In Obstetrics and Gynecology (OB/GYN), doctors deal specifically with the female reproductive organs, which means a lot of visual inspection of the vaginal area. Whether you're a doctor, surgeon, nurse, or nursing assistant, knowing how to properly drape a patient is detrimental to the patient feeling protected and secure with the hospital staff, along with having some privacy. This video will cover different types of draping techniques.

Almost every website on the web has buttons that enable users to interact with it. They are easy to make, but making them interesting and reactive to user's activities is more of a challenge. This video demonstrates how to create animated rollover buttons in Adobe Flash CS4 quickly and easily. Your website will be much more dynamic and enticing if you apply the skills taught in this video.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...
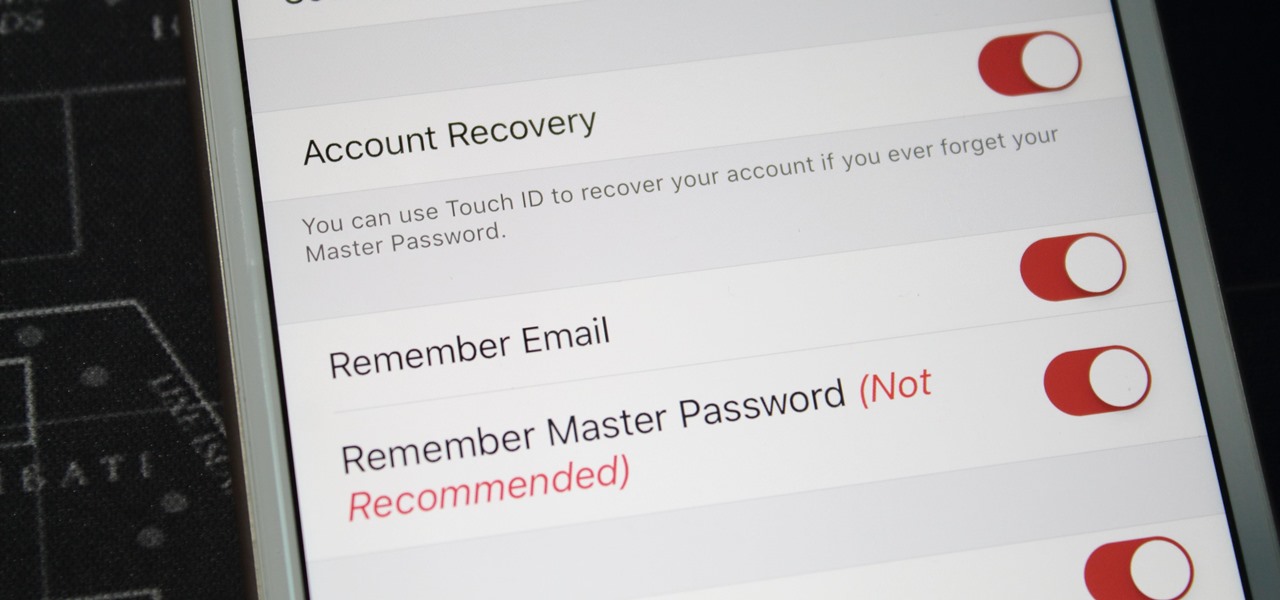
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

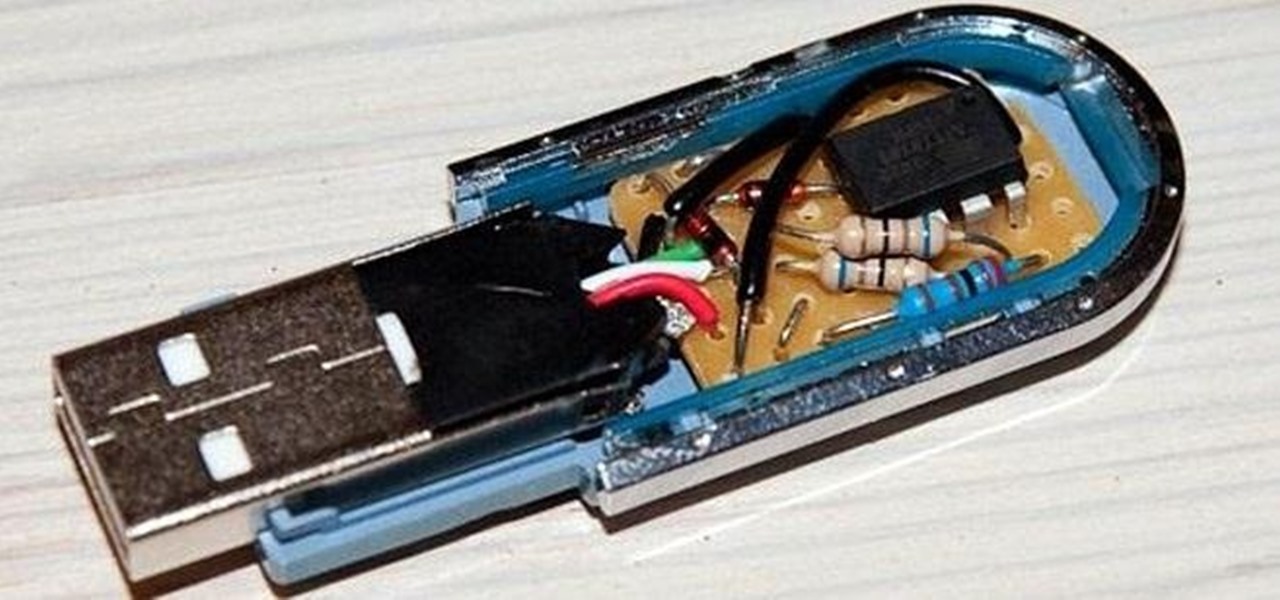
A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

