This video shows the viewer how to secure crimp beads using both crimping pliers and chain-nose pliers for the purpose of jewelry making. The video uses two millimeter crimp beads, beading wire, and both sets of pliers to demonstrate the technique. To crimp using the crimping pliers, the viewer will utilize both notches of the pliers to crimp the bead onto the wire. In order to crimp using the chain-nose pliers, one must simply flatten the bead onto the wire. Crimping is a good method to secu...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

The Lab Rats, Andy Walker and Sean Carruthers, explain Media Access Control (MAC) addresses. Filtering MAC addresses allow you to very specifically control access to your wireless network.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

Julia, AKA Hairbeauty4you, gives detailed instructions on how to do a quick half up-do with a twist in under 10 minutes. She notes that this style is best for medium to long length hair. Julia starts with straight hair, then sections off the top part and clips temporarily. She then separates another section on either side of the top part- from the ear to the clipped section- and pulls it back into a high pony tail and repeats identically on the other side, securing each with clear rubber band...

Do you need to lock the door but don't have the keys? This may happen if you are sharing your keys with someone else, staying at a friend's house, or for a variety of other reasons. Check out this video for a sneaky way to secure that door tight without even sticking a key in the lock.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

It can get pretty chaotic when you're gaming. When you're playing a fast-paced game like Black Ops, frustration, urgency, and confusion will lead to a sudden loss of control, i.e. a panic attack. There's an enemy at your six and you try to spin around, but it's too late—and that sudden rush of adrenaline will tear your controller to shreds. It's a step beyond mere button-mashing, because it's not really intentional—you just put a little more force on that thumbstick than needed. And now you'r...

You don't want anybody to have access to your cell phone. Nobody. Well, instead of the standard unlock mechanism, the one anybody can unlock your cell phone with, the Motorola DROID, and Android enable mobile device, allows you to create your own unlock pattern, secret to anyone else, which wakes it from sleep mode. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up a secure lock on a Motorola DROID cell phone.

In order to begin, you will need the following: Three hair tiesBobby pinsHair spray or spray gelRat tail combHair net

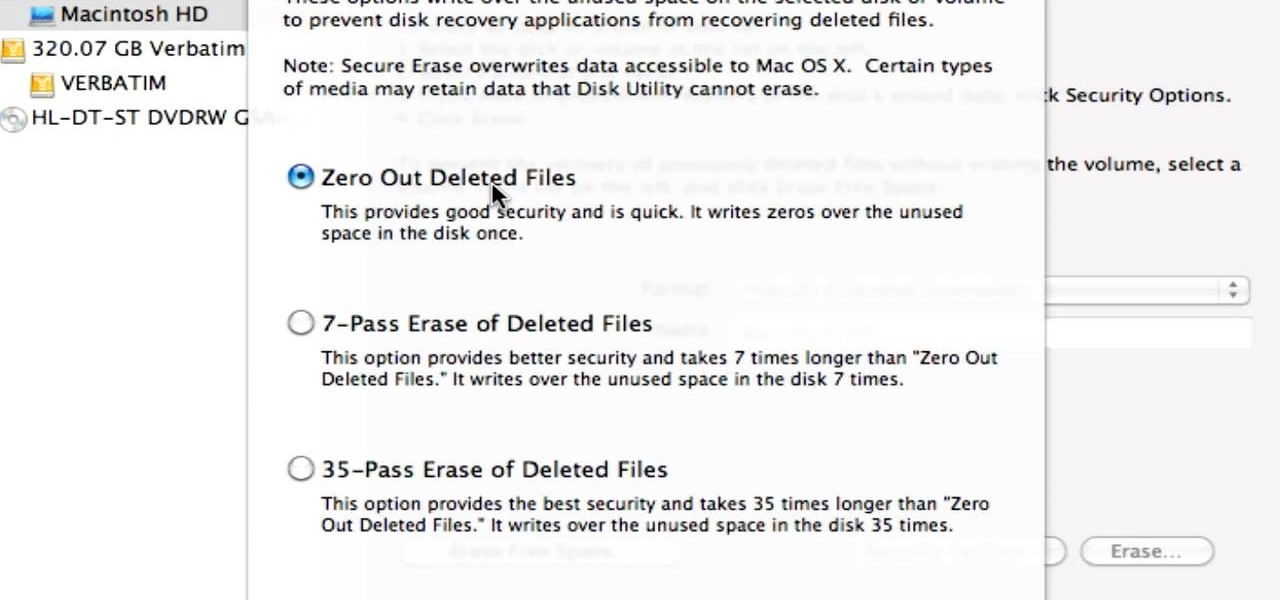
Did you know that even after you've emptied your Mac's trash can, the data still has not been permanently removed from your system? Anyone who knew where to look could easily unearth this data. You can prevent this by using the secure empty trash option on your Mac. Whenever you put something in the trash, instead of pressing delete, go into 'finder' up top and press 'secure empty trash'. What this will do is replace the data that is left behind on your hard drive with random ones and zeros. ...

