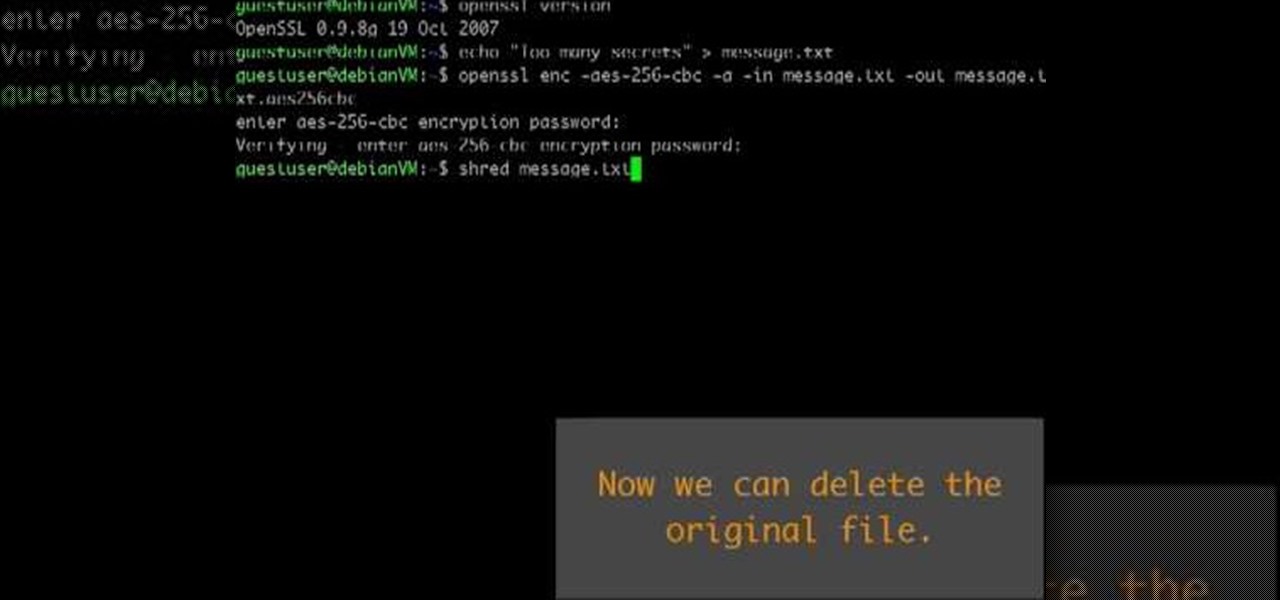
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...

Debra Hardy provides detailed instructions on how to make darling decorative Santa soy votive candles in this video. She first cuts the red felt into 6 3/4 inch by 2 inch strips for the Santa suit, wraps it around and adheres it to the bottom of the glass votive. Next, she secures a smaller strip of the white faux fur on top of the red felt also towards the bottom of the candle to create the bottom of Santa's jacket. Debra then instructs the viewer to cut a 6 3/4 inch by 1/4 inch black felt s...

Cocorais shows you how to style your hair into a Selena Gomez style up-do with short hair. Start by curling your hair, which is optional but it gives the hair shape and volume. Take your curled hair and sweep it to one side (opposite side of side-part if you have one), leaving a little hair on the other side to frame your face. Ignore any hanging hairs. Comb your hair into a ponytail, and tie it to one side. Gather your hair and tie it into a bun, using bobby-pins to secure it. For the rest o...

Crimp can be made easily and covered to the jewelry by using the following instructions. First purchase the proper supplies of crimping tool. This tool acts like pliers and is used by placing the bead in the appropriate slot at the tip and then squeeze the handle together. The multiple slotted tips are the key to the tool, and are needed to create a proper crimp. Then, select the proper crimp bead. The thin metal crimp beads come in a variety of materials and sizes. This will be used to secur...

Learn how to tie a perfect bow. To do a basic pony bow, place the gathered hair in the center of the ribbon and tie a single knot to secure it. Making two loops, cross one loop over the other and pull the loop on top through the hole you've created. Straighten out the ends and tighten so the two loops are on top and the two tails on bottom. Make a headband bow. Run the ribbon along the hairline, drawing the ends up on top of your head. Secure a knot and tie a bow. By tweaking the loops out a ...

This video teaches the viewer how to make a memo book with a paper bag. For this craft you will need two paper bags, memo paper, adhesive, ribbon, and scissors. To begin, you'll need to cut off the bottom of the bag and discard it. She explains where to make decorative edges on the bags before sewing them together or using hot glue. Fold and crease the open end down about one third of the way. Open and then fold a little farther down to allow room for the spine of your memo book. Repeat this ...

