In this tutorial, we learn how to make paper rose with construction paper. First, take a piece of pink paper and cut a thin strip out of it. Next, take that strip and fold it in half twice. Now, cut the paper in half so you have several strips of paper. Now, fold in the strips to make them look like petals. Next, cut two thin strips out of a green piece of paper and craft them into the shape of a stem. Then, cut thin strips out of the green and shape them into leaves. After this, combine the ...

In this how-to video, you will learn how to tie a rope halter knot. This is useful if you are about to go horse riding. First, bring it through the loop and bring the knot under the neck of the horse. Push the loop up and then make another loop and bring the end back through it. The knot has to go around that loop. Pull it and make it go up and back. It will not slip because it is secured against the loop. This video shows you the easiest way to tie a rope halter knot for your horse.
In this video, we learn how to delete hidden driver viruses. First, scan your computer with anti-virus and try to delete the virus that is harming your computer. If you have done this and your anti-virus can't delete it, download HijackThis from Trend Secure. Go through the download stages and install the new software. Now, open up HijackThis on your desktop. Once it's opened, open up the "misc tools" section. After this, click on "delete a file on reboot". Now, write the virus location name ...

This is a sped-up video of the FlowerGod showing how to make a beautiful feather anklet. The video is sped up to four times its normal speed. He begins by putting a basic feather anklet around a girl's ankle. Then he gets a piece of paper, to have a safe place to use some glue. He deposits a small amount of glue from a bottle of glue, and then uses this glue to secure several more decorations onto the anklet. These include some pink and white flowers, as well as a green feather. In the end, t...

Follow this video to view suggestions on how you can decorate a Christmas tree. It is best to start placing the lights first. Try to space them evenly and you can secure them in place by means of crafting wire. When you finish with the lights start decorating the Christmas tree with garlands and tinsel. Apart from giving a nice effect they will also serve to hide the wires of the lights. The next step is to start hanging the baubles and trinkets. Instead of including several colors try decora...

Learn to steal Kim Kardashian's pin curls and bangs with this video tutorial! Items needed: curling iron, straightener, blow dryer, hair spray, mousse, dual prong clips or bobby pins, comb and medium length bangs.

Learn how to wrap a short electrical cord. Treat your power cords right, and make them last longer, by learning how to store them correctly.

This is just a short climbing tutorial that demos what happens just after you go into the crevasse. Ditching the pack is easy if you have pre-hooked the pack to harness. The nest step is securing yourself with a prussik and getting it ready to use as a stirrup. But as we see, practice practice practice. Check out this instructional climbing video that offers some self rescue tips from a crevasse while climbing. These are good safety tips and procedures to learn.

Air horns are extremely loud. That's why they're used by truck drivers, fire trucks and ambulances to clear the way in a hurry. This video will show you how to make your own air horn, using stuff you've probably already got in a junk drawer.

F for FAKE. This video has been labeled a "Faux-To". Commonly contested as bogus science, we believe this video to be a hoax. What's your opinion? Comment below.

Spray the Styrofoam ball with a color that adheres to the scheme of the ribbon and ornaments. There will be white space when you make a Christmas ornament tree, and the color on the ball will help to conceal the space.

Choose ribbon in an appropriate color, texture and width. Are you trying to match the ribbon color to a particular gift wrap? Will the ribbon width give you the size bow you want? How will you be using the bow?

Place slip knot on hook. Hold yarn taut with 2 sets of 2 of fingers placed about 1½” apart, with tail in other hand. Create loop that crosses over bottom of 1st strand with loop toward right side. Fold loop over main strand going past tail. Insert hook below at tail strand. Pull up a loop using main strand for this loop. Pull 2 ends of yarn taut while leaving slip knot on hook. In 1st chain work 1 single crochet. Skip 2 chains; work 1 double crochet in 4thchain. Picot stitch by chaining 3 & a...

Learn how to sew a button by hand. Not wearing your favorite shirt because it’s missing a button? Don’t worry—sewing on a new one is simple and fast.

The human body contains nine units of blood—but in matters of a traumatic cut or injury, it's always better to be safe than sorry. If you're unsure whether you're in an emergency situation, get to an emergency room and let them decide.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

Apple's new iPhone XR, XS, and XS Max are sure to be hits this year. Of course, that means plenty of hungry customers are looking to sign up for a model once preorders begin on Friday, Sept. 14, for the XS models, and Oct. 19 for the XR. Luckily, there are preemptive actions you can take right now to avoid waiting outside an Apple Store overnight or getting kicked out of the preorder queue online.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Apple officially unveiled the long-awaited iPhone X, its tenth-anniversary edition iPhone, on September 12. With preorder and release dates just around the corner, you'll want to brush up on all things iPhone X to make sure you get your hands on one as soon as possible. After all, preorders start Friday, October 27.

