How To: Get VPN Connection
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Take a look at this new and contemporary Prom Bun Hair Style which is super cool and exclusive to adorn. Its over the top style has a unique and sophisticated appearance which appends a ritzy accent to your urbane persona. Try out this style following this simple tutorial. Step 1: Comb Your Hair to Make Them Smooth and Tangle Free. Once Done Gather All Your Hair in a

Mermaid Braid Hair Style Tutorial For Beginners!!!!
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

Today I would like to share a few data about painting on silk with all the creative readers. The knowledge comes in handy if you want to give a homemade gift or even try to sell a few of your masterpieces.
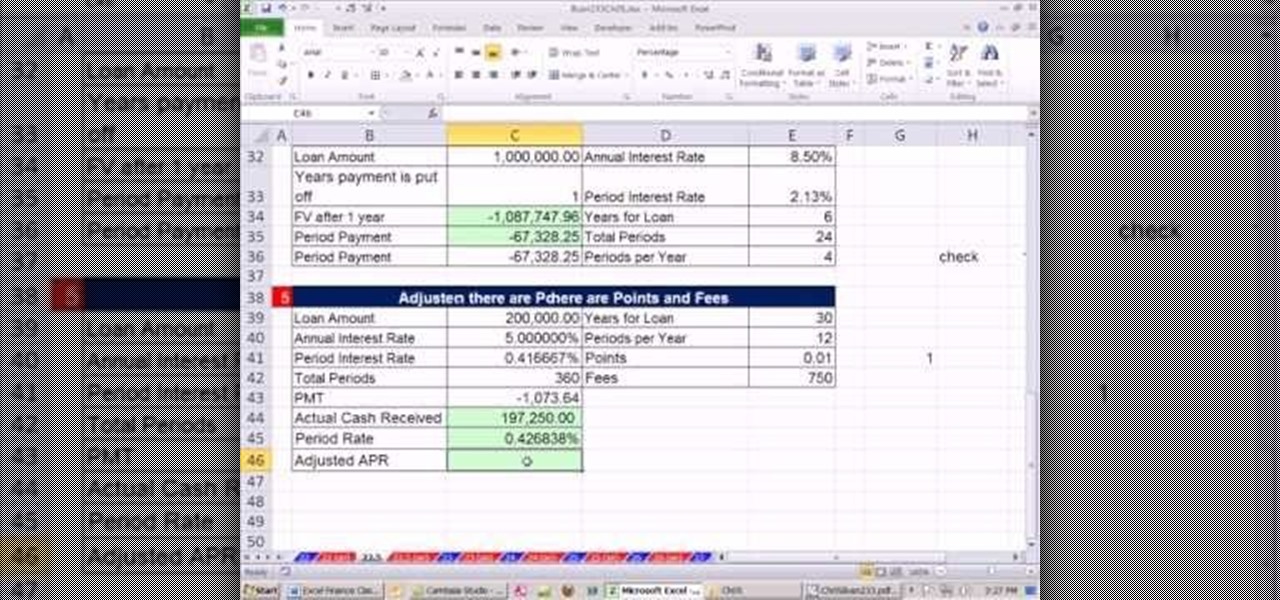
As you might guess, one of the domains in which Microsoft Excel really excels is finance math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 12th installment in his "Excel Finance Class" series of free video lessons, you'll learn how to calculate average and marginal tax rates with Excel.
Watch this instructional travel video to learn about obtaining a tourist visa to Brazil. Visa fees include the following:

