When it comes to making smartglasses that look more like regular eyeglasses and less like sci-fi helmets, Corning International might be among the suppliers to make it happen.

Honeywell recently completed successful testing of virtual window technology that enabled drivers to maneuver an otherwise windowless combat vehicle on rough terrain at speeds exceeding 35 miles per hour.

Augmented reality headset and software maker Meta Company announced today board member Joe Mikhail will serve as the company's chief revenue officer.

Mobile 3D scanning company Scandy has released a new app for devices on Google's Tango mobile AR platform that gives users the advanced 3D scanning capabilities.
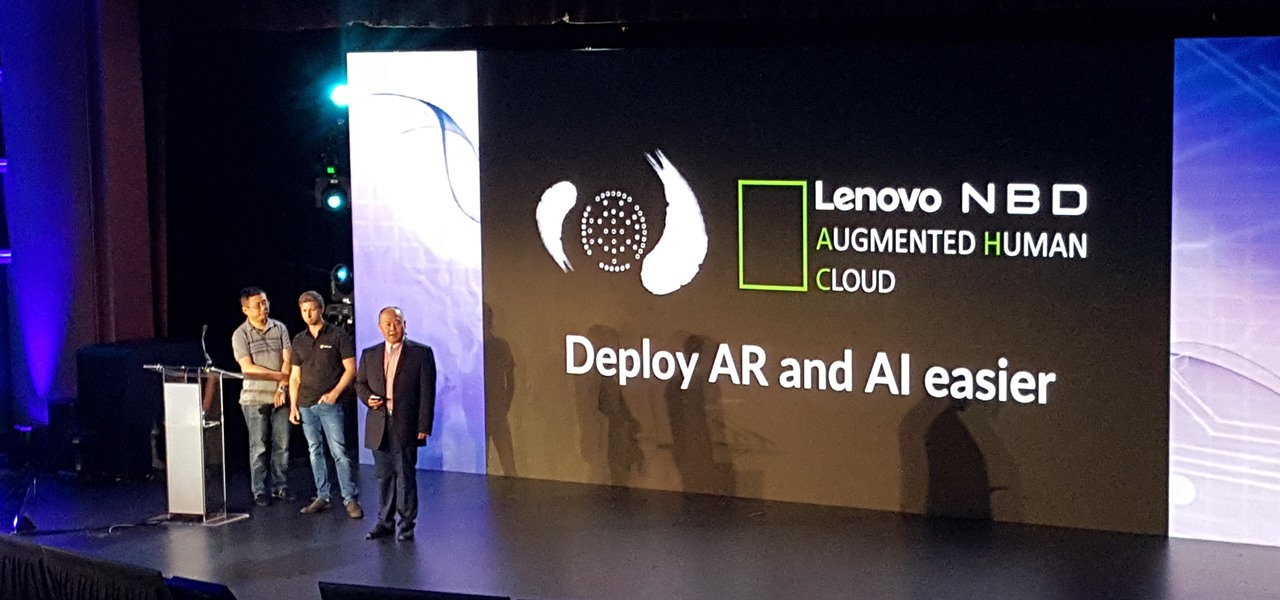
Lenovo has partnered with Wikitude to develop a cloud-based platform for delivering industrial-focused augmented reality content, the companies announced at the Augmented World Expo today in Santa Clara, California.

When it published its 2016-2017 catalog last year, Savannah College of Art and Design (SCAD) became the first college to leverage augmented reality technology for a college catalog.

