When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

Now that its first developer conference is in the rearview mirror, Magic Leap continues to nurture its content development community, this time with an assist from strategic investor and retail partner AT&T.

After about 40 days of beta testing, Apple pushed out iOS 11.4.1 to everyone as a stable build on Monday, July 9, exactly one week after the final beta appeared.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.
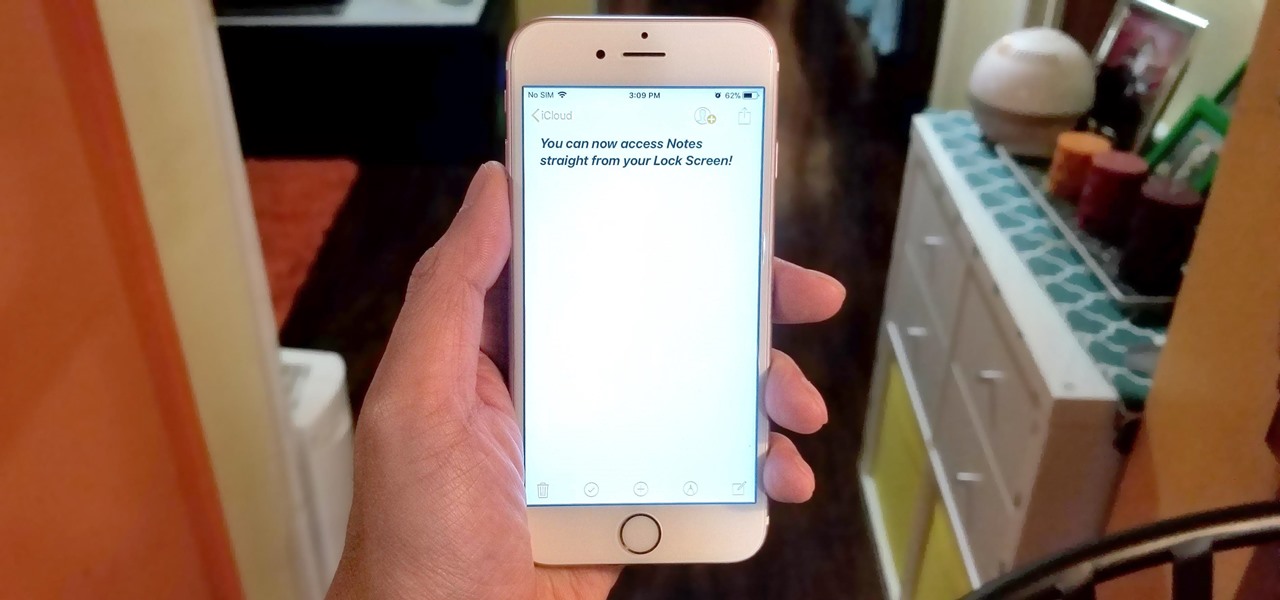
All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

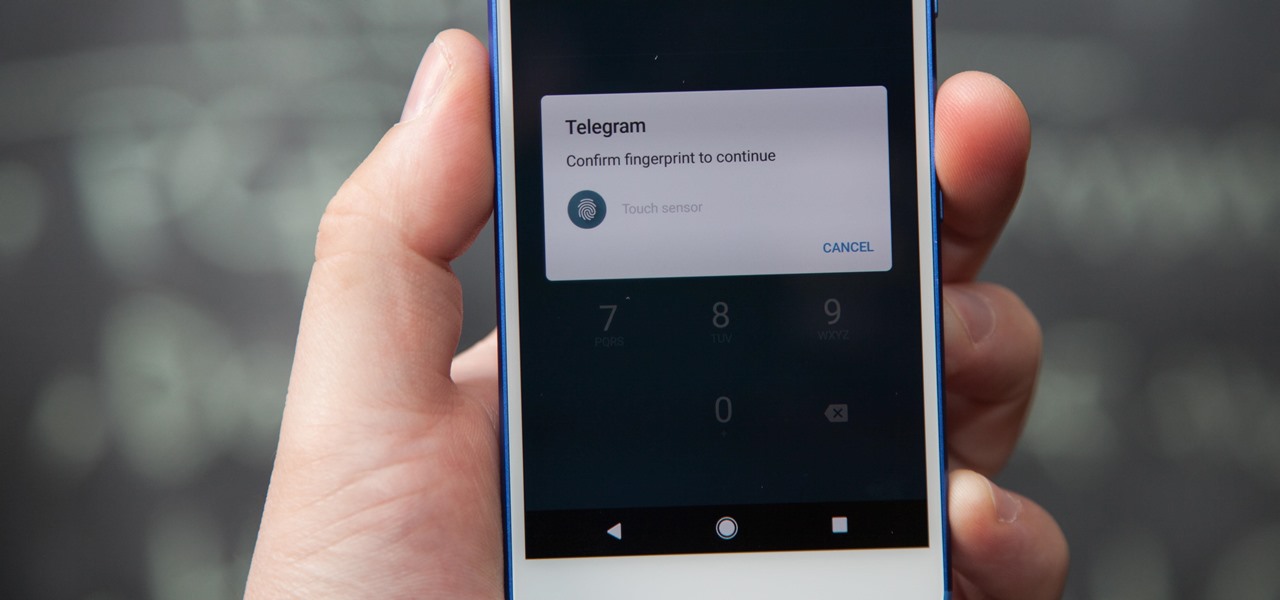
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