Because of quirks with cell radios and how Android was previously set up, custom ROM support for Galaxy S phones has been sparse these past few years. It's been almost nonexistent for US customers, while international users would see some ROMs. Thanks to Android Oreo's Project Treble, this will all be changing soon.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

The new iPhone X will be released on Friday, Nov. 3, in Apple Stores located in over 55 countries and territories. For those of you who would rather skip the in-stores lines that will start building well before the 8 a.m. local time openings, you can preorder the iPhone X on Friday, Oct. 27, starting at 12:01 a.m. PDT.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

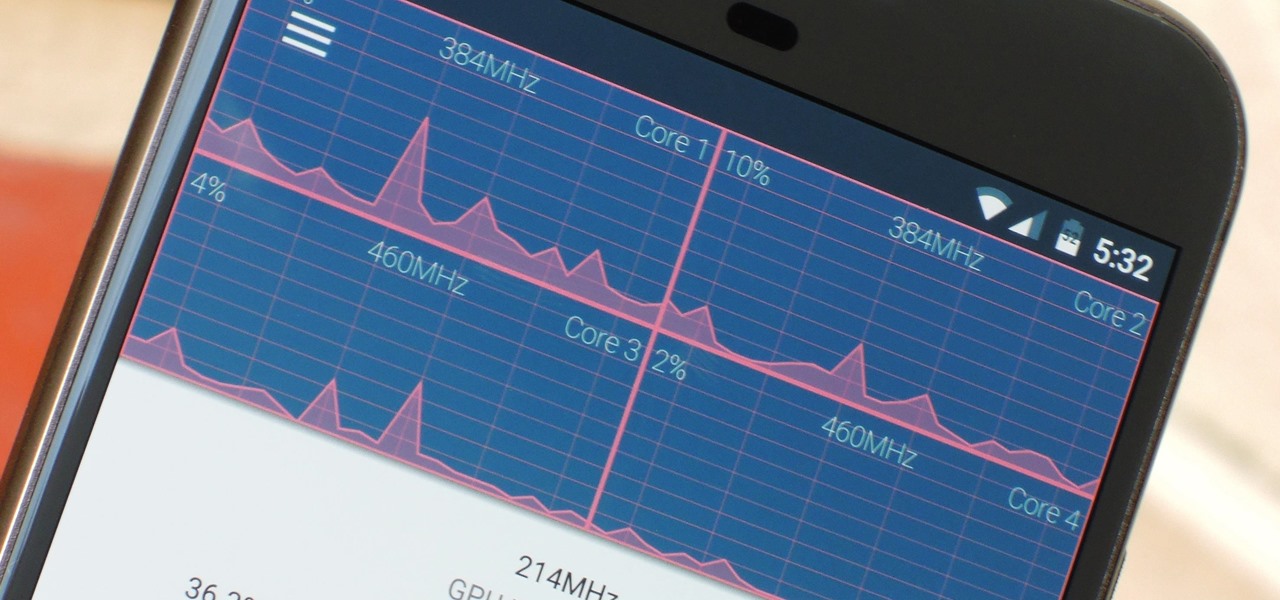
The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest browsers on the market.