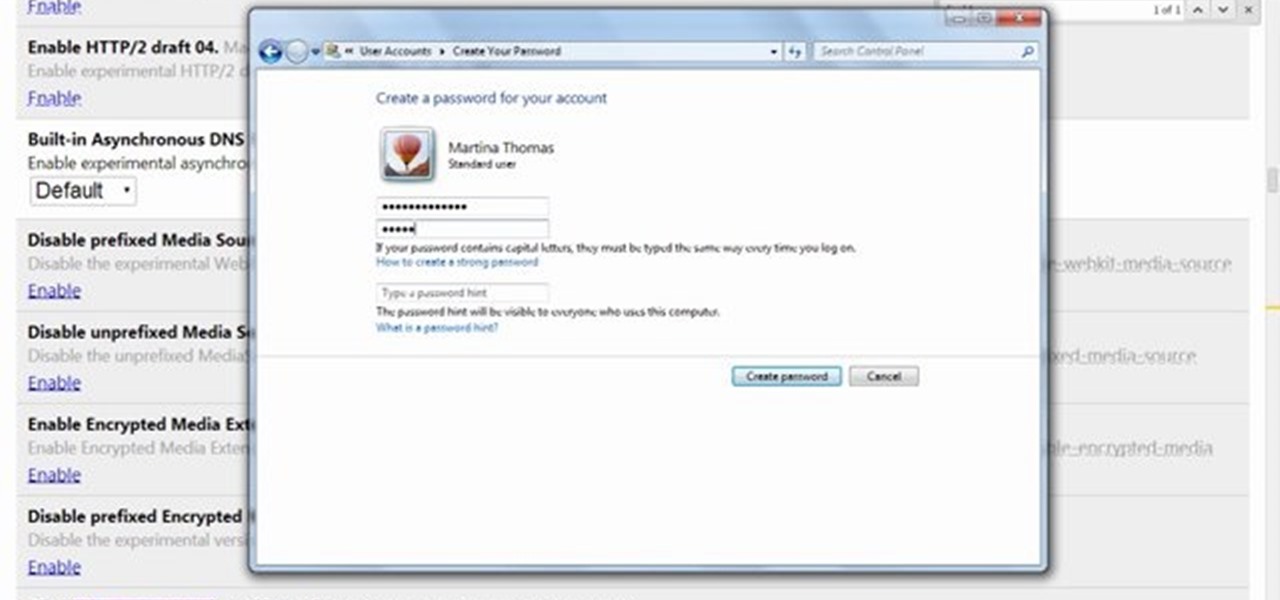
This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.

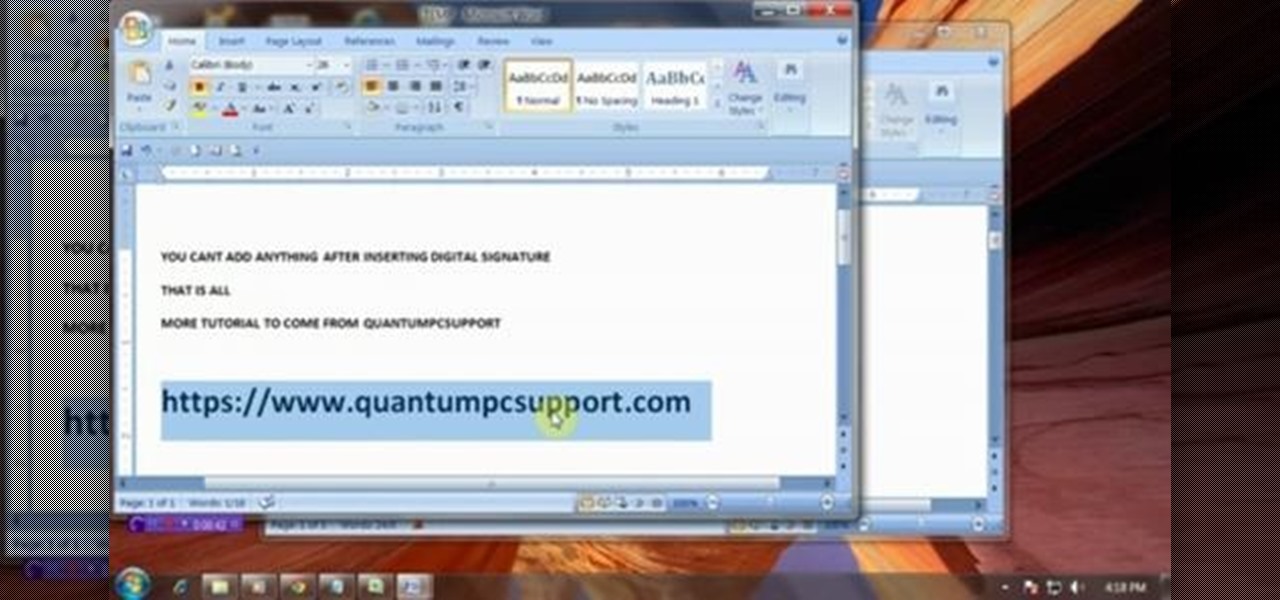
This video will guide you how to make digital signature in MS Word. The digital signature will allow to secure your document from tampering. When you set digital signature in your word text then you can't insert anything in the document anymore. You could add your image of signature with text.

