When Apple released their plus-sized iPhone 6 and 6 Plus models, it only made sense that they would include a one-handed feature to accommodate the larger displays. That particular feature is called Reachability, and with just a quick double-tap of the Home button, the screen shifts to the bottom half of the device for easier use with one hand.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

The weather outside might be frightful, but heating bills are downright scary this time of year. Heat is absolutely essential during the winter season, but it's also really expensive. If you aren't blessed with a fireplace or unlimited disposable income, fear not, because you can still heat your home on the cheap using flower pots and tea lights—even if the power goes out.
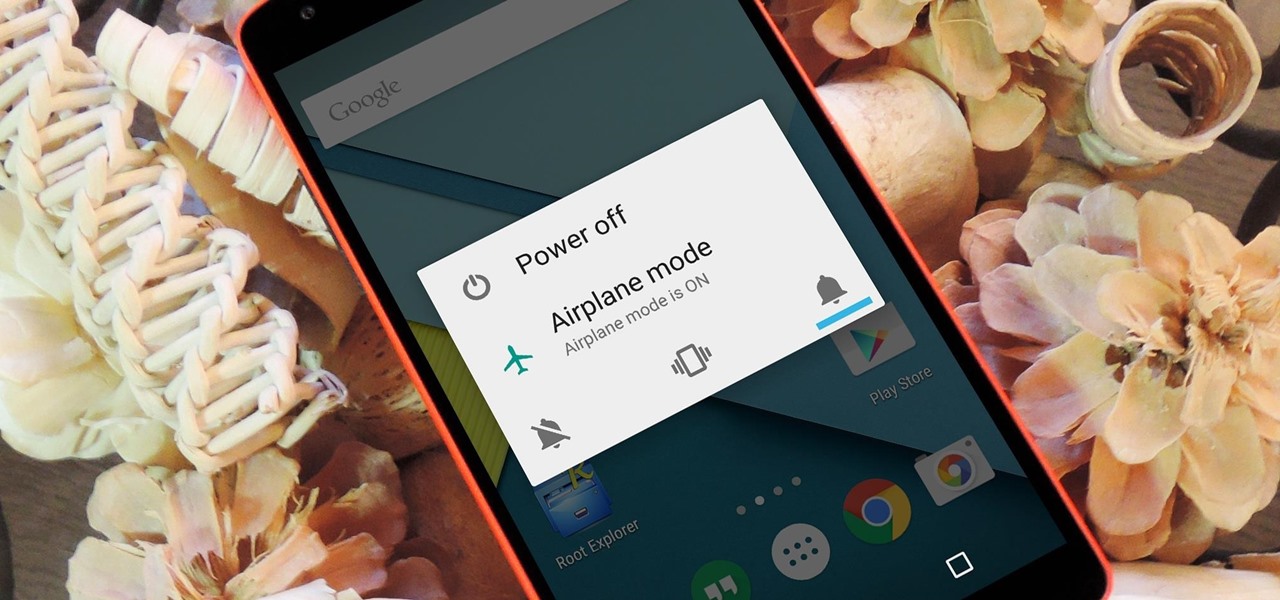
In an effort to make things simple and more secure, Google decided to slim down the power menu in Android 5.0. What once provided a quick link to shut your device down, turn on Airplane mode, and toggle volume states, has now been relegated to a simple power switch. Lucky for us, developer Gar Ynych has created a flashable ZIP that will revert these changes and restore functionality to the Nexus 5's power menu. In a few simple steps, you can add the volume toggles and Airplane mode switch rig...
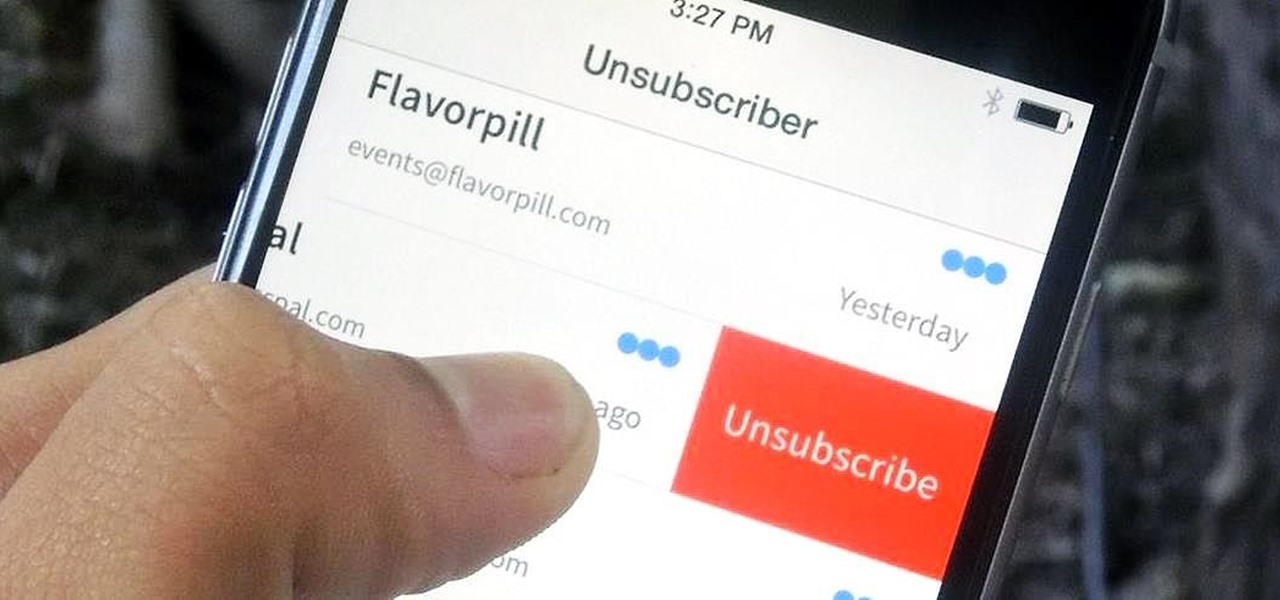
You've undoubtedly used your email address to sign up for a chance to win something online or to purchase something on sale. Often, these offers are too enticing to pass up, and you reason that you'll live with the consequences of handing out your information for the chance at making out big.