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

When you place your iPhone over a card reader for Apple Pay, it'll always pull up your default card. That might work fine for you, but perhaps that isn't the card you want to use. The problem is, you don't have time to switch cards before the payment goes through. That might result in using your rewardless debit card to buy groceries when you could've snagged 2% back by using your Apple Card.
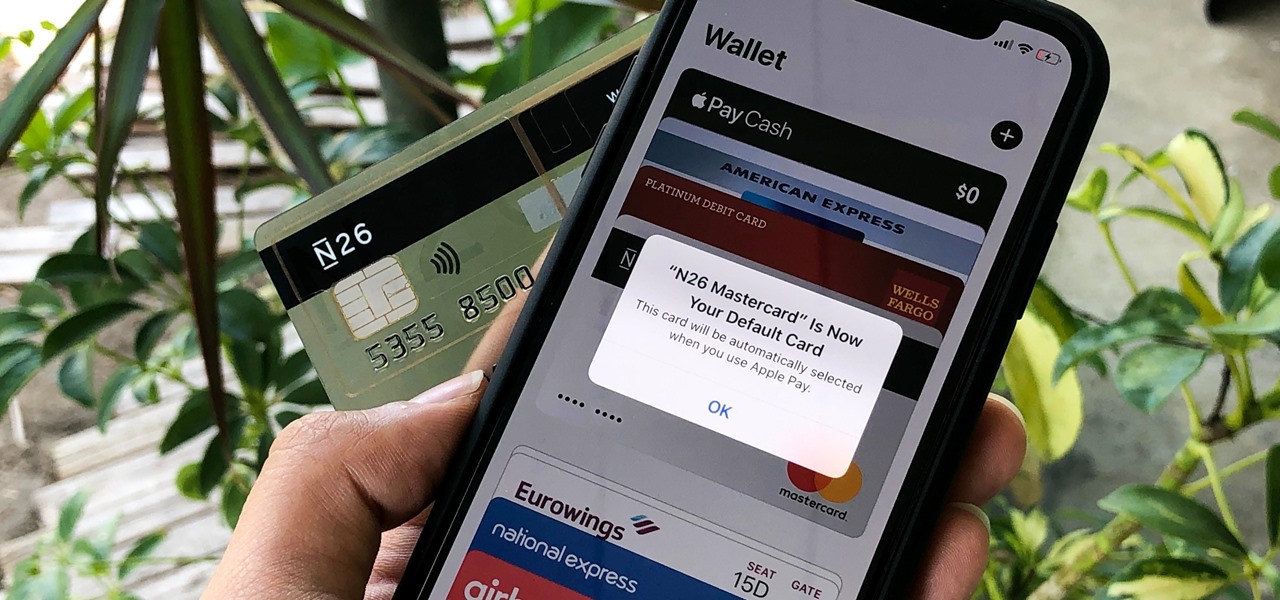
Using Apple Pay in stores to make purchases is as easy as holding your iPhone near the NFC