One of the biggest features to come out with Android O was the addition of a new System UI Tuner submenu that lets you customize the navigation bar at the bottom of your phone's screen. But as it turns out, this same feature can be enabled on devices running Android Nougat, even without root access.

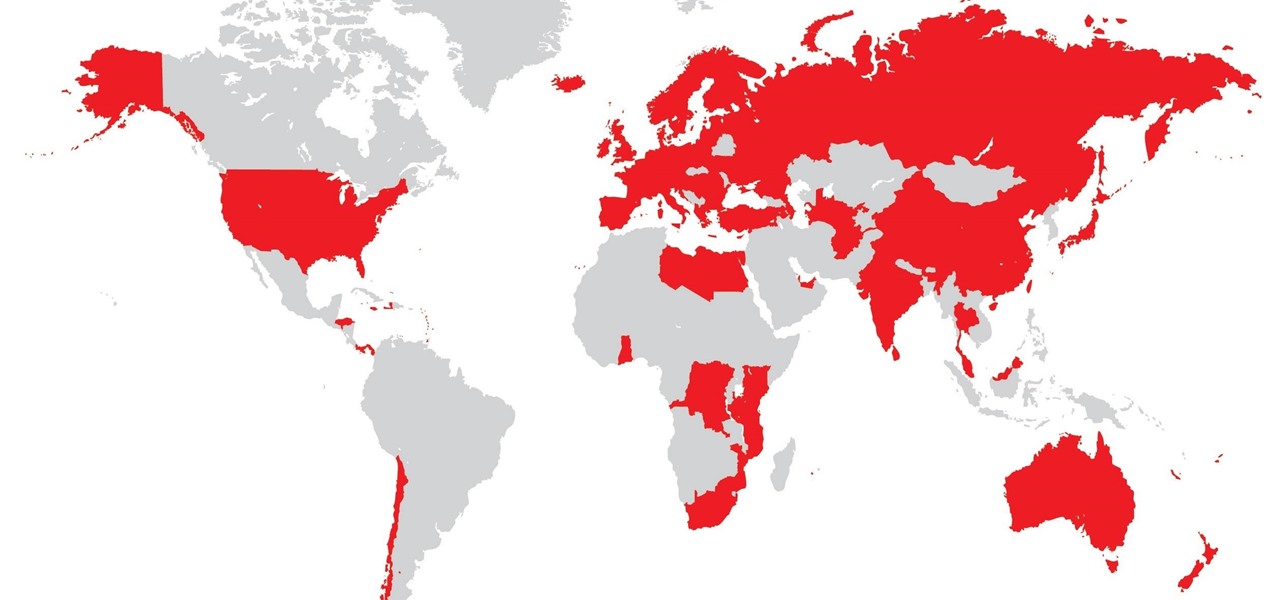
Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

If you ever imagined turning the surface of your desk into one large augmented computer, well the future might not be far off, my friends. Lampix, the company that transforms any surface into a smart surface, is currently working on a portable and quite fashionable lamp to project an augmented computer onto any surface that you can interact with using your hands.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

As with any new smartphone (but especially with Apple), the iPhone 8 is generating rumor after rumor. This newest rumor, however, rocks the boat a bit, as BGR reports that the iPhone 8 may release at Apple's standard time in the fall, but the 3D camera will be pushed to the 8s.

Dreaded are the days when you're working on a masterpiece, then all of a sudden, your Windows computer crashes, loses power, or an app just gets up and quits. Well, now there's an app for that.

Vodafone India has merged with telecom company Idea Cellular to become India's largest mobile player this week.

We live in a computer world full of file formats. Whether we are talking about images, videos, or text documents, there are dozens of file types for each, and there are new ones added every year to applications. Keeping in mind that many of these formats were created before the internet was widely available (at least, in infant form), the primary reason for this glut of often complex choices is competition.