This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

In last week's guide, we covered the best places to purchase digital copies of computer games online. This week we'll cover another type of downloadable content: those available for video game consoles. Every major console out today either has or plans to have a DLC platform, but which one is the best? If you don't like leaving your house and want to play console video games, which console should you get? Below I will break down what the online marketplace offers so you can decide which conso...

Notthecoolmom gives a craft lesson on how to make a diaper wreath for a baby shower. To make the wreath you will need the following materials: a package of 56 size 1 diapers (preferably with a design of some kind), a Styrofoam wreath, a spool of ribbon, and rubber bands (optional). Start by laying your diapers around the wreath to get an idea of spacing. Be careful not to make your wreath too full. You don't have to use all of the diapers it depends on the size of your wreath. To put the diap...

This video shows you how to use an exercise band to do bicep curls, triceps extensions and shoulder raises along with some fun extensions of these basic exercises. When doing the bicep curl with the band it is very important to ensure that the band is firmly secured under your shoe, so that it does not slip forwards and snap. Once the band is secure you must curl the arms up towards the shoulders, keeping your elbows bent and close to your sides. The arms are still working in a negative resis...

Ever had a spoke break on your bike wheel? Don't throw the wheel away! Repairing a spoke only takes a few tools and some patience. You will need, at a minimum: a freewheel tool (used to remove the part of the wheel that engages the bike chain), a wrench, and a screwdriver. First, remove the tire and inner tube from the wheel. Next, remove any parts of the broken spoke that are accessible from the underside of the wheel rim. If the spoke is attached to the side of the wheel where the freewheel...

One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. It's like having a safe built right into your smartphone, and it couldn't be easier to set up.

When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

TrueCrypt is a free open-source program for encrypting data and it's excellent for securing hard drives, but it also has the ability to hide a secret operating system inside another operating system. CNET shows you how this "insider secret" operating system is created. This operating system will be impossible to prove to people like the Feds.

If your pet has recently had surgery or been ill, they may need to wear a medical collar. A medical e-collar or a cone will prevent your pet from chewing or licking an area of their body that they shouldn't be touching. In this video from Dr. Lauren, you will learn where to get an e-collar and how to secure it to their head so that they stay safe and happy.

In this video tutorial from Get Connected TV, hosts AJ Vickery and Mike Agerbo will show you how to safely move your iPod files to your home pc, for back up purposes, just in case something were to happen to your iTunes account or your iPod is damaged, or music directory accidentally deleted. The program they introduce in this video is called iPod-Rip, and they lead you through the steps necessary to back up your iPod files safely and easily, without damaging or deleting your files.

Tinkernut presents the Bluetooth headset hack! This video shows one of the vulnerabilities of some bluetooth headsets. To prevent this vulnerability, it's best to invest a little more money into a more secure headset and making sure your headset is turned off when not in use. You can find all of the links and scripts used in this video, as well as find answers to questions you may have at the link below:

This how-to video shows you how to open your above ground pool after it has sat there all winter. Make sure to remove water on top of the cover, any debris, and tubing securing the cover. Open your above ground pool and get it ready for summer. Check the skimmer, filter, and pump before allowing anyone in. Don't forget to install the diving board properly.

