In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...
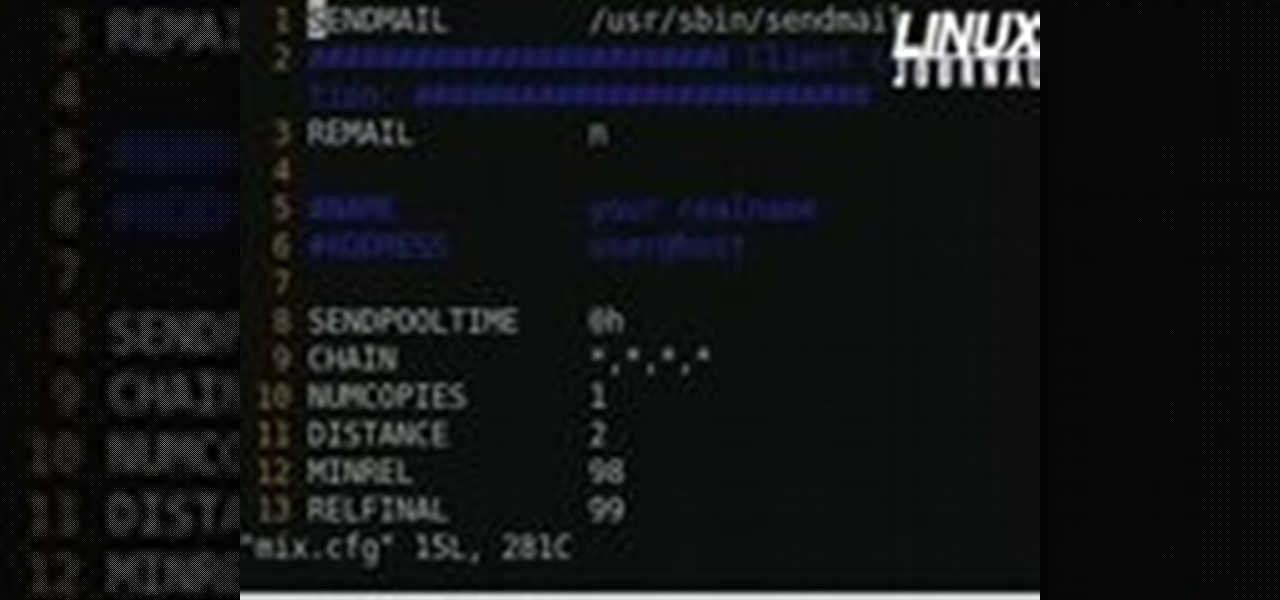
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

Video: . This video will show you how to secure your kayak to a J bar roof rack carrier.
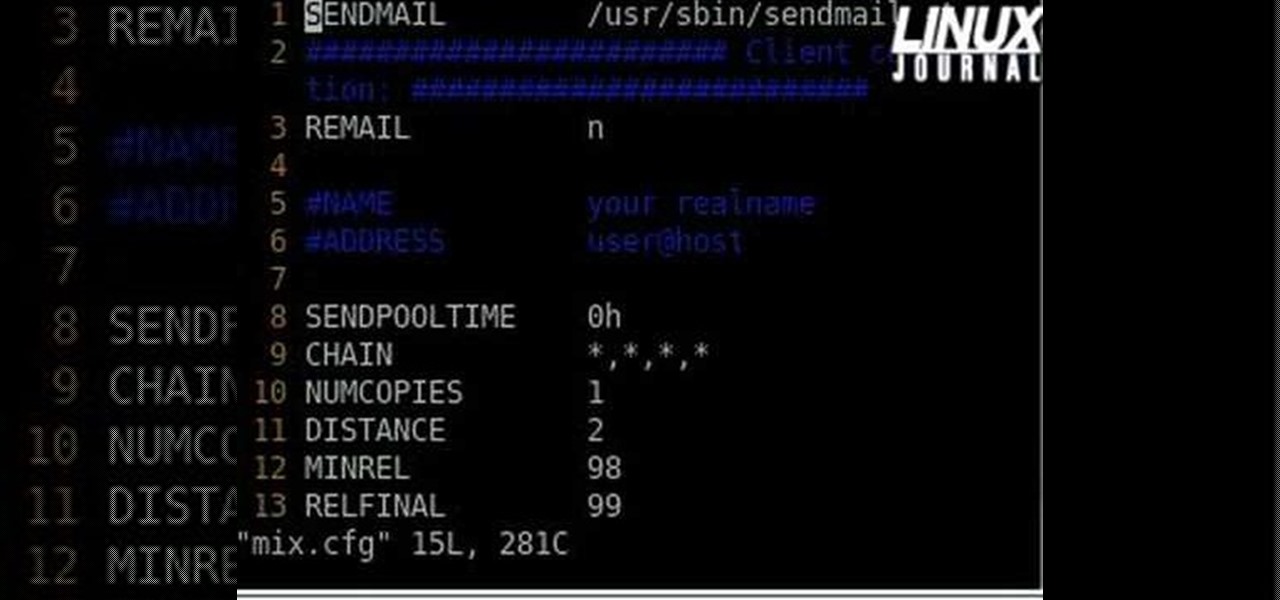
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