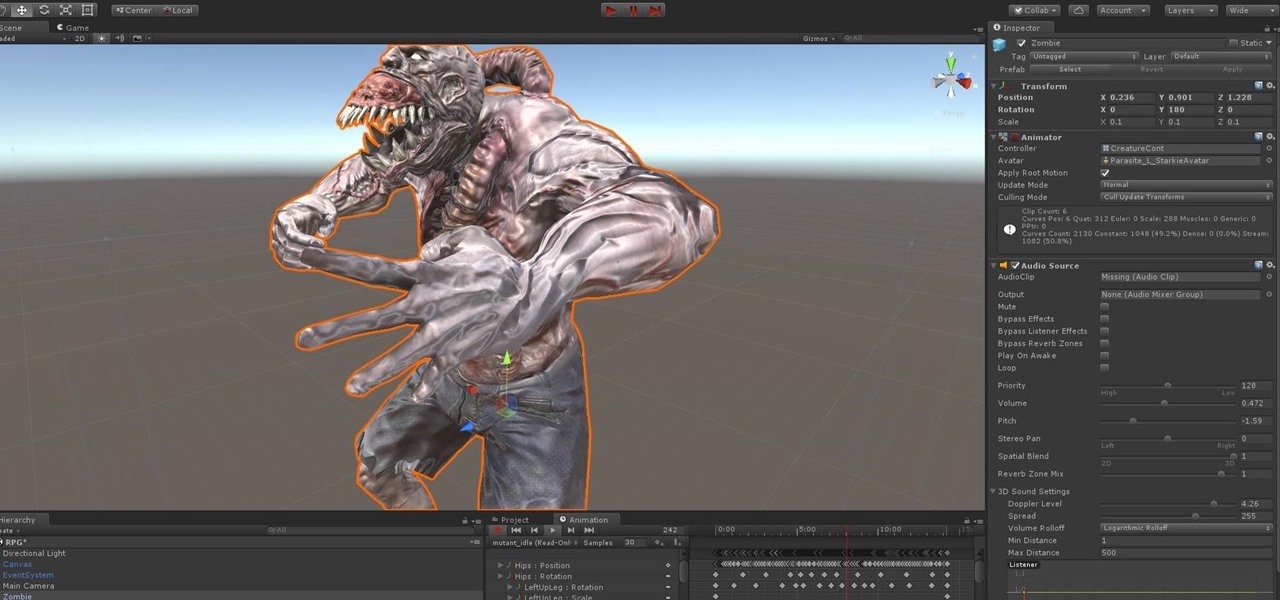
Any developer working with the HoloLens knows that the fight for polygons is a very real conflict. For all of the magic it creates, the HoloLens is a high-powered mobile device that has all the typical processing limitations of a mobile device.

Since the 1960s, bacteria have been hopping a ride into space on space vehicles and astronauts, and have been cultivated within experiments on space shuttles and the International Space Station (ISS). The extreme growing conditions and the low gravity environment on the Earth-orbiting vehicles offers a stable research platform for looking at bacteria in a different light.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.

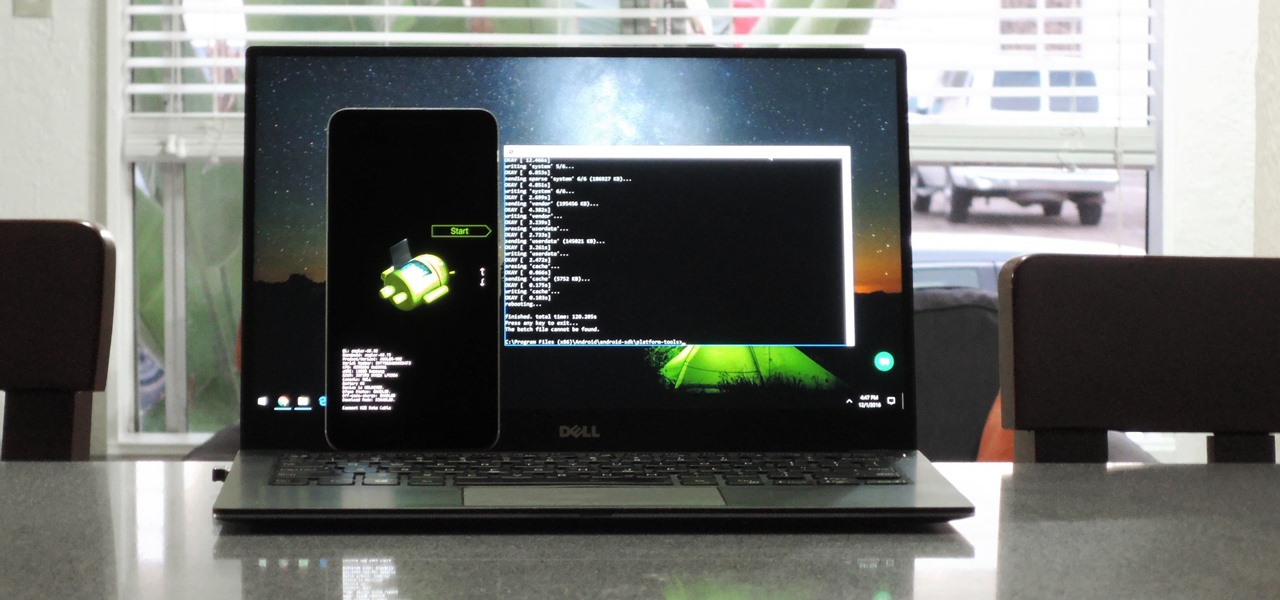
If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