Whether you use a third-party keyboard or the stock offering, your Samsung device keeps a history of the last 20 words you copied on its clipboard. Samsung added this feature to Android to help make multitasking a bit easier, but if you use a password manager like LastPass, this feature quickly becomes a gaping hole in security. While you're copying and pasting your various passwords, the last 20 of them become freely available to anyone that gets their hands on your device.

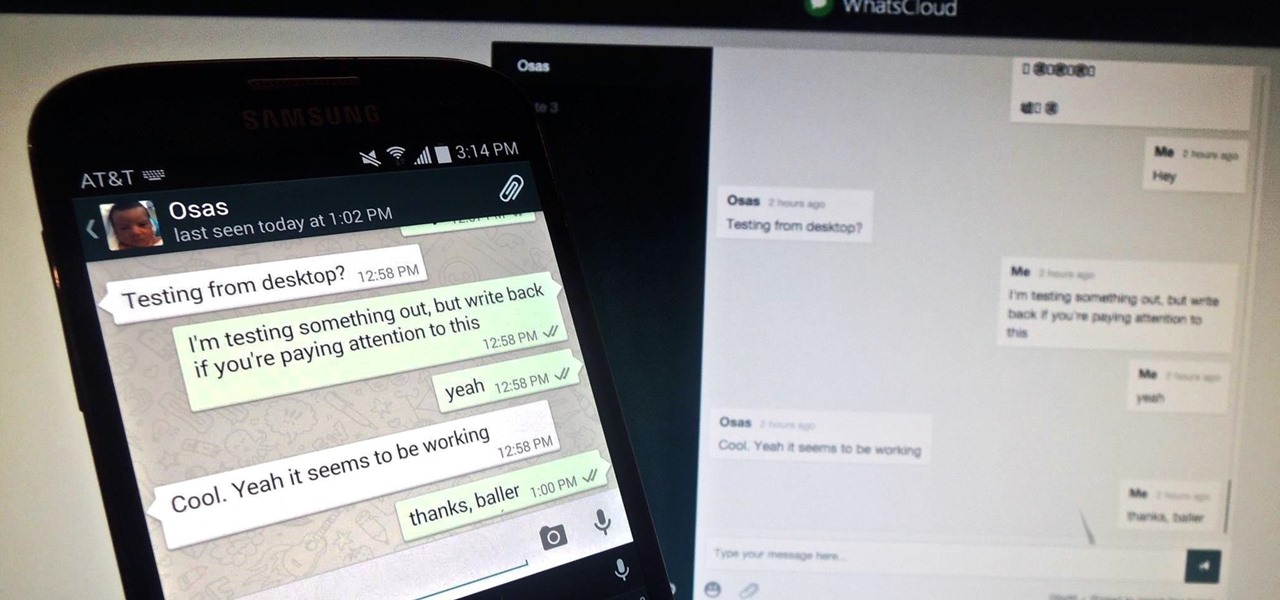
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.

