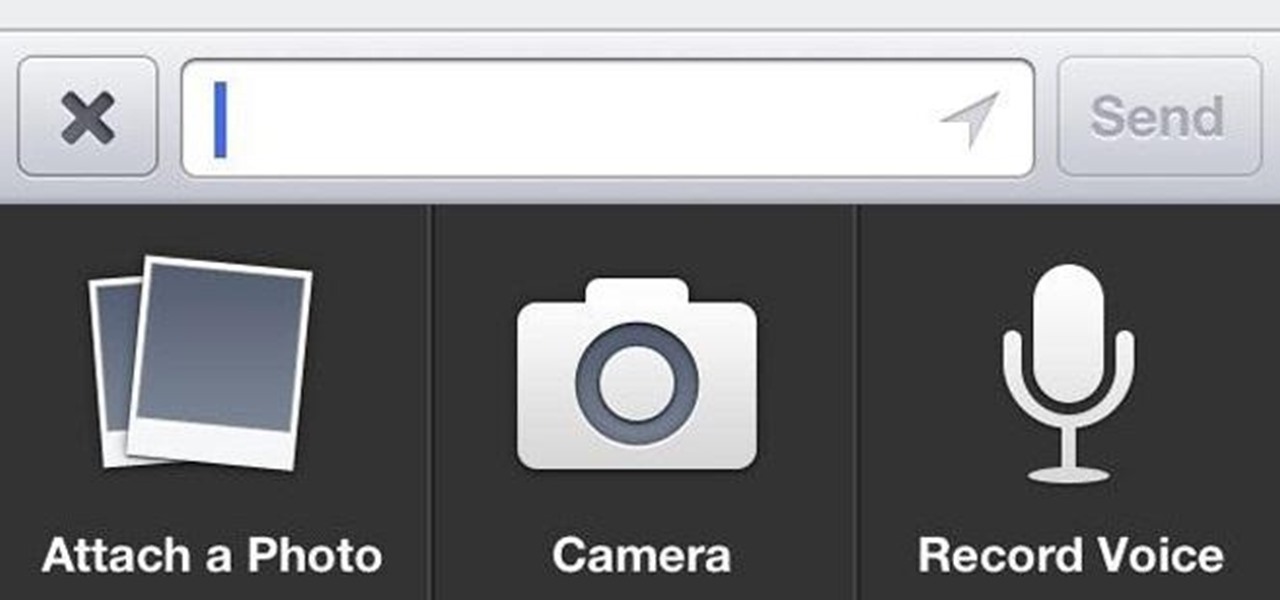
Facebook has been revamping its Messenger apps these past few months, trying to lure in more users. Competing in an already crowded market of third-party messaging applications, Facebook Messenger just upped the ante, by introducing voice messaging.

After everyone updated their shiny Apple devices to iOS 6 a few months ago, they were shocked to find that their beloved YouTube app was missing. As it turned out, Apple decided to kick YouTube off their list of pre-installed stock apps. The new YouTube app (found in the iTunes App Store) is definitely better than the native one from iOS 5, but it's lacking a direct upload to YouTube option. Sure, you could upload videos from your iPhone's Camera Roll, but the options are limited as to what y...
Facebook has always been notoriously difficult to customize. Personally, I think this is an improvement over MySpace's totally open platform (some people should not use code), but users should still have the option to change a few things if they want. While you'll never be able to choose your own background image or add an obnoxious number of aWeSoMe quiz results to your profile, there are a few browser plugins that let you at least change the color scheme.

It's tough out there on the battlefield, especially when your stuck in the trenches and your comrades are dropping like flies. There's no hope. At least, until the next airsoft battle.

Here's a way you can turn a mousetrap into a fun little handgun that shoots up to 40 feet! This is a great project because it can be made with simple materials, very basic tools, and in just a few minutes!

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

Drinking games just got a little more sophisticated (kind of). Startup SmartThings built this awesome Arduino-based machine that automatically pours a shot whenever the US wins a medal in the 2012 Summer Olympics. Goldschläger for gold, Cuervo for silver, and Jack Daniels for bronze.

Grab your long-handled wooden spoon and let's get to bed making. There is a science in making the immaculate and consistent military-style bed. Use this method at home and know that your making your bed just like soldiers do every day.