When you first receive bObi, the battery is not plugged in. Luckily all you need is a Phillips head screwdriver to install it before bObi starts working for you.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.

Fashionably cool and awesome, this marvelous French Twist hair Style is as simple to make as it is elegant and stylish to flaunt. Just in few easy and accessible steps, this urbane style makes your appearance special and any outing memorable. Step 1: Comb Your Hair Neatly to Remove Any Tangles and Make Them Smooth. Step 2: Hold the Hair Together Like a Pony and Twist Them Till the Middle of the Pony and Make a Roll as Shown. Step 3: Once You Have Secured the Roll, Cover It with Surrounding Ha...

Being in your twenties is tough. You're not a child anymore, but also not quite a full-fledged "adult" yet. Sure, you do adult things like cook asparagus sometimes, but you're also sweating about securing enough likes on your social media posts.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Mac OS X has convinced many traditional PC users to switch platforms. While Windows 7 may do something to stem that tide, a lot of you PC users reading this have probably thought about switching right? If you have, watch this video. It will give you a PC-user centric rundown of OS X and allow you to make a more informed decision about what operating system is best for you.

In this Flash and ActionScript video we will learn how to change the user's mouse cursor to a piece of artwork we made and then make it explode when a users clicks on a certain area of the stage. Also, see some helpful tips on basic Dynamic text. The exploding cursor is a great way to start learning ActionScript and Flash 8.

Microsoft recommends a unique user ID and password for every user. In order to switch user ID or log off one need to click to the 'Start' menu as shown in the video. Press the move button at the shut down menu as shown. In the sub menu you can see the Change user and Log off. The window will typically shut down and restart on change of user ID or Log Off. In case you need to leave your PC unattended you can press 'Lock' from the same menu which will refrain anyone from changing your desktop s...

It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

In last week's guide, we covered the best places to purchase digital copies of computer games online. This week we'll cover another type of downloadable content: those available for video game consoles. Every major console out today either has or plans to have a DLC platform, but which one is the best? If you don't like leaving your house and want to play console video games, which console should you get? Below I will break down what the online marketplace offers so you can decide which conso...