reader and authenticating with Face ID or Touch ID. That method uses the primary payment card in Apple Wallet automatically, and your primary card may change from week to week based on your spending, so you'll probably need to change it periodically.
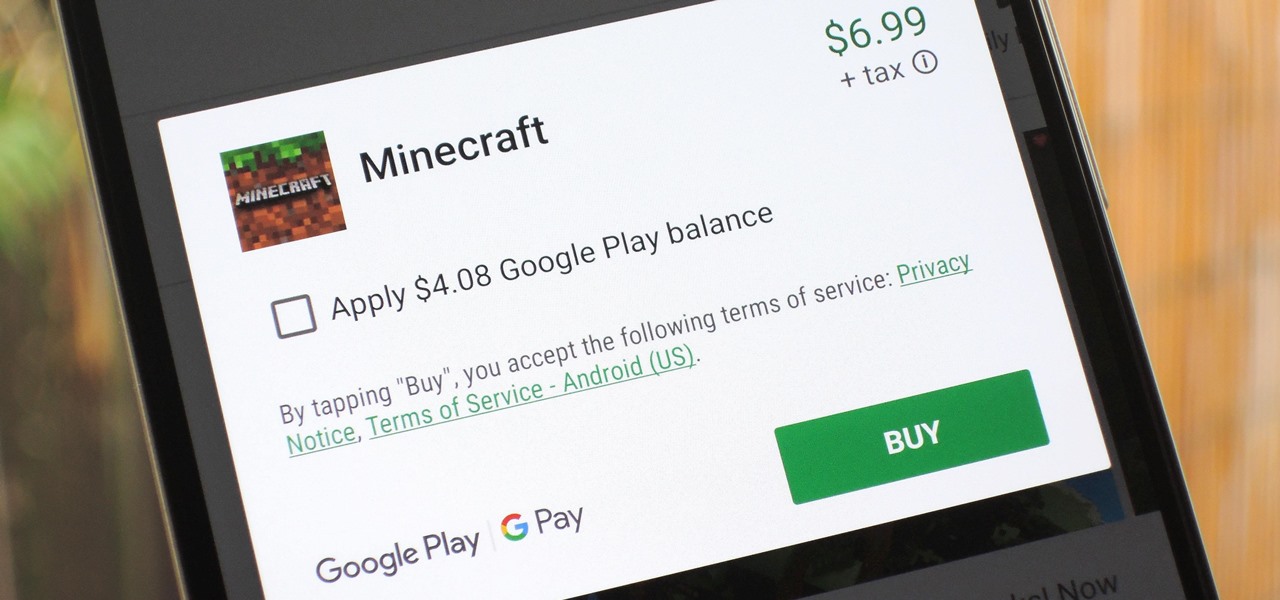
The iTunes App Store makes it easy to buy an app or game on someone else's behalf, and it's a great way to send an iPhone user a thoughtful gift. The Google Play Store doesn't have such functionality, but there are still a few workarounds to accomplish the same goal: gifting an app to an Android user.
