Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

Augmented and virtual reality motion tracking leader Leap Motion, Inc. announced that it has secured $50 million in Series C funding to fund expansion into new territories and industries.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.
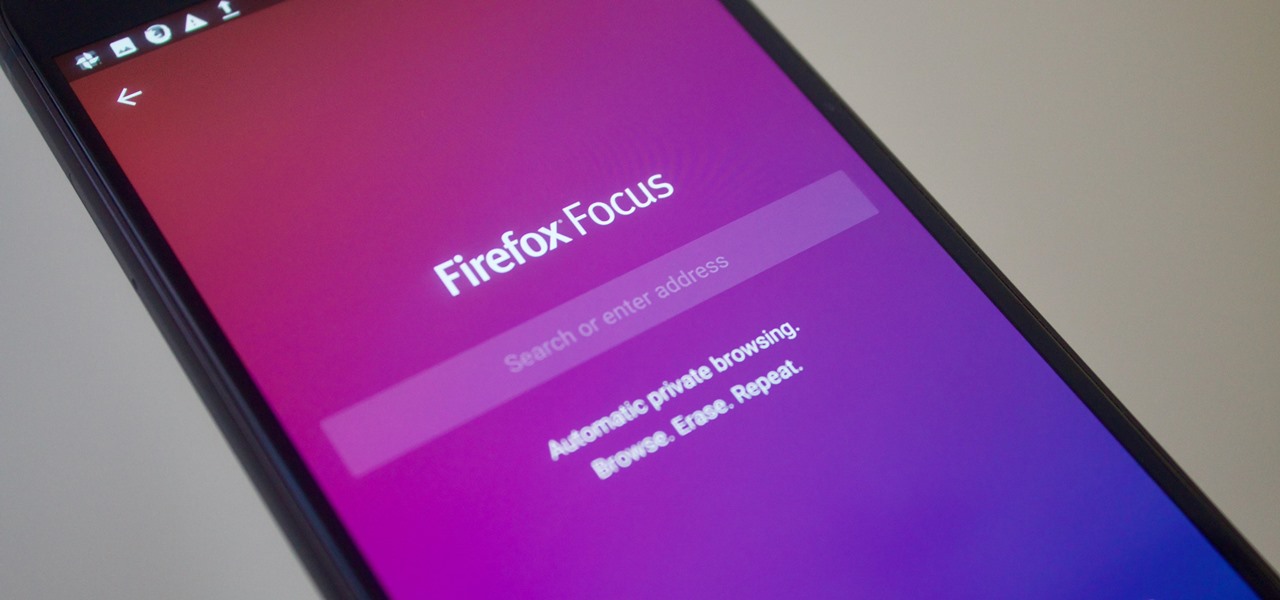
Firefox Focus is Mozilla's effort to make your internet experience a little more secure. Originally released in November 2016 for iOS, Focus blocks internet trackers, search history, anything that gets in the way of a clean, private browsing experience.

With the British exit from the European Union looming, the UK is looking to the auto industry to help boost their economy and secure jobs through the upcoming years. Today, Business Secretary Greg Clark and Transport Minister John Hayes announced the government investment of $136.7 million (£109.7 million) across 38 different automobile projects, as a part of the Plan for Britain.

Independent game developer PlayFusion announced today a partnership with NEXON Korea Corporation, resulting in a Series A preferred share round to fund development of their entertainment platform. PlayFusion's platform applies augmented reality, Internet of Things (IoT), and audio recognition to Lightseekers, an original property that combines mobile gaming with smart action figures, trading card games, and other media.

Facebook Messenger is getting ready to roll out a Snapchat-esque feature that will let users send messages that self-destruct after a certain amount of time, so you'll have an extra level of security when you need to send sensitive financial information or, more likely, risqué texts or images.

