Supreme Deer Hunting is a Facebook game from MindJolt Games. Challenge your hunting skills in this classic hunting game. Earn points to upgrade your gear for better hunting. Realistic shooting with range, weapon accuracy, etc. Trophies for reaching certain goals.

Chipping and pitching are important golfing techniques that are vital to lowering scores and improving your overall golf game. Learn to pitch and chip like the pros from a professional golf instructor in this free golfing video.

Sometimes the save feature stops working for the old Super Nintendo games. But you can't fault them for that, everything has a limit and chances are you've drained the poor battery dry. Take a look at this instructional video and learn how to replace the SNES game battery. So before you throw away that game, check out this tutorial instead.

Check out this video tutorial from the Homemade Game Guru for a new idea in making the clean-up of pollution, emissions and litter more enjoyable for everyone. This video will take environmentalism and make it into a game anyone can make from home. So, see how to make a green environment spinner game.

Have you ever had the urge to throw a ball at someone, but knew you could never do it? Regardless if for merely a gag or out of frustration, we all have that someone we would love to use as target practice, but know fully well we can't purposely try to hurt another person. Well, we have the solution here...

Grandmaster Alexandra Kosteniuk teaches you in this chess video tutorial, how to pin your opponent down from the middle game of chess. This chess example is from the game Kosteniuk vs Gaeva in Verdun (1995). White plays and wins by checkmating with the queen and rook. To see how to master the chess move, just watch and see.

Check out this chess video tutorial Grandmaster Alexandra Kosteniuk on how to win the game. This game is taken from the Book of Stamma (1737). White plays and wins. You will see a good example of a smothered mate in the chess conundrum. Here, you will learn how to smothermate the king, which is just like checkmating, but smothering it, causing one sacrifice after another.

Grandmaster Alexandra Kosteniuk shows you how to play a real game of chess in this video tutorial, showing you how to checkmate the king with two variations in endgame/middle game chess. This example is from the game DesChapelles - De Labourdonnais, Paris 1836. White plays and wins the chess game by first playing the knight to check the king, with a sacrifice. Then the queen moves in for the endgame/middle game chess kill.

Play the new co-operative game Pandemic with tips from this how-to video (no, the game Pandemic has nothing to do with Valentines Day, but don't hearts and flowers always remind you of communicable diseases?).

Here is a video introduction and review of a strategy game, it's Ingenious (no, really--the game is called Ingenious). This Ingenious game is for one to four brains, or players (depending on how you prefer to see it).

This six-part 3ds Max video tutorial will guide you step by step through the process of exporting from 3D Studio Max into the award-winning, science-fiction, first-person shooter, computer game Crysis.

Bananagrams. Why would a wod game be called Bananagrams? Well, maybe because all of the game tiles are held inside a banana (no, not a real one). This gives you a brief description of how to play the Scrabble-style word game. Fun, high-speed, and competitive.

This three part tutorial covers everything from downloading the needed programs, to saving an iso image, to converting the image into a playable file, to moving it to your psp, to explaining the optional settings.

