This is a great, sophisticated hairstyle you can achieve without using any heat (which can often damage your hair). It's an easy and useful secret - just braid your wet hair in the evening, secure in place and then undo it all in the morning!

Deadbolts are a security lock which are usually put on exterior doors. Many saftey experts recommend increasing the strength of your home deadbolt lock. This quick tutorial teaches you how to make your deadbolt extra secure and increase the safety of your house.

Need some help figuring out how to put a password on your wireless router? This home-computing how-to from the folks at CNET TV will teach you everything you'll need to know to do just that. For detailed information, and to get started protecting your own wireless network helpful video guide.

Protect your email account from would-be hackers and crackers with this free video tutorial from the folks at MacMost. If you have a Gmail, HotMail, Yahoo! Mail or other web-based email account, this video is much recommended. For more information, and to secure your own online free email account, watch this helpful guide.

Learn how to tie a Tack Knot - a secure way of attaching a rope to a fixed object such that it won't come undone even if shaken and flogged. This is a fine knot for camping, climbing, sailing or Boy Scout training.

Learn how to tie an Anchor Hitch (also known as a Bucket Hitch) - A very secure means of attaching a rope to an anchor or any other object that you can't afford to loose (like a bucket down a well, I suppose - thus the alternate name). I actually do use this hitch for temporary anchor attachment (preferring to permanently splice instead) as well as for my bucket lanyards when washing down my boat's deck.

Learn how to tie a Draw or Thief Hitch - a means of securing a rope with two standing ends - one end is load bearing, and the other can be pulled to release the knot. I used this knot extensively for raising the mast on my first trailor-sailor - Tie this above the spreaders, stand the mast up, then pull on the release line to untie it without having to climb aloft. This knot can be used in sailing, boating, general use, camping and bondage.

This video shows you how to tie a Thief Knot. This knot looks a Reef Knot to the casual observer and so can be used to determine if a thief is tampering with your belongings bag - secure it with a Thief Knot, and if you find it re-tied with a Reef Knot, you know someone has been messing with your stuff. This is used in sailing, boating, general use, camping and bondage.

Jared of the TechCentric crew gives you the lowdown on the basics of keeping your VoIP conversations secure and, on the other side of things, how to use the Cain VoIP sniffing application. For detailed instructions on keeping your VoIP conversations private, watch this hacking how-to.

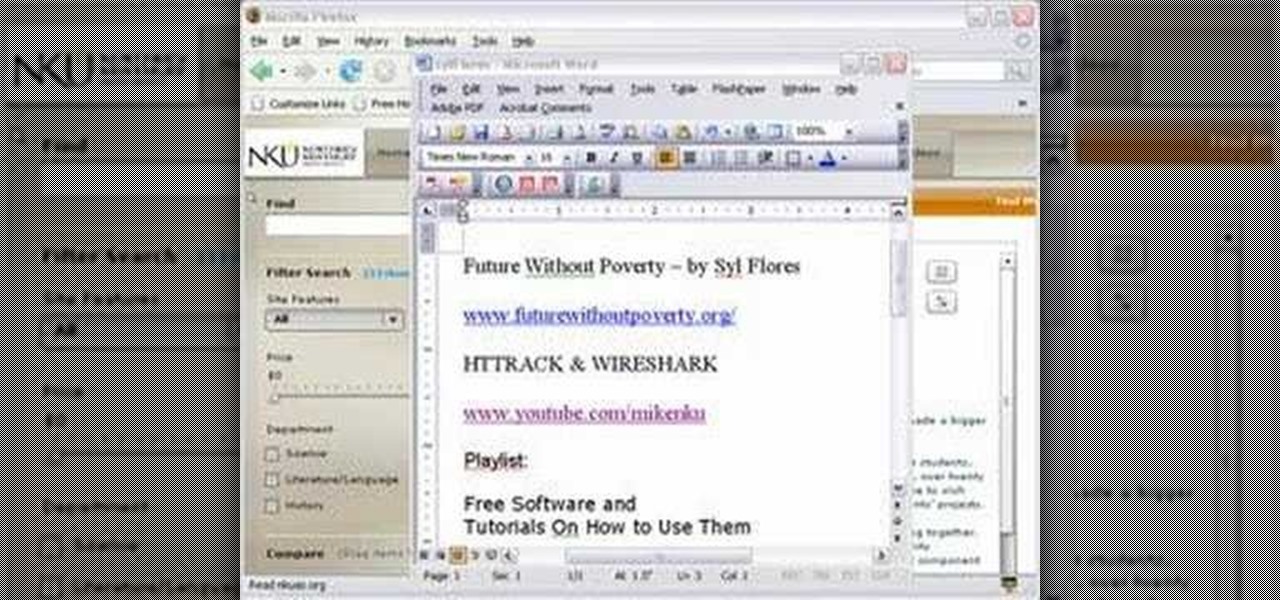
Mike Lively of Northern Kentucky Universtiy demonstrates how to grab a website's resources for reconstruction in Flex using HTTRACK and Wireshark. This tutorial is especially helpful for sites you want to grab that think they are very locked down and secure. All with the free softwares HTTRACK and Wireshark.