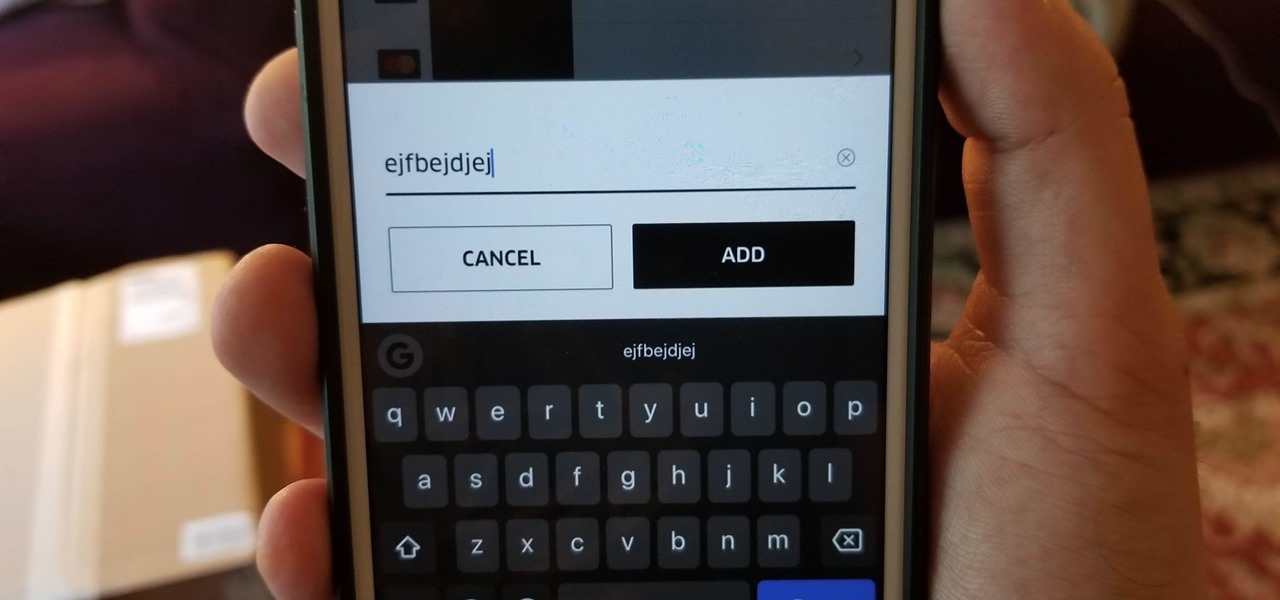
Uber is one of the best ways to get around, but nobody said it was cheap. What's even more infuriating is when you have a bad experience with a ride. Sure, you can get a refund, but then you need to figure out where to enter in the promo code for the coupon that Uber sends your way.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.
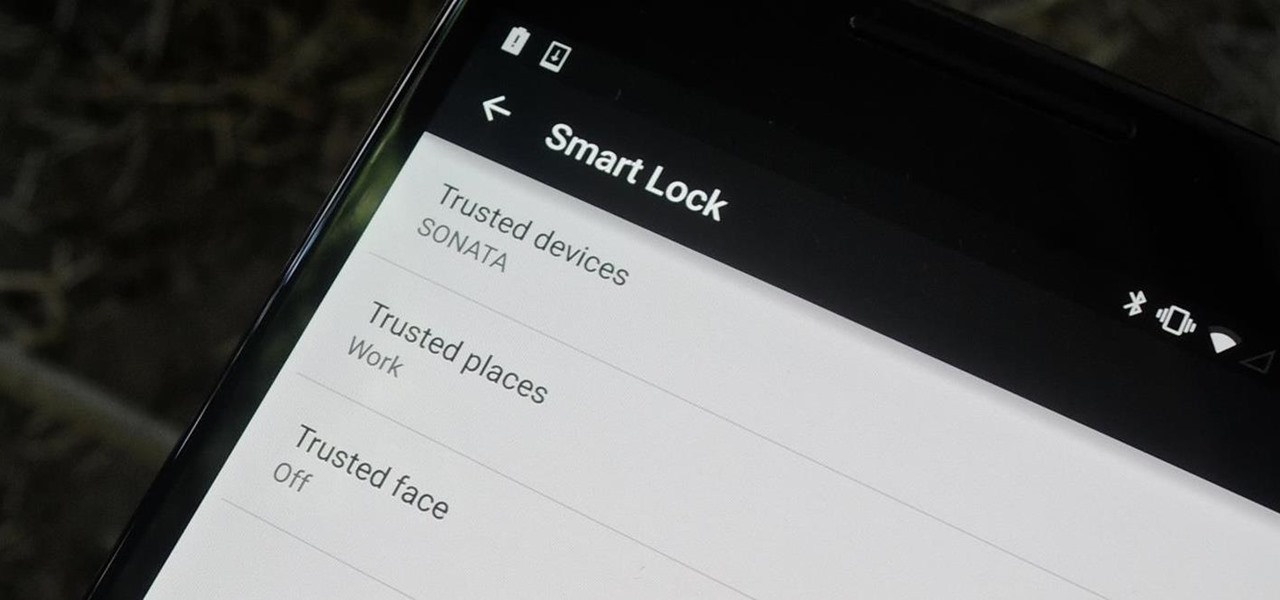
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).
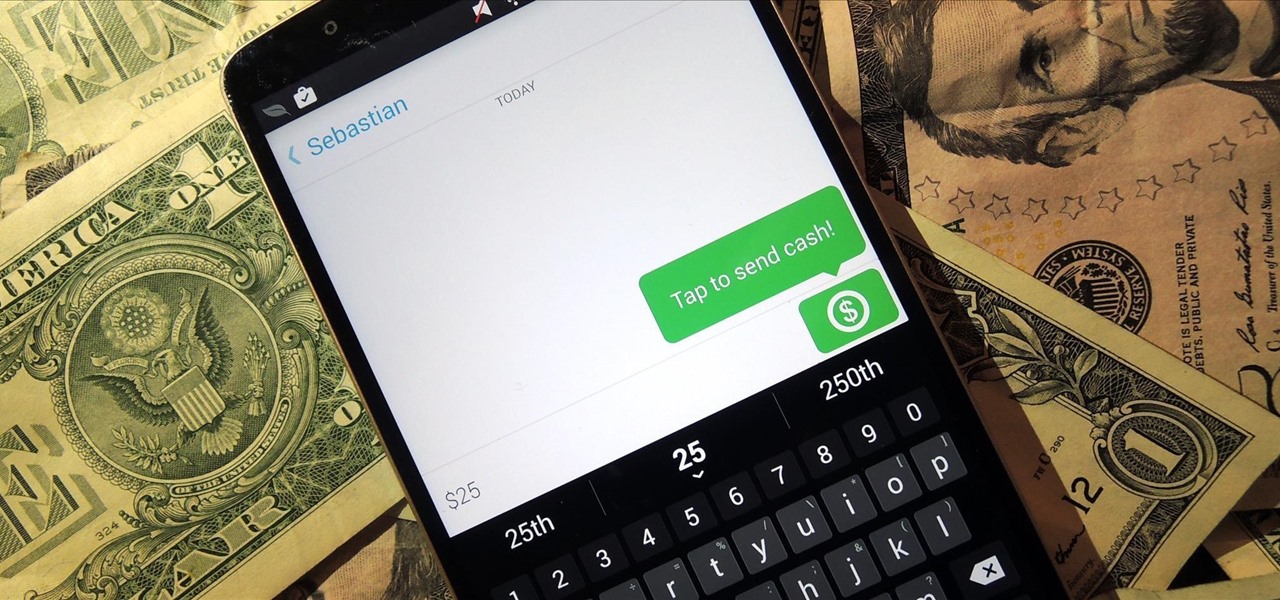