This how-to video shows you how to open your in-ground pool after it has sat there all winter. Make sure to remove water on top of the cover, any debris, and tubing securing the cover. Open your in ground pool and get it ready for summer. Check the skimmer, filter, and pump before allowing anyone in. Don't forget to install the diving board properly.

This how to video show you how to keep your shoe from sliding up and down your heel while running. This will making those longs runs less painful.

Did you know that someone could be watching what you're doing on your computer via another computer? That's right - if they are using VNC or Apple Remote Desktop software they can moniter what you're doing and even control your computer?

2 Mins To Show You How To Tie The Ultimate Secure Knot That You WONT BE ABLE TO UNDO... After Its Tied You Have To Cut It To Get It Off...

In this tutorial, we learn how to make your home safe and secure with tips from Lowe's. You should do a safety check on your house at least once a year. Start with the entryway, making sure you have an insulated wood door in the doorway. Make sure there is a lock and a deadbolt lock on the door as well. Once inside, make sure you have timers to control your lighting, so it can come on even when you're not at home to detract any robbers. In the garage, make sure you have an electronic door ope...

In this video, we learn how to do some easy hairstyle for school. To do an easy bun, take a hair tie and put it in the hair in a side twist bun. Let some of the hair stick out, then take bobby pins and stick them in the bun to secure it, then you're done! The next look requires you to take your bangs and braid them together. After this, pull the braid behind your head and secure it with a bobby pin. The next look requires you to braid a section on the side of your hair, then put it into a pon...

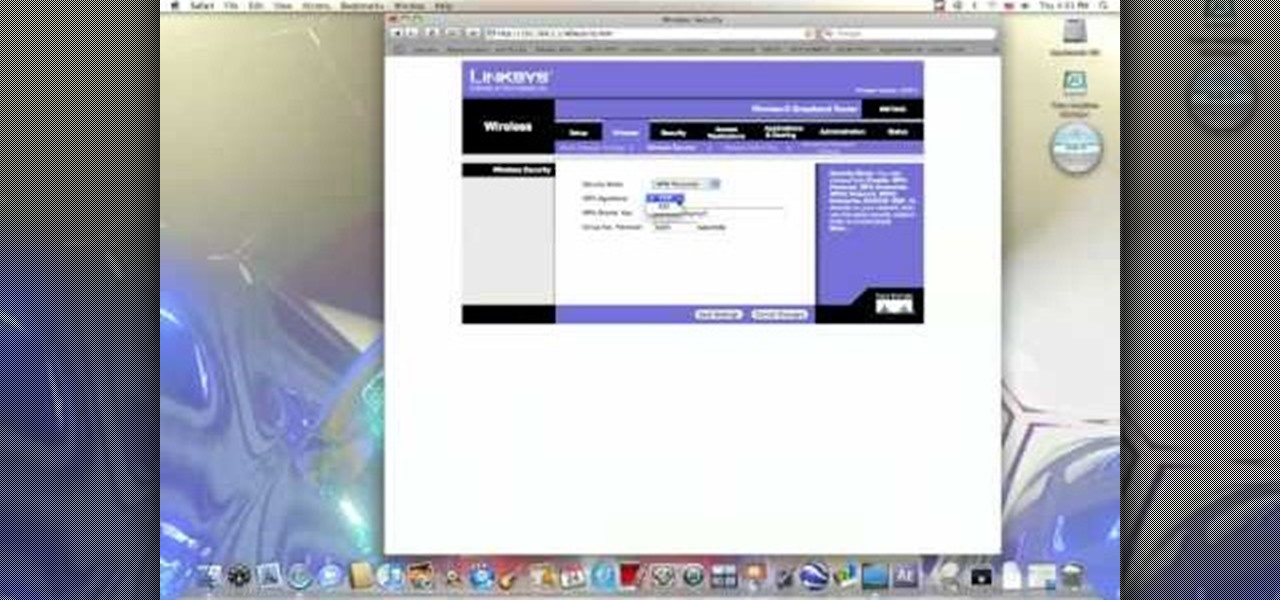
In this video from benjamoon we learn how to secure a linksys wifi network from a Mac. First type in your IP address in your browser bar which is 192.168.1.1 then press enter. If it asks for a password it is admin. Click on Wireless and here you can edit your name and who can access your wifi network. Under wireless security, go to WPA personal from the drop down menu. When you make your password, make it very challenging. He recommends just banging your hand against the keyboard, as long as ...