If you want to protect your word doc from other, you can give it a password. When anybody wants to open, it will ask a password. This way your valuable document will be secured from unauthorized access.

In this video I did a very simple nail design that can be worn by women and teens on valentines day or just regularly too ! It is a very easy to create design and looks not only pretty but also immensely elegant!

Make sure your private documents are completely secure. This episode by Tinkernut deals with not only encrypting your files, but also hiding them in a hidden volume.

Ever been halfway to work or school and suddenly remembered you forgot to log off your computer? A lot of people are constantly logged in to email and social media accounts, so if you have a mischievous roommate or sibling, this situation could be disastrous. That's where TweetMyPC comes in—it's a free Windows application that lets you send commands to your computer just by tweeting. Image by Twittermania

Stay secure on public wireless networks by making your own FREE virtual private network (VPN). This tutorial shows you how to set up an OpenVPN server and connect to it from your laptop.

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.

For roasted chicken, you would expect it to have a nice, brown crispy skin. You would expect it to be moist inside with great flavors throughout. By using the rotisserie function (very common in France) on the Cuisinart Brick Oven. Check out the recipe for this delicious herb-roasted chicken from Chef Hubert Keller.

For this hijab style, start with hair completely covered and a large rectangular pashmina scarf. Pull the scarf over the head with one side hanging longer than the other. Pull the scarf tightly over the forehead to the nape of the neck and pin it together at the nape. Take the shorter end of the scarf and tuck it back toward the nape of the neck. Then pull the long end under the chin and up around the head until it is tight. Secure the end with a pin. Earrings can be worn through the scarf as...

The narrator starts by explaining what a squash book is. A squash is designed to keep photos, journalling or what ever you like. To start we require a 4x4 pattern paper and 3x3 chipboard. We then glue the chipboard onto the pattern paper. We then cut the corners of the pattern paper. We then fold the flap in and glue down. We repeat this to form another cover. Next we grab a 6x6 pattern paper, we then complete a series of folds. One diagonal, half horizontal and half vertical folds. We repeat...

To create almost any headband look, start by using a real human hair headband with extensions. Mostly, the extensions will come with an interchangeable headband for different colors. Now, start by pinning back the front crown area of your hair, if you have bangs you can leave them out of the hair that you are pinning back. Secure the crown of your hair with bobby pins. The headband with extensions should have three little combs. These will help secure the extension and the headband onto your ...