Snapchat is definitely not known for its stellar privacy or security features, but that hasn't stopped them from gaining millions of users. Now, those millions of users can do more than just share pictures and videos—they can share money.
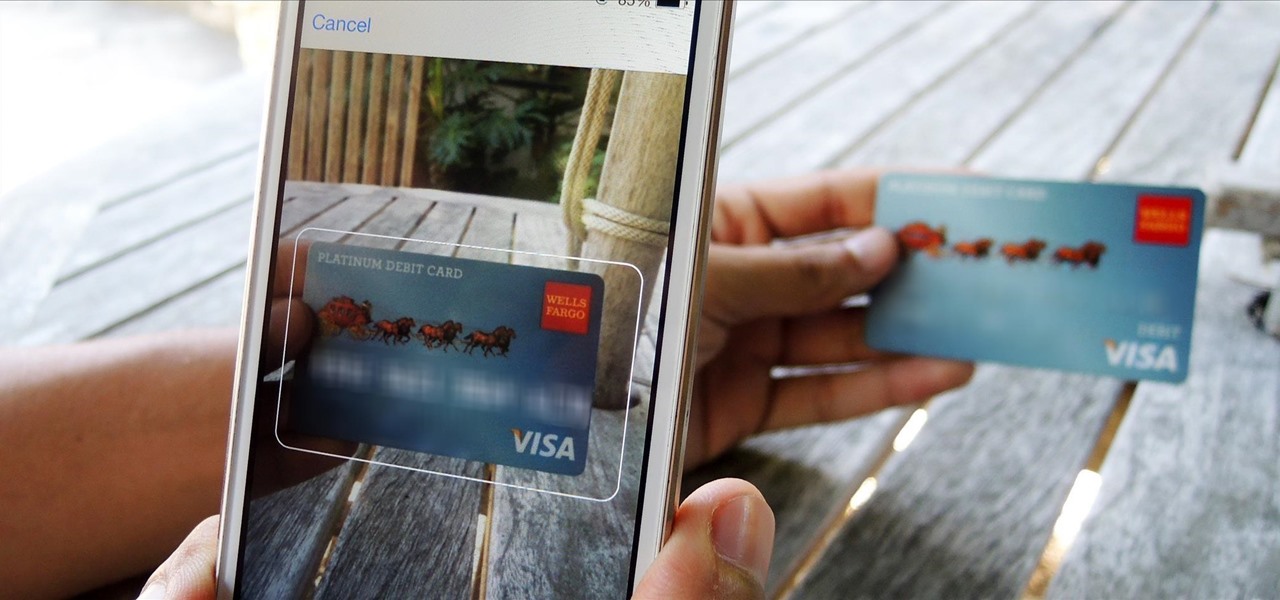
There's a feature that debuted in iOS 7 that lets you to save your credit or debit card information in Safari so that you can auto-fill text boxes when purchasing something online. Unfortunately, you still had to manually fill in your card info the first time, and if you wanted to disable the feature for security concerns, it was entirely useless.