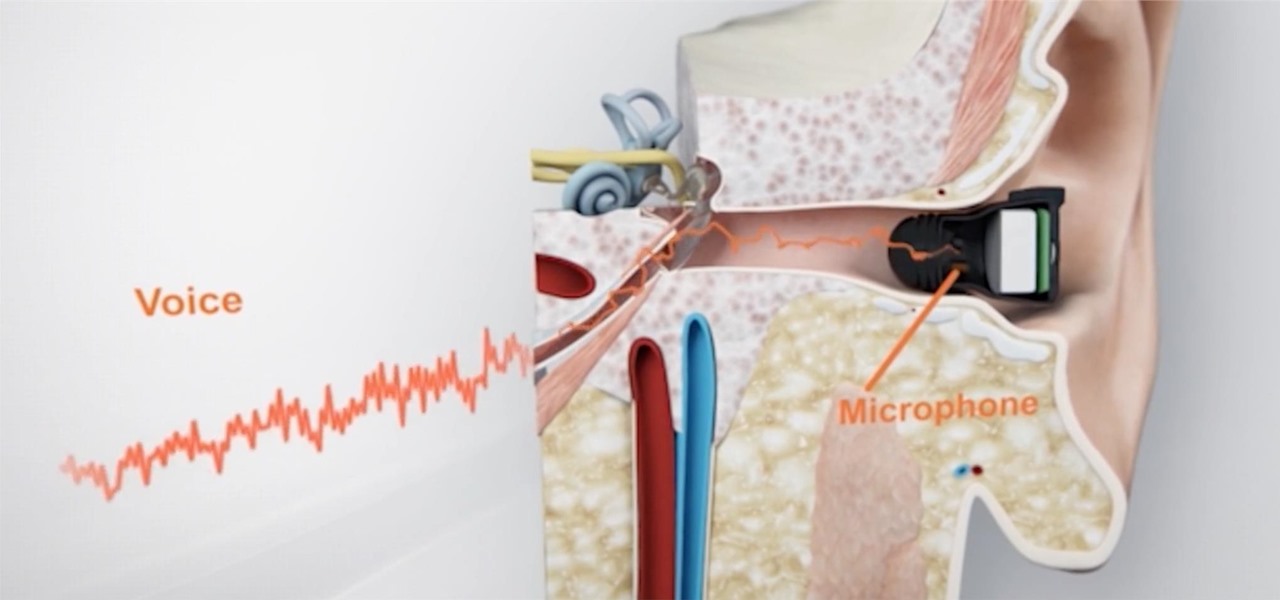
What's better than wireless in-ear headphones with noise-canceling technology? Giving them a microphone to hear you talk from inside your head. And that's exactly what you get with RippleBuds; its inside-facing mic helps keep your voice crystal clear over phone calls, and makes sure Siri, Cortana, and Google Now will always get the right command.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.

In this tutorial I am going to show you how to change some file metadata, this could be very useful if you want to edit or access a file and remove any evidence of your changes.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/)

This is a really tasty "scary" snack as it incorporates a lot of the flavours you'd usually put together (along with the almonds)

Making the bed is a challenging task, but trying to put a duvet cover over top your comforter is a challenge on a whole different level.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

This is a simple process for those wanting to capture a circular view of an object with their smartphone or other type of camera.