Battlestations: Midway for the XBox 360 takes place at the very start of America's involvement in World War II, beginning with Pearl Harbor. Take a look at this instructional video and learn how to win the Battle of Tulagi and secure the strategic islands with these tips from G4TV.

Watch this quick instructional cinematography video that shows how to balance a Canon XL2 professional HD digital camera on a GlideCam 4000 Pro. Learn how to secure the camera using this handheld camcorder stabilizer to prevent unwanted swaying, shoot fluid traveling shots, and produce professional works.

If you can find people who speak English in China, you'll probably get where you want to go faster. Memorize this basic Chinese phrase and feel a lot more secure once you get to China!

This knot is common in the climbing world. We use it to secure two ropes together. Often used to form a loop on a prussik (cordalette) to construct an anchor. Can also be used to connect two ropes to rappel. This knot has many applications in the real world not just climbing.

Materials: Scrap fabric, elastic thread, cardboard, scissors, cellophane tape, and other bits and bobs ie feathers, buttons

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

Need to secure your track to the road bed for your model railroad? Well, this video tutorial will show you how to do it, not to mention show you how to weather your flex track.

We continue to field stories underscoring the strong trends of Investment in augmented reality in various sectors. This week, one company strengthens their offerings to the enterprise sector, while two other companies capitalize on the promise presented by augmented reality to consumers – specifically, in gaming.

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.

Looking a for a secure and secretive entryway to your Minecraft base? Check out this video to learn a great design that uses pistons to make a trap door. With this trap door you can control who gets into your base, and who gets sent to the lava pit.

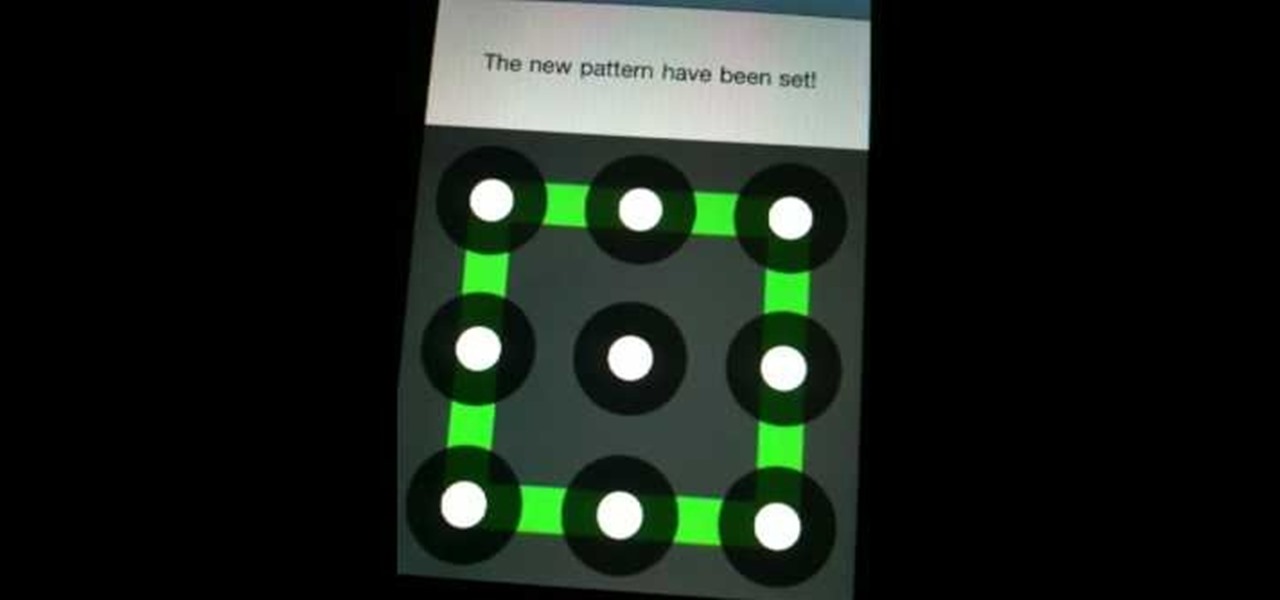
Concerned about unwanted eyes setting upon the information in your Android phone? This video will show you how to turn on the screen lock feature of your Android smartphone. Keep the information on your Android device to yourself with a lock screen.

