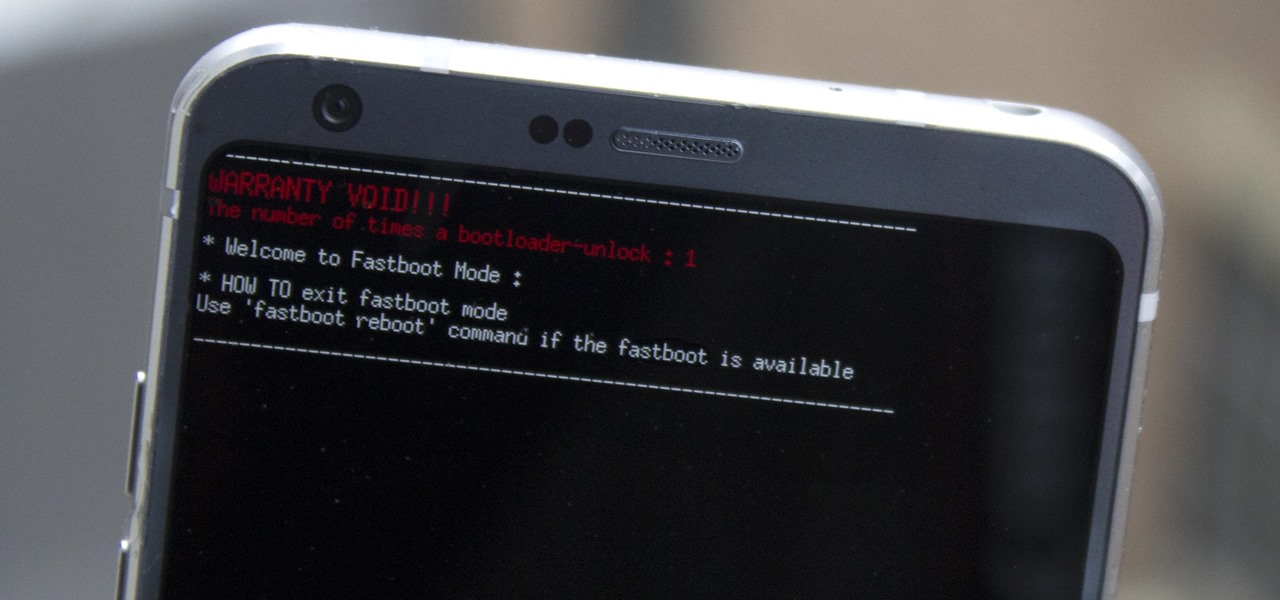
Preorders for the LG G6 have all been fulfilled, and the phone has been up for grabs at local cell phone providers for three weeks now. However, not every LG G6 was created and released equally. The T-Mobile variant of the LG G6 features an unlockable bootloader, while most other North American variants come with a tightly locked down bootloader, which effectively limits the full potential of your brand new fairly expensive phone.

Chinese search engine giant, Baidu, has just announced its own autonomous car platform which is intended to speed up the development of driverless vehicles.

It's always nice getting paid to do something you love. That's why Nintendo is offering all Nintendo Switch owners a chance to find vulnerabilities before another hacker beats them to it first. Depending on the vulnerability you find, Nintendo is willing to shell out rewards starting at $100, all the way to $20,000, to the first bug reporter who uncovers it.
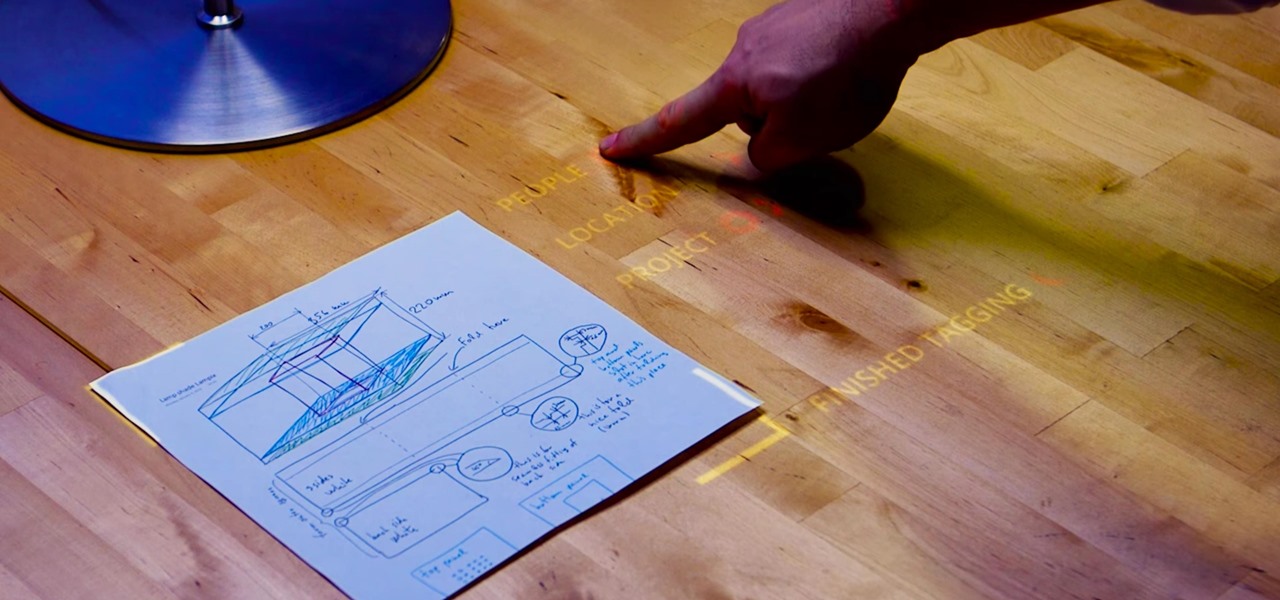
Judges at the South by Southwest (SXSW) Accelerator Pitch Event named Lampix the winner in the Augmented and Virtual Reality category, conference organizers announced today. The ninth annual competition, which took place over the weekend in Austin, Texas, pitted 50 startup finalists against each other in 10 technology categories.