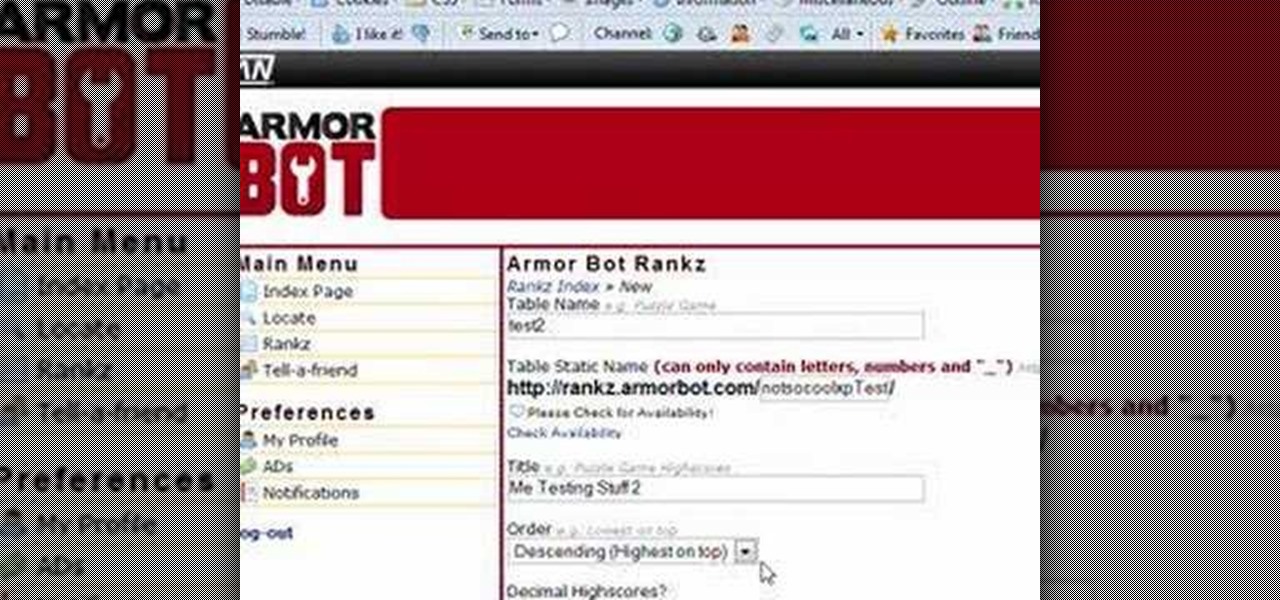
Learn how to create a high score table for Flash games using Armorbot.com Part 1 of 2 - How to Create a high score table for Flash games.

This tutorial shows you how to download and use old roll playing games like those from an NES OR SNES to learn languages online. Make sure to watch the second video or you won't get very far.

Board game enthusiast Scott Nicholson reviews a new game each week showing you the pieces and rules of play, as well and demonstrating the game with friends. This weeks game, Heroscape, is about buying and fighting with miniatures for kids and adults put out by Milton Bradley.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

After leveraging the well-known intellectual property of Rovio's Angry Birds for its first game for the Magic Leap One, Resolution Games is singing a new song with a familiar refrain for its next game for the augmented reality headset.

Norway-based production tools company Vizrt is putting the real into augmented reality with its broadcast AR solution that's designed to keep sports fans (and other audiences) watching.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

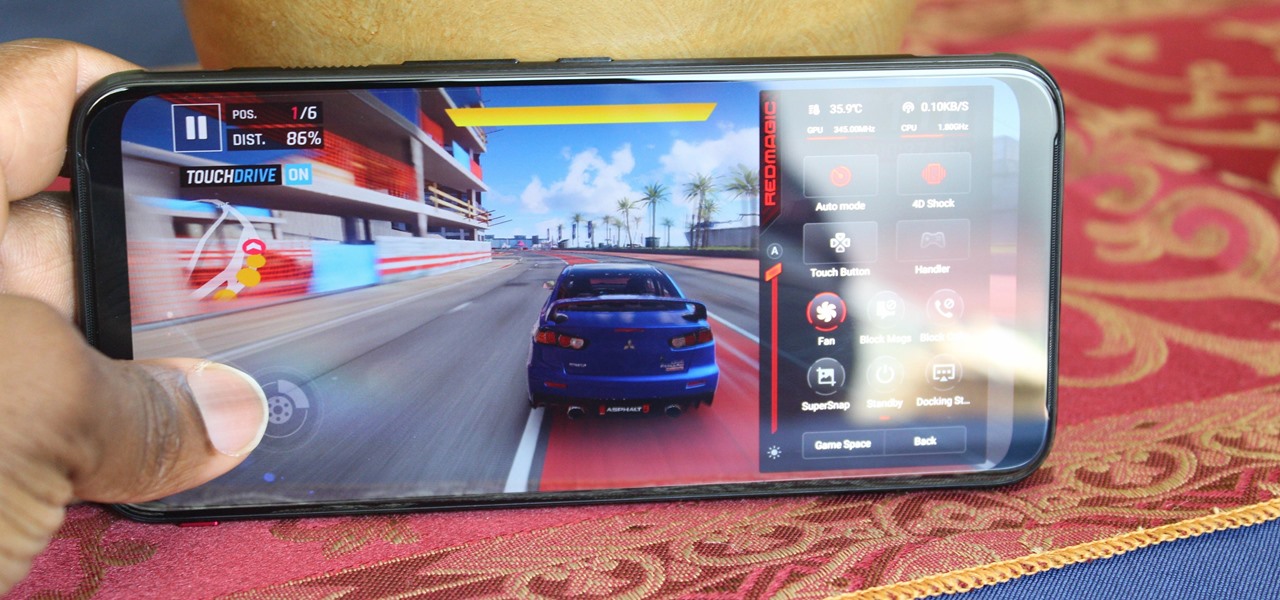
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