One thing that's always important to have in your home office is a bulletin board, because they let you quickly display papers that you need to see every day, such as schedules, notes and memos.

I always found that those safety lights for bicyclists on the market were never good enough when riding in the dark. That got me thinking about people who use wheelchairs and how unsafe the night could be when they want to go out. So here's what I came up with:

First of all the tutor advises that this is a good idea to do it regularly. It is advisable to drain it out otherwise it shall stop the boiler from working. Before starting your work you have to switch off your boiler. Now allow the water to cool down because it is very hot. First find out the radiator and the drain valve attached to it. Now take a hose pipe which is long enough to drain the water from the radiator to your backyard. Slide the pipe over the inlet and then secure it the link. S...

This video on typhoon preparedness comes from Andersen Air Force Base in Guam, where typhoons are common. The key to surviving a typhoon or other disaster is preparation. Stock up on enough food and supplies to last your family for about a week. Routinely check expiration dates on food, water and batteries and rotate your stock. Be sure window screens are in place and in good condition in the event the power is off for several days.
Wrestling with the whys are wherefores of WiFi? Can't figure out how to secure your network? Take heart: This remarkably thorough, seven-part home networking tutorial will get you up and running faster than you can say `Wireless G.'
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

You may wish to block websites from being accessed on your computer for any number of reasons. Maybe you're a concerned parent who wants their kids to browse the internet safely. Maybe you're an employer who wants to secure office computers or blacklist innapropriate websites.
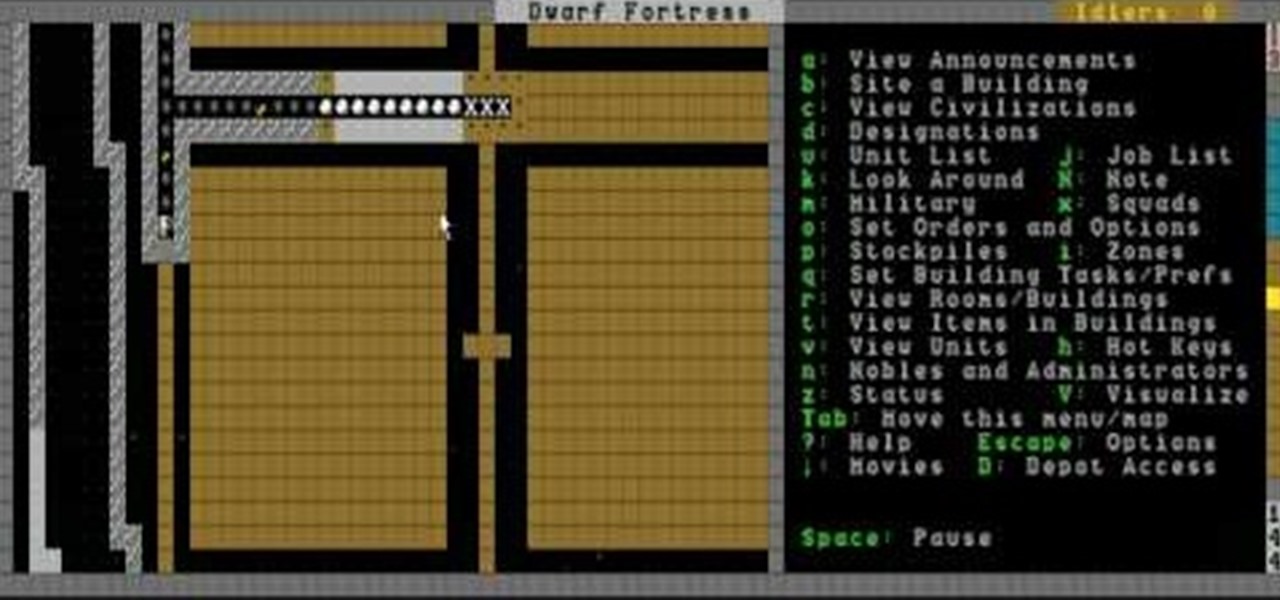
In this video, you'll learn how to use military patrols to repel invaders, make secure entrances to your fortress, and create bins in Dwarf Fortress.