A new Windows Insider Preview, version 15055, was released on Friday, March 10. Along with the normal collection of bug fixes and new features came a secret addition to the Mixed Reality Portal in the update. Windows Mixed Reality, along with Cortana, can now teach you how to use the platform, and, hopefully, usher in with it some understanding of what mixed reality is.

While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality.

Every day the young world of mixed reality is creating new ways for people to work with with computers. We are looking for, and finding, new ways for these head-worn computers to understand what we tell them. Sometimes it is with our hands, sometimes it is where we turn our head, sometimes it is what we say. In the case highlighted below, it's where we walk.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

Google and Microsoft have both established platforms and hardware for emerging digital realities, but Apple, true to form, hasn't had much to say on the subject. They've shown interest in augmented reality, and we've seen patent filings that indicate research and development, but a recent rumor points to that research ending up in your car instead of a rose gold headset.

Microsoft's HoloLens may the coolest new advancements in technology we've seen in quite some time, and anyone (with deep pockets) can buy one right now. But so far it's been an isolated platform where you experience mixed reality alone and others watch you air tap nothing but air. Developers are working to change that, and we're seeing the first examples crop up online already.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Mixed reality can give you the feeling that you've uncovered a hidden world layered into the physical one you already know. This can happen in so many ways, from a trading card that births a hologram or a first-person shooter with robots blasting through your walls. Xperiel—a California-based augmented and mixed reality company—wants to create a platform to make that a whole lot easier for developers.

As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

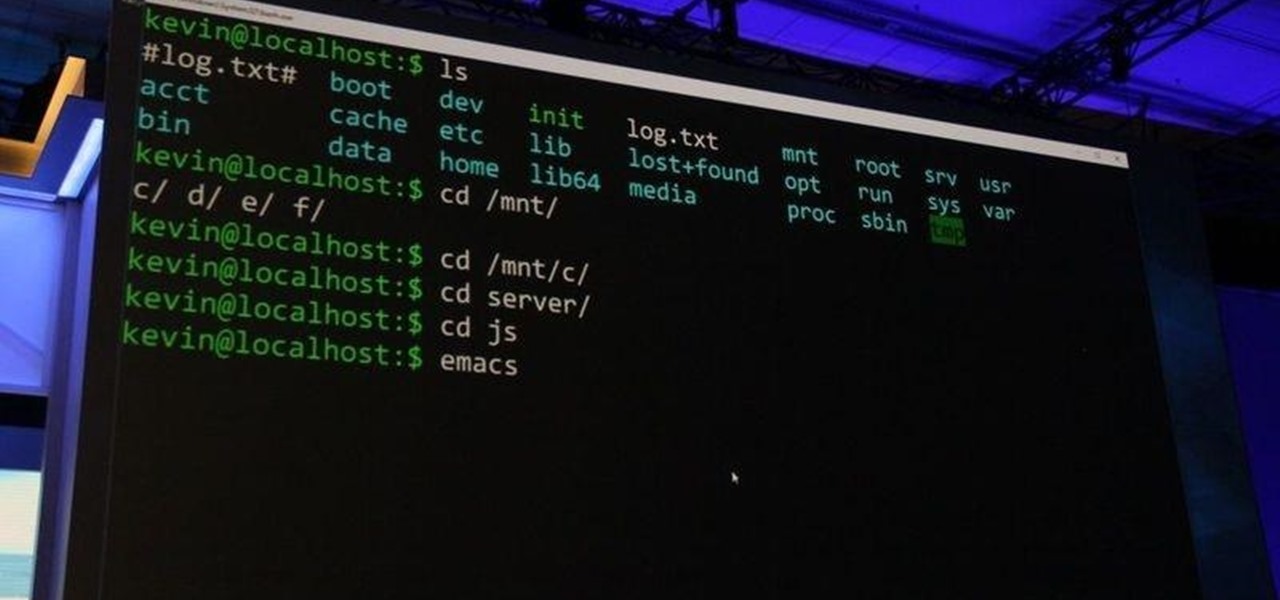
Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Ah, the age-old problem of sharing pictures with friends and family. Ten years ago, the best method available to us was passing around duplicate photos printed out at the local drug store. As easy as smartphones have made this act, you'd think we'd be satisfied by now.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