TrueCrypt is a free open-source program for encrypting data and it's excellent for securing hard drives, but it also has the ability to hide a secret operating system inside another operating system. CNET shows you how this "insider secret" operating system is created. This operating system will be impossible to prove to people like the Feds.
In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be encrypted when a password is placed. Further below here is where you actually choose the password, this ensures that only people who know the password will be able to see the contents of the document. Below this is the d...

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to secure your Gmail account.

If you can find people who speak English in China, you'll probably get where you want to go faster. Memorize this basic Chinese phrase and feel a lot more secure once you get to China!

Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

Contrary to what most people do, letting your dog stick it's head out the window is not a safe way of transporting your animal! Check out this video for some tips on how to safely travel with your dog.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

In iOS 13, Apple introduced HomeKit Secure Video, which allows smart home devices with cameras to give iPhone users a private and secure way to store recorded videos. Plus, it has benefits such as object detection and activity notifications. Logitech is the first to add support for HomeKit Secure Video with its Circle 2 cameras, and all it takes is a quick firmware update to get started.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

In this clip, you'll learn how to get started using Secure Computing's Secure Web Protection proxy service. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

Buns and updos are gorgeous hairstyles, with one caveat: If they're not pinned perfectly and securely in place, all your hard work braiding and curling will go to waste as your hair slowly unravels.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

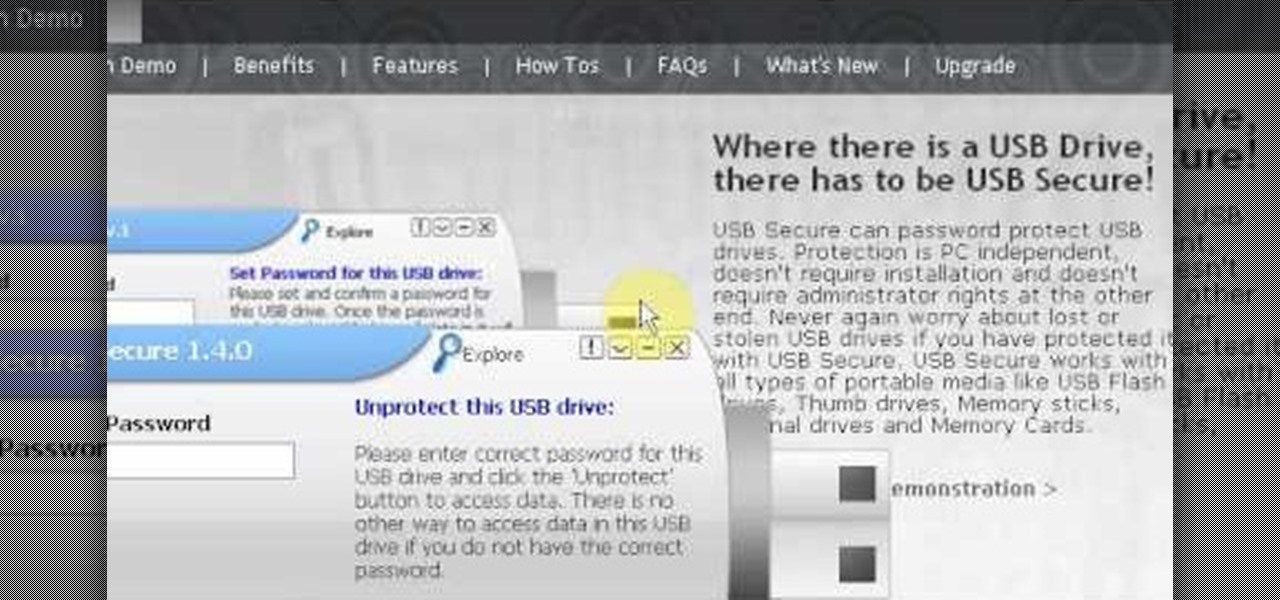
Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