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

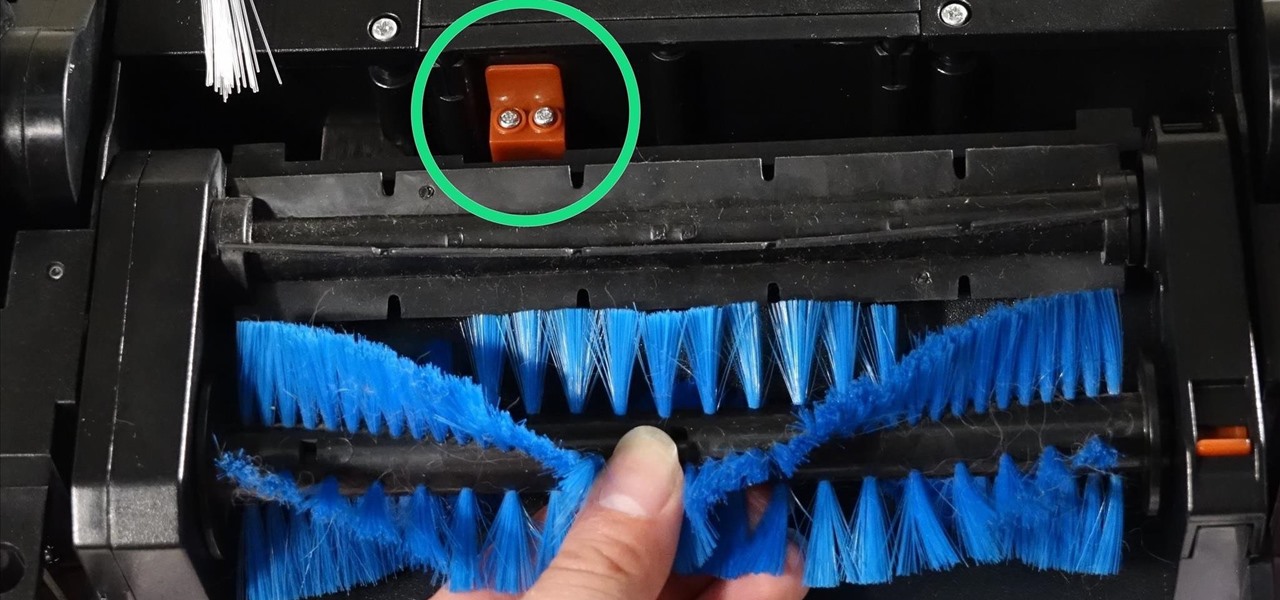
One of the quickest repairs for bObi is replacing the main brush motor. To do this, you'll need a Phillips head screwdriver and a replacement main brush motor.

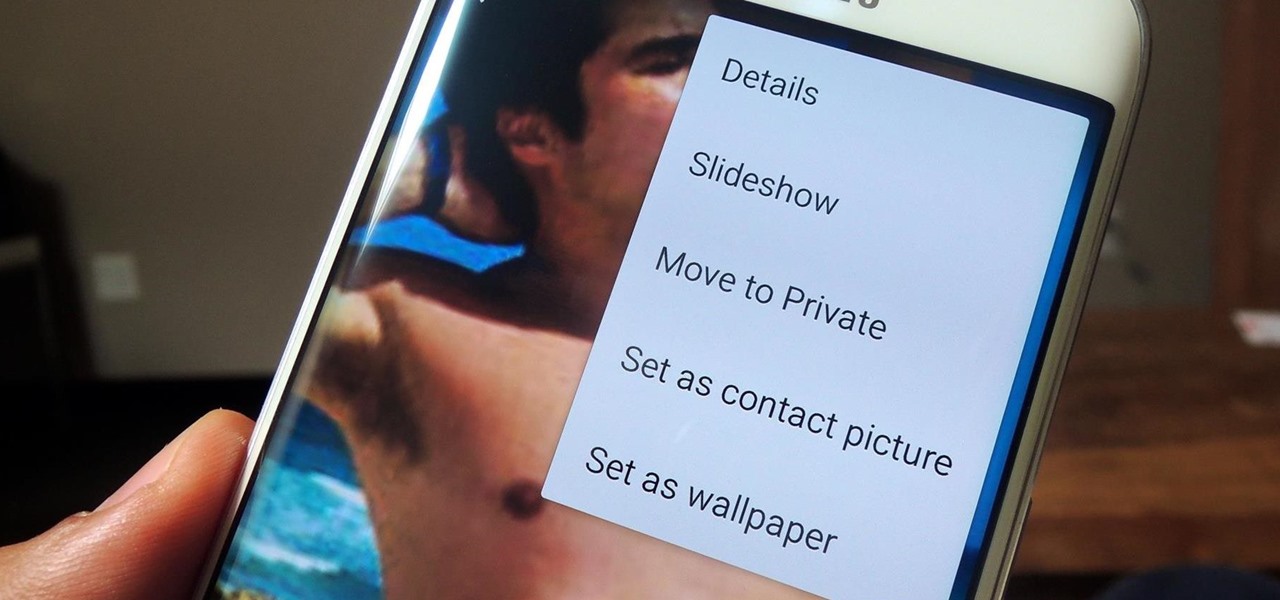
If you have a smartphone, chances are you have something on it you don't want others seeing. Whether it be photos, videos, or documents, some things are best left private. Not everyone is a saint, after all.

