Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

When you first receive bObi, the battery is not plugged in. Luckily all you need is a Phillips head screwdriver to install it before bObi starts working for you.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.
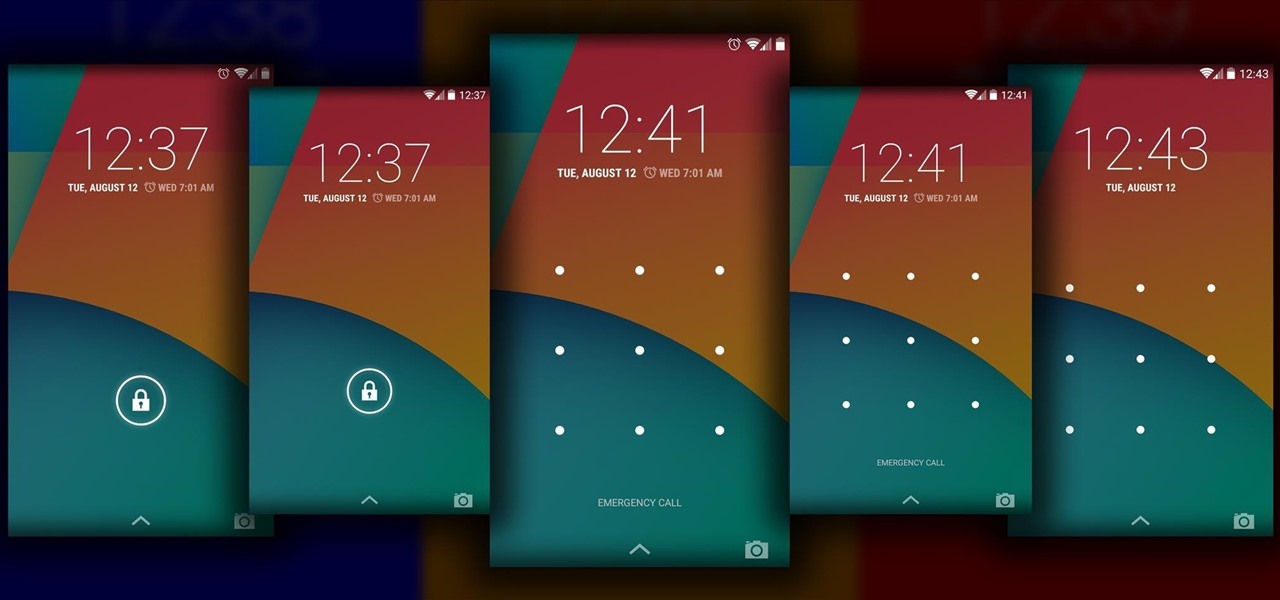
The Android lock screen interface is an integral part of our everyday use. For those of us who use lock screen security, it functions as a barrier between the sensitive data contained within our smartphones and potential outside access. Even if you don't use a pattern or PIN to secure your phone, you still interact with the lock screen every time you go to use it.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.

Welcome back, my greenhorn hackers!

Adding water features to your garden can help to create an enviroment that more closely resembles nature. The sound of a trickling fountain can make your garden feel more peaceful and relax. Paul Tamate, a leading landscape designer working with water features and Asian-inspired garden designs in San Francisco says, "design spectacular water features as the centerpiece of gardens that serve as retreats from modern life."

Fashionably cool and awesome, this marvelous French Twist hair Style is as simple to make as it is elegant and stylish to flaunt. Just in few easy and accessible steps, this urbane style makes your appearance special and any outing memorable. Step 1: Comb Your Hair Neatly to Remove Any Tangles and Make Them Smooth. Step 2: Hold the Hair Together Like a Pony and Twist Them Till the Middle of the Pony and Make a Roll as Shown. Step 3: Once You Have Secured the Roll, Cover It with Surrounding Ha...

Being in your twenties is tough. You're not a child anymore, but also not quite a full-fledged "adult" yet. Sure, you do adult things like cook asparagus sometimes, but you're also sweating about securing enough likes on your social media posts.

So many times, you turn on your computer, you open your front door, or you sit down on the couch to watch some well-earned TV, when you think -- Gosh! If only I could do this or this, life could be so much easier! And then, if you were a boring person, you would slouch even further down on the couch and continue to watch those reruns of The Sopranos.

The new Call of Duty: Black Ops 2 is the hottest game on the market right now, and there's no doubt it'll end up being the most unwrapped gaming gift come Christmas morning. The first-person shooter hopes to carry on the tradition of its many predecessors in bringing the most action-packed gaming modes, along with a high-replay value, to its legions of fans.

Costume parties are in full effect this weekend, so with that said, how cool would this look at your Halloween party? Instructables user castor009 made two holes in the head (one for inserting the PVC tube, the other where the liquid will spew out) and insert the pipe and tubing, then stuffed it to secure everything. He then fit the bottom tubing through a pencil holder and attached it to a water pump. Then just add whatever you want to serve at the party (I would suggest anything red or blac...

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Spray the Styrofoam ball with a color that adheres to the scheme of the ribbon and ornaments. There will be white space when you make a Christmas ornament tree, and the color on the ball will help to conceal the space.

Choose ribbon in an appropriate color, texture and width. Are you trying to match the ribbon color to a particular gift wrap? Will the ribbon width give you the size bow you want? How will you be using the bow?

Place slip knot on hook. Hold yarn taut with 2 sets of 2 of fingers placed about 1½” apart, with tail in other hand. Create loop that crosses over bottom of 1st strand with loop toward right side. Fold loop over main strand going past tail. Insert hook below at tail strand. Pull up a loop using main strand for this loop. Pull 2 ends of yarn taut while leaving slip knot on hook. In 1st chain work 1 single crochet. Skip 2 chains; work 1 double crochet in 4thchain. Picot stitch by chaining 3 & a...

Learn how to sew a button by hand. Not wearing your favorite shirt because it’s missing a button? Don’t worry—sewing on a new one is simple and fast.

The human body contains nine units of blood—but in matters of a traumatic cut or injury, it's always better to be safe than sorry. If you're unsure whether you're in an emergency situation, get to an emergency room and let them decide.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

If you're looking to improve your browsing experience, then a VPN is the right way to go. If you're tired of censored or geographically blocked sites and wary of companies selling your data, then a good VPN can be your answer to a problem that limits every aspect of your experience online.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

In Obstetrics and Gynecology (OB/GYN), doctors deal specifically with the female reproductive organs, which means a lot of visual inspection of the vaginal area. Whether you're a doctor, surgeon, nurse, or nursing assistant, knowing how to properly drape a patient is detrimental to the patient feeling protected and secure with the hospital staff, along with having some privacy. This video will cover different types of draping techniques.

It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

Check out this Do It Yourself (DIY) RV maintenance and repair video to learn how about RV battery maintenance. Know how to do it to keep your batteries running strong in your recreational vehicle with this RV tutorial video.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.