Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.
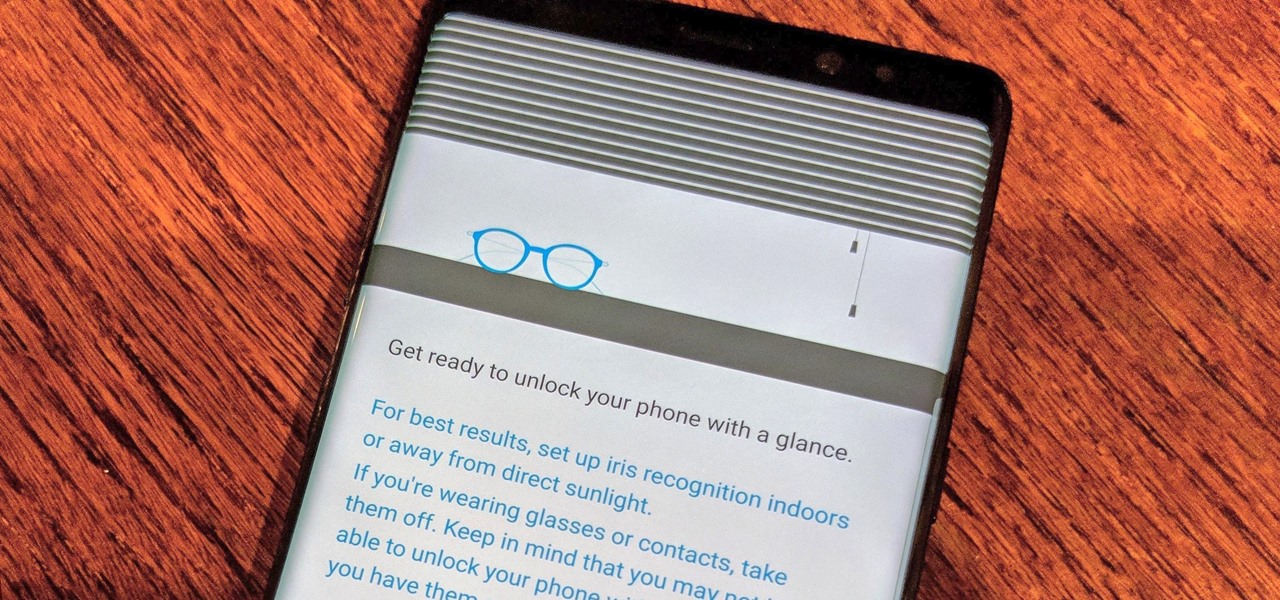
Over the past few days, we've learned a lot about Samsung's upcoming Galaxy S9 and S9+ smartphones. In addition to a full list of hardware specs, we have complete renders direct from renowned leaker Evan Blass. Of course, Samsung always has a few surprises up their sleeve, and today, we have some new information about the facial unlock method arriving on the S8.

As the Samsung world anxiously awaits an official Android Oreo update, some Galaxy Note 8 users are waking up to find their devices have jumped the line. Are you one of them?

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest browsers on the market.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

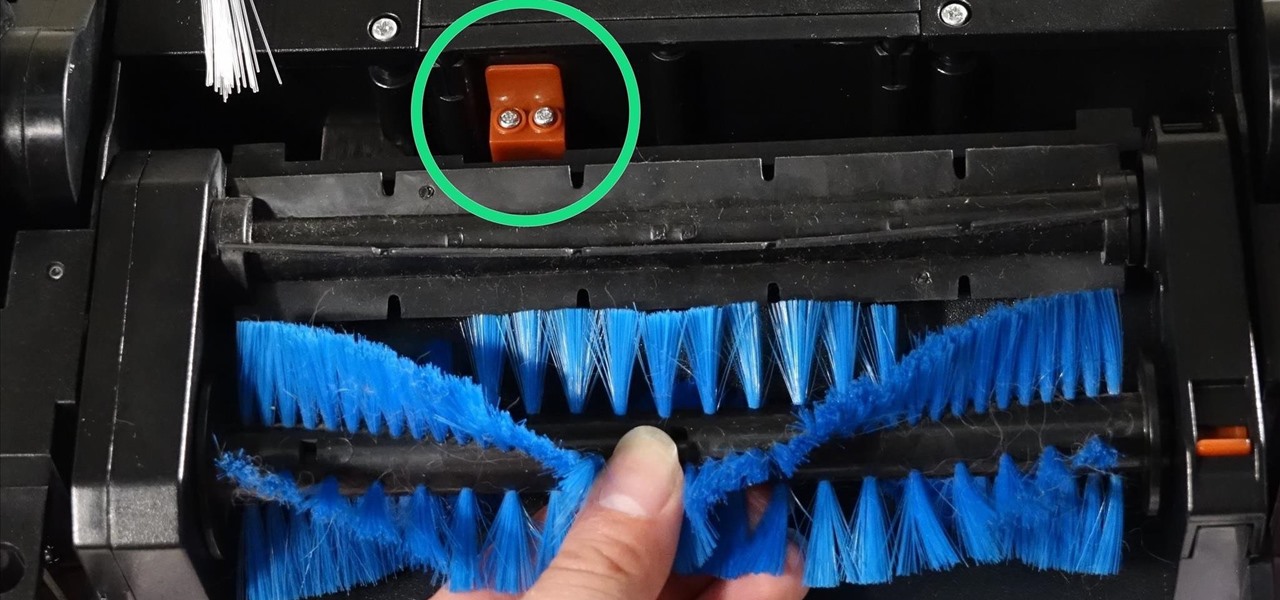
One of the quickest repairs for bObi is replacing the main brush motor. To do this, you'll need a Phillips head screwdriver and a replacement main brush motor.