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

With the new year just around the corner, it's a time we all reminisce about the year that was. In the midst of families fighting over white elephant presents and the financial stress that comes with holiday gifting, you may also be dealing with the stress of hosting parties and get-togethers as well as the decorating that goes with it.

Probably SSH is not as clean and fast as other useful tools like netcat, but it has some features which are very useful, and when you'll need them, here's how to behave with that huge amount of computers all over your house.

No matter how many PSAs are published on the topic, studies continue to show that we are generally terrible at creating secure passwords and PINs. Using the same password (or variations of it) for multiple sites is another huge no-no that the majority of people ignore, and even though you should change your passwords frequently, most of us don't.

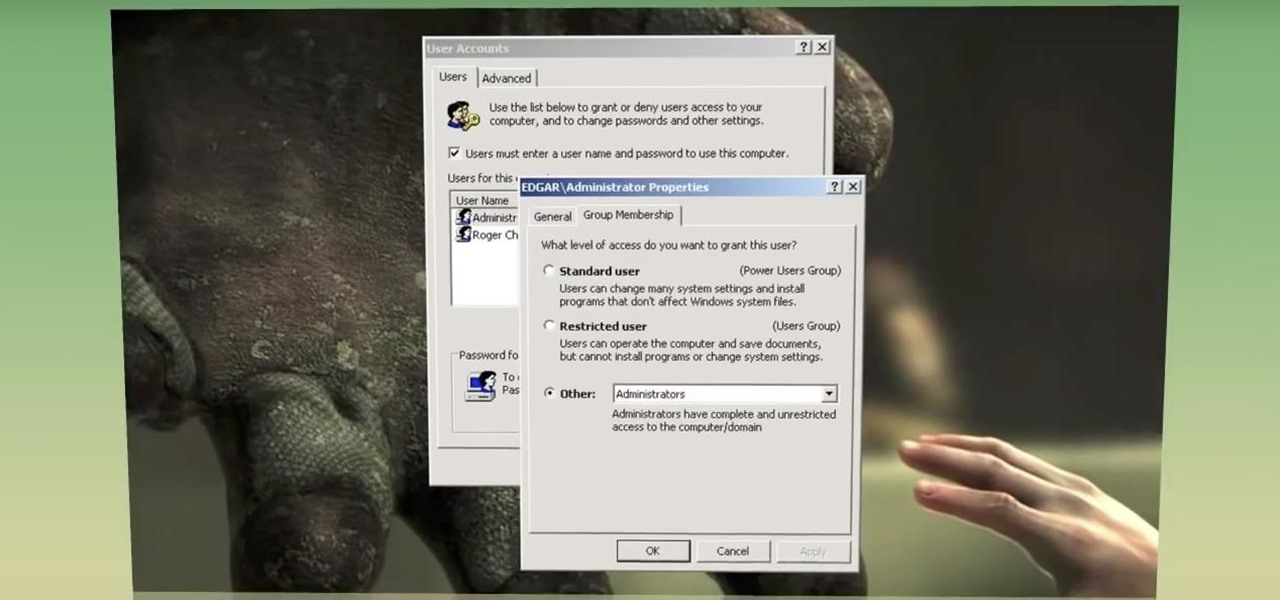
Configuring user accounts is extremely important for those with a family shared computer or anyone using a work computer. Assigning different accounts with their own distinctive accessibility, customizations, and applications is the best way to manage a computer with multiple users.

Everyone knows that using your phone and driving is illegal, and rightfully so. Tons of people die on the road everyday due to careless people texting or calling someone. Everybody knows that it's wrong, yet everyone still does it anyway.

In this video tutorial, viewers learn how to disable User Account Control in a Windows Vista computer. Begin by clicking on the Start menu and select the Control Panel. Then type in "user account" in the search box and click on "Turn User Account Control on or off" under User Accounts. Now deselect the checked box and click OK. Finish by clicking on Restart when the Microsoft Windows window pops up to reboot the system for the changes to take effect. This video will benefit those viewers who ...