Use three tools to create a simple ponytail. Use a hairbrush, a bobby pin, and a bungee band holder for this look. Using a bungee band instead of a standard ponytail holder eliminates some of the issues typically caused by pulling hair through ponytail holders. Start by using a bristled brush to brush the hair to one location on the head. Secure one hook of the bungee band in the ponytail and wrap the tail around the rest of the hair. Wrap it around again, and secure the other bungee band hoo...

Using ASP.NET Secure Services and Applications Services

Need to know how to tie a Bowline with a few ways of securing it? This way shows you how to secure it with a seizing so that it won't accidentally come undone. Included is a little variation of the bowline with a built-in seizing. If you don't have electrical tape to secure the bowline feed the bitter end back through the hole. It also makes it so you don't have a tail line dangling if you're towing something.

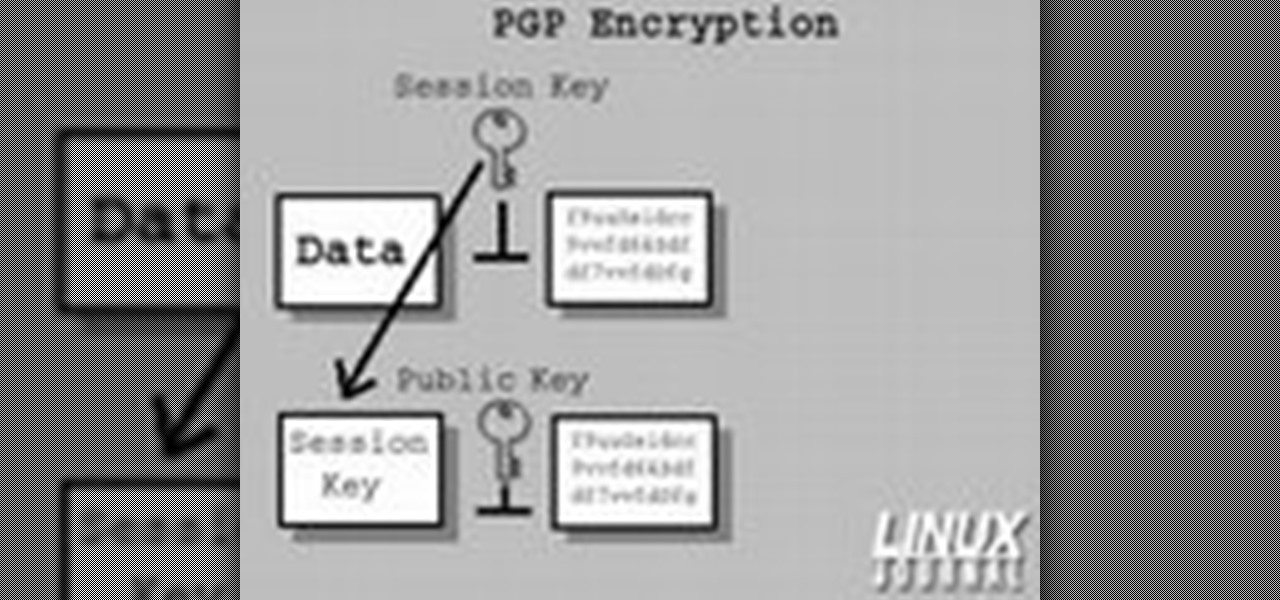
In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

Picking a secure password is not only important for protecting your privacy, it's also very easy. Provided, that is, that you know how to go about it. This free video lesson from CNET TV will walk you through the process. For more information, and to get started creating and using high-security passwords yourself, watch this video tutorial.