This video will show you how to disable secure virtual memory in Mac OS X. From the top left of your screen click on the apple icon. Click on system preferences from the pull down menu. Click on the security icon. Click on the image of the closed lock from the bottom left of the window so that you can change make changes.

Now we'll learn how to secure PDFs so that we can safely send them out to clients for review and be assured that they can only access the content the way we want them to. Turn off things like printing and content extraction. Password protect your PDFs so that they can't even be opened without a password.

This is a tutorial on how to secure your wireless network. This tutorial shows you how to setup a WEP encryption key for your wireless network.

Rubber bands are an ordinary, everyday, common household item, right? Their hidden in your desk, wrapped around your bills, holding your pencils together at the office, but what else can you do with rubber bands? What are some extraordinary uses? Woman's Day Magazine tells you how you can repurpose those rubber bands!

In this tutorial, we learn how to wear a full formal kilt outfit with accessories. You will need: socks, garters, shoes, kilt, sporran, kilt pin, jacket, vest, and knife. First, put your socks on, then wear the garter around the sock, folding the top of the sock over the top of the garter. After this, put your shoes on, by lacing them up to the top of the socks. Next, open your kilt and wrap it around your wait. The strap should go through the buckle, then through the hole in the strap. Secur...

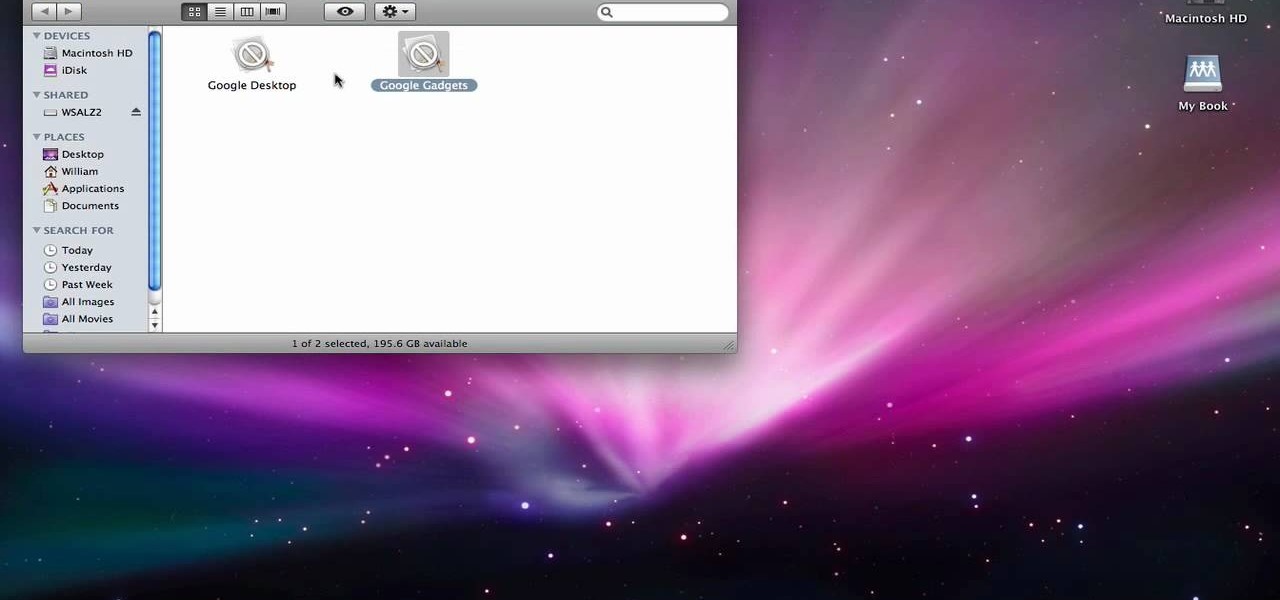
In order to completely delete items from Mac OS X. Download Google desktop. This will search your computer and the web and your computer. Go to Applications. Right click on Google Desktop. Go to Show Package Contents. Drag contents into the trash. Next, go to Google Gadgets. Click and drag it to the trash as well.