In this tutorial, we learn how to build a PVC greenhouse. The dimensions of this will be 12' x 18'. First, you will use 1/2" PVC pipe that is 12' long that crosses in the middle to make a "t" shape. The frame can be made of treated 2'x 4's. Once you have the frame up, you can use thick plastic to securely cover the pipe and wood and clamp it into place. Once you have this done, you can place your tables inside of the greenhouse and start growing your plants! If you notice the plastic not hold...

In this tutorial, we learn how to get rid of wasps and hornets without using chemicals. Take a piece of bacon and wrap it around a stick. Then secure that stick by hanging it over a bowl of water with dish soap on it. The bacon will entice the bees to come towards it. Then, the bees will eat so much bacon they will have a hard time flying and they will end up flying down into the bowl of water. Then, the soap will make them be able not to fly and they will drown in the water. This is very eff...

There are two basic ways to twist hair so that it lies on the scalp. One way to twist the hair is to section the hair into the desired size of segments. Use one hand to twist the hair with the thumb and forefinger while holding the hair down secure with the other hand. Another way to twist hair is to separate the section into two pieces. Twist one section over the other and pick up another piece while twisting the strand around again. This will feel similar to braiding, but with only two stra...

Happy140 demonstrates how to fold and wear a bandana. Folding a bandana and placing it securely onto your head for everyday use is easy using a few simple steps. The first step is to take the bandana and fold it into a triangle so that all the points touch each other and are even. Then, fold the top point down so the bandana forms a trapezoid shape. The next step is to fold the bandana in half lengthwise. Wrap the bandana around your forehead. Tie the ends of the bandana into a knot behind yo...

This video is a tutorial explaining how to erect a tipi shelter. You must make sure all poles are 11' by 10' to have the correct height tipi. The instructor then aligns three marks and ties a clove hitch around all three poles. The next step is to raise the pole by using the rope to keep the structure stable. The next step involves putting the covering onto the lead pole and the bring the covering around 360 to complete. The last step involves securing the covering with rope by tying a knot a...

This video demonstrates how one can makes a homemade paint ball caddy on the cheap. The presenter uses a gallon sized kitty litter bucket. The presenter only spends $8.00 on the kitty litter bucket at Costco and it will hold at least two bads of paint balls. The presenter demonstrates how he added another screw top lid to the kitty litter bucket. By simply cutting a circle the same size as an existing screw lid and then super gluing the lid inside the kitty litter bucket, you have a secure se...

Find the indication light, located at the top of the Whirlpool refrigerator just inside the door. This tells you when to change your water filter. A green light indicates the filter is good and a red light indicates you need to change the filter.

Make sure your electronics gear stays in order! And make sure your running wires are safe. Check out this video tutorial from the Good Idea Guys at Good Buy Guys to learn how to tape down a cable correctly. Keep those microphone cables, audio cables, and extension cords secure and safely underfoot. Tape Tex shows you how in "How to Tape Down a Cable". A great helpful tip for cable safety.

Google Earth is a great tool of the web, if you know how to use it the right way. Learn everything you need to know about using Google Earth in this powerful video series set to show you all the basic maneuvers and tricks to using the well known application. Google Earth is a cross-platform program, so the steps shown in this video series will work on Windows operating systems, as well.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

This week, the beginning of an epic legal battle was set to begin between augmented reality players Magic Leap and Nreal, the small China-based startup accused by the former of stealing trade secrets.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

When Apple acquired the popular Workflow app in 2017, many were worried that it would either get replaced with something much worse, or just disappear entirely. Thankfully, Apple put these concerns to rest with the launch of Shortcuts. In iOS 13, Shortcuts is becoming more powerful than ever, providing functionality on the iPhone that the original Workflow team could only dream of.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

The last time we heard from Meta, the makers of the Meta 2 augmented reality headset, things looked pretty bleak. Now, as several new facts have come to light, we have confirmation regarding the beleaguered company's fate: Meta is done.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

After years of struggling, it appears BlackBerry has finally figured out how to update its iconic design for modern times. The BlackBerry KEY2 pays homage to past devices such as the Bold 9000 while adapting to modern times with the Android OS. The result is a device that might be the best BlackBerry to date.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.