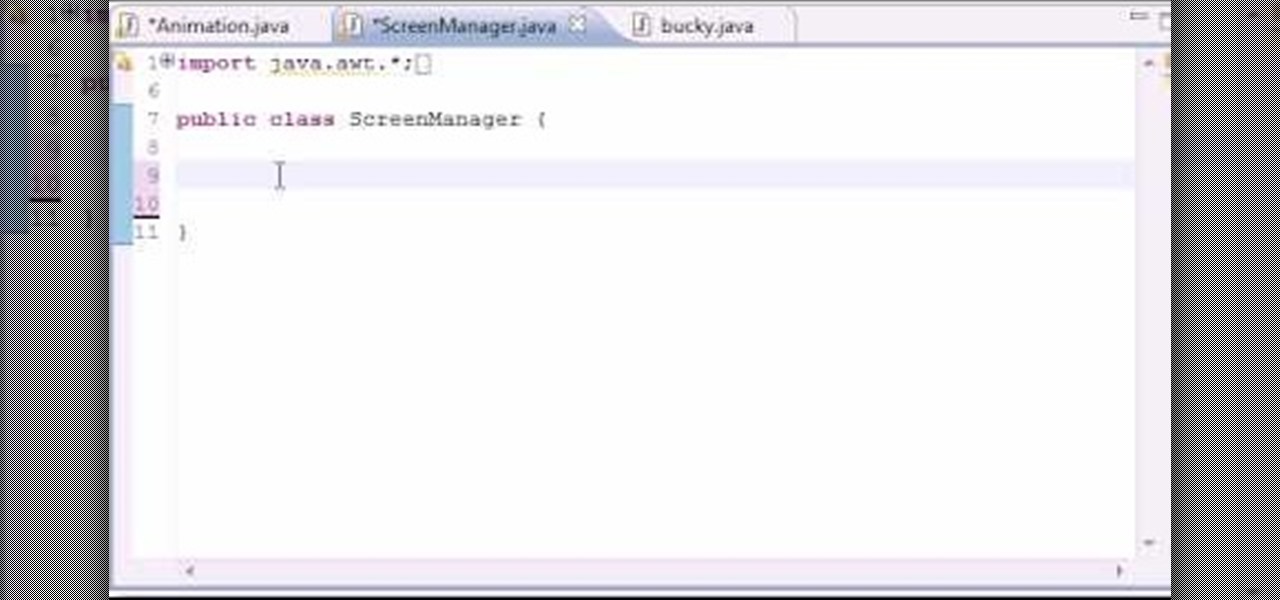
In this 14th video in a series about JAVA game development, "thenewboston" (Bucky Roberts) explains how to redefine your screen to avoid annoying flickering. Flickering in JAVA games often occurs because of time lags as the viewer watches the computer draw a new screen, pixel by pixel. Pre-installed code in JAVA can be used to eliminate this problem by taking advantage of "Buffering" and "Page Flipping". These functions permit you to delay the composition of a new screen until it is finished,...

Users will need an exercise ball to perform this exercise. Begin by going on your knees and elbows on the ball. Users basically go into a plank position in the ball. Now users will need to go into a straight position from the shoulders to the knees. Now users will draw the alphabet using their elbows, while rolling the ball. To make the exercise more challenging, users may choose to lift one or both knees off the ground while doing the exercise. This video will benefit those viewers who want ...

The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.

Need to know how to run an application as another user? This Windows 7 tutorial will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in just under a minute's time. For more information, including detailed, step-by-step instructions, watch this Win 7 user's guide.

