
Market Reality: Disney, Universal, & FIFA World Cup Turn to Augmented Reality for Marketing Muscle
Augmented reality is really picking up steam as a tool for marketing departments to pitch their products.


Augmented reality is really picking up steam as a tool for marketing departments to pitch their products.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

When it comes to differentiating from the competition, brands are continuing to leverage augmented reality to give consumers to the point that there are few "firsts" left to achieve in the marketplace. While L'Oreal jumps on the augmented reality bandwagon for cosmetics, Acura finds a new way to make augmented reality a spectacle in the automotive industry.

If you're a developer in the augmented and mixed reality space, there's a high probability that you're intimately familiar with the 3D application and game engine Unity. In May, at VisionSummit 2017, Microsoft announced that 91% of all HoloLens applications have been made with the software. But there's a section of Unity that you may not be familiar with, which has become very important to augmented, mixed, and virtual reality (known collectively as XR, for "extended reality") — Unity Labs.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.
Google's monthly Android security updates are generally welcome—at the very least, they provide a feeling of security that our device is now somewhat safer than it was 30 days ago. Vulnerability patches, slight enhancements to performance, and overall bug fixes are generally included in the monthly OTAs, but as it turns out, they're not always for the better.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.
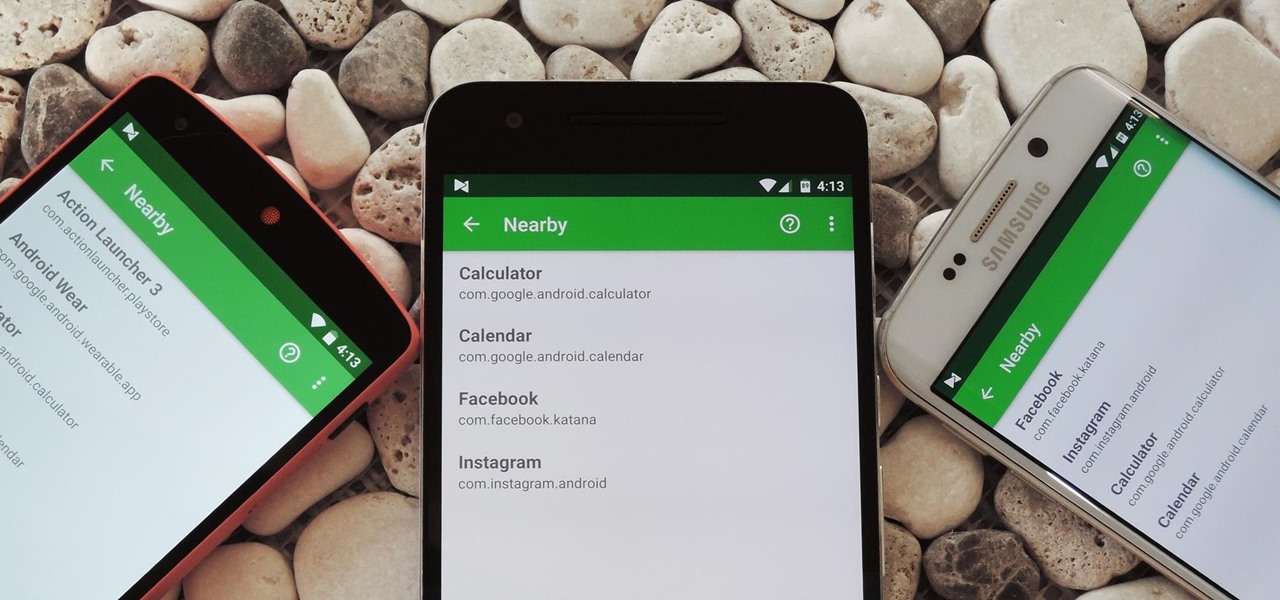
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.
The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.
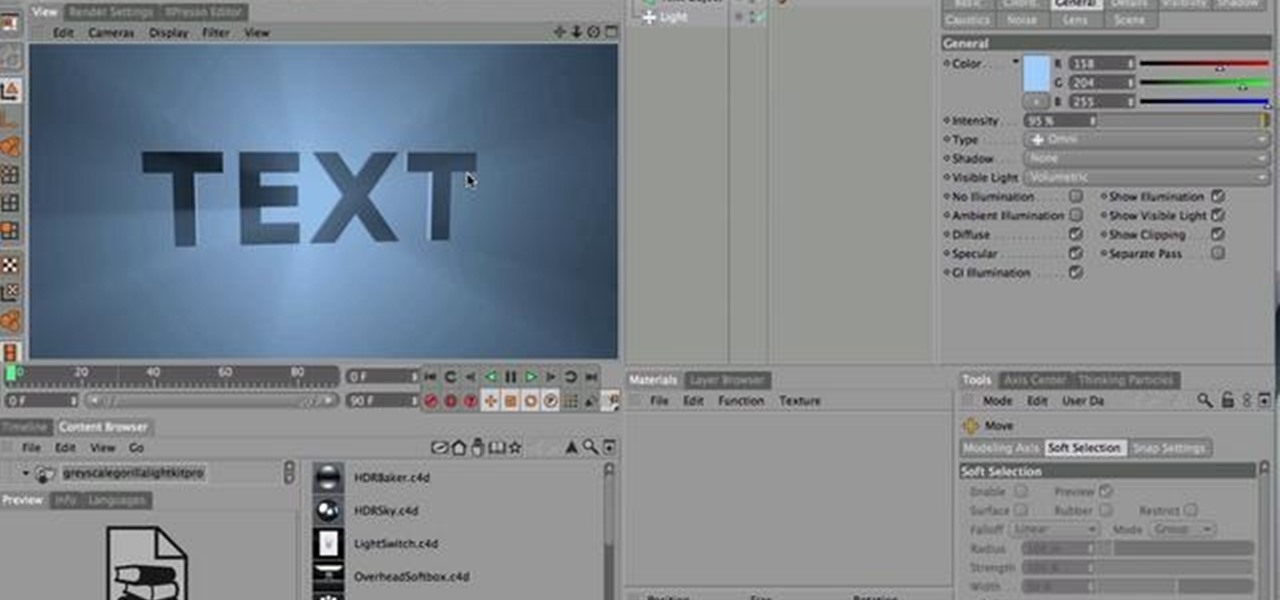
In this C4D user's guide, see how to create and employ volumetric lighting. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get started using this trick in your own Cinema 4D projects, watch this 3D modeler's guide.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:
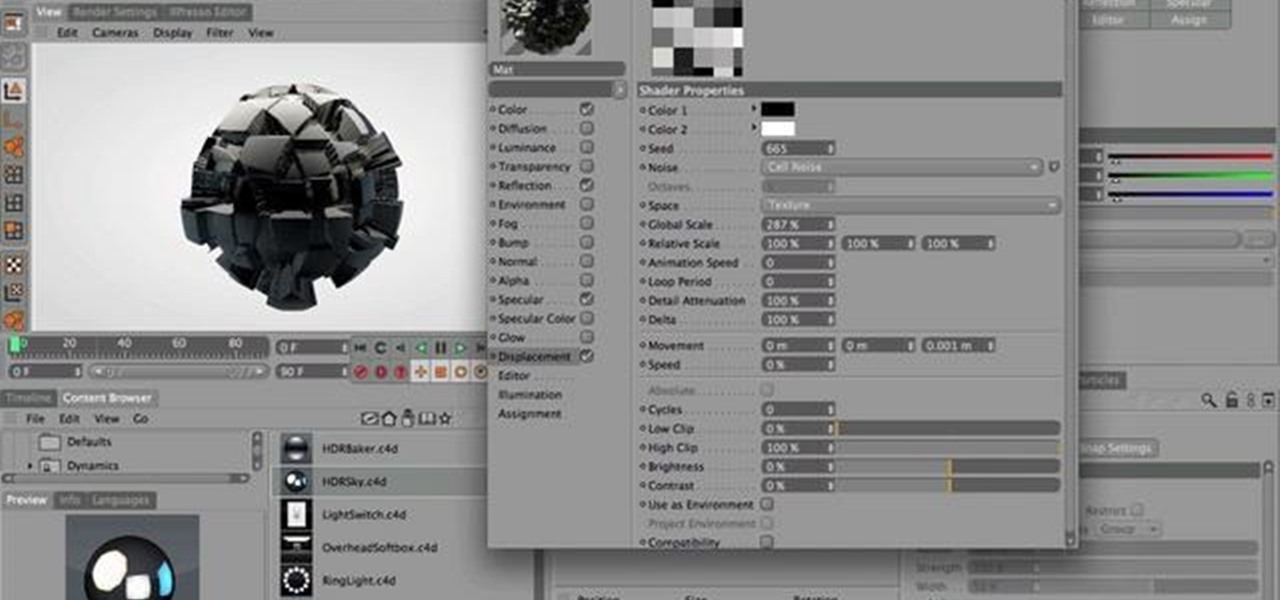
In this C4D user's guide, you'll learn how to use sub polygon displacement in your projects. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, including complete instructions, watch this 3D modeler's guide.