This video shows you how to use couplers for cake decoration using these steps: 1. Couplers usually come in two plastic pieces, a base and a ring. This system fits inside cake decorating bags or cones and allows you to use the same icing with different tips.

Worried about your baby or toddler either wrecking or wrecking themselves in your home? Baby proofing time! Make sure your house is safe and secure for your child when they start exploring their turf.

Save money on prom transportation by turning your parents’ station wagon into a one-of-a-kind limousine.

Seat belts save lives… but are you wearing yours the right way? Size up yours for a safe ride. You Will Need:

It’s never too late to clean up your credit record – and save yourself thousands of dollars in exorbitant interest rates in the process. Learn how to repair your credit with this guide from Howcast.

Moving is one of the top ten most stressful life experiences. Here’s how to pack it up without wanting to pack it in.

The modern knot is an updated version of the classic chignon. Here’s how to get the look. You Will Need:

Create a cute headband out of your own hair with this braiding trick. You Will Need:

Learn how to make an origami catfish. Get a piece of square paper. Fold diagonally from the upper right tip to the lower left tip of the paper. Fold the lower right tip to the upper left tip and open it up halfway. Hold the right fold and slightly open it placing your finger inside the flap. Gently press downward to create a square-shaped fold on top. Grab the left side of the square and fold it towards the right. Grab the other fold, the one made earlier, and do the same fold as the one done...

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

After adding dual cameras to its camera glasses, Snap is finally taking full advantage of the depth-sensing abilities of newer iPhones as well, extending the use of its new 3D Camera Mode.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

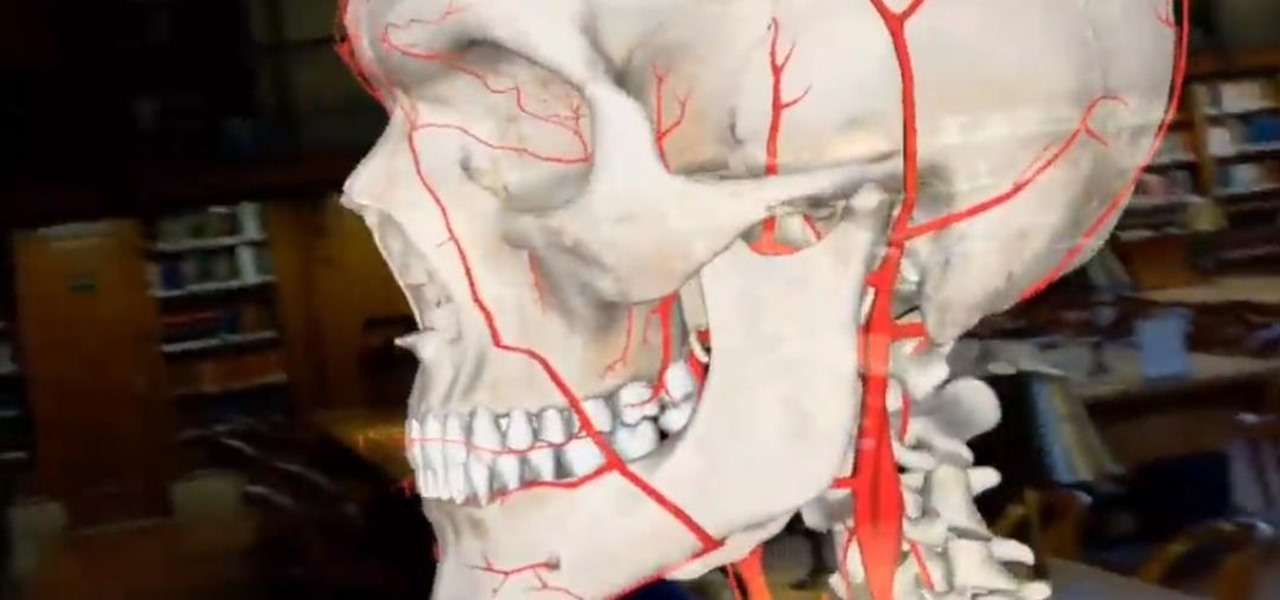
Not content to merely assist surgeons via the HoloLens, Medivis has expanded its augmented reality suite to Magic Leap One with an app for medical students.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