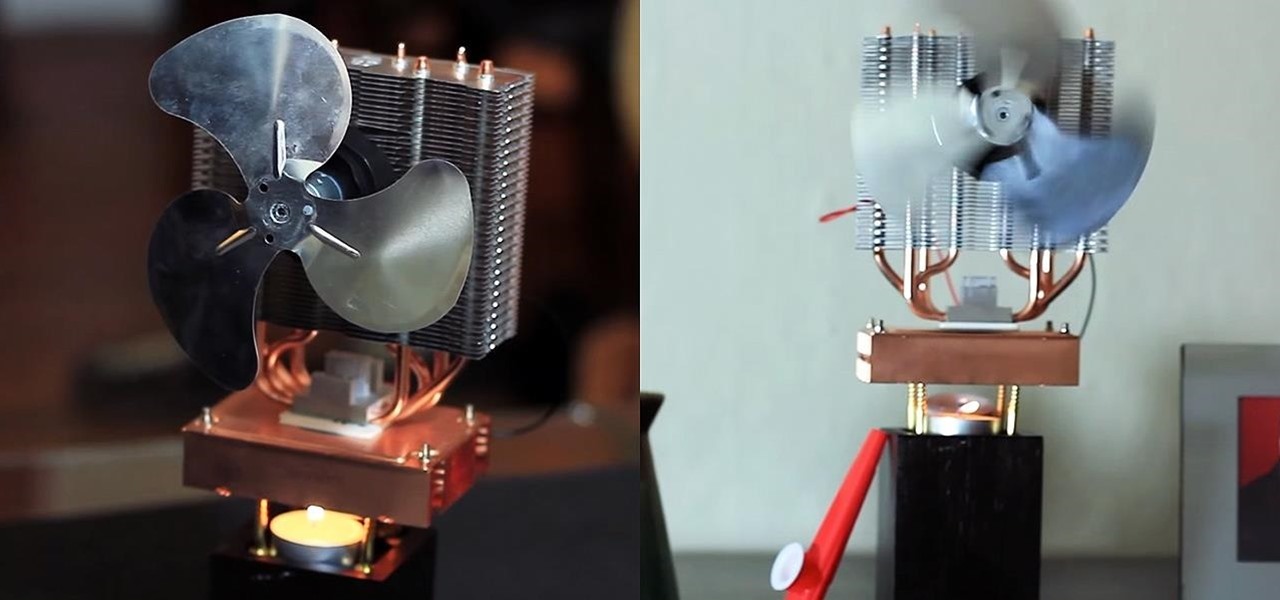
Staying cool in the summer heat sometimes feels like it takes all the energy in the world. But what about a fan using no-cost electrical energy? If you're looking to keep cool during a power outage, or if you don't want to break the bank by running your DIY air conditioner all day long, you can use candlelight to power a fan!

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

This is an easy step by step tutorial how to lock your jewels in a hotel room or in a public safe. Be aware that in a public safe it is more secure to use the second method of locking by a magnetic card, not by a PIN code that can be easily seen by someone nearby.

Adding to the recent recent slew of bugs and issues within iOS 7, it now seems that emails sent with attachments are not encrypted, despite Apple's claims that they are.

Locking up your iPhone with a passcode prevents mischievous friends from looking at your pics and emails, and makes it harder for thieves to access your data before you get around to wiping it. For even more security, there's the password option, which gives you more than just 4 lonely digits.

Impeccable is the word for this distinctive and exclusive Ladder Hair Style. Extremely elegant and graceful, girls with long hair will be going to love this. Follow these simple steps and just with a little effort arrive at special and distinguished look. Step 1: Comb Your Hair to Make Them Smooth and Tangle Free. Gather All Your Hair and Tie Them in a Pony. Step 2: Take a Small Chunk of Hair from One Side of Pony and Braid It Leaving a Small Strand of Hair Before Each Weave at Inner Side Onl...

The new year is just around the corner so it is the perfet time to make an easy DIY calendar that will keep you organized on 2014!

