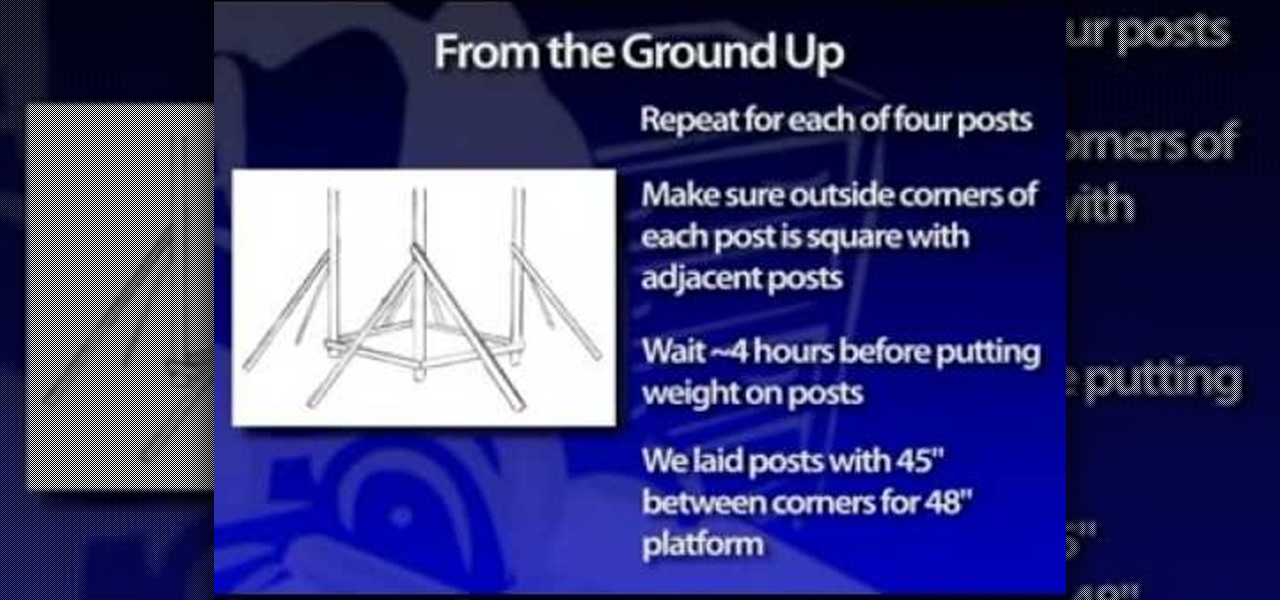
In this video tutorial, you'll find instructions for building a standard joist design playground slide, supported by 3-by-4 posts and secured with galvanized fasteners. All fasteners exposed to the outdoors must be weather-resistant, galvanized, zinc-coated brass or stainless steel. Standard homeowner tools are all you'll need to complete your slide—a tape measure, post-hole digger, circular saw, sawhorses and a level. A good drill/driver is a great tool if using decking screws as fasteners. ...

Keep your RV Entrance Steps in tip top condition with this instructional RV video. This tutorial demonstrates how to maintain and repair your recreational vehicle entrance steps. Most RVs have electric steps, which are fairly maintenance free. The biggest component is lubrication. Make sure to lubricate once every thirty days using a lithium-based grease and spray every point. Learn how to inspect the wires underneath your RV and make sure everything is secure. Just follow the simple steps in...

One important part of jewelery making involves properly attaching clasps. This how-to video jewelry making tutorial demonstrates the proper way to attach them. Begin by threading the crimp bead and the clasp onto the bead wire. Using chain nose pliers feed the thread around and loop it back around through the crimp bead. Use the pliers to hold the crimp bead tight. Crimp the bead down securing the wire and clasp.
Take a look at this instructional video and learn how to load virtual console games onto your Nintendo Wii. You'll need the Twilight Hack and an SD card for this process. The Twilight hack allows you to run unofficial software through the SD (Secure Digital) card inserted into your Wii. Since the Twilight hack was found through the lastest Zelda game Twilight Princess, the game needs to be loaded every time before you can run any "homebrew" software.

Asphalt5 is a racing game for the WebOS phone operating system, originally developed by Palm. If you want to play it (and you should) on your Nokia N900 handset there are some complications you're going to have to get through, and this video will show you how step-by-step.

In order to build a trip wire, you will need the following: a knife, fishing line, a rope/string, sticks, and a large stone.