Blue light (like that from our smartphone) tricks the human brain into thinking it's still daytime, even if it's coming from something as small as a screen. So while you're playing around with your new Pixel or Pixel XL after dark, subconscious signals to be awake are preventing you from getting to sleep as early as you should.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

When you think about consumer VR headsets, you either imagine a computer-tethered powerhouse like the Oculus Rift and HTC Vive, or something portable yet limited that utilizes your smartphone like Google Cardboard. Somehow, we haven't seen much in-between, but the Idealens aims to fill that gap.

The most genius summertime snack hack that we've come across recently is, without a doubt, the campfire cone. Astounding in its simplicity and ease of preparation, yet brilliant in its execution, the campfire cone has something for everyone: parents and children, expert and novice campers, backyard barbecuers, and oven lovers alike.

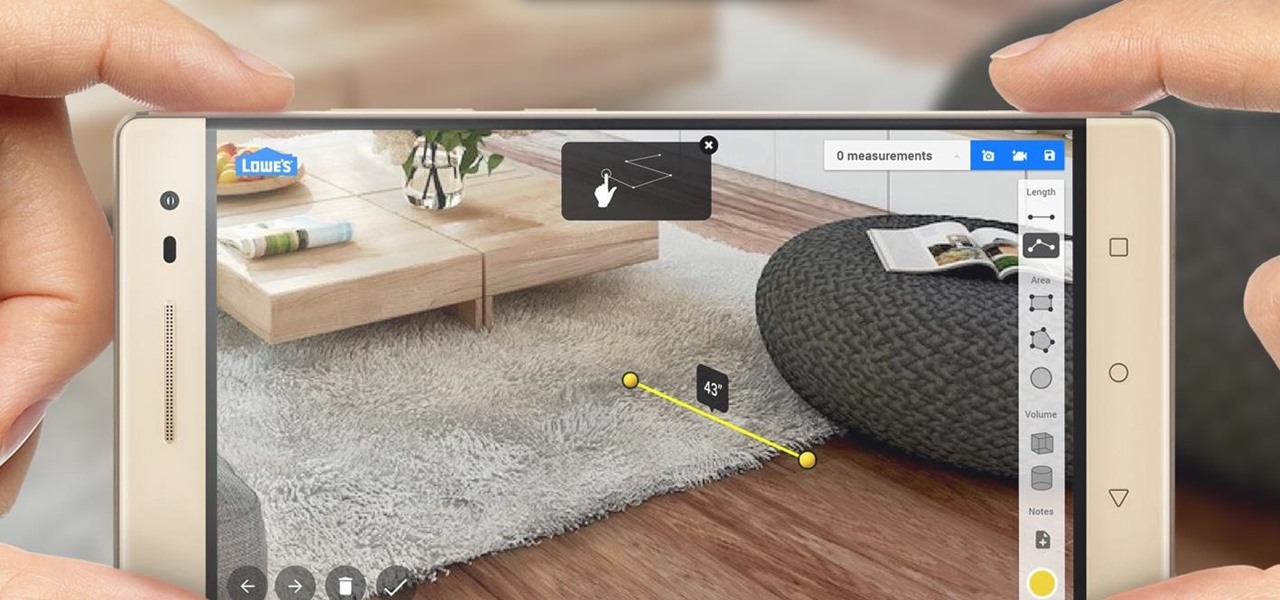
Augmented reality began on smartphones but technical limitations have prevented further development. Google's Tango (formerly Project Tango) aimed to change all that, and with Lenovo's help, they now have their first device.