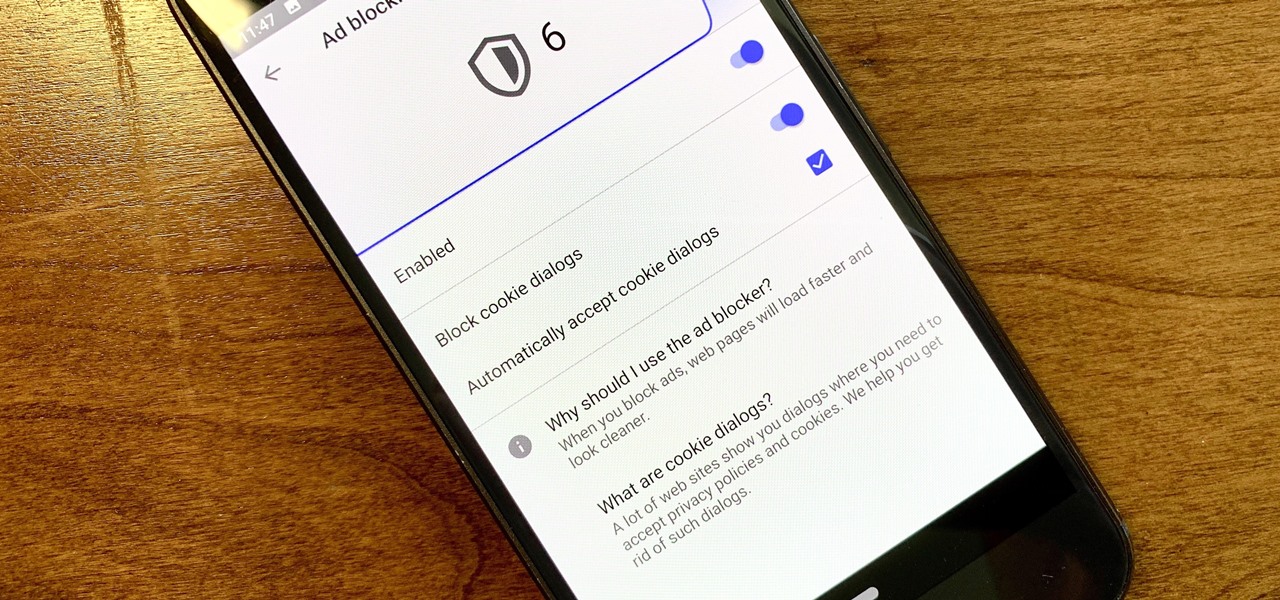
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

While Google has a water-resistant phone in the Pixel 2, its CES booth was anything but. According to Tech Crunch, Google had to shut down its two-level outdoor booth once it began to rain at the Las Vegas trade show. Even though Las Vegas is the driest city in the country, Mother Nature always has her idea of fun.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

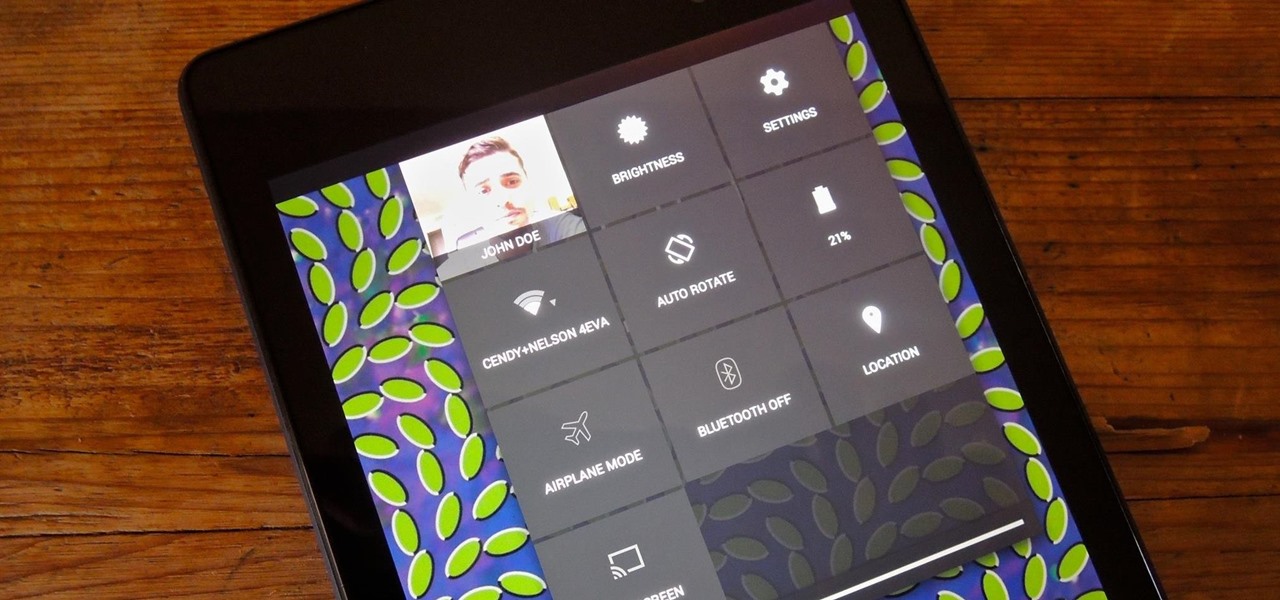
Accessing notifications and quick settings from the lock screen just makes things move quicker and more efficiently, unless of course we're using a secure lock screen. It makes sense that if we have face, pattern, or pin security enabled, we may not want notifications accessible, but really, that should be something we decide for ourselves—and now we can.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