First of all you have to place your thumb or attach a pin on the ribbon such that there is a space of two to three inches left outside. Bend the ribbon back to the center to create your first loop. Now you have to pass the ribbon back underneath the bow. Then you have to again return to the center to create a complete second loop. Now continue passing the ribbon over and under the bow. Now return to the center and then repeat this step to create six loops in total. After this you have to turn...

For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Taking one-handed pictures with your phone can quickly devolve into a juggling act. You have to secure the phone in landscape mode (if you're doing it right), tap to focus, and then somehow hit the shutter button without shaking the device too much. Fortunately, Samsung has a nifty feature that'll help you keep a more secure grip on your Galaxy S9 or S9+ as you take photos with one hand.

One of the best-received features of the OnePlus 5T was the relatively secure face unlock, which made it quick and easy to get into the phone. Unfortunately, this feature wasn't included with the slightly older OnePlus 5 at first, but now, face unlocking is finally out of beta and available to everyone with a 2017 OnePlus.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

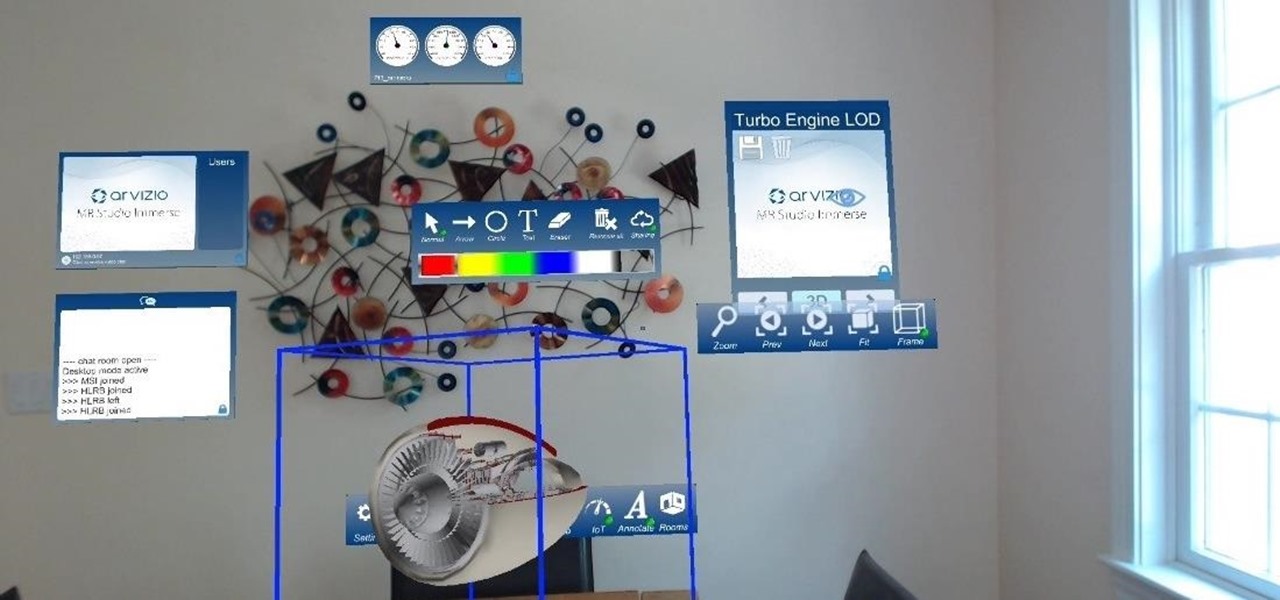
HoloLens developer Arvizio has expanded its collaboration suite of tools for enterprises with a device that can stream and record mixed reality experiences in high-definition for local and remote audiences.

Nauto, which develops driver-monitor cameras and algorithms for autonomous vehicles, is among a growing list of driverless startups able to attract tens of millions of dollars in funding after raising $159 million in its latest round of financing.