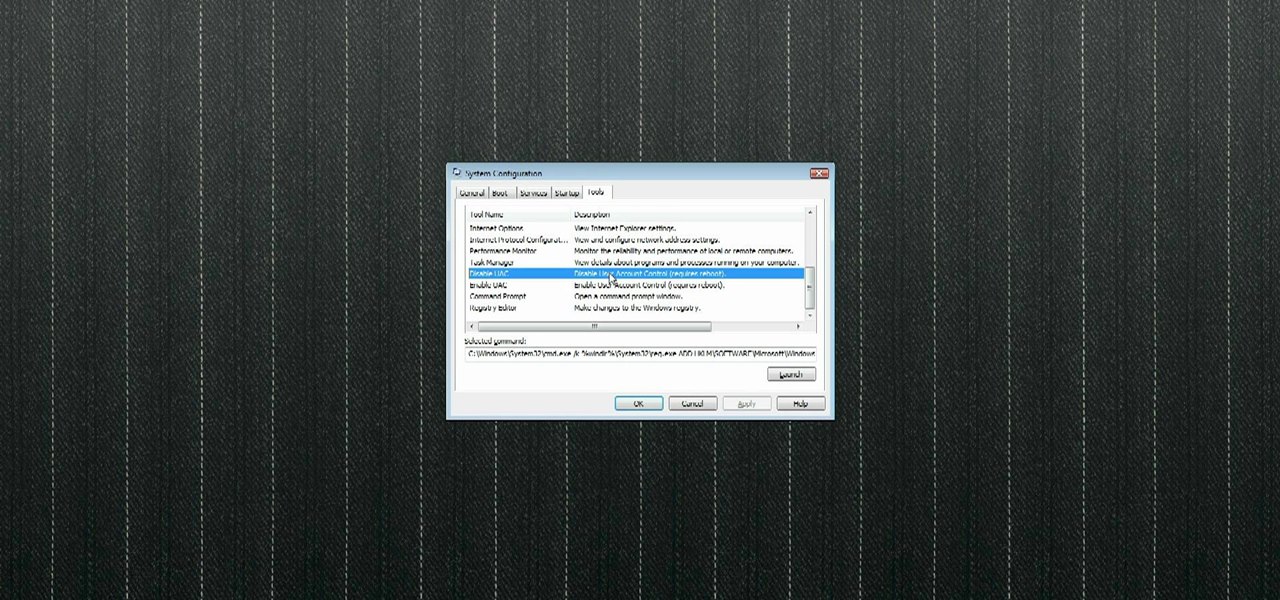
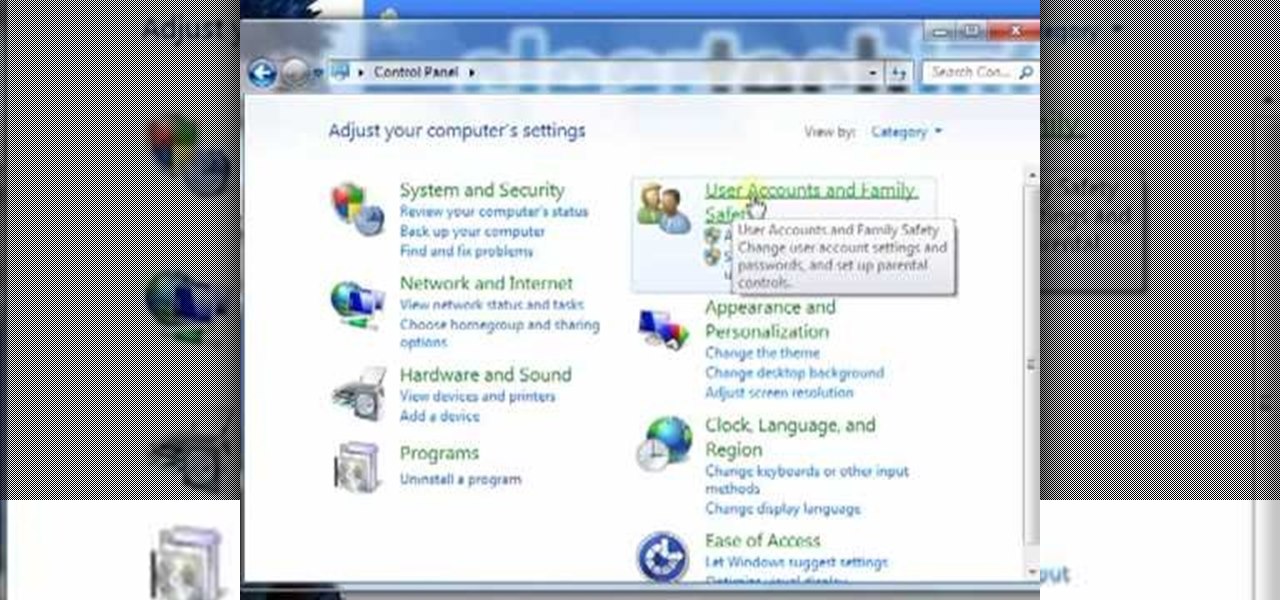
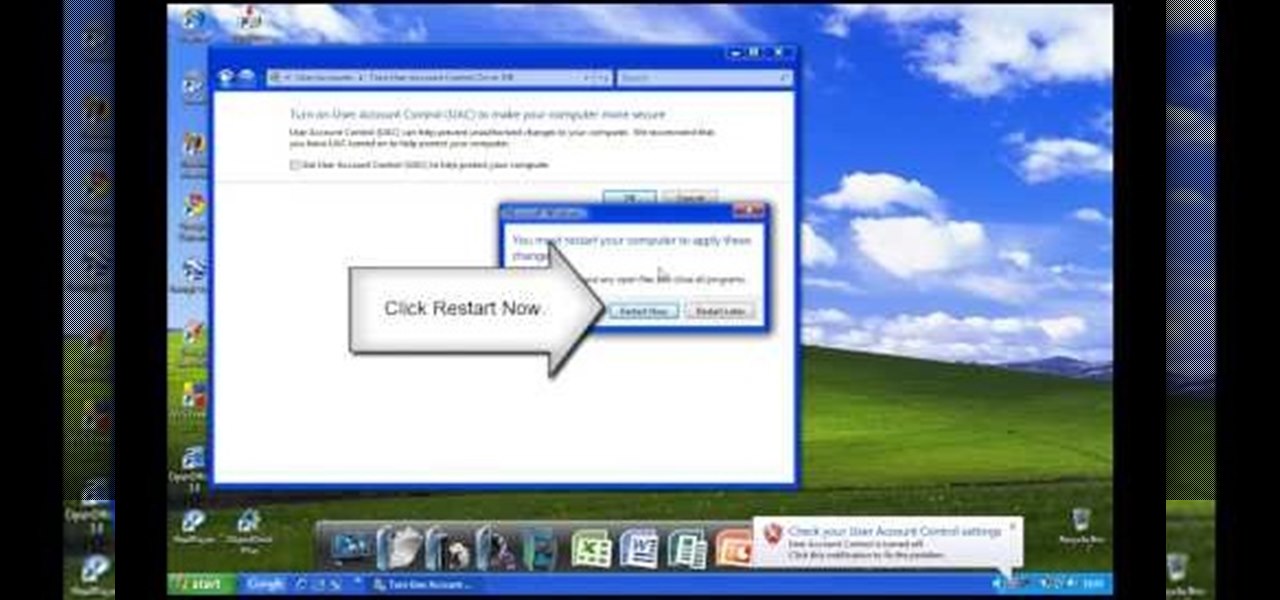
In this video tutorial, viewers learn how to disable the User Account Control in Windows Vista. Begin by clicking on the Start menu and select Control Panel. Then click on User Accounts and Family Safety. Now select "Add or remove user accounts". Then click on "Go to the main User Accounts page" under Additional things you can do. Now click on "Change User Account Control settings" and deselect the box. Finish by clicking OK and restart your computer. This video will benefit those viewers who...