Check out this Minecraft building guide to learn how to build a machine gun that can fire 25 arrows a second. If you need to secure your home from mobs, or you just want to have an awesome machine gun, watch this video.

iPhone and Android both have a lot of great features. Enjoy the best of both worlds when you install Android lock on your iPhone. This is a great way to secure your iPhone. Use Android lock to get an extra layer of security.

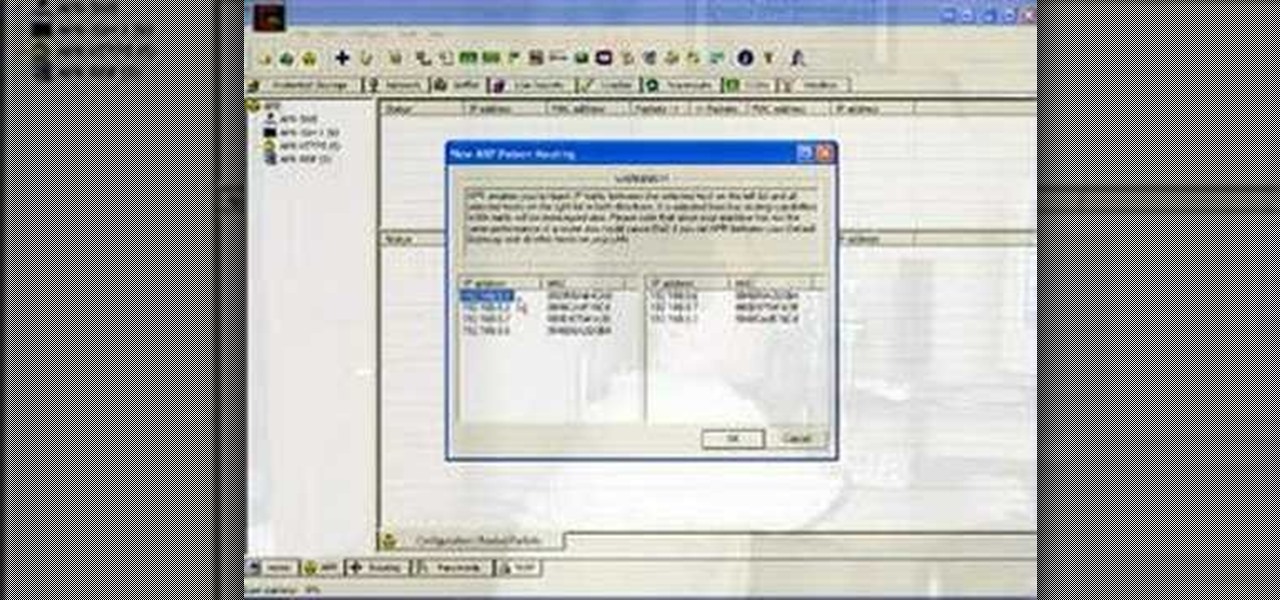
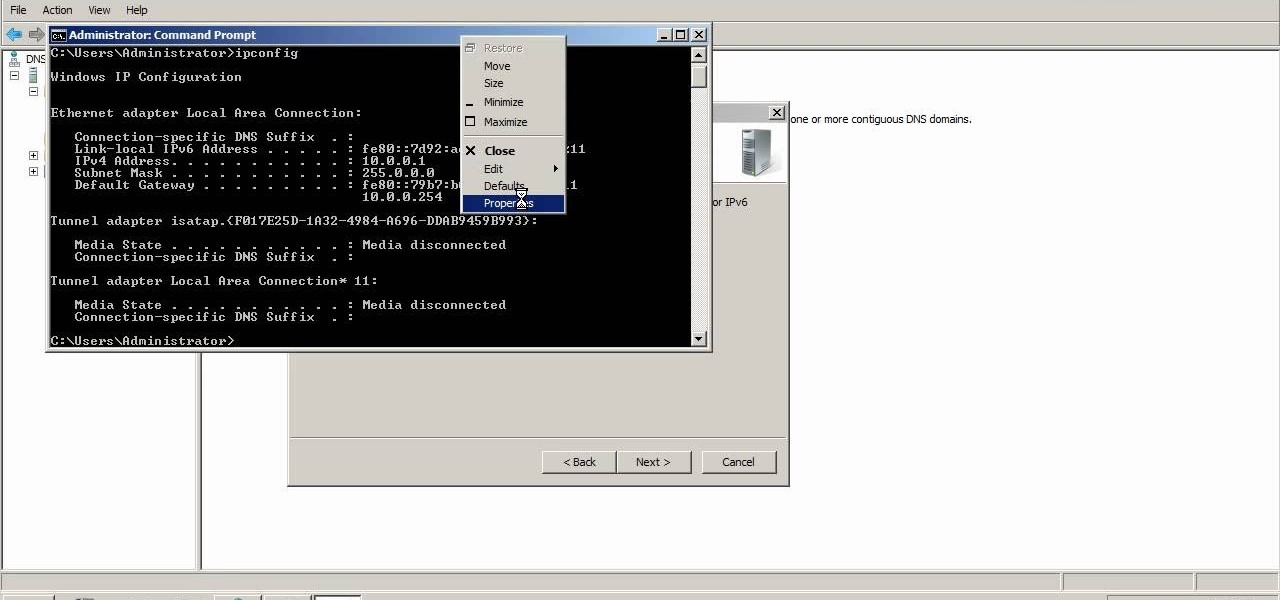
A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.