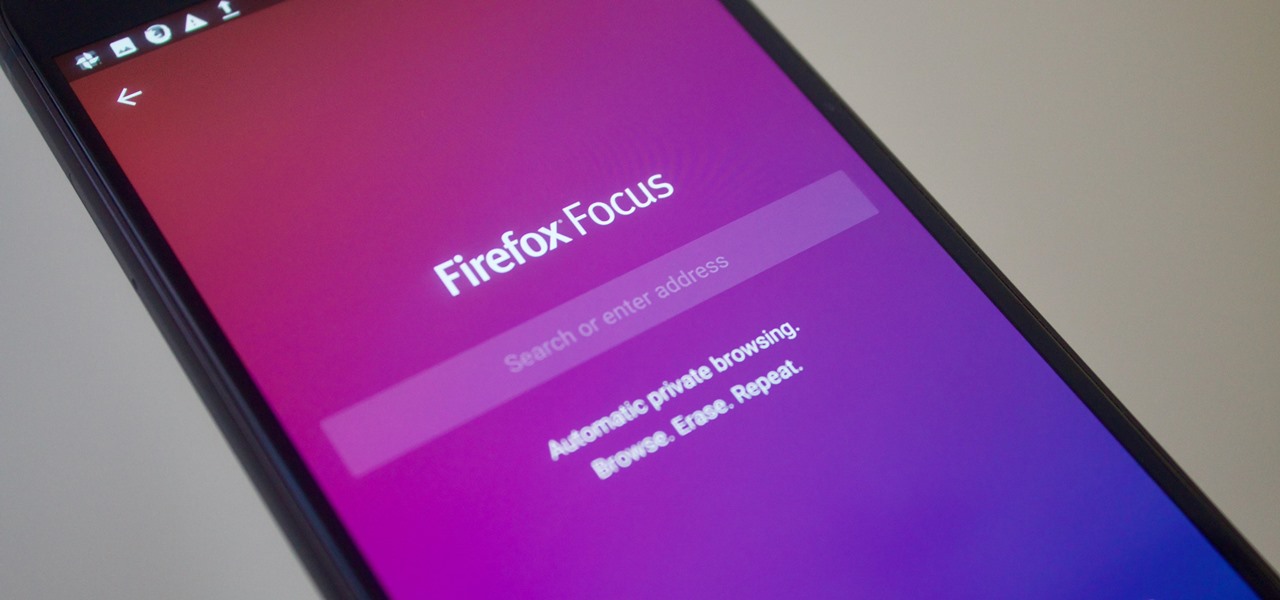
Firefox Focus is Mozilla's effort to make your internet experience a little more secure. Originally released in November 2016 for iOS, Focus blocks internet trackers, search history, anything that gets in the way of a clean, private browsing experience.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

Independent game developer PlayFusion announced today a partnership with NEXON Korea Corporation, resulting in a Series A preferred share round to fund development of their entertainment platform. PlayFusion's platform applies augmented reality, Internet of Things (IoT), and audio recognition to Lightseekers, an original property that combines mobile gaming with smart action figures, trading card games, and other media.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

bObsweep Standard and Pethair both come with their lithium-ion battery installed for you. But if you ever need to remove and replace the battery on either model, follow the walk through below.

The original implementation of Android's face unlock feature was a mess. It took too long to unlock (when it worked), brought up a huge interface that overpowered the lock screen, and maybe most egregiously, was able to be "hacked" by someone holding up a picture of your mug.

Android 5.0 has a killer new feature that should make securing your device easier than ever. It's called Smart Lock, and it essentially lets you bypass your secure lock screen when you're in a "trusted environment." This means that if you're connected to a known Bluetooth device or near a pre-programmed NFC card, you don't have to bother entering your pattern, PIN, or password.

Buns make the look of a woman highly fashionable and cool. Transform your appearance into highly swanky and dashing by following this simple tutorial to make an awesome Long Hair Messy Bun and instantly transform your simple look into a fashionable one. Step 1: Comb Your Hair and Make a High Pony. Now Take Small Section of Hair from the Pony and Start Backcombing the Surface Side. Step 2: Now with Your Fingers

Gmail is a free, advertising-supported email service provided by Google. Users may access Gmail as secure webmail, as well as via POP3 or IMAP4 protocols. Gmail initially started as an invitation-only beta release on April 1, 2004 and it became available to the general public on February 7, 2007, though still in beta status at that time. The service was upgraded from beta status on July 7, 2009, along with the rest of the Google Apps suite.

When you're on the go, it's important to keep your belongings organized and at an arm's distance so you're not fumbling in public for your keys, cards, or phone.

Are you thinking of a ponytail or a simple bun? If you can make a ponytail, you can make a bun, and in this guide, we'll show you how to make a bow bun—for beginners. It's a very easy, but very cute and chic, way of tying up that short hair.

UPS offers a four-step guide to prepare packages for shipping. These instructions include shipping advice on packaging materials and proper labeling that can help items arrive safely and on time. And when you are ready to ship, UPS Internet Shipping guides you through the required address fields. Packaging solutions made easy. That’s logistics.