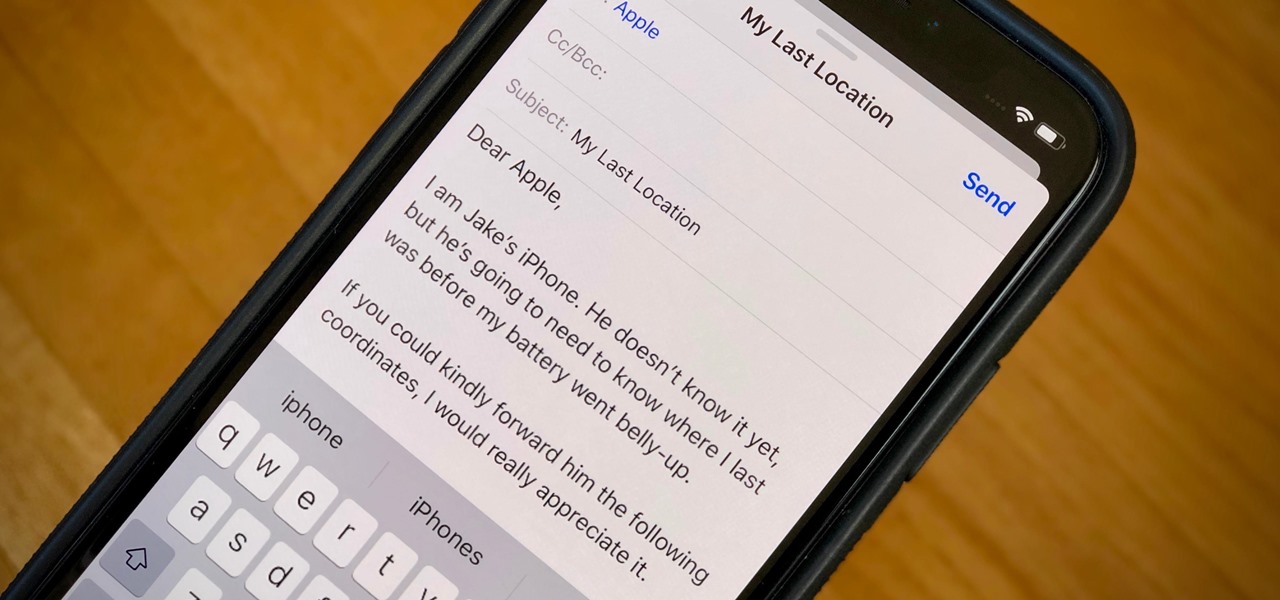
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.

