
How To: Braid hair into fishtail pigtail braids
Fishtail braids can be a little tricky, but the look is worth the effort. Divide the hair into two sections. In order for the hairstyle to look neat from the


Fishtail braids can be a little tricky, but the look is worth the effort. Divide the hair into two sections. In order for the hairstyle to look neat from the

The seated hammer curl using resistance bands is used to target primarily the biceps, however because the wrist remains perpendicular to the ground rather than parallel, the forearm also gets a workout.

The seated row with resistance tubing is a great back exercise. The largest muscle in the back is scientifically known as the latissimus dorsi. You might see it referred to as the "lats" or "wings." The lats are used any time you pull something. For example, when you open a fridge or a car door, you are primarily using your lat muscles.

This exercise is a convenient alternative to the traditional barbell row. The main target is the upper back, or scientifically, the latissimus dorsi. The "lat" muscles function to pull things. So whenever you open a door, your lat muscles are allowing the movement to take place.

If you are ready to take your ab workouts to the next level, this exercise is for you! The plate crunch can be used as a progression to the traditional workout ball crunch. The range of motion is virtually the same. However, a bar plate is placed behind the head to increase difficulty.

The seated chest press can be done from any chair with a seat back. This exercise is great for shaping and strengthening the chest muscles. The chest is scientifically named the pectoralis. This muscle is used any time you push a chair up to the table, shut a car door, or push a shopping cart. There are two muscles that make up the pectoralis. They are the pectoralis major and minor. The pectoralis major is always the prime mover during chest exercises.

The use of heavy duty resistance bands (also referred to as "Powerlifting Bands") as a strength training aid has become increasingly popular over recent years. The bands are used for accommodating resistance; a technique that involves creating maximal tension throughout a full range of motion.

The seated leg extension is used to isolate the quadriceps muscles. The quadriceps muscles are located on the front of the thighs. As you might have guessed, there are four muscles that make up the quadriceps. Each muscle works in unison to extend the knee. In everyday life, the "quads" are used when you jump, walk, sit, kick, or stand.

If you are trying to work the hips and butt, this exercise is for you! The side kick mainly targets the gluteus muscles. Any movement away from the center of the body is known as "abduction."

The outer thigh lift is a great way to work the butt. Whenever leg abduction (movement away from the midline of the body) takes place, the gluteus muscles are involved. Instructions for the outer thigh lift are as follows:

The use of chains as a strength training aid has become increasingly popular over recent years. Chains are used for accommodating resistance; a technique that involves creating maximal tension throughout a full range of motion.

The rush to secure face masks and hand sanitizers in March left many Americans concerned for their safety. With an expected second wave this fall, consider stocking up on PPE now.

The race to the driverless finish line just got more challenging as Apple seems to have joined the pack. Friday, the global superpower secured a permit from the California Department of Motor Vehicles that allows them to test autonomous cars in the state.