Want to secure your home? There are plenty of ways to go about it. You can make your doorbell send you a text if someone rings it while you're not home, or build a motion-triggered security camera. Even better, you can beat potential crooks at their own game by installing a door they can't even find.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

In this how to video, you will learn how to build a patio enclosure with seating walls. You will need measuring tape, a level, a dead blow hammer, a square, masking tape, safety glasses, and work gloves. You will need the courtyard collection as well. First, draw out a plan for the enclosure. Mark the locations of the posts and panels with tape. Openings should be three to four feet wide. Start building walls at posts. Adjustments must be made at corners. Start by placing four corner blocks. ...

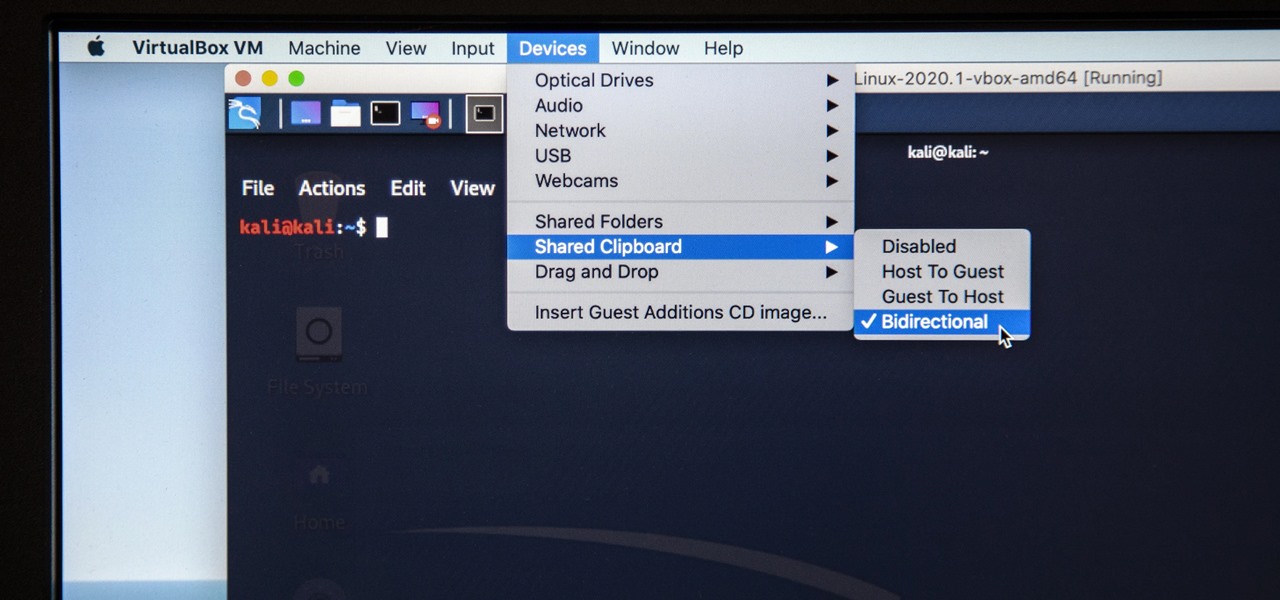
Last week, I updated VirtualBox on my computer since I had skipped a few versions, then I could no longer copy text or paste text from my Kali virtual machine to my host OS and vice versa. Installing the Guest Additions didn't seem to do anything, and the bidirectional shared clipboard was enabled, but there was one thing that did work for me that may help you out too if you experience the issue.

With the upcoming Memorial Day weekend serving as the unofficial start of summer, Pepsi is turning to Instagram to help sell its soft drinks to quench the thirst of beachgoers and BBQers.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Messaging apps can be a double-edged sword. Not only do they let you interact with other people, but they also let you go back and reminisce on past exchanges. However, that same archive can be used against you in certain situations. Luckily, Signal can be manipulated to remove any record of past messages.

It has not been a good year for Apple, as far as software scandals are concerned. From autocorrect nuisances to secret slowdowns of aging iPhones, Apple has had a lot to answer for. iOS users now have another issue to worry about — it's being called "chaiOS," and it's wrecking havoc on iPhones with just a simple URL.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

Google caught a lot of flak for the Pixel 2 XL's POLED display issues, regardless of whether the problems were real or perceived. It's too late to contract another screen manufacturer at this point, but Google is doing the next-best thing: Fixing as many user complaints as possible with software updates.