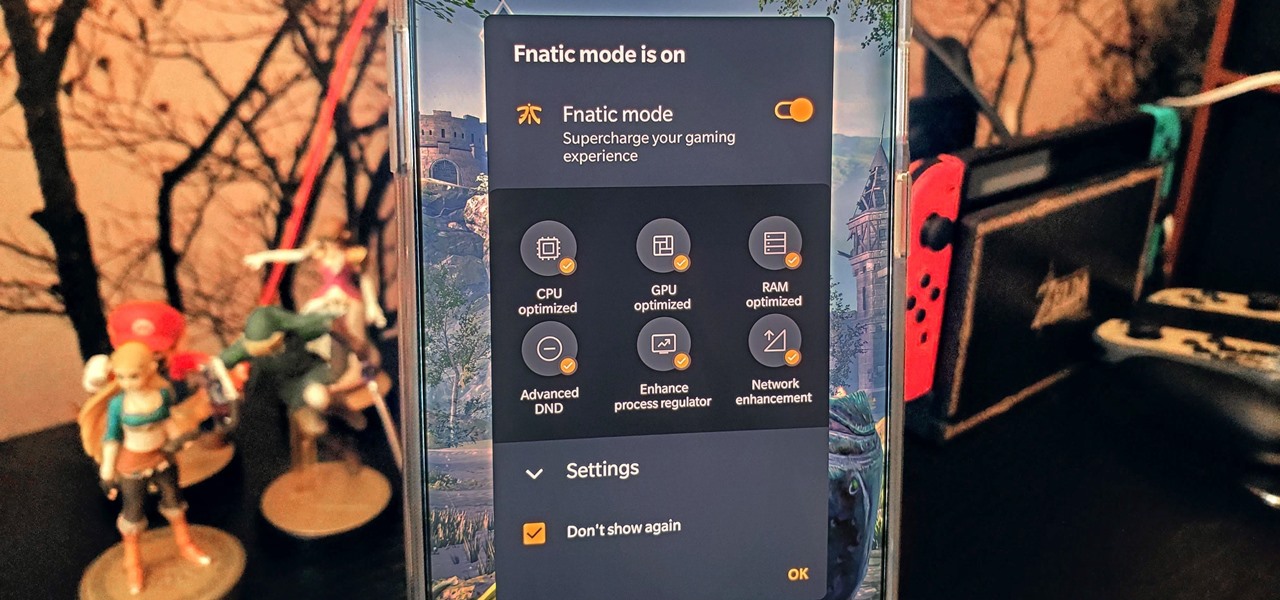
The OnePlus 7 Pro is an outright beast. From the highly rated display with minimal bezels to the 90 Hz refresh rate, there's no denying this phone is great for gaming. Although not explicitly marketed as a gaming phone, it seems OnePlus unintentionally created one by cramming in great specs and game-friendly software features like Fnatic Mode.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

While a release date for Harry Potter: Wizards Unite has not yet materialized, co-developers Niantic and WB Games have finally released gameplay footage and an in-depth game description to whet the appetites of eager Harry Potter fans.