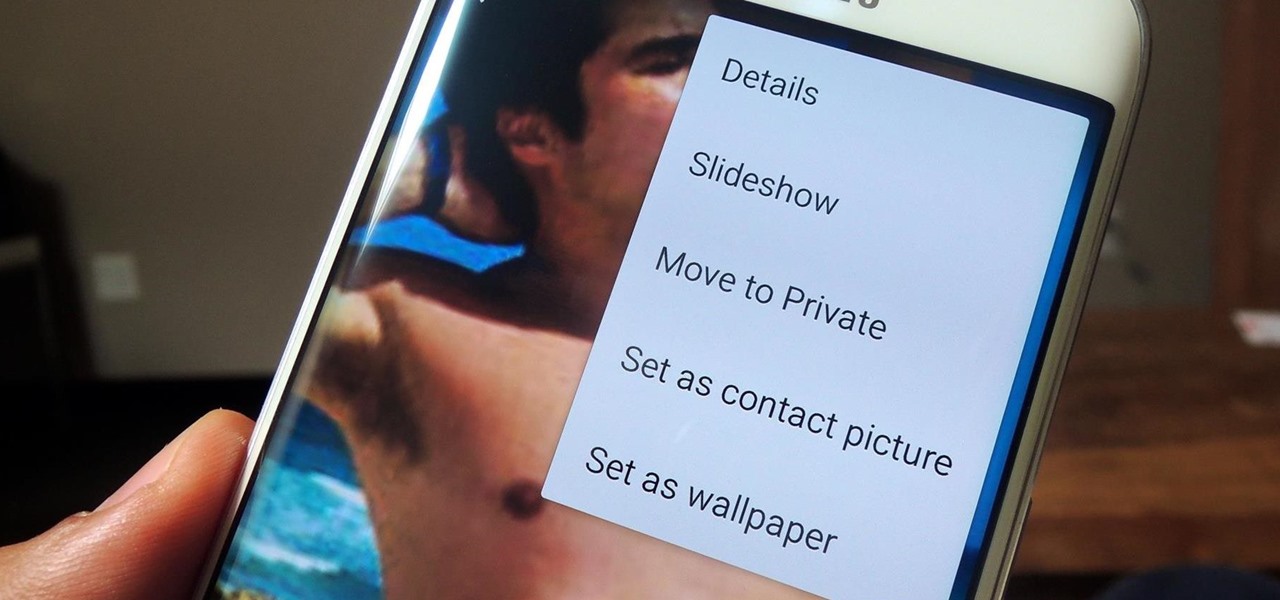
If you have a smartphone, chances are you have something on it you don't want others seeing. Whether it be photos, videos, or documents, some things are best left private. Not everyone is a saint, after all.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

With the new year just around the corner, it's a time we all reminisce about the year that was. In the midst of families fighting over white elephant presents and the financial stress that comes with holiday gifting, you may also be dealing with the stress of hosting parties and get-togethers as well as the decorating that goes with it.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

No matter how many PSAs are published on the topic, studies continue to show that we are generally terrible at creating secure passwords and PINs. Using the same password (or variations of it) for multiple sites is another huge no-no that the majority of people ignore, and even though you should change your passwords frequently, most of us don't.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

