
How To: A Self-Protection Guide
A Self-Protection Guide 1) You can help protect yourself from violent crimes.


A Self-Protection Guide 1) You can help protect yourself from violent crimes.

If you are a pet owner, going on vacation can be stressful. Usually, you need a friend or neighbor to come over everyday and feed your pets. However, by enslaving robots you can keep your pet happy and enjoy a stress-free holiday.

Spring has sprung, which means it's time to plant all those delicious vegetables and lucrative cash crops. If you are like me, every year you meticulously plan every aspect of your garden before dutifully neglecting it all summer. I decided enough was enough and built this simple automatic watering system.

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

A few days ago, CloudOn released their free mobile app that brought Microsoft Office directly to your Apple iPad. The cloud-based service effectively runs Office on their end, allowing you to use apps like Word and PowerPoint to edit your documents, which you would house in Dropbox. But after overwhelming demand, they removed the free app yesterday from the iTunes App Store.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

The widely used expression "free as a bird" intimates an enviable existence: delicate, yet mighty wings transporting to destinations no human could so breezily venture. But despite their fanciful, superhero ability, in truth, the avian race leads one of the most difficult existences in the animal kingdom. Yes, birds have existed for eons—they likely evolved from small dinosaurs of the Jurassic period—but for these creatures, life can be ruthless.

The days of trundling hoops, hopscotch and painted wooden rocking horses are long since past. The latest trend in toys? Biofeedback. Electroencephalography. A decade into the 21st century, the toy market is awash in products that incorporate functional neural sensors.

Update: New Trailer (7/9/10) In July of 2008, Fawaz Al-Matrouk, director of "To Rest In Peace", brought me on to shoot his USC graduate thesis film. Two years, 3 cameras, and over 15,000 miles later, the film is in its last week of post, having completed our final color correction at Light Iron Digital in Culver City yesterday.

As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

Find Your Base Material The base material for your doll can be anything 100% naturally made. Traditionally, sticks and twigs are used. Some people prefer to use corn husks, braided grass or similar items. The choice is yours, the only "rule" is that it be made of 100% natural materials. These sticks/twigs/husks/etc. will be shaped into a stick figure, one long piece for the body and one shorter (about 1/2 the length of the long one) for the arms.

By LukeLiu4434 Knowing how to pick a lock can come in handy if you ever lose your key to your house, bike, or anything else secured by a padlock. While it may sound difficult, picking a lock is a very basic skill and very doable. Here's how you can do it.

The video gives a step by step tutorial on how to replace the water pump, all belts and the shaft seals on a Porsche 944 S2.
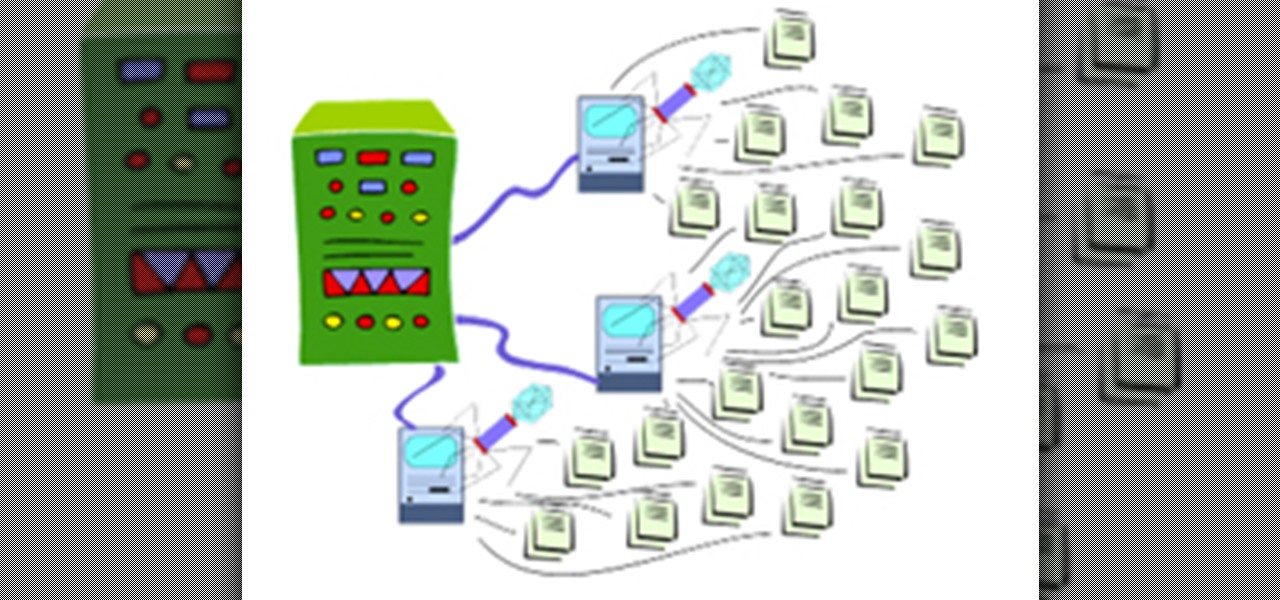
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

The community here on Null Byte has always been great and helpful in sharing their know-how, even before I took up admin duties in this World. I jumped at the chance of leading Null Byte because I enjoy teaching and informing people on all of the important need-to-know things out there, but more so than that—there is a deeper reason.

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.
+Nik Cubrilovic discovered last week that Facebook could track your web activities even after you logged out of your Facebook account. After some blatant denials from Facebook spokespeople, Facebook decided to fix the logout issue, but not before +Michael Arrington, on his new Uncrunched blog, made a concise post revealing Facebook's dishonesty: Facebook submitted a patent application for "tracking information about the activities of users of a social networking system while on another domain...

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

I've been unreasonably excited about Dungeon Defenders (NOT DUNGEON DEFENDER!) for almost a year. Playing it at PAX did nothing to damper that enthusiasm. I had a chance this week to speak with co-founder/development director Jeremy Stieglitz and marketing diretor Philip Asher from Gainesville, Florida based developer Trendy Entertainment to find out a little more about the game, and how it came together.

Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan horses in disguise. Their attempts even trick people into unknowingly becoming spammers themselves.

I've been dealing with emotional difficulty for many years. It started when I had surgery for the epilepsy I was dealing, and quite literally, dying with. Since the surgery on March 28, 1990 I have had no seizures, but I have had plenty of emotional difficulty. Along with that, surviving some traumatic events has added some emotional baggage...in other words struggling...along the way.

Who could resist a retro SCRABBLE board game for two bucks? Suereal definitely couldn't, especially with the challenge of totally revamping a board game into something genuine and creative. Craftster's Craft Challenge #51 last June was meant to bring life back to an old board game with the following expectations:

Kick Ass Game Review Part 1: Background & Voice Talent There are three parties involved in bringing you The Kick Ass Game:

Deadly natural disasters can happen at any moment— earthquakes, hurricanes, tsunamis, floods, fires and especially tornadoes. That's why you have to be prepared.