Whether you're the proud owner of a brand new Apple iPad or are merely considering picking one up, you're sure to appreciate this video tutorial, which presents a complete overview of how to use the mobile device's user interface. For more information, including detailed, step-by-step instructions, watch this iPad user's guide.

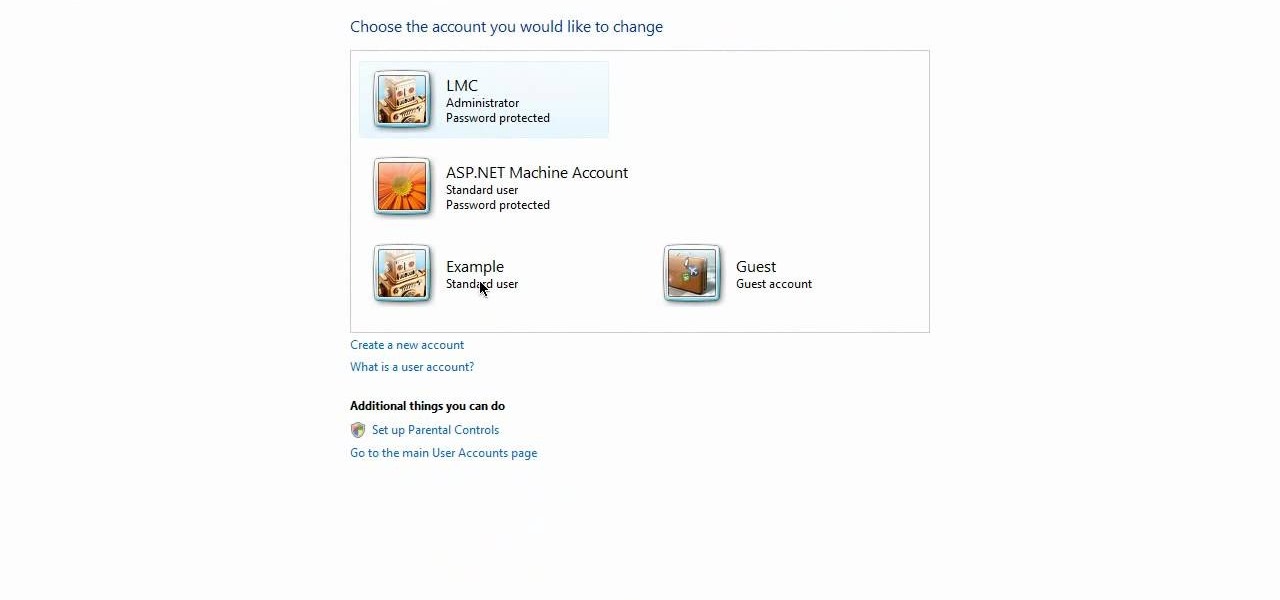
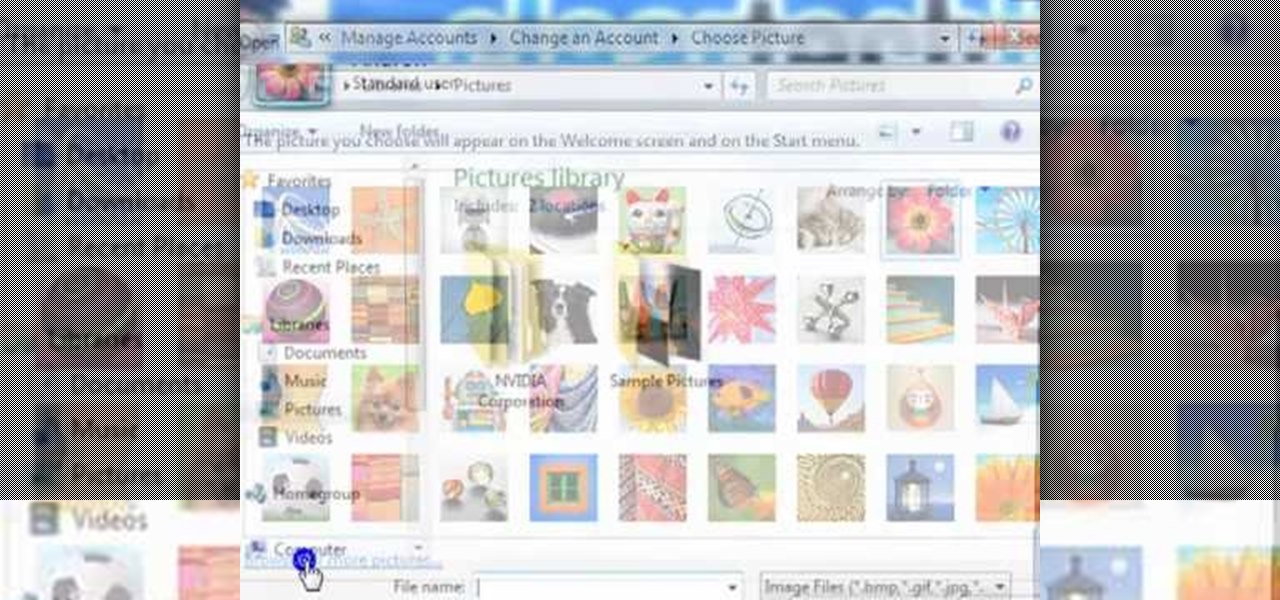
In this video tutorial, viewers learn how to create a new standard user and administrator account. Begin by clicking on the Start menu and select Control Panel. Then click on User Accounts and Family Safety and click on User Accounts. Now select the "Manage another account" option and click on "Create a new account". Users are able to name the account and select the account type (Standard or Administrator). Finish by clicking on Create Account. Users are then able to make changes to the accou...

In this video, Nub shows us how to delete a user account. First, you will click "start" then "control panel". Then click on "user accounts" and then "manage another account". You must be logged in as the administrator to do this. A new window will pop up once you click on this and you will see all the user accounts on your computer. Click on the user you want to delete and a menu will show up. Click the button that says "delete this account". A message will appear asking if you want to save t...

In Windows Vista start off by going into the control panel in the start menu. In here go into "user accounts and family safety". Inside go into "user accounts". A screen will appear where you can make changes to your user account. Here there should be an option to turn user account control on or off. Click on this will bring up another window where if you uncheck the solitary checkbox you will have succeeded in turning User Account Control off. After doing so click ok and then press restart n...

This video contains instructions about how to disable or enable the user accounts on Windows Vista. It is very simple; just go to control panel -> user accounts and safety -> user accounts. You can click the check box on or off to disable or enable the user accounts. This can also be done by using command line. Open run and type the following command:

ClearTechInfo live up to their by offering clear and concise information on how to manage user account settings in the new OS from Microsoft, Windows 7. Begin by pressing the start button and going into the control panel. In here look for 'user accounts and family safety', open it. Now go into user accounts and then manage another account. If you are the administrator then you can change whichever setting you want for whichever account but if you're just a standard user you can only alter you...

In this video tutorial, Chris Pels will demonstrate how to create a custom user control in ASP.NET that can be used throughout a web site or across many web sites. Start out by learning the basics of creating a user control that will be used in multiple pages including validation, controlling formatting using style elements, and loading/saving data for the user interface elements. Throughout the video considerations for building user controls that can be easily maintained and used across mult...