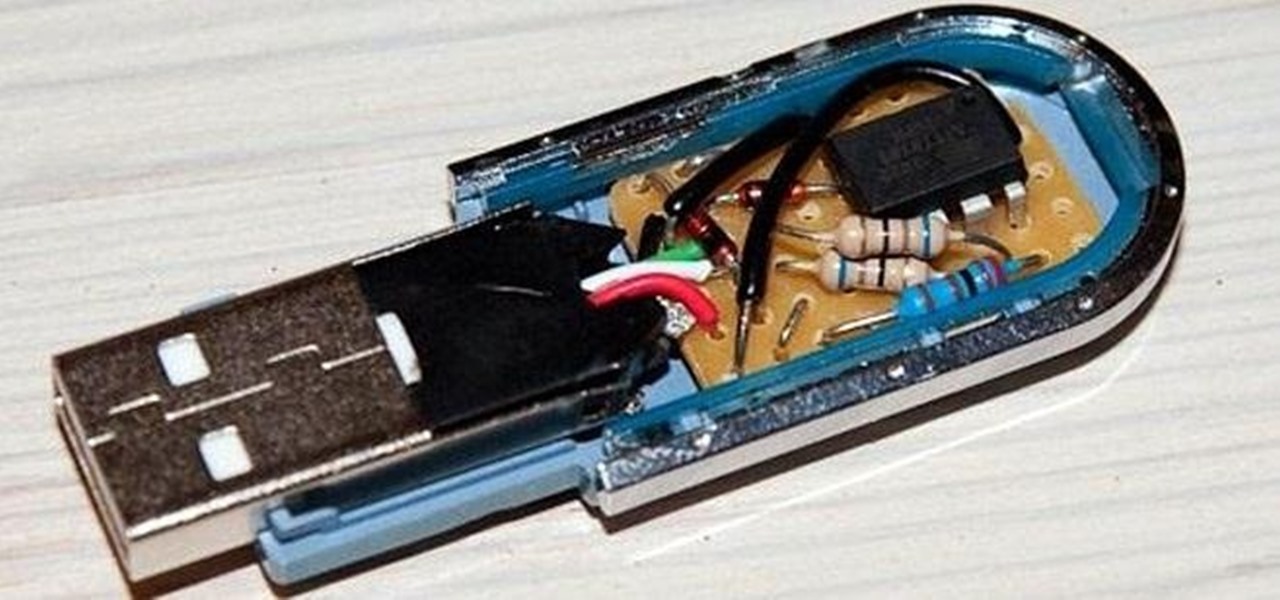
Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on.

Everyone knows that using your phone and driving is illegal, and rightfully so. Tons of people die on the road everyday due to careless people texting or calling someone. Everybody knows that it's wrong, yet everyone still does it anyway.

In these video tutorials, viewers learn how to tie the ribbon on ballet shoes. Make sure that the elastic and ribbon are adequately secured on the shoe. Begin by flexing your foot. Take the inside ribbon and loop it across the top of your foot. The outer side ribbon will go over the inner ribbon. Pull the ribbons tight enough so there is no gaping or sagging. Then, wrap the ribbons around the ankle and tie them together. Now, tuck the tie under the flat part of the ribbon. These videos will b...

Washington State has a history of large earthquakes, as does California. More than 1,000 earthquakes are registered in Washington State each year. More than 10,000 are recorded in California each year. In an earthquake, non-structural elements, which is anything that does not actually hold the building up, may become unhooked, dislodged, thrown about, and tipped over. this can cause extensive damage, interruption of operation, injury and even death.

Not every nurse can get an IV every time, that's why it's important to stay in practice for the proper technique used for inserting a peripheral IV. This is a common medical procedure that all fields related to medicine should know. Even the soldiers in the military are taught how to insert an IV — every soldiers, not just the medics.

First of all keep the chicken under the running water and then pad it dry. Then you have to remove the neck, inner portions and the fat from the abdominal cavity. Now season the inside of the chicken with salt and pepper by standing it up inside the bowl. You can now add the desired spices. In this case you can use garlic cloves and lemon pieces. Now close the abdomen cavity and lay the chicken on the cutting board. Wedge the wing tips under the wings. Close the neck cavity by wrapping the sk...

Fifty cent coins and quarters made before 1964 were made of 90% silver. This is considered jeweller's quality silver so can easily be made into a ring. Kennedy Half Dollars can be found at coin shops or on ebay for four or five dollars a piece. Begin with an anvil which can clamp onto a table. This will allow you to hammer without damaging the table. If you don't have a anvil, you can use any flat surface that is sturdy and made of metal. Next, take a small hammer, position the coin on its ed...

It only takes 15 minutes to install new RAM in a Macbook Pro. Before starting, remember to make sure that the power is off. Turn it over and release the latch in the left hand side. This will release the door and expose the battery. Remove the battery. With a #00 Philips screwdriver, remove 4 small screws lined up on the top of the opening. Next, remove the other 4 screws on the other side next to the hinge. When that is done, remove the cover. You will see the RAM directly in the middle. On ...

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

Check out this informative video tutorial from Apple on how to set up iChat to text, video or audio chat with friends. iChat is an application that's part of every new Mac. It lets you stay in touch with friends and family in fun innovative ways.

Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to organize your Mail in Mac OS X's Mail. See how to sort messages with rules, create smart mailboxes, and comlpletely organize your mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of Mac OS X Mail. See how to set up mail with your email accounts, compose messages, add attachments, view attachments with Quick Look, and search through Mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

Create and animate a stop motion LEGO brickfilm! Yes, that's right... you can make your very own animated brickfilm, but wait... what exactly is a brickfilm? Brickfilms are animated films using LEGO, Mega Bloks, or other plastic construction building block toys. Most are stop motion, but some brickfilms are even made with CGI, traditional animation and live action.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Watch this video to learn how to properly secure a bookcase in case of an emergency.