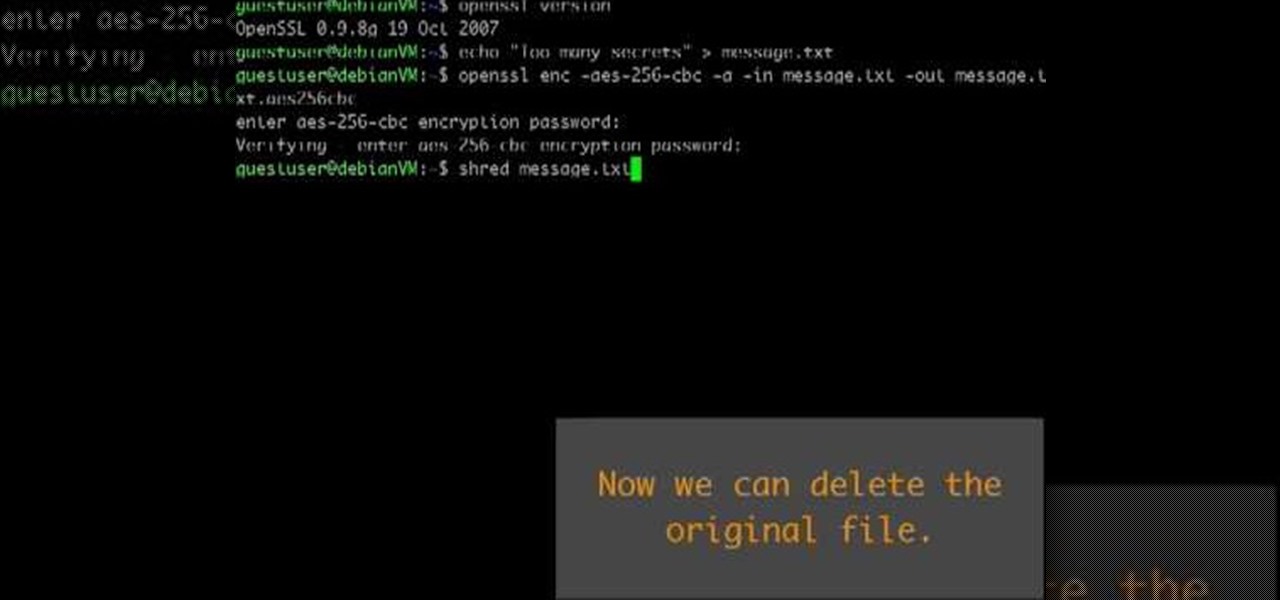
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...

Debra Hardy provides detailed instructions on how to make darling decorative Santa soy votive candles in this video. She first cuts the red felt into 6 3/4 inch by 2 inch strips for the Santa suit, wraps it around and adheres it to the bottom of the glass votive. Next, she secures a smaller strip of the white faux fur on top of the red felt also towards the bottom of the candle to create the bottom of Santa's jacket. Debra then instructs the viewer to cut a 6 3/4 inch by 1/4 inch black felt s...

Cocorais shows you how to style your hair into a Selena Gomez style up-do with short hair. Start by curling your hair, which is optional but it gives the hair shape and volume. Take your curled hair and sweep it to one side (opposite side of side-part if you have one), leaving a little hair on the other side to frame your face. Ignore any hanging hairs. Comb your hair into a ponytail, and tie it to one side. Gather your hair and tie it into a bun, using bobby-pins to secure it. For the rest o...

Crimp can be made easily and covered to the jewelry by using the following instructions. First purchase the proper supplies of crimping tool. This tool acts like pliers and is used by placing the bead in the appropriate slot at the tip and then squeeze the handle together. The multiple slotted tips are the key to the tool, and are needed to create a proper crimp. Then, select the proper crimp bead. The thin metal crimp beads come in a variety of materials and sizes. This will be used to secur...

Learn how to tie a perfect bow. To do a basic pony bow, place the gathered hair in the center of the ribbon and tie a single knot to secure it. Making two loops, cross one loop over the other and pull the loop on top through the hole you've created. Straighten out the ends and tighten so the two loops are on top and the two tails on bottom. Make a headband bow. Run the ribbon along the hairline, drawing the ends up on top of your head. Secure a knot and tie a bow. By tweaking the loops out a ...

This video teaches the viewer how to make a memo book with a paper bag. For this craft you will need two paper bags, memo paper, adhesive, ribbon, and scissors. To begin, you'll need to cut off the bottom of the bag and discard it. She explains where to make decorative edges on the bags before sewing them together or using hot glue. Fold and crease the open end down about one third of the way. Open and then fold a little farther down to allow room for the spine of your memo book. Repeat this ...

This video shows you how to use couplers for cake decoration using these steps: 1. Couplers usually come in two plastic pieces, a base and a ring. This system fits inside cake decorating bags or cones and allows you to use the same icing with different tips.

Worried about your baby or toddler either wrecking or wrecking themselves in your home? Baby proofing time! Make sure your house is safe and secure for your child when they start exploring their turf.

Save money on prom transportation by turning your parents’ station wagon into a one-of-a-kind limousine.

Seat belts save lives… but are you wearing yours the right way? Size up yours for a safe ride. You Will Need:

It’s never too late to clean up your credit record – and save yourself thousands of dollars in exorbitant interest rates in the process. Learn how to repair your credit with this guide from Howcast.