First, make sure that your image is hosted on a secure place online (such as your own Photobucket account). Then go to ImageMaps.com and use this free site to create your own image map that can now be added to your website.

Adding a SIM card to your Samsung Galaxy Tab is easy! If you have this new Android tablet and are looking to see how to install the SIM card, this video will clearly show you how it's done. Simply remove the slot's cover, insert the SIM card, making sure it's secure and snug, and then closing the cover. That's it!

If you have the chance to briefly talk and sit with a literary agent (such as at a convention), you only have so much time to impress them and pitch your book to them. These tips are the best ways to get an agent and secure representation.

You can create some lovely and cute cloth pumpkins to decorate your house for Thanksgiving! All you need is some scrap material in fall or pumpkin colors, and a few rolls of toilet paper. Wrap the fabric around the toilet paper, tuck and secure!

When you film at home with just a regular camera using the built-in microphone, the quality can be bad to worse at best. If you are looking to improve the sound the best that you can with low budget solutions, check out this video. You will get tips on how to secure your locations and also how to monitor the sound going into your camera.

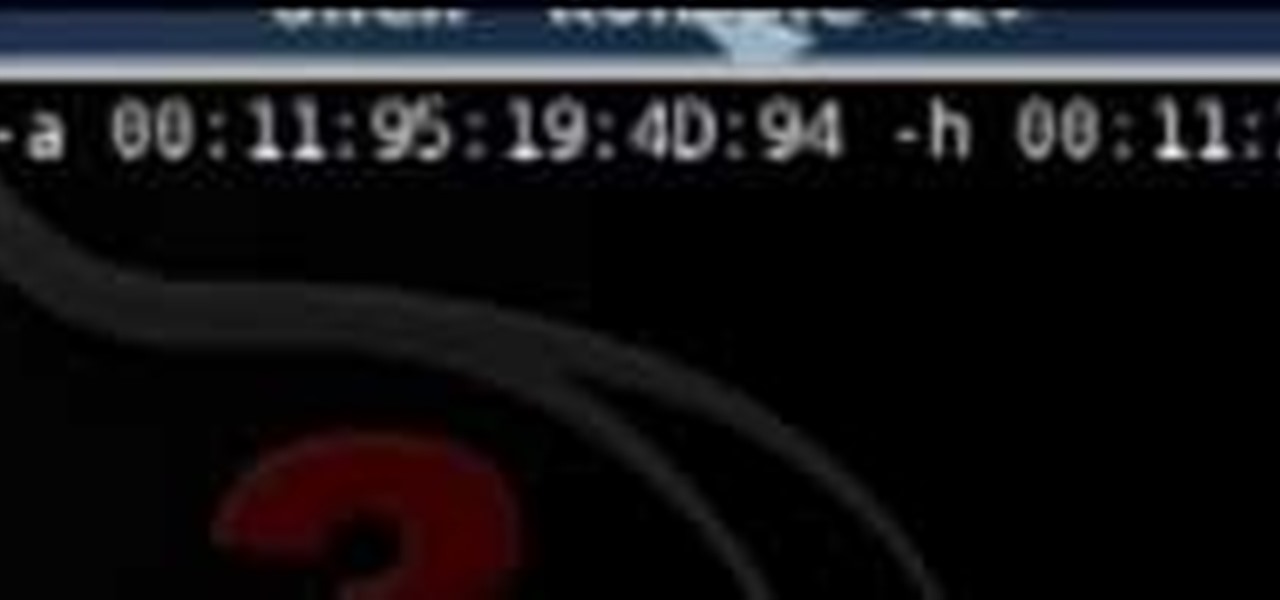
Interested in finding out just how secure your WEP-protected wireless network is? Let this video be your guide. It's a simple process and this home-networking how-to will teach you everything you'll need to know. For specifics, including detailed, step-by-step instructions, and to get started cracking WEP networks with BackTrack yourself, watch this helpful video guide.

Looking for an easy way to make certain that your sensitive personal information is secure? With Identity Finder, it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over three minutes. For more information, including step-by-step instructions, take a look.

VPN's are an invaluable set up for small business', and larger business', when it comes to keeping your information secure with remote employee's. This video details all of the info that you need to know about setting up and maintaining a great VPN!

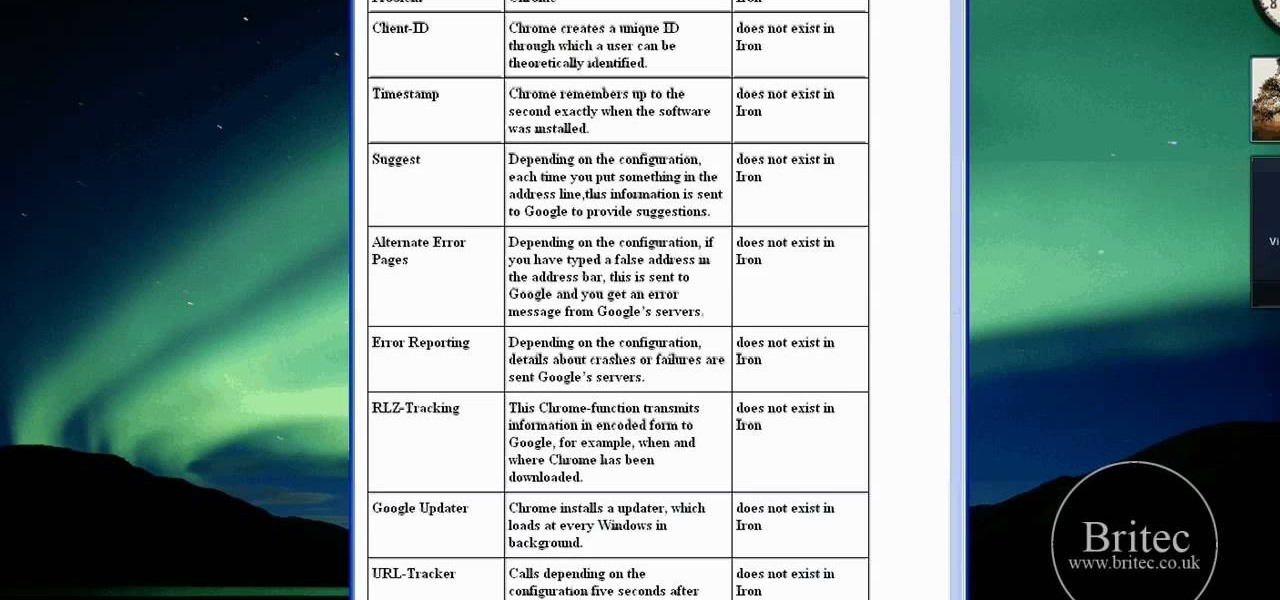
Interested in using Google Chrome but concerned about protecting your privacy while surfing the web? Meet Iron Browser, a secure but otherwise identical clone of the Google Chrome web browser. This clip from Britec will teach you where to find it, how to install it and how to get started using it.