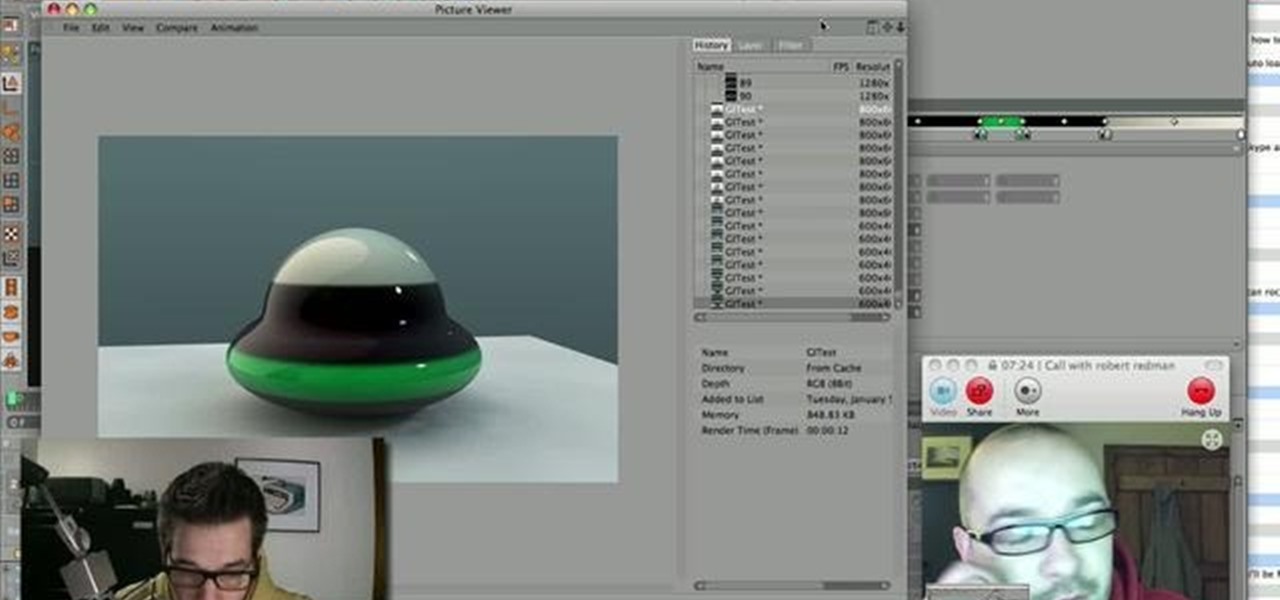
Learn how saving an irradiance cache can save time on rendering in this C4D-user's guide. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, including complete instructions, watch this 3D modeler's guide.
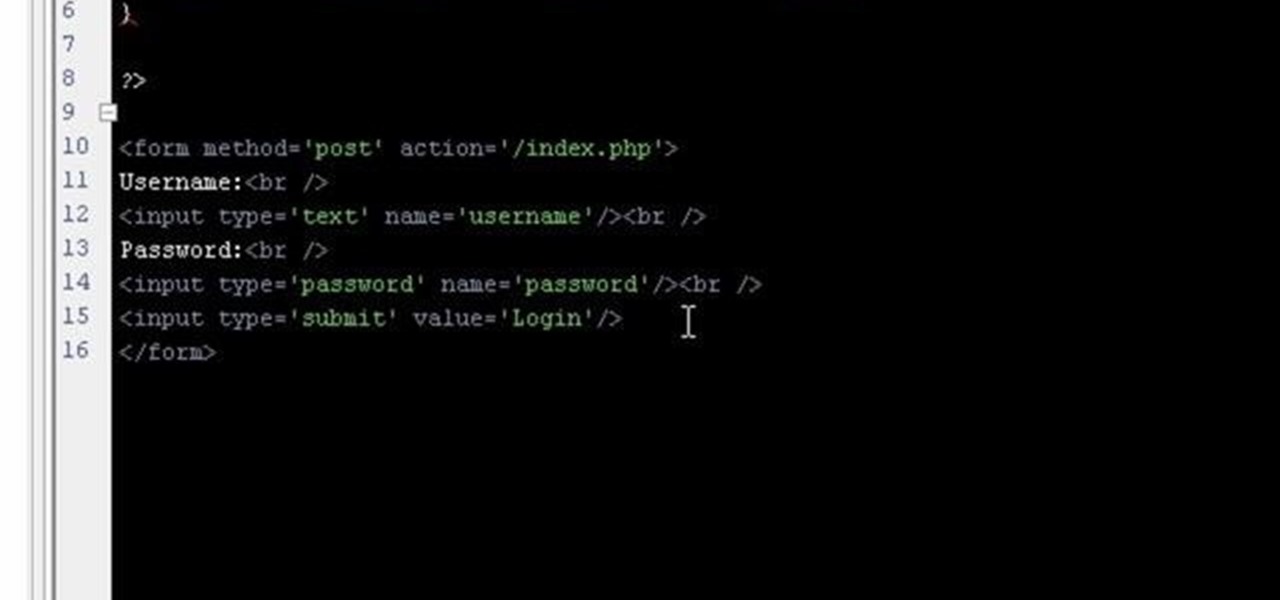
If you're working on a website and want users to use it repeatedly and form a community on it, you should probably give them a way to create an account and log in to your site. This video will show you how to create an AJAX login script using AJAX with jQuery, which will allow your users to do exactly what I described above, making your website much more professional and a much better place for people to stay and click on ads or whatever else you want them to do.