Moving is one of the top ten most stressful life experiences. Here’s how to pack it up without wanting to pack it in.

The modern knot is an updated version of the classic chignon. Here’s how to get the look. You Will Need:

Create a cute headband out of your own hair with this braiding trick. You Will Need:

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

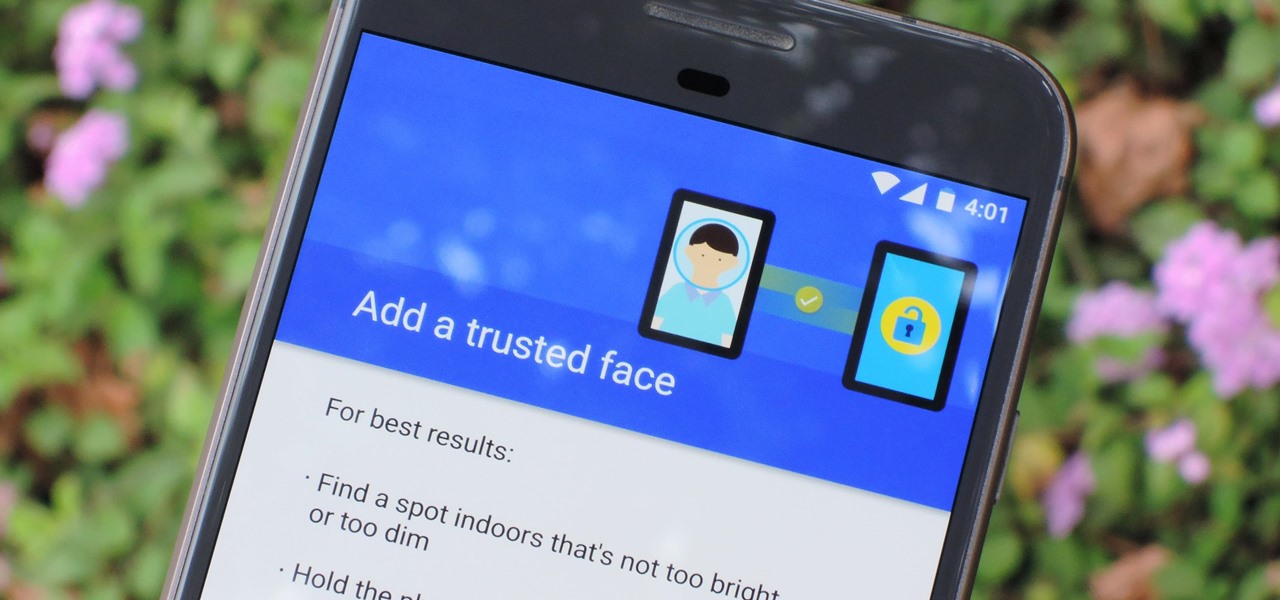
The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

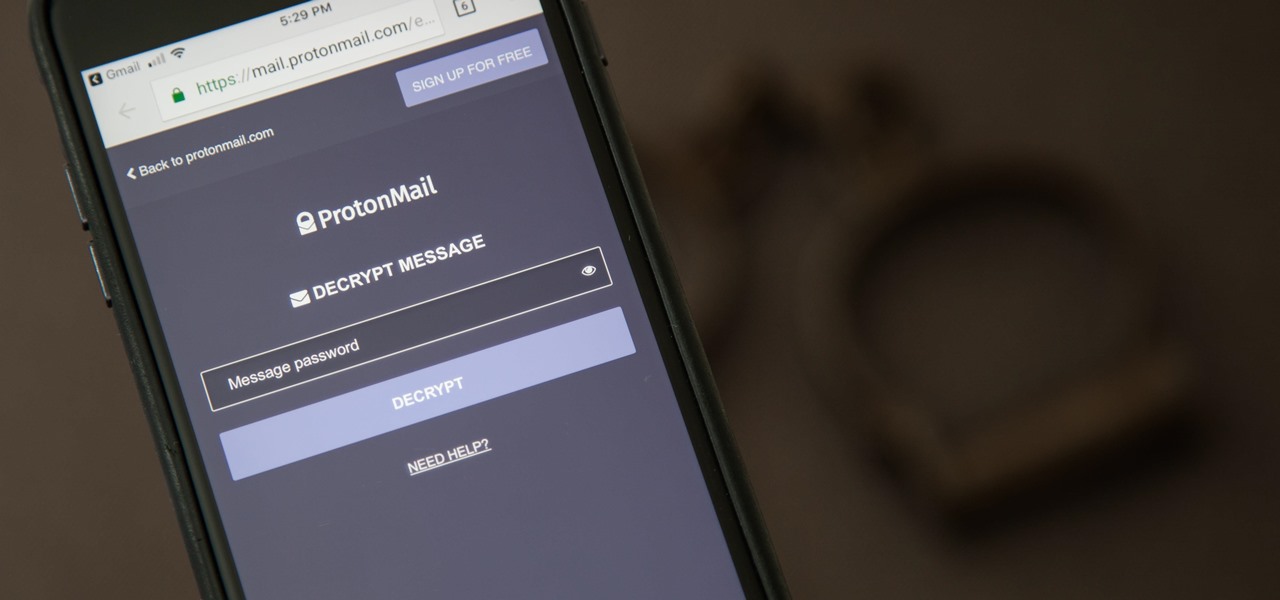
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or extensions to read or reply to the messages.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