The padlocks that secure most of America's high-school lockers are one of the easiest types of locks to open in the world for thieves and other miscreants. The easiest, cheapest way to do so is using a shim. These can be bought online, but why both when you can make one yourself out of an old soda or beer can? This video features a professional lockpicker at a conference explaining exactly how to make your own can shim and use it to open any padlock. You little devil you.

In this video, we learn how to pack a suitcase like a professional concierge. First, you want to tuck in the edge of the case and pack the shoes at the very bottom. After this, tuck shoes or underwear into boots and shoes to help save room. Next, lie the jeans over the luggage and then fold shirts up to where you are rolling them from the bottom up and place them on the pants. Add in any more shirts, then place the waist band and bottom of the pants over the shirts. Use tissue paper on the to...

Eddie shows us how to remove a boat from the water in this video tutorial. First, take down the canvases and wrap them up. Now, put the antennas down and drive the boat to the loading dock. Next you will need a large truck that has a hitch and trailer attached to it, and secure everything so the boat stays on and doesn't come off of the trailer. Take the drain plug out of the boat before you transport it, to make it lighter. Transport the boat to your house, and place bricks over the front so...

Know your knots! With this free video tutorial, you'll learn how to tie a multiple scaffold knot. The multiple scaffold knot has a couple more loops in it to make it stronger and more secure than the regular scaffold knot. The knot is easy to tie provided, of course, you know how to go about making it. For an easy-to-follow, step-by-step overview of how to tie this useful fisherman's knot in a minute's time or less, watch this free video knot tyer's guide.

In this how to video, you will learn how to open a 6th generation Ipod Classic. First, make sure to turn it off and make sure the hold button is on. Take a prying tool to undo the clips inside the device by sliding it in between the cover and back. Once the clips are undone, place thumb tacks on the sides and tops while popping the base out. Be careful, as there are cables inside that you do not want to break. The orange part is the battery while the blue object is the hard drive. Once you ma...

This video illustrate us how to preform a simple interrupted suture in surgery. Here are the following steps:

This video shows the viewer how to make a UNA box from pieces of hardwood, and 2 pieces of dowel. The box is made by building the normal box from the wood. The lid is then secured using a large piece of dowel so that it can pivot. Additionally to the first large dowel another smaller piece of dowel is secretly added to stop the box opening this has to be removed for it to open so makes it harder for intruders to open. The box can then be sanded, painted and used to hide small objects!
Check out this informative video tutorial from Apple on how to get familiar with a Mac in comparison to a PC. If you're used to working on a PC, this video will show you some of the basic differences between using a PC and a Mac. Once you get to know the fundamentals, you'll find that it doesn't take long to get familiar with the Mac.

Check out this informative video tutorial from Apple on how to stream music wirelessly with AirPort Express and a Mac. If you have a Mac or a PC and iTunes, it's easy to stream music wirelessly. It's called AirTunes. All you need is an AirPort Express and a set of powered speakers, or stereo, or AppleTV, and the room you want to hear music in.

Ever wanted to learn how to make a rekey a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... key making. Just watch this video tutorial to see how to properly make a replacement key for a lock.