When you first receive bObi, the battery is not plugged in. Luckily all you need is a Phillips head screwdriver to install it before bObi starts working for you.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.

Fashionably cool and awesome, this marvelous French Twist hair Style is as simple to make as it is elegant and stylish to flaunt. Just in few easy and accessible steps, this urbane style makes your appearance special and any outing memorable. Step 1: Comb Your Hair Neatly to Remove Any Tangles and Make Them Smooth. Step 2: Hold the Hair Together Like a Pony and Twist Them Till the Middle of the Pony and Make a Roll as Shown. Step 3: Once You Have Secured the Roll, Cover It with Surrounding Ha...

Being in your twenties is tough. You're not a child anymore, but also not quite a full-fledged "adult" yet. Sure, you do adult things like cook asparagus sometimes, but you're also sweating about securing enough likes on your social media posts.

Costume parties are in full effect this weekend, so with that said, how cool would this look at your Halloween party? Instructables user castor009 made two holes in the head (one for inserting the PVC tube, the other where the liquid will spew out) and insert the pipe and tubing, then stuffed it to secure everything. He then fit the bottom tubing through a pencil holder and attached it to a water pump. Then just add whatever you want to serve at the party (I would suggest anything red or blac...

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

In these home security and safety videos, learn how to upgrade your house in some important ways. Our expert, Jon Olson, will show you how to secure your windows and sliding glass doors, some of your home’s most vulnerable entries, with bar locks. Learn how to install a door guard latch to keep small children from getting out, as well as a peep hole to see who’s at the front door. Finally, get some important fire safety tips and learn how to install smoke detectors for your home.

It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

Instagram wants to bridge the gap between advertising and shopping for a more central buying experience. The app has long been a platform for advertisements, with both companies and creators using it as an outlet to link to products, so it's only natural for Instagram to allow users to buy content featured in posts without ever leaving the app.

The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one of the biggest problems can be fixed.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

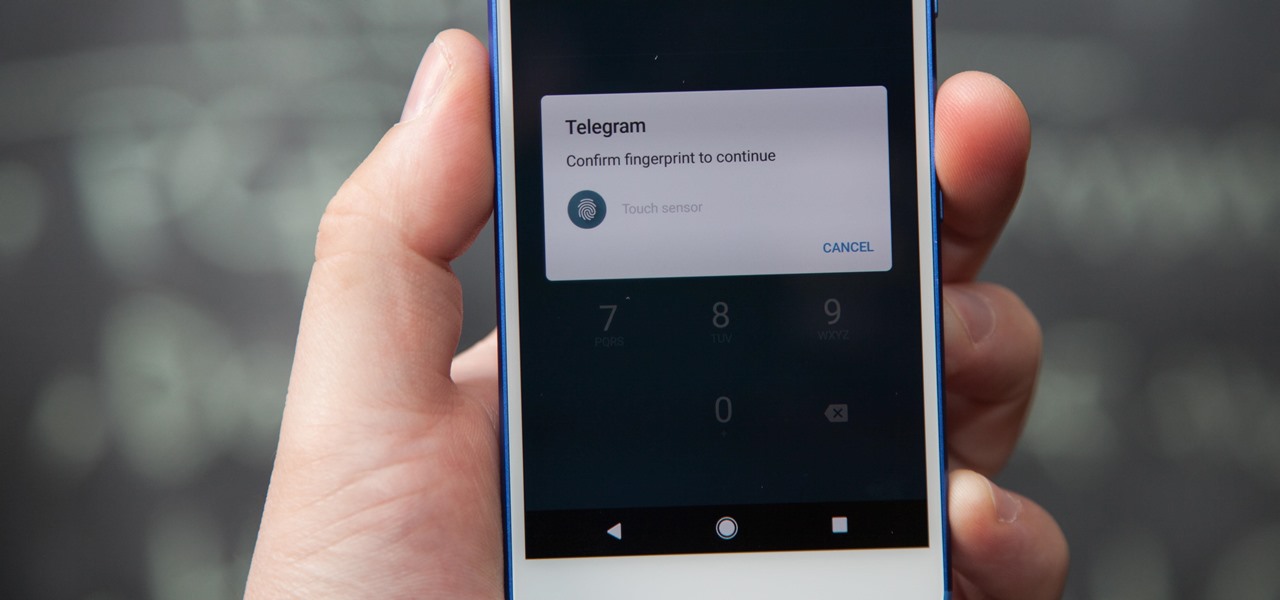
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Hearthstone is a collectible card game by world-class developer Blizzard Entertainment. It has taken an entire generation of casual and professional gamers alike by storm. So many people play it, chances are you've already sunk some money into it. So, if you're going to pay a little anyway, you may as well get a discount.