Got some seriously sensitive information to keep safe and a spare-no-expenses attitude? Then the new Solarin from Sirin Labs is the smartphone for you and your $17,000.

When Android Nougat is released sometime this fall (or sooner), a new feature called "Quick Reply" will allow users to respond to incoming text messages directly from the notification. It will definitely be nice to carry on a conversation without leaving the screen you're currently viewing, but unfortunately, most of us won't get that Android Nougat update for quite some time.

Using a fingerprint scanner to keep intruders out of your phone might not be as secure as you think. Two researchers from Michigan State University, Kai Cao and Anil K. Jain, developed a relatively cheap and effective way to beat fingerprint readers, and successfully tested their method on a Samsung Galaxy S6 and Huawei Honor 7.

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.

Apple's once flawless mobile operating system has seen its fair share of bugs recently. From Messages and Wi-Fi settings crashing to having your photos and contacts exposed, iOS has been standing on shaky ground for a while now.

Five Phases of Hacking:- The five phases of Hacking are as follow:

A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.

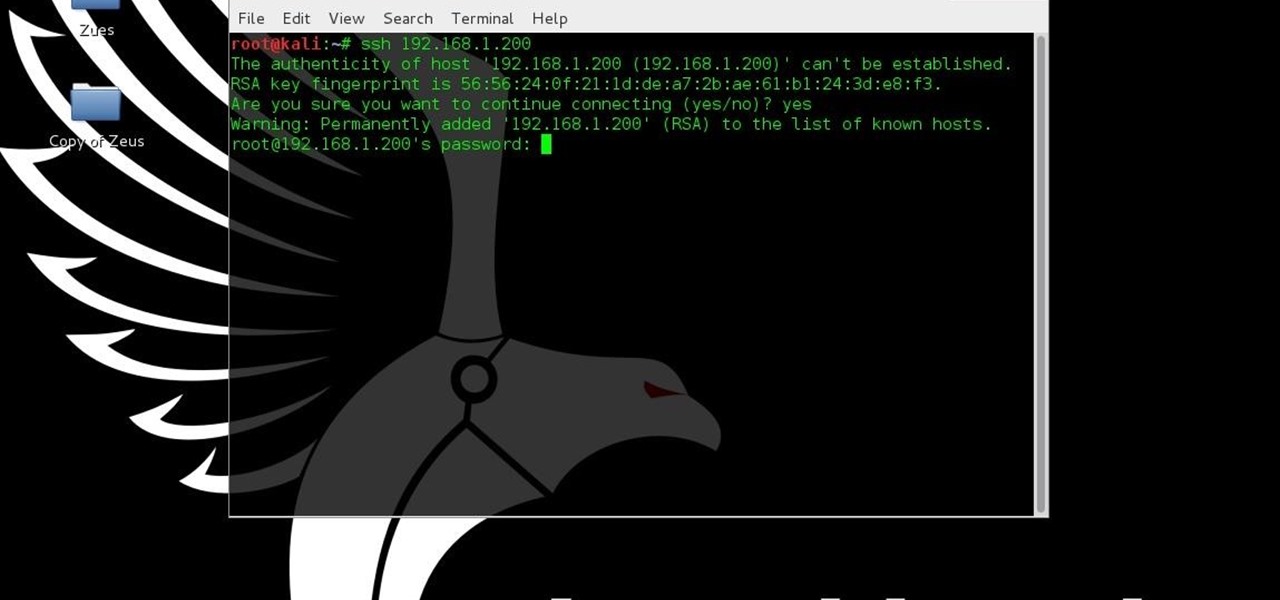
I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

Dropping upwards of $60 on a new game can really break the bank, and being a struggling college student leaves me having to decide whether to pick up the latest title or, you know, eat. But often my more primitive urges win out, meaning the only way to enjoy the latest and greatest games are vicariously, using increasingly-popular live streams.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

Thanks to the internet and its increasingly lack of privacy, secrets don't even seem safe in our own homes anymore. So how do you hide your secrets, stash your cash, or keep your valuable jewelry out of sight where no one can find it? Well, the answer might be right above you... if you're standing under the threshold of a door, that is.