This video is a tutorial on how to make a diaper cake. The cake is not edible. To begin, you will need a pack of diapers and rubber bands. Roll up the diapers from the waist down and secure them with the rubber bands. Put several rubber bands around a bottle of wine and secure the diapers in tiers around the bottle of wine. Cover each tier with tissue paper before adding the next one. Wrap each tier in blankets. Top off the cake with a can of formula wrapped in a decorate blanket. At this poi...

Have some files you don’t want anyone to see? Or maybe it’s just been a while since you’ve emptied your trash bin. The trash bin function is not a permanent delete but you can erase files off your Mac with this tutorial.

They say it is always darkest before the dawn. If that's the case, then perhaps there's a light ahead for Magic Leap after more unfavorable news in the form of executive departures.

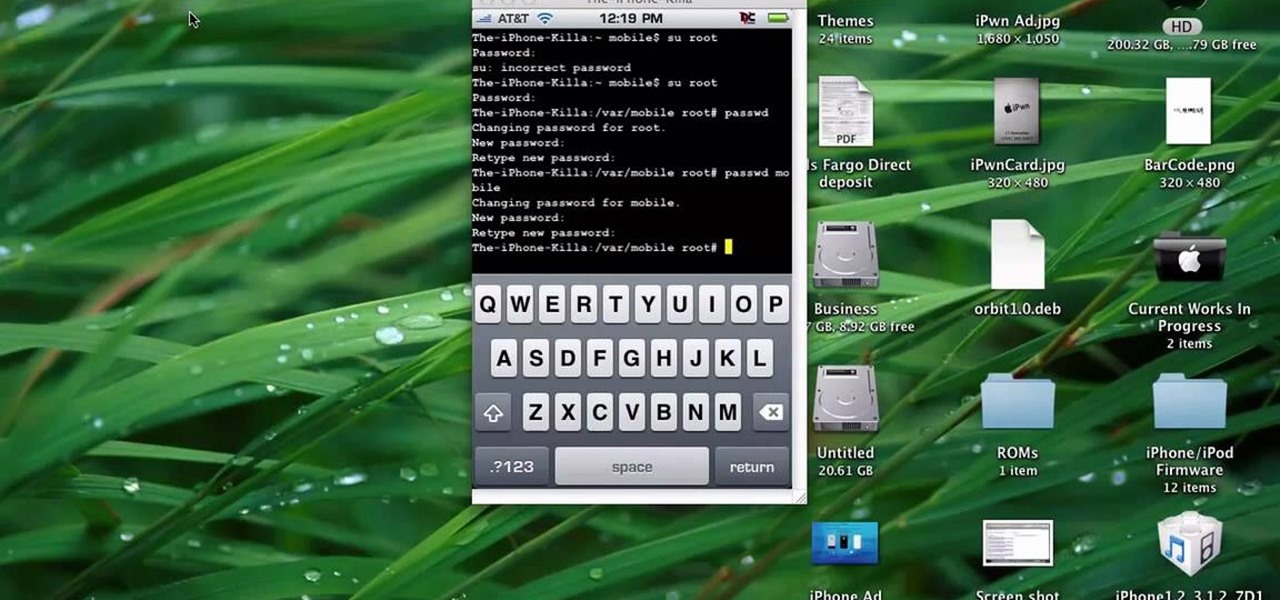
A massive leak appeared the web today, and it's got some huge security implications for every iPhone on the market. On the plus side, it also has some potential for enabling deep-level modifications and jailbreak tweaks.

Got some valuables that need to be protected in your Minecraft world? Watch this video to learn how to build a seriously secure, heavy duty, combination lock. This video will show you what materials to use to make this combination lock.