In this video tutorial, Chris Pels will show how to determine what capabilities a user’s browser has when viewing pages in an ASP.NET web site. First, learn how to access an instance of the HttpBrowserCapabilities object from the ASP.NET Request object associated with the web page request. Next, see the different information available in the HttpBrowserCapabilities object such as the type of browser and whether the user’s browser supports JavaScript and Cookies. Then see an example of how to ...

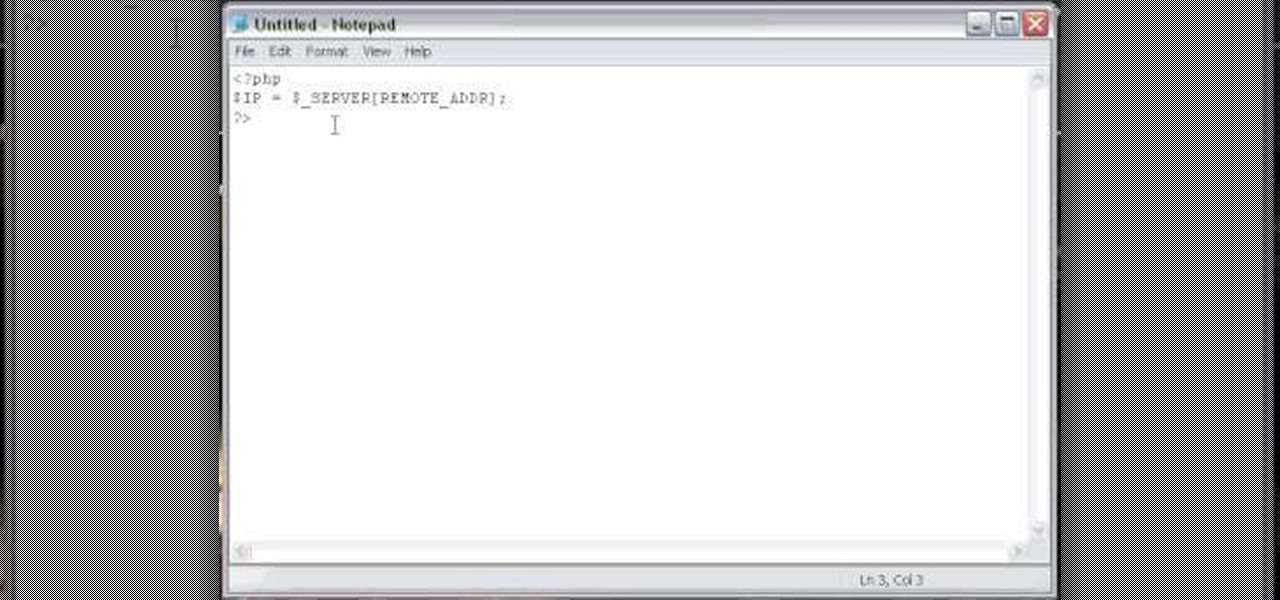
How to program a user registration using php, sql and phpmyadmin. Part 1 of 3 - How to Program a user registration with PHP.

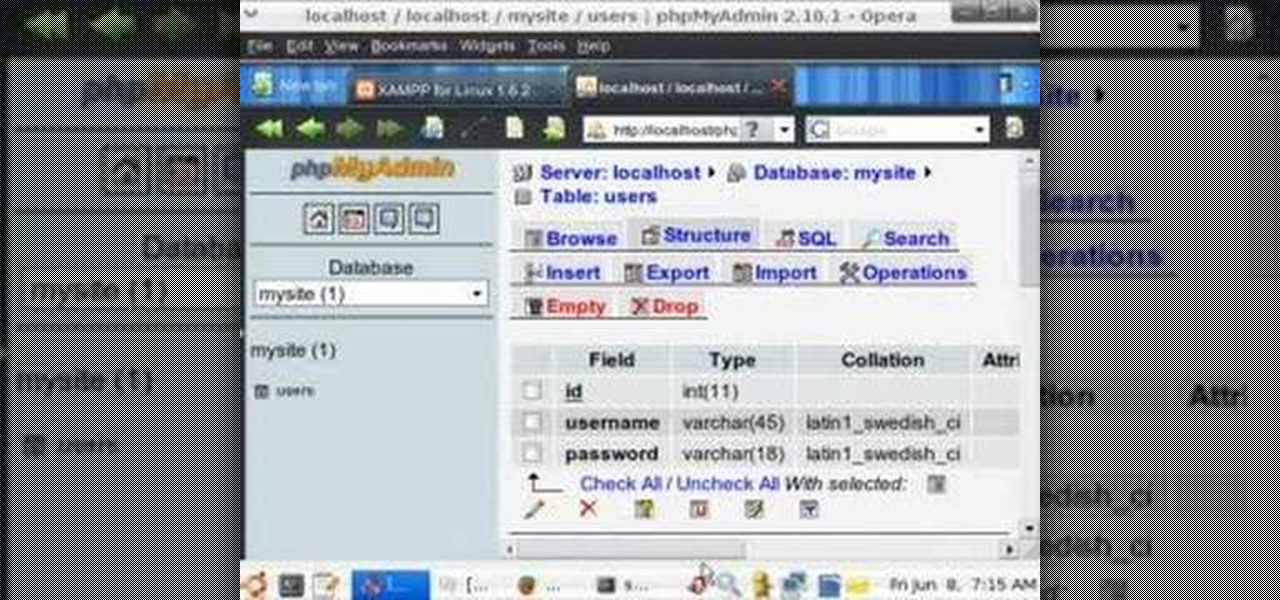
A PHP programming tutorial on how to set up a user database. Part 1 of 2 - How to Create a phpMyAdmin user database.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