In this video tutorial, viewers learn 4 different hacks that will make typing easier in Windows. Begin by clicking on the Start button and select Control Panel. Then click on Ease of Access Center and select "Make keyboard easier to use". Now users are able to configure the keyboard options for easier use such as: turning on/off the mouse keys, sticky keys, toggle keys and filter keys. All the features have more specific settings for self-adjusting to the user's liking. This video will benefi...

Flash and Actionscript can be used together to create damn near any sort of animation or website feature that you could want. This video will teach you how to do just one thing: generate a random frame using Flash CS4 and Actionscript 3. This is handy if you want to create a button that will link to several different objects randomly. Fun if you want to add the zest of unpredictability to your user's website experience.

In this video tutorial, viewers learn how to browse web pages without a mouse. Users will need to use the Mozilla Firefox browser. When you're in the Firefox browser, press F7 or click on Firefox, click on Preferences and select the Advanced tab (Mac OS X). Now check "Always use the cursor key to navigate within pages". This will activate character browsing, allowing the user to use the arrow keys to move up and down the page. Holding Shift will allow users to select a text. This video will b...
In this video tutorial, viewers learn how to make custom drawer icons for their stacks in Mac OS X. Users will need to go to the site provided in the video. There users will need to follow the instructions and download the icon sets. Once downloaded, place the icons into the appropriate folders. Users may need to restart the computer. Once restarted, the icons will be neatly overlapped in drawer icons. To add a folder to Stack, simply drag it to the dock. This video will benefit those viewers...
In this video tutorial, viewers learn how to remove/change the arrow on the shortcut icons in Windows. These arrows allows the user to know that the icon is only a shortcut. Users will need to download the program, Vista Shortcut Overlay Remover. The program allows users to display an arrow, light arrow, custom arrow or no arrow. This program also provides an option to disable the " - Shortcut" extension on any shortcut icon. This video will benefit those viewers who use a Windows Vista compu...
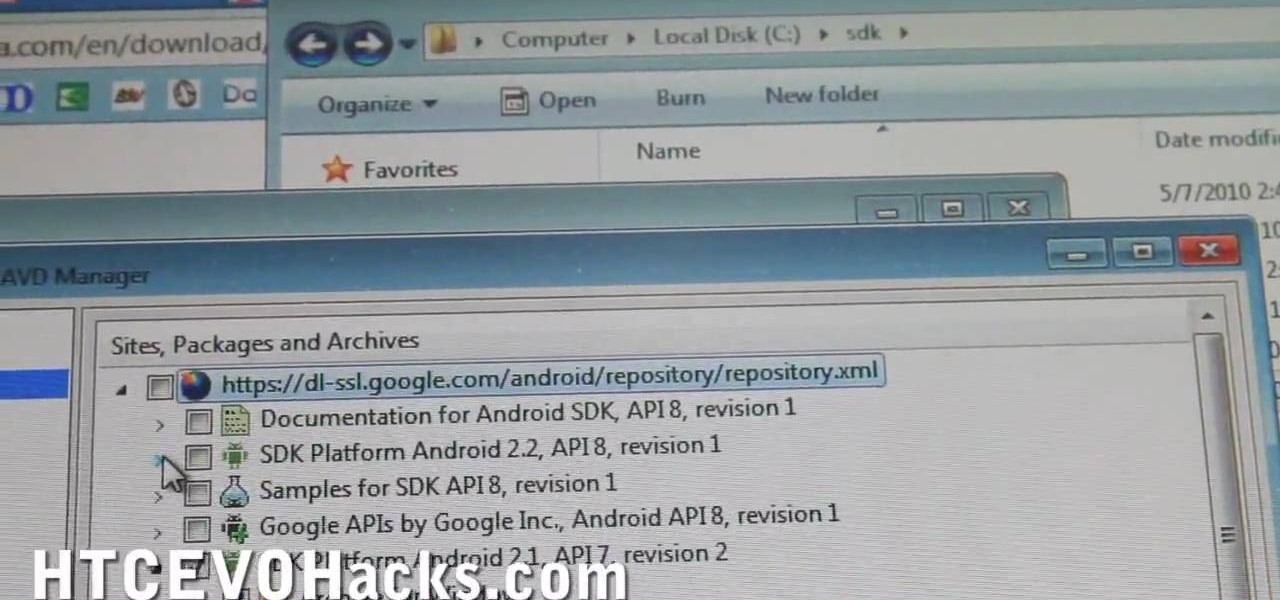
In this video, learn how to hack your HTC EVO 4G and root it for "Super user" access. Once you have rooted your device you can install custom ROMs, apps, overclock the CPU and a whole lot more. So, follow along with this step by step demo and root your phone to discover the possibilities!

Follow along as we are shown how to set a password for a new user in Windows 7. -First, go to the Start menu.

When you're a Windows OS user it's very easy to send out attachments on emails as .doc documents, made in Microsoft Office or Excel. But just because you're a Windows user doesn't mean your friend or coworker is. Or say that you're a MAC user and your friend keeps loading you with Microsoft Office documents. What do you do, other than telling him to stop already?