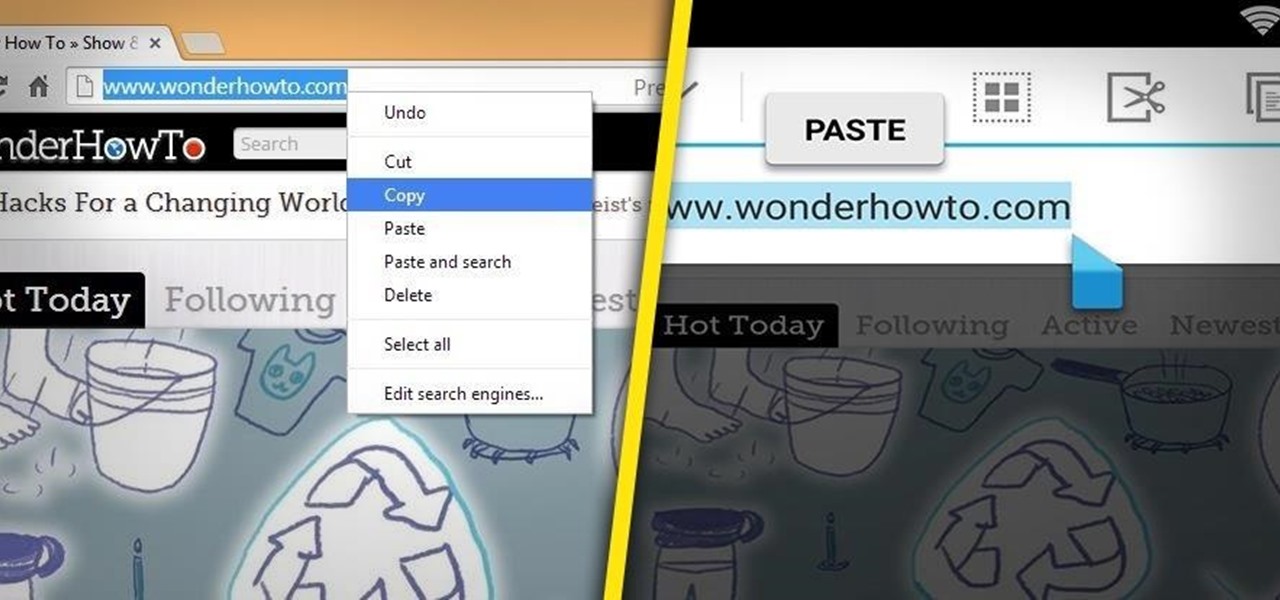
Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.

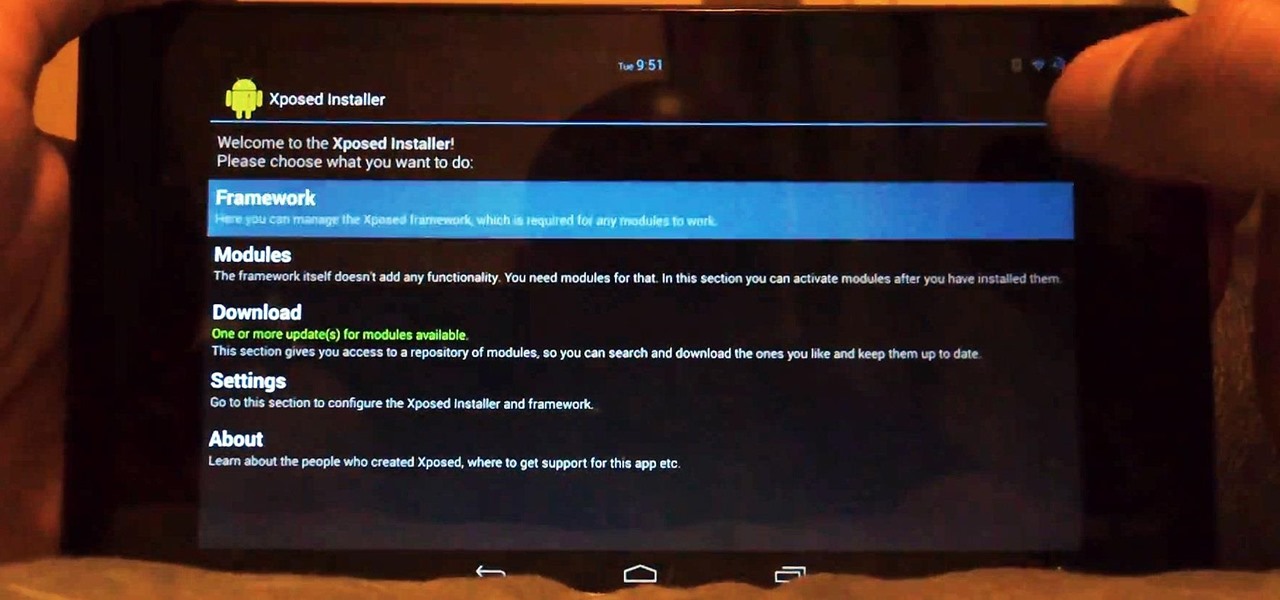
With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.

