you have lying around the house.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

Check out this video tutorial from the Homemade Game Guru for a new idea in making the clean-up of pollution, emissions and litter more enjoyable for everyone. This video will take environmentalism and make it into a game anyone can make from home. So, see how to make a green environment spinner game.

With the British exit from the European Union looming, the UK is looking to the auto industry to help boost their economy and secure jobs through the upcoming years. Today, Business Secretary Greg Clark and Transport Minister John Hayes announced the government investment of $136.7 million (£109.7 million) across 38 different automobile projects, as a part of the Plan for Britain.

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

See how to create a three-dimensional outer-space environment for your Flash games in Papervsion3D. Whether you're entirely new to 3D Flash design or a seasoned developer merely looking to better acquaint yourself with Papervision3D, you're certain to be well-served by this free video tutorial from the folks at Lynda.

In this clip, learn how to take advantage of Adobe After Effects built-in noise plug-ins to create an outer space environment. Whether you're new to Adobe's popular motion graphics and compositing software or a seasoned video professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

A quick tip on environment maps in Blender. Blender 2.49b. Whether you're new to the Blender Foundation's popular 3D modeling program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look.

Washington State has a history of large earthquakes, as does California. More than 1,000 earthquakes are registered in Washington State each year. More than 10,000 are recorded in California each year. In an earthquake, non-structural elements, which is anything that does not actually hold the building up, may become unhooked, dislodged, thrown about, and tipped over. this can cause extensive damage, interruption of operation, injury and even death.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

In this video tutorial, you'll learn how to creat a 3D environment with a skybox within Papervision 3D. Whether you're entirely new to 3D Flash design or a seasoned developer merely looking to better acquaint yourself with Papervision3D, you're certain to be well-served by this free video tutorial from the folks at Lynda.

Learn how to set up your render environment and layout backgrounds in Swift 3D scenes. Whether you're new to Electric Rain's popular Flash-oriented 3D modeler or just looking to better acquaint yourself with the program, you're sure to find much of value from this free video software tutorial. For more information, including a complete walkthrough of the process, watch this web developer's guide.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

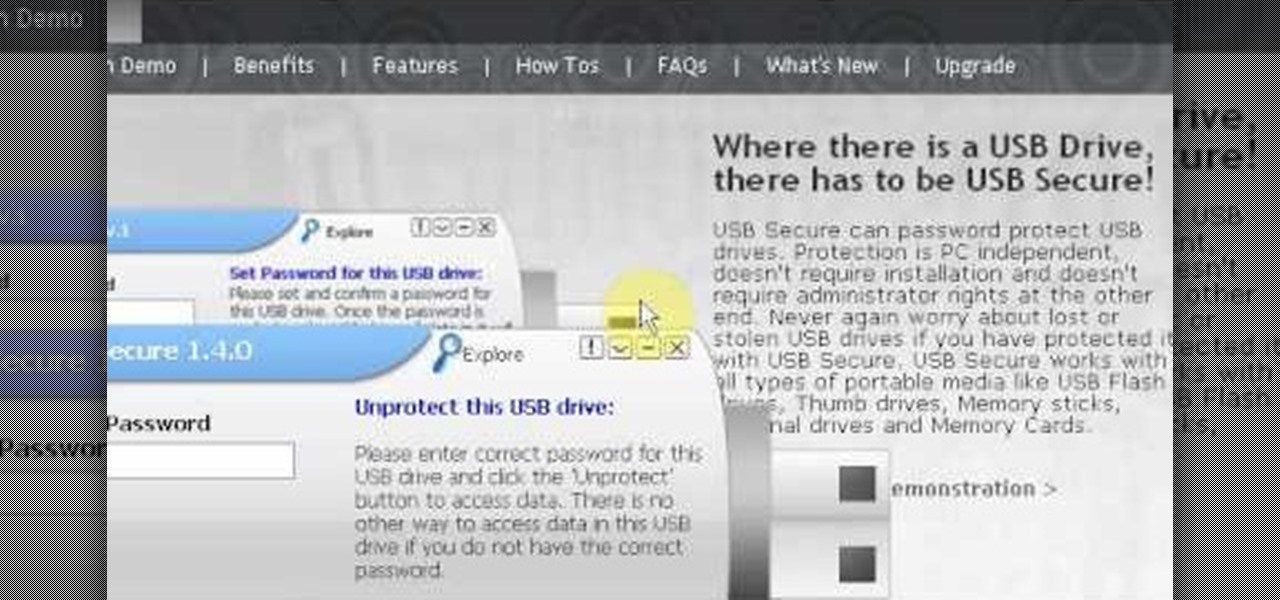
Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

Use three tools to create a simple ponytail. Use a hairbrush, a bobby pin, and a bungee band holder for this look. Using a bungee band instead of a standard ponytail holder eliminates some of the issues typically caused by pulling hair through ponytail holders. Start by using a bristled brush to brush the hair to one location on the head. Secure one hook of the bungee band in the ponytail and wrap the tail around the rest of the hair. Wrap it around again, and secure the other bungee band hoo...

Using ASP.NET Secure Services and Applications Services

Need to know how to tie a Bowline with a few ways of securing it? This way shows you how to secure it with a seizing so that it won't accidentally come undone. Included is a little variation of the bowline with a built-in seizing. If you don't have electrical tape to secure the bowline feed the bitter end back through the hole. It also makes it so you don't have a tail line dangling if you're towing something.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

This Unreal Engine 3.0 Gears of War lesson deals with creating outside environments and sky spheres.

Buns and updos are gorgeous hairstyles, with one caveat: If they're not pinned perfectly and securely in place, all your hard work braiding and curling will go to waste as your hair slowly unravels.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

In this clip, you'll learn how to get started using Secure Computing's Secure Web Protection proxy service. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

It's really easy to take lazy route and purchase fire starters at a grocery or hardware store to aid you in creating campfires, but storebought fire starters tend to have massive amounts of environment polluting chemicals and toxins that you probably shouldn't be anywhere near.

How to draw and paint rock cliff mountain environmental concept background. This landscape scene is created in a video demonstration using Photoshop. his step by step video shows you laying down the base color, blocking in shape for painting, assigning value and color composition, and refining detail for the final concept painting.

This tutorial utilizes the Distort tool in order to convincingly put a comp of a poster into a second environment. Whether you're new to Adobe's popular graphics editor or a seasoned design professional looking to better acquaint yourself with the various features and functions of Photoshop, you're sure to benefit from this free software tutorial. For more information, watch this designer's guide.

Picking a secure password is not only important for protecting your privacy, it's also very easy. Provided, that is, that you know how to go about it. This free video lesson from CNET TV will walk you through the process. For more information, and to get started creating and using high-security passwords yourself, watch this video tutorial.

The Clinch Knot is used to secure your fishing line to your fishing lure. In this video, learn how to tie a secure clinch knot, step by step. You can't fish without a sturdy lure, so watch the video and practice until you master the knot on your own. Once you've got it, attach your bait and you are on your way! Happy fishing!

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Don’t play Russian roulette when it comes to your wheels. Keep your bike secure with these precautions.

A formal occasion calls for a classic look. You Will Need