This homemade hairspray-powered PVC rocket takes less than an hour to construct and only costs about 20 dollars to make. Check out my video below for the step-by-step instructions on building your own backyard rocket, and follow the written guide below for reference.

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

Oh how we love open source software. If it wasn't for Open Office, we never would have been able to write that seven-page English paper while on our friend's Microsoft Office-lacking laptop during an impromptu road trip to Mexico. And Ubuntu, an open source secure operating system, offers you similar convenience. A much more intuitive computer operating software than your standard Windows or Mac OS, Ubuntu is great if you know what you're doing.

Cake pops would cease to have a reason for existence without lollipop sticks. After all, the stick is the only thing distinguishing cake pops from plain cake.

Celebrites make party hopping look so easy. Flitting around from red carpet event to after party to after after party, they always seem to look so flawless in their pictures. But here's a little secret: They have some help from Hollywood's top hairstylists.

Wire wrapping is like the bread and butter of jewelry making. It doesn't matter if you're into vintage inspired, assemblage necklaces or Steampunk pieces - wire wrapping is essntial for securing everything in place and often times is even used as part of the decor.

In this tutorial, we learn how to make a photo cube. This project can be done in a couple of hours and only costs a couple of dollars! To start, you will first get an exact measurement of the width of your wood. After marking these, you will cut the wood using a band saw. After the eight blocks are finished, line them up in a cube and use clear packing tape to secure them together. Use a sharp blade to trip the tape. You can then open up the cube to show six different sides and tape your phot...