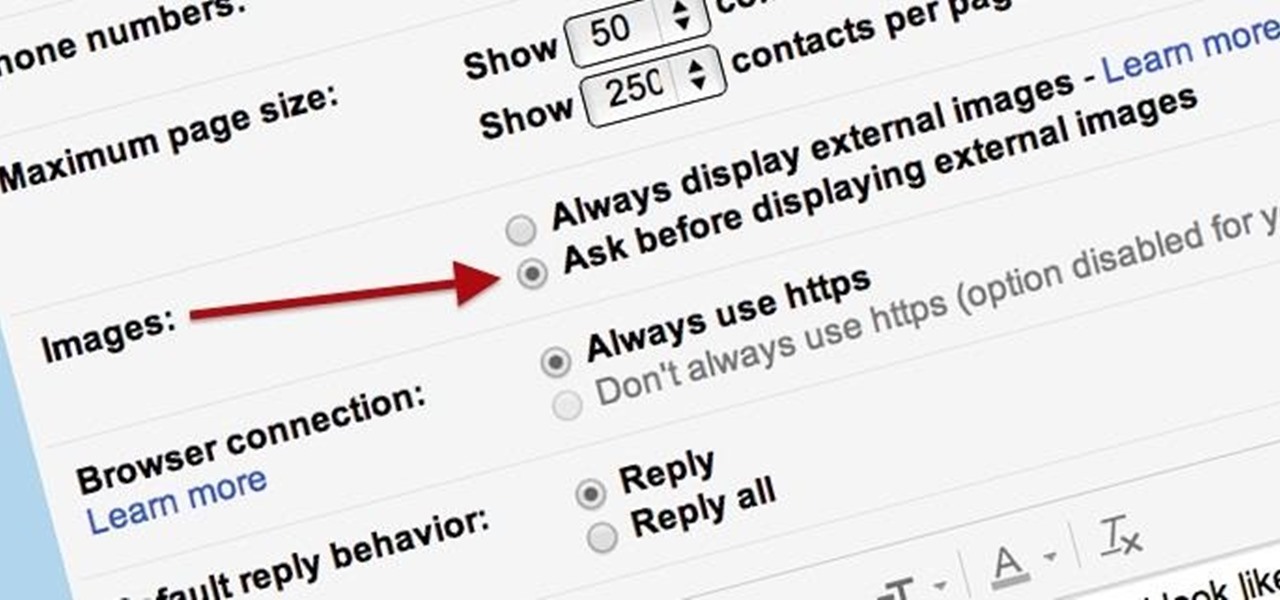
Securing your email address is one of the most important things you can do on the internet. Hackers, spammers, and overly aggressive marketers can turn your Gmail inbox into a heap trash if you're not careful.

Gmail is a free, advertising-supported email service provided by Google. Users may access Gmail as secure webmail, as well as via POP3 or IMAP4 protocols. Gmail initially started as an invitation-only beta release on April 1, 2004 and it became available to the general public on February 7, 2007, though still in beta status at that time. The service was upgraded from beta status on July 7, 2009, along with the rest of the Google Apps suite.

This is a create creation as a toddler toy. My girl loves this toy, she even wanted to take it to bed at night ... Sometimes, some of the most simple toys are some of the most like toys. This toy is cheap and can be completed in 10 minutes at most.

How to easily unclog your bathroom sink or kitchen sink and for zero dollars! Over time the bathroom sink or kitchen sink will get clogged up with gunk that will lead to poor drainage. Follow the steps outlined below for a hassle free unclogging solution.

Taking photos in the dark or in low-light settings can be tricky. Just using your normal flash can make your subject look washed out, but not using it can result in a totally dark photo with no subject at all.

A quick way to revamp an old dresser is to change out the knobs for some new decorative ones. Here’s an easy and budget-friendly way to make your very own DIY dresser knobs using shells – perfect if you’re looking to add a little bit of the beach to your decor: What you’ll need: shells (I got mine from the Dollar Store), nuts & washers, bolts (about 1 to 1.5 inches longer than the thickness of the shell), scrap rigid cardboard, rubber bands and epoxy glue.

Want to secure your home? There are plenty of ways to go about it. You can make your doorbell send you a text if someone rings it while you're not home, or build a motion-triggered security camera. Even better, you can beat potential crooks at their own game by installing a door they can't even find.

You've seen security cameras everywhere in the public space. How many are there? Where are they? This is information that can be difficult to come by. It's not just criminals that are interested in information on this. It's your fundamental human right to be able to go about your daily life without being monitored and watched at every step. You might think that these cameras are for safety, and they can certainly help make people feel secure. Then it automatically follows that these people sh...

These three videos will show you how to build a rustic, distressed kitchen table. I'll be walking you through the process of selecting some recycled timber from a junk pile, and with a little care and some simple joinery techniques, transform that waste timber into a distressed timber kitchen or dining table. In fact, you could use the table for whatever you wanted really.

One of the biggest downsides to the iPhone is that it isn't as easy to customize as other smartphones. It's true that this makes Apple products more secure in some ways, but it also means that you have to jailbreak your phone and void your warranty if you want to change certain things.