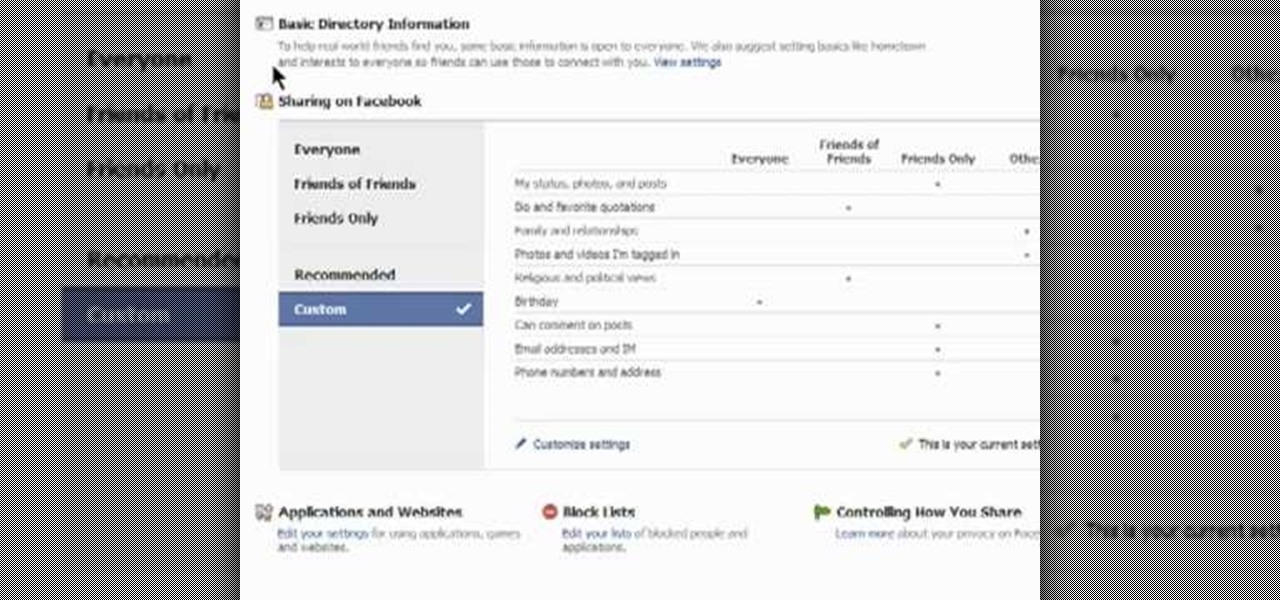
This clip presents an overview of the most important privacy settings on Facebook. Fortunately, with the right knowledge and the new Facebook Privacy Settings regime, protecting your data can be easy. So easy, in fact, that this video guide can present a complete overview of the process in about two minutes. For more information, including step-by-step instructions, take a look.