As a root user, you have a lot of responsibilities to make sure your phone stays secure. Expectedly, some things may slip through the cracks. Remembering to check which apps have been granted root access is extremely important. All it takes is one bad app, so it's good to learn how to avoid that at all cost.

On Sunday, Microsoft did what everyone expected the company to do by unveiling the long awaited HoloLens 2.

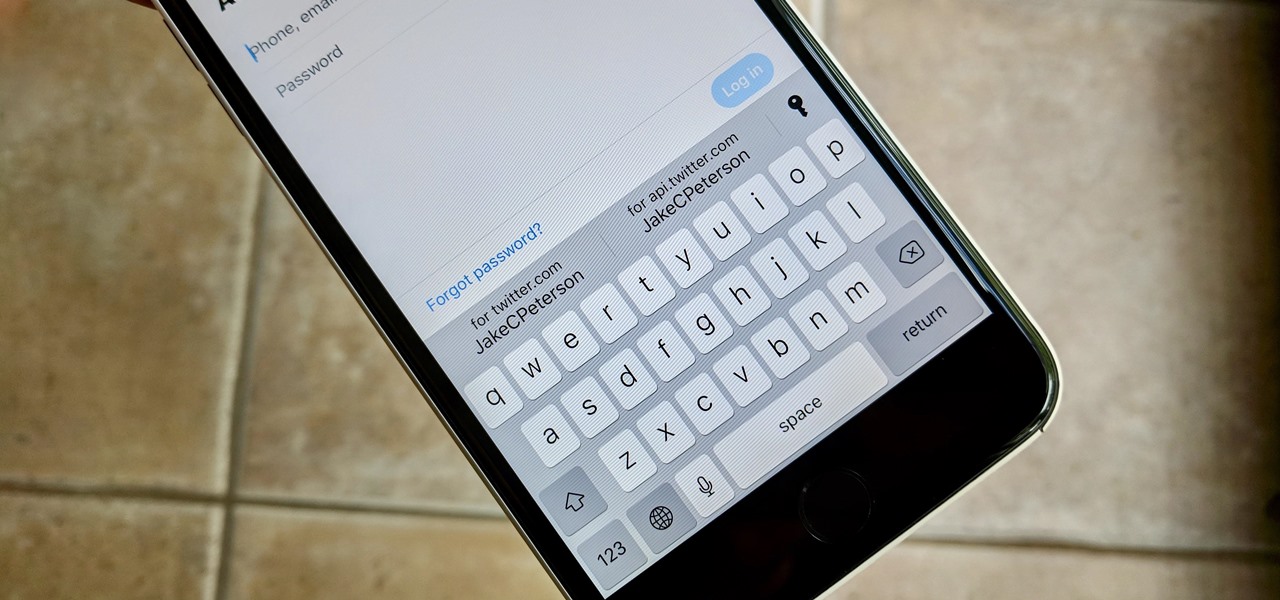
Apple's dedication to iPhone security is one of the company's biggest selling points. It's no surprise then that iOS 12 offers users a simple yet powerful way to make, save, and auto-fill strong passwords to your iCloud Keychain when creating accounts in both Safari and in apps. The best part? You hardly need to do a thing.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.