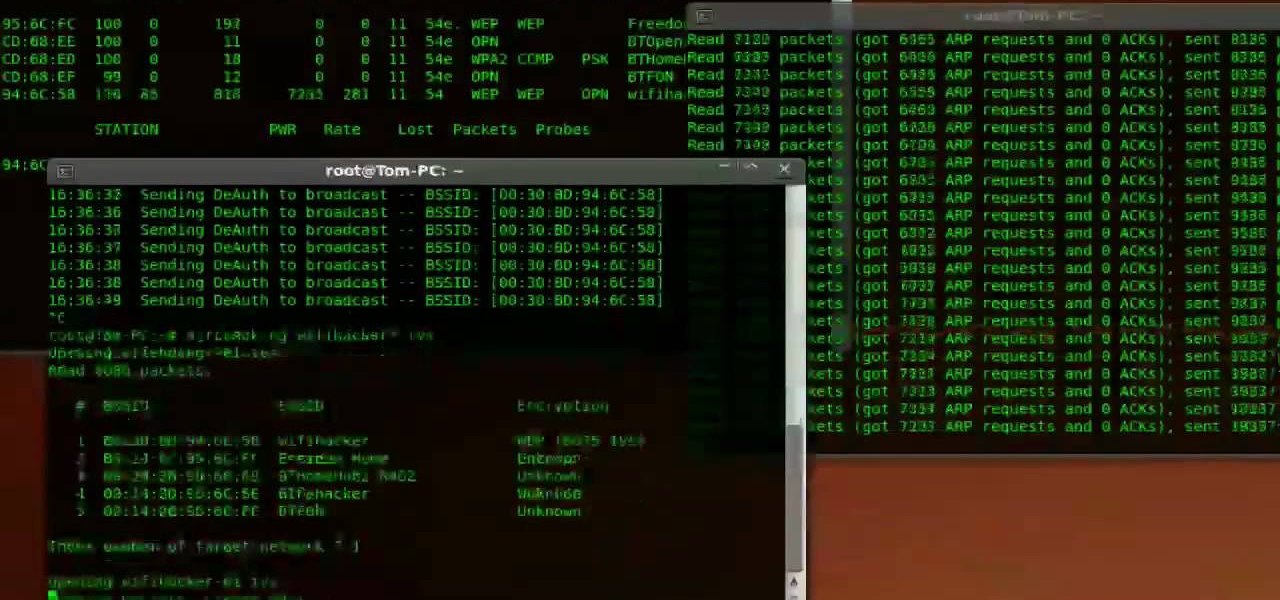
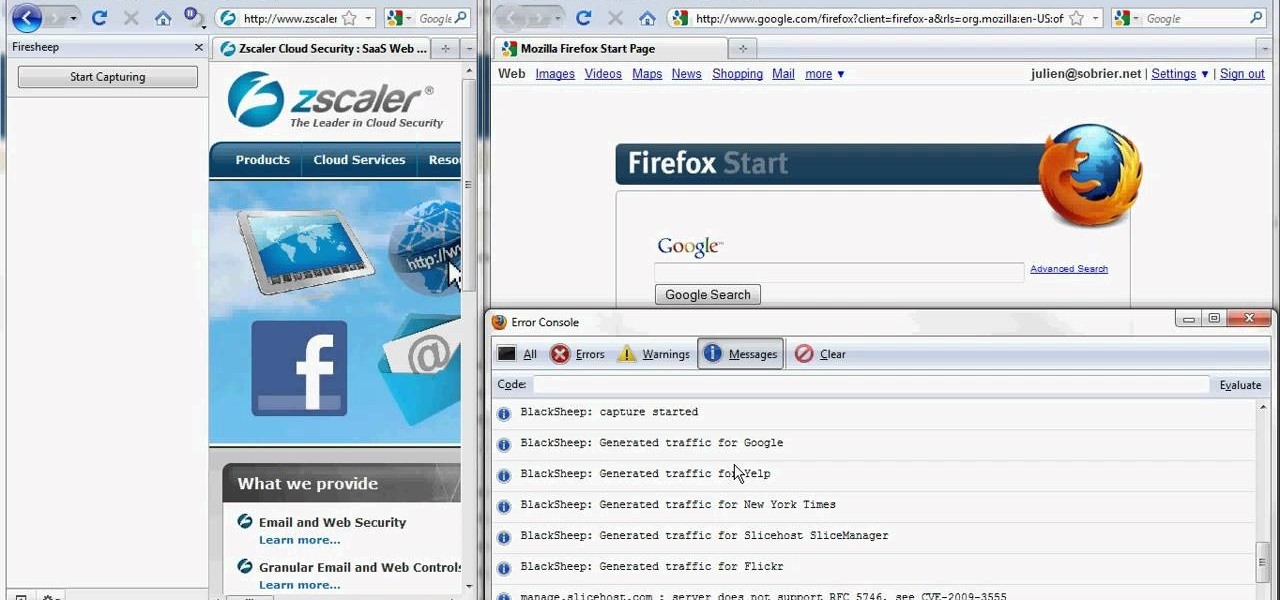
If you're scared of using public Wi-Fi networks with Firesheep out and about, then maybe you should fight back. Don't switch to another web browser— keep using Firefox safely with the help of a new Firefox Add-on that combats Firesheep's password stealing capabilities. It's called BlackSheep, and when installed and running, it will alert you whenever Firesheep is active on your network connection.

In this tutorial, we learn how to cross stitch. This is easy to master and just involves using one stitch. To start, you will first need to line your fabric up with the needle and mark the center. From here, secure it to the back with a small knot. Next, you will put this around an embroidery circle and then tie the thread to the needle. From here, start with the center point and count out how many spots you need to go on the design. After this, create a diagonal stitch across one block of th...

In this tutorial we learn how to build pet steps for your animals with Lowe's. Start out with making the lines for the sides of our steps on a piece of ply wood. Cut these out with a circular saw and then start assembling the steps. Use wood glue, nails and a hammer to do this. After you have these assembled from the bottom up you can insert the steps for the inside of the stairs. Make sure all of this is secure and everything is nailed in properly. Then, add in padding to the steps for your ...

In this video, we learn how to reconstruct a t-shirt into an off the shoulder top. First, take a large shirt of your choice color and cut along the line on the shoulder, leaving a 1/4" seam allowance. Next, roll the hem and sew with a sewing machine. Next, cut a strap 4" wide and fold in half, then sew along the edge. After this, use a safety pin to pin one side to the shirt and then to the other side of the shirt. After these are secure, draw marks along the neck line of the shirt. Cut out t...