Learn how to put up a tarp for shade and protection from the rain in this video. First, find two trees with a nice flat spot in between them. Throw a rope up over a limb at least fifteen feet or so high. Now, tie the rope off to itself or to a smaller limb. Next, secure the rope on the other tree and leave the slack on the ground. Next, put the tarp over the rope evenly and anchor one end with a wire tie, small rope or bungee. Now you hoist the tarp up using one end of the rope and pull it to...

This video shows how to style your hair based on the Final Fantasy video game character Yuna. First you will need to spray your hair with a root gel spray, which is a spray that gives your hair texture. Then blow-dry your hair upside down.

Leah for May Arts Ribbon shows how to make a flower loop bow. The following items are needed for it: Needle and thread, scissors, May Art Ribbons and a ruler. Buttons or flowers may also be needed to put on top of your bow as per your selection.

You'll need five baked eight inch square cakes, five - seven cups of white icing, five sugar cones, a little glitter, a little bit of pink icing, a pastry bag, silver non parils, gummy balls, candies, pink and red icing, mini canned hearts, red sprinkles, colored paper and tape and 5 toothpicks. Cut one cake into fourths and stack them one by one on top of a stack of the other four cakes, secured by white icing. Poke a hole in the tops of each of the cones, then sprinkle each one with edible ...

This is a video on how to weave in ends on kniting. First take two ends at a time, tie the new color and a half not around the current working color, and tie them. The thread the end onto the yarn needle, and go througha few of the yarn stitches. Next give it a little pull to make sure nothings coming loose. Go up to the next yarn ends, and do the same thing. What you have to make sure you do is weave the yarn through light colors. Also make sure the knots are secure, and are not going to com...

In order to make a Silicone Ring Mold you should first get a small plastic container. This will be your mold box. First, you should cut the bottom out of the container. Next, use double sided tape to stick the ring down to the base of this. Next, secure the mold walls to the base. Now, mix the silicone mix in a separate mixing cup. Make sure you mix this thoroughly until the color is uniform. Now pour the silicone into the mold in a fine stream on the side of the ring, this will help prevent ...

How to make a great green apple martini. First we start with the tools of the trade, you will need a glass, champagne or martini glass will do, next a set of tumblers, a speed pour-er, and a martini strainer. Now that all of those are laid out we need to chill the glass down, so take the larger tumbler and fill it 3/4 full of ice. Add the ice to the glass and set aside. While the glass is chilling out, we need to get our liquor out and ready to mix, these are the liquors needed:

In this how-to video, you will learn how to make a small jug with a handle using a wheel. Place the clay onto the wheel and start spinning it. Grasp it with your hands as it spins and make a vertical shape. Use your thumbs to make the interior bowl shape. Now, use your hands to make the clay more vertical. Keep doing this until you get the desired height. Now, insert your hand into the interior to widen the shape. Make the top more narrow with your fingers. Make the edge stick out as well wit...

This video demonstrates how to create an origami ninja star. Prepare a square shaped piece of paper. Lay it down on a table or on a flat surface. Fold the paper right across the middle in a vertical orientation. Fold it once more in the same manner as the first fold, now creating a more slender vertically standing rectangle. Fold the upper portion of the origami diagonally forming a small triangle on top of the rectangle. Do the same on the bottom portion of the origami. Fold the upper portio...

This video demonstrates how to make a balloon light saber. For this project, you will need the following: long balloons.

Learn how to ‘Paint onto your T-Shirt’ by watching this video. Materials required for this include the following:•Marabu Textil Plus Start Kit – 6 colors included with paint brush•Marabu Metallic Outliner Paints•Crocodile clips•Masking tape•Pencil•Design printed from the computer•Tracing paper•A large cardboard wrapped in cling film•A dark colored T- ShirtBegin by placing a tracing paper over the design and secure it to the table using masking tape. Next, use a pencil to trace the design on t...