Encryption is on everyone's mind these days, from the FBI's battles in court with Apple to WhatsApp's recent announcement of end-to-end encryption for their one billion users. Now you can add Signal, whistleblower Edward Snowden's favorite messaging app, back to that whirlwind discussion. Created by Open Whisper Systems, Signal is an encrypted messenger app that allows you to send text, images, video, and audio messages without the fear of prying eyes. They already have an Android and iOS app...
BeEF is an XSS-exploiting framework that lets you "hook" or gain control of victim web browsers. In this part of XSS exploitation, we will be working on finding an XSS-vulnerable website. We can simply do this by Google Dorking.
Apple released iOS 7.0.6 last week, an update to fix a serious security flaw that allowed hackers to not only capture sensitive user information such as bank statements and passwords, but also modify that same data on secure HTTPS sessions.
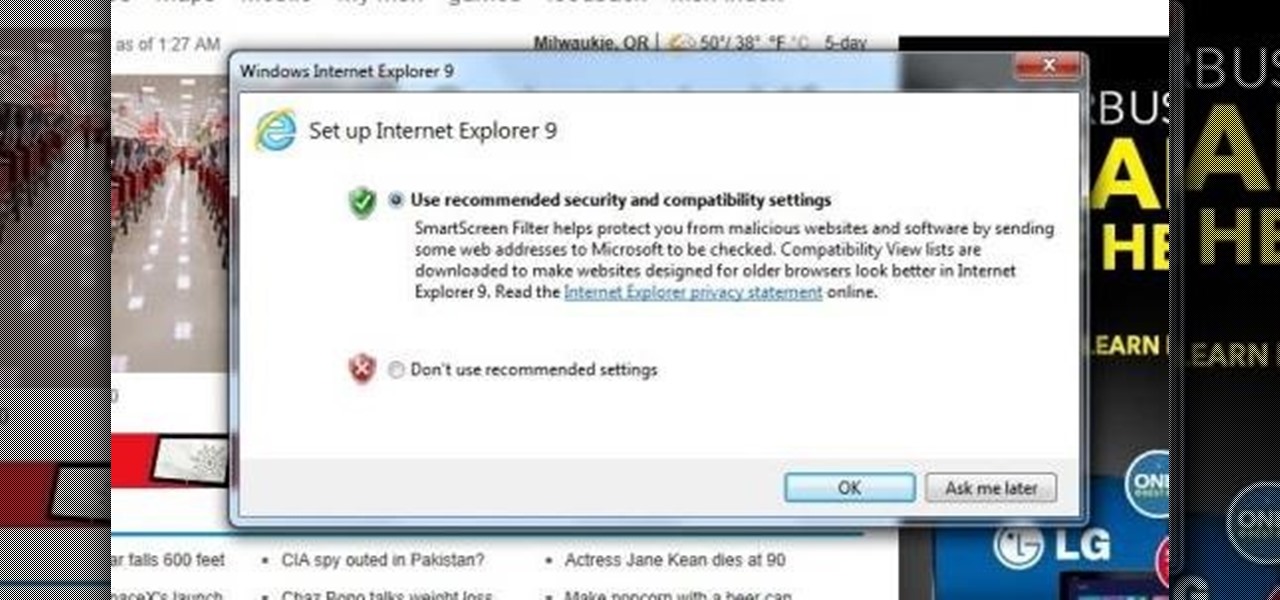
After you've updated Windows 7. Internet Explorer 9 is automatically installed. This is just a two step process of knowing it's been upgraded, and is ready to run and get you on the web.

When downloading any application on an Android device, you will always be prompted by the following... Whether it's Angry Birds, Shazaam, or Chrome, every application will ask for permissions. If you try and deny these permissions, it won't install, leaving you with no other option but to accept. So what can you do?

Along with the release of the new iPhone 5, Apple has introduced EarPods, which now replace the soon-to-be-defunct EarBuds. For three years, Apple has been testing the EarPods with users to try and find the most secure fitting, best sounding headphones for that price range. Loose Fit?
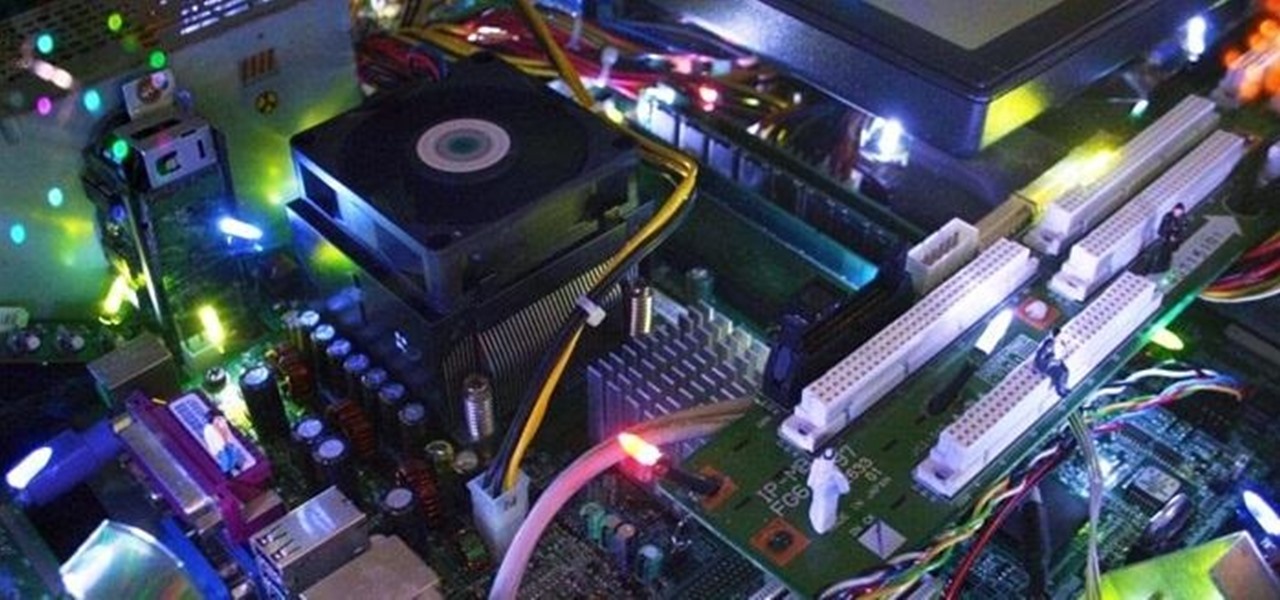
I have an interest in using recycled materials in sculptures, particularly circuit boards and other wasted electronic and mechanical components with which I put together sprawling cities lit with fairy lights. These cityscapes can conjure an image of a parallel society built from what we throw away. Utopian or dystopian, the ‘Electri-Cities’ remain a feast for the eyes and the mind. What makes them particularly intriguing is the population of tiny model railway people—they bring a host of nev...