Installing beadlocks in your tires can help make sure that the wheel is secure and won't be going anywhere. There are many different types od beadlocks that can be purchased, but for this tutorial, you'll be finding out how to install one in an RC tire.

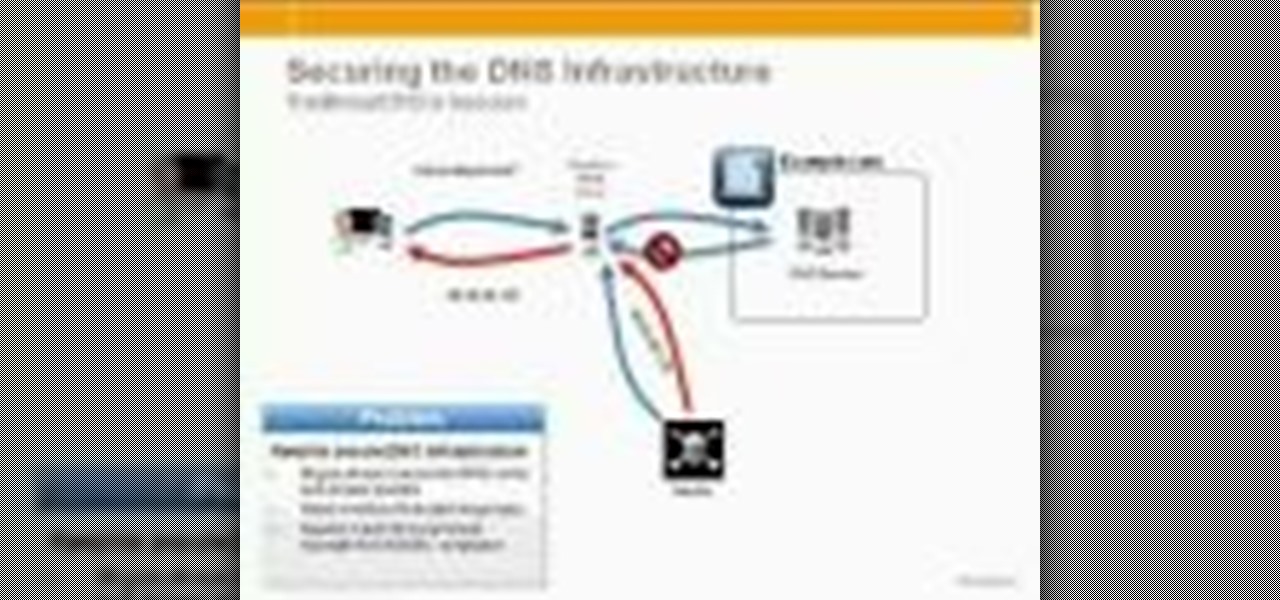
In this tutorial, Peter Silva talks with F5's Sr. Field Systems Engineer, Michael Falkenrath about the new BIG-IP GTM v10.1 DNSSEC feature. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

From Ms Lola, learn how to attach a lace frontal so that it integrates with your existing hair. Lace frontals are designed to add thickness and length to thin and/or bald hair lines and crowns, where hair is needed. When applied correctly, they give a totally natural appearance, are extremely comfortable and stay secure for weeks! Learn how to strut your stuff in this unique style with help from this free video.

In order to put custom themes and such onto your iPod or iPhone, you will need to install SSH or Secure Shell. This tutorial will show you how to do this, step by step.

In this DIY clothes making tutorial, learn how to make a Japanese Obi belt, perfect to add to any little black dress. Traditionally, Obi refers to various Japanese belts and sashes used for attire such as formal kimonos and martial arts uniforms. Obi’s are often worn with kimonos to secure the robe in place as well for the purpose of decoration. In this tutorial, learn step-by-step how to make an Obi belt in the comfort of your own home.

You can make your own canopy for your boat and save hundreds of dollars from the store bought ones. You’ll need 1 inch pvc pipe, some nuts and bolts and you‘re set. You’ll set you’re canopy off of some swivel brackets that secure on the pvc pipe with 2 inch screws. This video will show you how to rig everything and you’ll be sitting in the shade in no time.