The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one of the biggest problems can be fixed.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

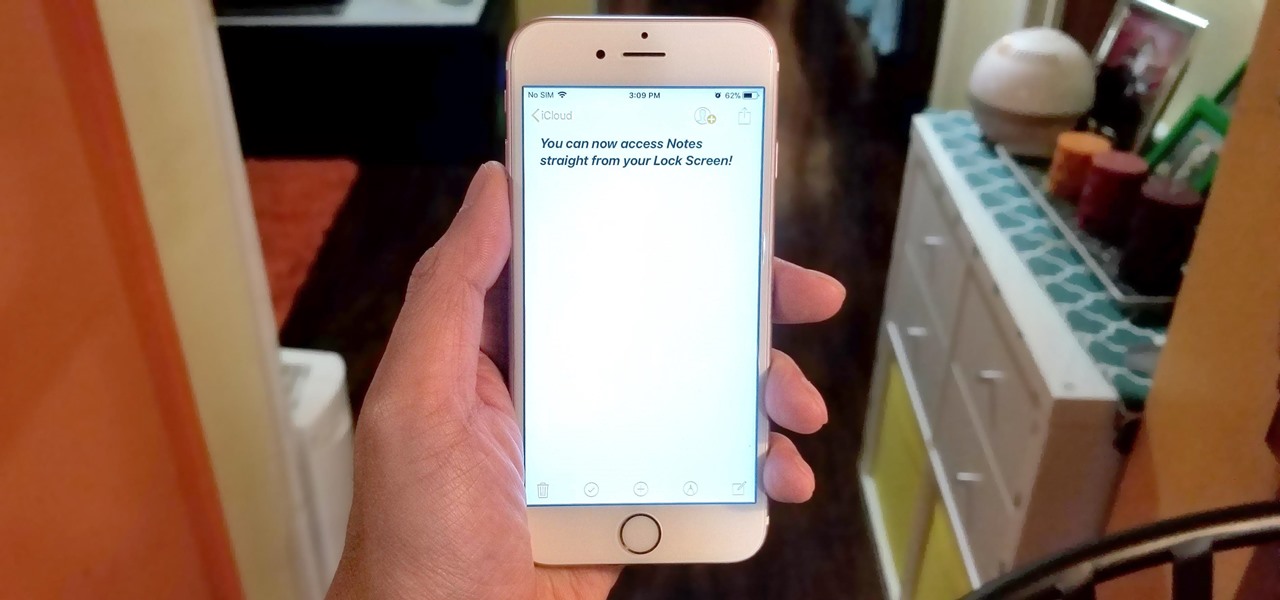
All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

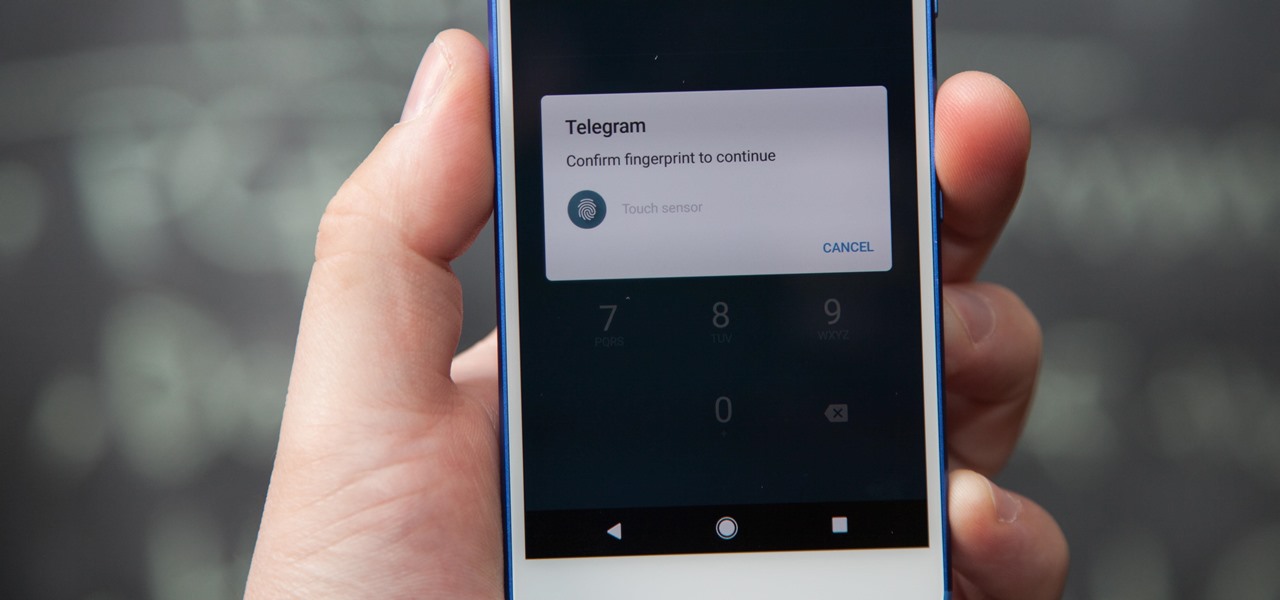
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