Rain can make for an amazing photograph, but it can do disastrous things to your equipment. This super simple DIY cover from Purple Summit Photography will keep out the rain so you can capture beautiful shots no matter the weather, and it's made using things you probably have lying around. Photo by Jon Shave

Hotly contested video. The question remains, is the science behind the potato fire bonafide or bogus? We have yet to try it over here at WonderHowTo, and the comments thus far haven't indicated a solid verdict. Try it out and let us know! Is this a hoax? Or can you truly start a fire with a potato, salt and toothpaste?

Successfully Complete Your CNA Training Program You must finish your CNA (Certified Nurses Assistant) training program and must secure a CNA training certification in order for you to be qualified to apply for CNA state exam.

Get out of your everyday ponytail rut and try something new. Here our hair expert shows you how to do a sleek, chic ponytail that is perfect for a night out. Texture

We always have so many file formats in our computer, we use MS Word to view .doc files, MS Excel to view .xls files, Adobe Reader to view PDF files, image viewers to view all kinds of image formats, and browser to view html files. It seems we need to install many programs to view so many kinds of file formats, and we have met a lot of people who wonder how to solve such problems. So can we transfer those files into one uniform and secure format? The answer is definitely yes, we are here to in...

Watch this "Grease On Your Hands" video tutorial from the Washington Post to see how to check and charge car air conditioner properly.

Watch this "Grease On Your Hands" video tutorial from the Washington Post to see how to change your dead car battery properly.

Have you ever wanted to have the power to make things disappear? Ryan Oakes is going to show you how to obtain that power with this trick. You will need a cloth handkerchief, a shoelace, and three to four key rings. Sometimes we use materials that require adult supervision... like scissors so make sure you have friends and family around whenever you do magic tricks.

Are you ready to learn a magic trick that is sure to amaze your friends and family? Ryan Oakes is going to show you how to pass ropes right through your body. You will need two pieces of rope, about four feet long each, a pair of scissors, and white thread.

Watch this video from This Old House to learn how to reshingle a roof. Steps:

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.

Hello everyone and welcome to Part II - The Ultimate Guide: Diagnosing & Fixing Connection Issues. In this tutorial we will discuss more advanced methods that I took in order to fix our home network. I have also attached a link to download the FREE eBook - so feel free to download it to you can refer to this manual when you are experiencing connection issues. I would also like to note that the manual has been loaded onto a free server - it will remain on the server until people stop downloadi...

If you've gained entry into Google+, one of the first things you should do is adjust your Google account settings. Your settings will now look quite different, and you can adjust your notifications, password retrieval methods, and more. There are many settings that you may not have been aware of before.

Don't want one of your Facebook "friends" knowing your status updates? Prefer to keep a few of those "friends" out of your photo albums? Would you like to prevent a few "friends" from accessing your address?

Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as this list from the Wall Street Journal of the fifty most common passwords gleaned from the 2010 Gawker hack. If your password is on one of those lists, you need to change it. Right now.

In a recent arbitrage tip, we showed you the secret to making money fast by buying and selling the same thing over and over again on eBay. But there's one thing you need to know about the buying part—get the lowest price possible! This article aims to show you some of the best methods to making sure you're paying the lowest prices on eBay, so you're the best arbitrageur out there, with your profits higher than ever!

Why settle on just pork chops or ribs when you can string up the entire pig? Serious Eats posts an great slide show on roasting a whole pig, from materials to the process to the perfect pig roastin' sauce.

Transform childish pigtail braids into an evening updo. Take a braid and coil it around itself and for a tight look, secure it with a bobby pin. Do the same on the other side. Watch this video hairstyling tutorial and learn how to create a special updo with braids. Create a braided bun updo hairstyle.

So, if you are interested in buying copper luster, you should take some time to watch this video series. Sue Shea offers her expertise in the world of antique collecting. Sue shows you the different types and colors of copper luster. She also warns you of the signs of discoloration and restoration. Collect copper luster - Part 1 of 17.