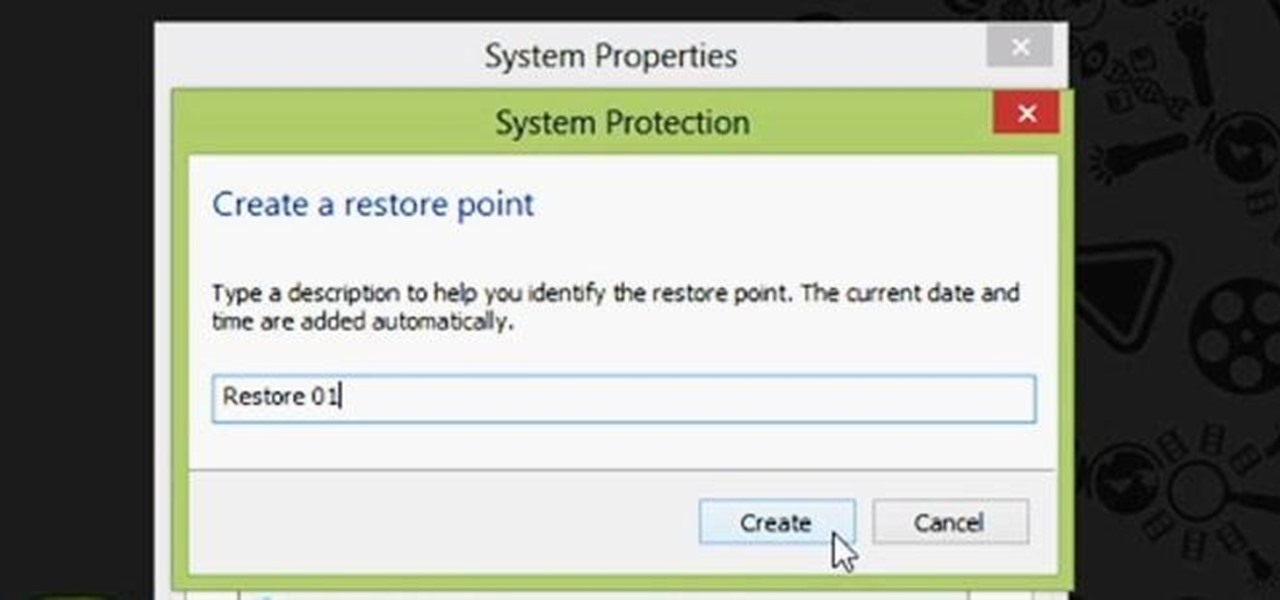
Restoring your computer to a previous point is an extremely important thing if something goes wrong. I've restored my computer at least a dozen times after downloading some suspicious software or running into an error I couldn't remedy on my own.

If you haven't met a person that's broken a pair of headphones, you might need to get out more. No matter how expensive or cheap a pair of headphones are, the sound can get buggy, the wire can get cut, or the headphone jack itself can be broken or ripped off the cord. But instead of buying a new set of headphones or borrowing the ones from your cousin with the earwax problem, you can easily fix it yourself.

The newest update of the Firefox web browser was released yesterday, and whether you were upgraded automatically or manually, Mozilla is advising that you downgrade to Firefox 15.0.1 as soon as possible. Firefox 16 is Mozilla's latest release, and is apparently extremely susceptible to malicious sites hacking their users complete browsing history.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Coca-Cola has unleashed a brilliant marketing campaign to celebrate the one year anniversary of their online Coca-Cola.FM radio in South America. In the latest issue of the popular Brazilian magazine, Capricho, the Coca-Cola advertisement literally turns the magazine into an iPhone amplifier. Attached on top of the real cover, the advert has two precisely placed flaps on the back page. Simply roll up the magazine, secure the flaps, then pop in your iPhone. Check out the video to see exactly h...

It can get pretty chaotic when you're gaming. When you're playing a fast-paced game like Black Ops, frustration, urgency, and confusion will lead to a sudden loss of control, i.e. a panic attack. There's an enemy at your six and you try to spin around, but it's too late—and that sudden rush of adrenaline will tear your controller to shreds. It's a step beyond mere button-mashing, because it's not really intentional—you just put a little more force on that thumbstick than needed. And now you'r...