It's been a long-rumored feature, but today, VoIP calling has finally started rolling out to users of Google's Hangouts service. Essentially integrating Google Voice into the popular messaging platform, Google has given Android (as well as iOS) users an easy way to make calls without eating up their plan's minutes.

Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side.

Being healthy and active will help you live longer, but finding the strength to work out? That's hard. What does it do for me right now? I mean, here I sit, writing this article, thinking about going for a run, and I feel good just for thinking about running. But will I do it? Nah, I'm too lazy.

Pushbullet is one of those apps that helps separate Android from its competition. By pushing the boundaries of cross-platform data syncing and file sharing, the service truly demonstrates how flexible and robust the world's leading mobile operating system can be.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

One of the coolest features of the Galaxy S5 is its IP67 certification. This means that the S5 is internally impenetrable to dust and can be submerged in water for thirty minutes at a depth of one meter. It's definitely a handy feature for folks who've lost a phone to a toilet in the past.

There are over one million apps in the Google Play Store, and many of them are restricted to certain device types, brands, and Android systems.

Update, November 12, 2014: Android 5.0 Lollipop is officially out now. If you haven't gotten the OTA yet, check out our new guide on installing the official Lollipop builds on any Nexus for download links and instructions, for Mac or Windows.

It's the biggest day of the year for all things Google. Their developer conference, dubbed Google I/O, gives us a peak at what the guys at Mountain View have been working on over the course of the past year, and this year, Android was center stage.

Lock screen apps are a dime a dozen, but every now and then one pops up that defies expectations. We've already covered some good ones for the Samsung Galaxy S4, including Picture Password Lockscreen (which gives you secret unlock gestures), SlideLock (which improves notifications), and TimePIN (which gives you a more clever PIN).

In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

Figuring out someone's password, pattern, or PIN isn't very difficult—simply watching over their shoulder or following the oil marks left across their screen is enough to figure them out and bypass whatever lock screen security they have.