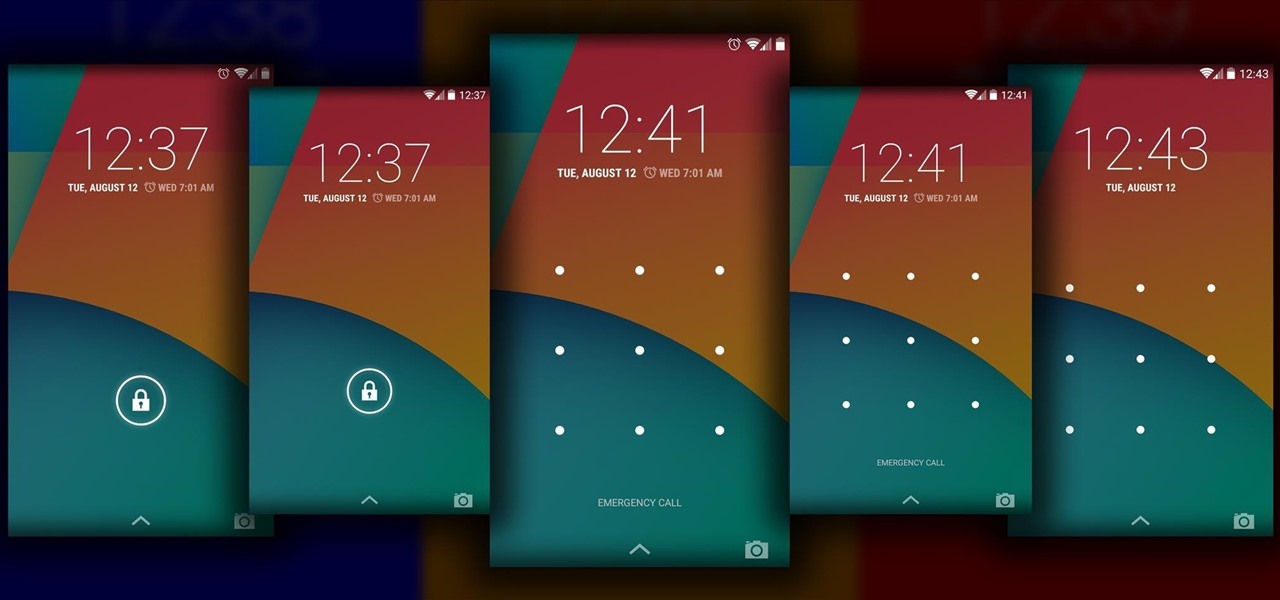
The Android lock screen interface is an integral part of our everyday use. For those of us who use lock screen security, it functions as a barrier between the sensitive data contained within our smartphones and potential outside access. Even if you don't use a pattern or PIN to secure your phone, you still interact with the lock screen every time you go to use it.