The Clinch Knot is used to secure your fishing line to your fishing lure. In this video, learn how to tie a secure clinch knot, step by step. You can't fish without a sturdy lure, so watch the video and practice until you master the knot on your own. Once you've got it, attach your bait and you are on your way! Happy fishing!

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Don’t play Russian roulette when it comes to your wheels. Keep your bike secure with these precautions.

A formal occasion calls for a classic look. You Will Need

A little precaution can go a long way to securing your online banking experience. Use these tips from Tekzilla.

Secure a square knot with tips from this video.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

Like everyone, you're on Facebook. And, also like everyone, you'd like to control the access your Facebook apps have BEFORE you even install them. Well, you can, with a sweet little Firefox add-on called FB-Secure. Take control of Facebook app privileges before they read your secret diary.

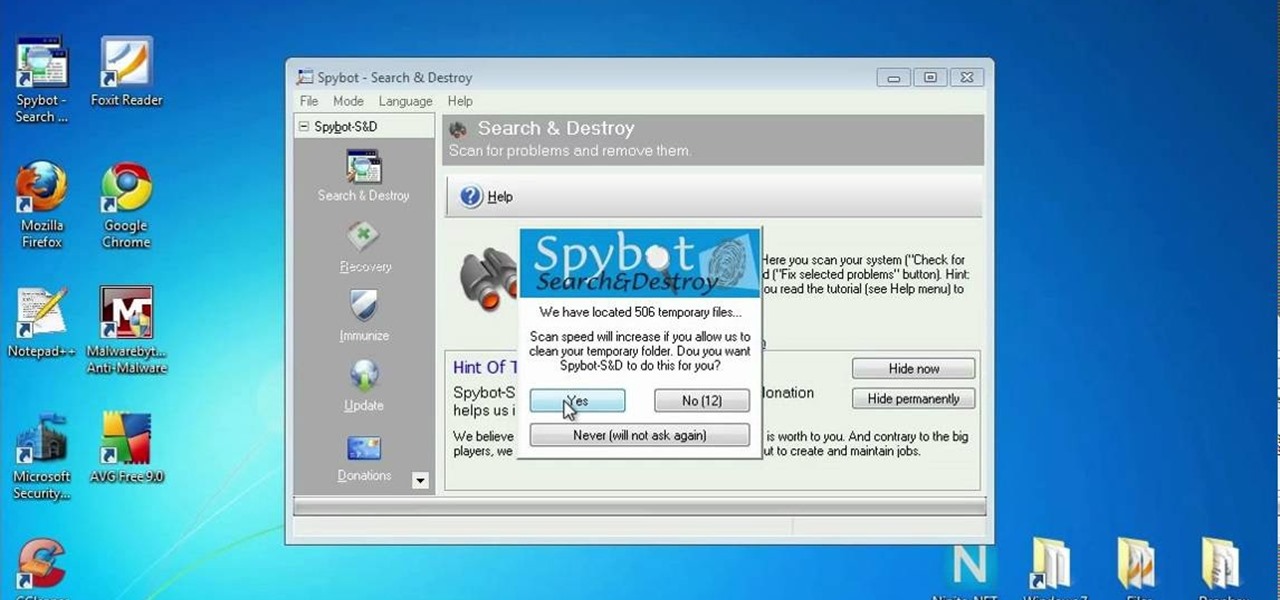
In this clip, you'll learn how to secure a new Microsoft Windows desktop or laptop computer. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started protecting your own new Microsoft Windows PC, take a look.