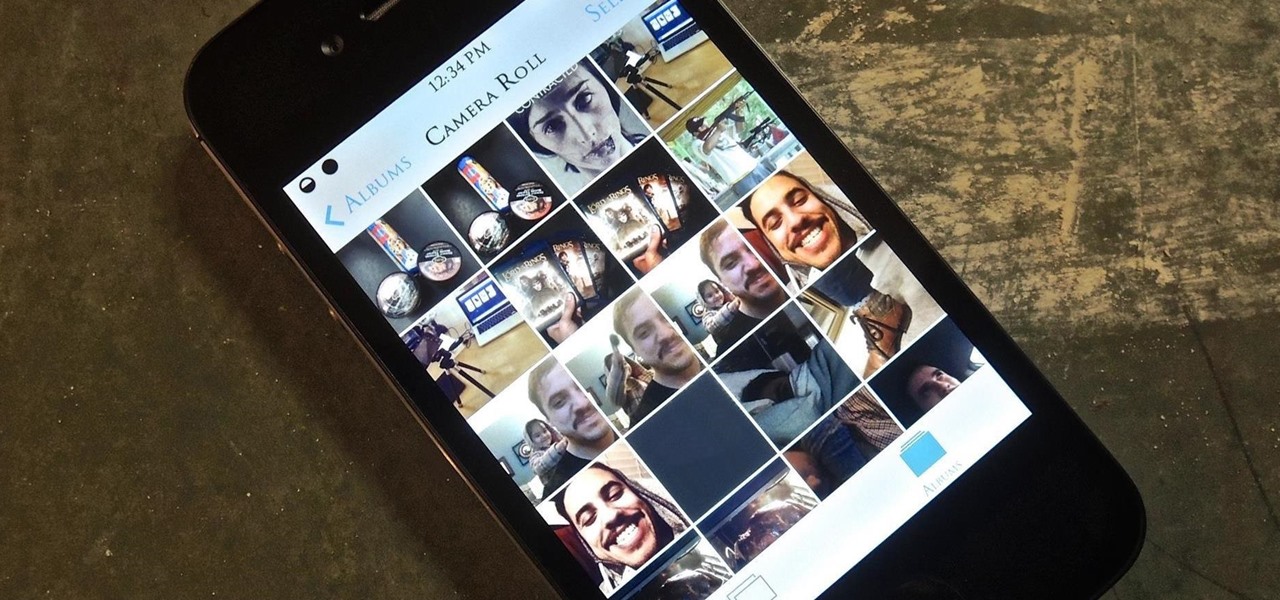
I have over 400 photos on my iPhone, and I don't even know where half of them came from. Scrolling through all of those pictures is a pain in the ass, but it's not nearly as bad as trying to actually find an old image. Organization is not my strong suit, so I'm definitely not the type to create new albums to sort through my 400+ photos.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

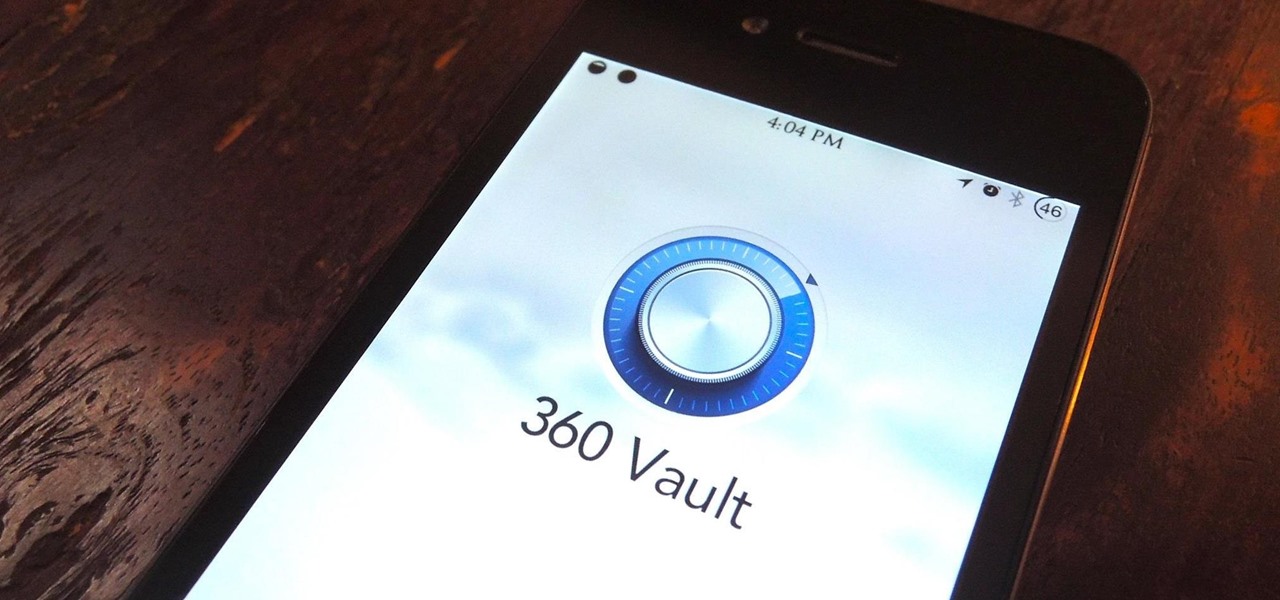
Let's be honest for a second; we all have sensitive material on our phones that we wouldn't want anyone else to ever see. Maybe it's to protect ourselves or someone else, or maybe it's none of your business why I don't want you to see pictures of my bachelor party. Regardless, sometimes we need to keep things hidden and safe.