Raw fruit "cakes" are all the rage these days, and this stacked watermelon cake is easy to put together and is perfect for people of all ages. It's also perfect for every diet, as it's low-calorie, low-fat, gluten-free, and full of "good" carbs.

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

bObsweep Standard and Pethair are made to easily transition between a variety of floor types, so they function efficiently in most spaces.

Your Apple Watch only looks as good as the band that it's bound to, but if you're looking to purchase one directly from Apple, expect to spend anywhere from $149 (for the Milanese Loop) to $449 (for the Link Bracelet).

Presented by Apartments.com When looking for a new apartment, it's hard not to notice the improvements (on large and small scale) needed prior to moving in. While your landlord may be taking care of new carpeting, cleaning the central air vents, and fresh paint on the walls, there may be some additional improvements on your list that you can take care of on your own. Here are five quick improvements you can check off your list before the big move.

They might be a little late to the party, but the Cyanogen team has finally released their newest ROM for the OnePlus One, Cyanogen OS 12. The launch had to be pushed back a few times due to some technical issues, but now we finally get to see what the Cyanogen team has cooked up for Android Lollipop.

Reddit is one of the internet's greatest sources of funny and interesting videos. Its user base is extremely active, and a system of upvotes and downvotes ensures that the best content always rises to the top.

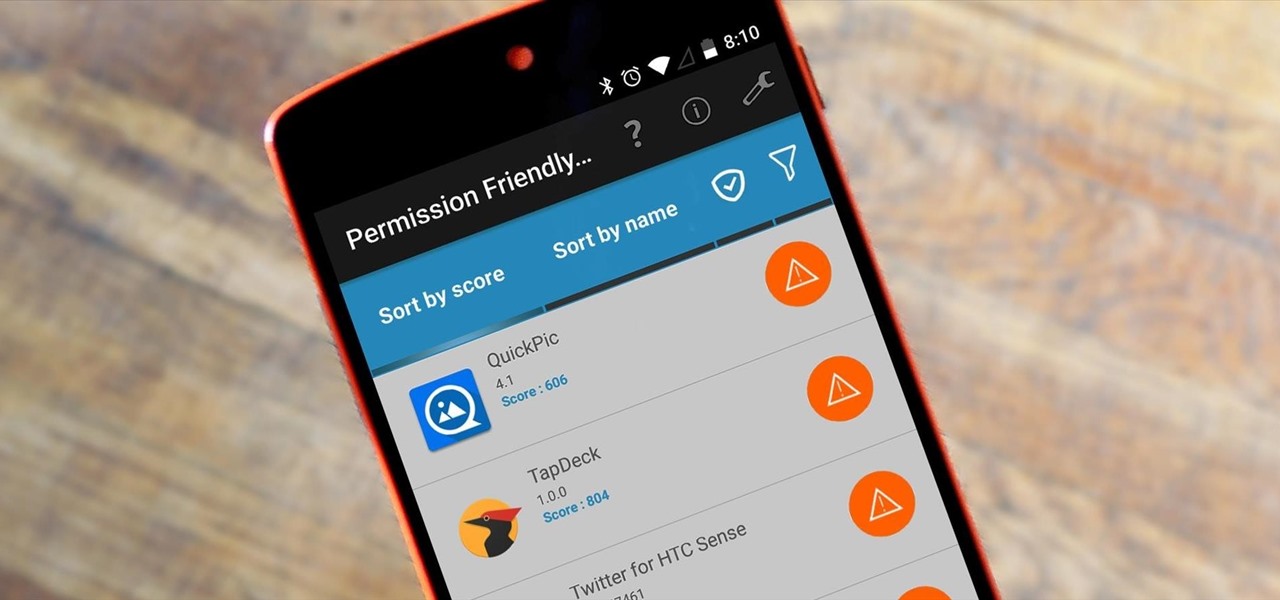
Android's permission system doles out access to certain system-level functions. Without it, our favorite apps wouldn't be able to perform their most basic operations. Picture a camera app that didn't have permission to access your camera sensor—now that wouldn't be much fun at all.

Before phones became mobile-gaming, music-playing, app-downloading devices, they were used simply to make convenient, cordless phone calls. There's so much on phones these days that a passcode is needed to keep everything secure, and making calls is now more complicated.