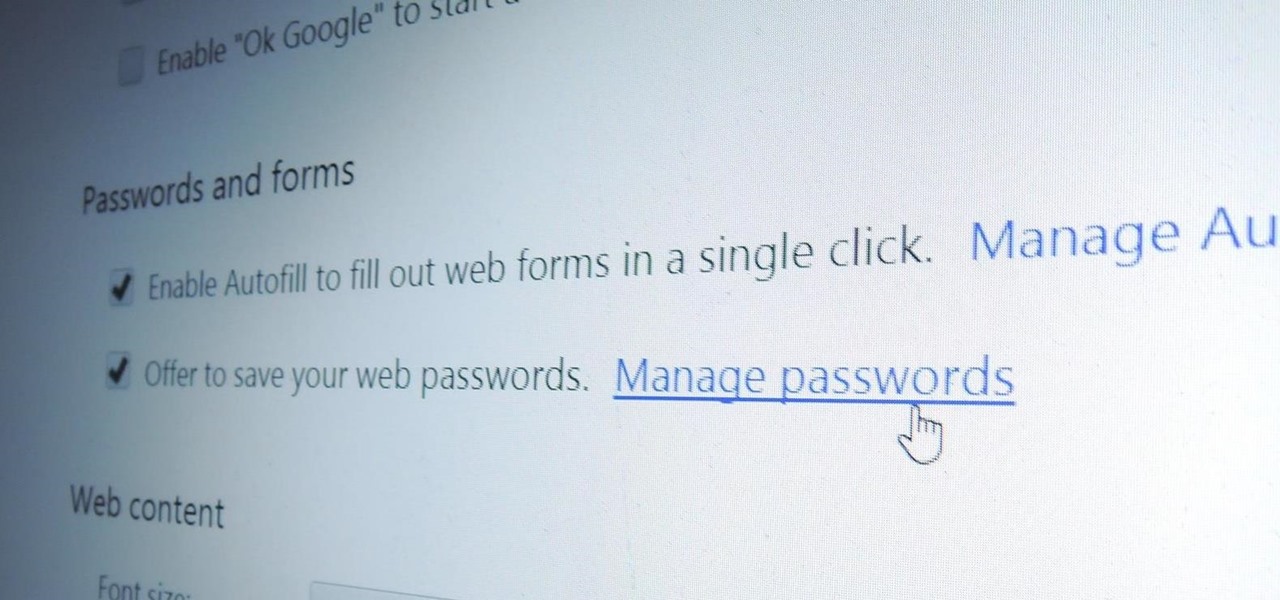
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

Over time, the dryer belt can become hard and brittle when the drum is turning loud noises such as squeaking, squealing or thumping noises can occur. Replacing the belt is an easy task for the do-it-yourselfer. All that’s required is a few simple tools. Here’s a step-by-step guide to help you install a new belt in your dryer.

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.