One of the best things about iOS 7 is the Control Center, which gives you quick access from anywhere on your iPhone to turning on or off Airplane Mode, Wi-Fi, Bluetooth, and more. It also makes it very easy to adjust the brightness of your display, and gives app shortcuts for your Flashlight, Calculator, Timer, and Camera.

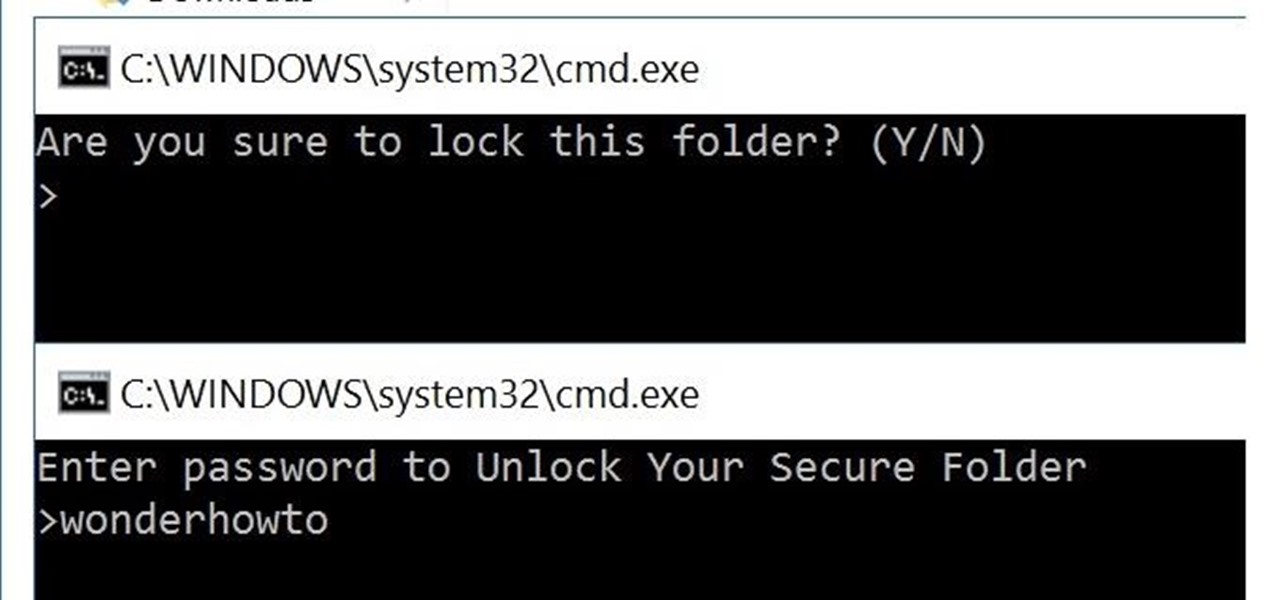
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

We will show you with easy step by step instruction how to create a beautiful edible apple swan. This swan is easy to create and can be done in under 5m. Makes for a great centre piece during a special dinner.

There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.

The high limit thermostat can be found in gas and electric dryers and serves as a safety feature that helps to prevent the dryer from becoming too hot when it’s running. The thermostat is designed to shut off power to the dryer’s heater when the dryer vent is blocked or clogged. The high limit thermostat on your dryer is something that does need to be replaced from time to time. Fortunately, it is a job that you can do on your own with basic tools.