Check out this Do It Yourself (DIY) RV maintenance and repair video to learn how about RV battery maintenance. Know how to do it to keep your batteries running strong in your recreational vehicle with this RV tutorial video.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.
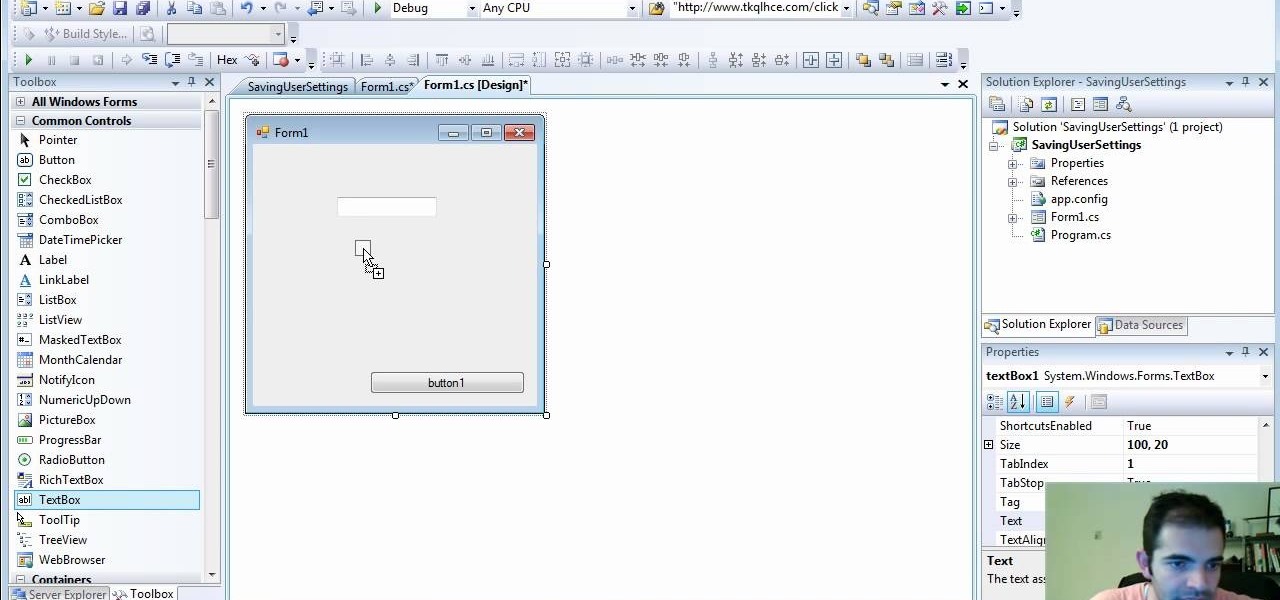
Check out how to save your user settings in Microsoft Visual Studio using C# programming, that way when you restart the program, it can remember some of your important information. This will specifically show you how to save your user settings using the .NET Framework instead of working with custom INI files.
Want to delete your Pro Tools user preferences in Mac OS X Snow Leopard (10.6)? Whether you're new to Digidesign's Pro Tools 8 or simply looking to pick up a few new tips and tricks, you are certain to benefit from this free software video tutorial, which presents a complete overview of how to trash your Pro Tools user preferences.

In this video tutorial, viewers learn how to use Flickr photos in their screen-saver. This task can only be done on the Windows computer. Users will need to download the program from the website provided in the video. Once downloaded and installed, there is an option in the Screen Saver Settings. Users are able to take photos from specific users or groups, or can search through tags and contacts. Further options include selecting the size of the photo and delay between switching the photos. U...

Depending on what your website is for, you may or may not care about allowing your users to download files from you. If hosting downloadable content sounds like something you want to do, watch this video! It will teach you how to allow your users to download files from your website using Dreamweaver. It's not very hard, and your users will probably be thankful that they don't have to go on the web every time they want to access your content.