Basically there are three quick ways to run a program as administrator. You can do that by clicking on cmd. We usually use this cmd prompt for finding your I.P. address and you can modify user accounts also. Another way is to click on start and type cmd in Run. Make a right click on cmd and click Run as Administrator. Final way to run program as an administrator by having right click on the program and select properties next select Compatibility, then select Operating System and finally, sele...

This video tutorial from Help-Vids shows you how to setup the automatic login in Windows XP so that you are automatically logged in as a specific user when you turn your PC on. Go to the start menu, select run and type the given command. When the user account dialog opens un-check the setting requiring the user to enter a name and password to use the computer and click apply. Fill in the user name and the password of the user that needs to be automatically logged in and click OK. Now when you...

Admin accounts are given special privileges to change the system (like installing programs) that user accounts are not. This tutorial shows you a quick way to check using Windows 7's calendar, and also how to go through the Control Panel to find out if you're an Admin or general User on your computer.

In this tutorial, we take an introductory look at node based compositing from the perspective of an After Effects user. If you are someone who has lots of experience with After Effects, and wants to get into using a program like Shake, Nuke, or Fusion, this will help you get on the right track. Whether you're new to Adobe's popular compositing application or are just looking to get better acquainted with AE and its various features and functions, you're sure to enjoy this free video software ...

Network mapping lets PC users organize multiple computers into a system that provides informational data access. This video tutorial shows how to set file sharing permissions and assign users designated privileges within a network. Establishing a network provides functionality within a workplace and facilitates virtual communication among users.

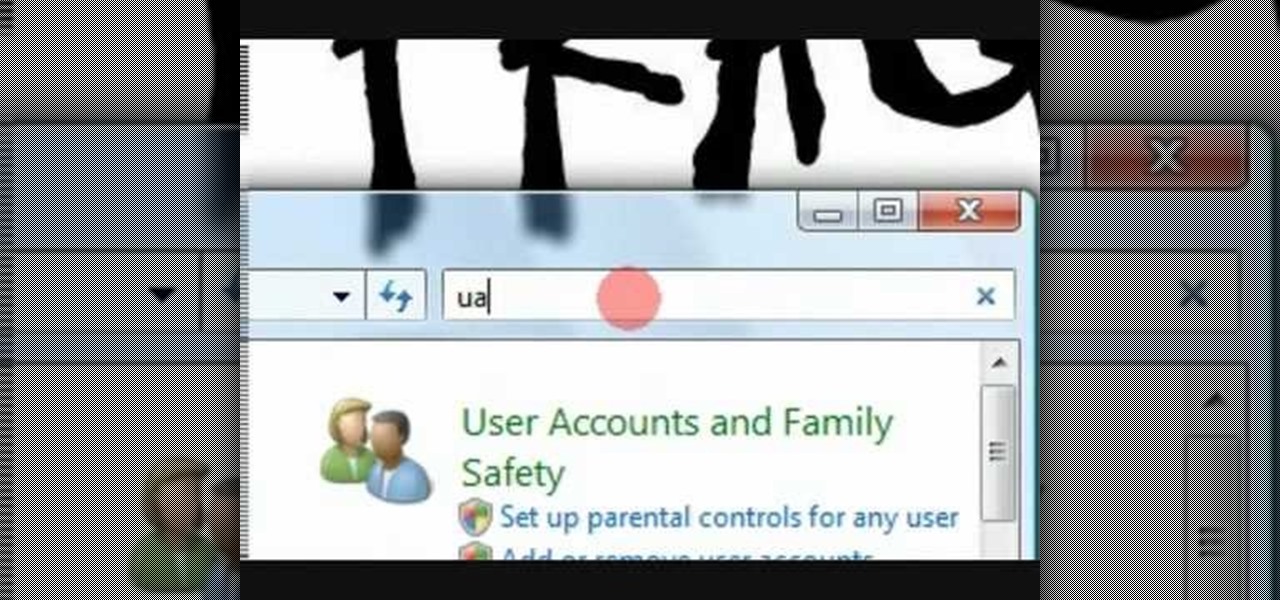
In this video the instructor shows how to set parental controls for a user ID account in Windows 7. To do this go to the 'Start Menu' and go to 'Control Panel'. In the Control Panel window select the 'User accounts and Family Safety' link. There is an option called 'Set up parental controls for any user'. Select that link and it opens a window where it asks you to Choose a user and set up parental controls. There you are presented with some user accounts that are currently active on that syst...

This video shows how to delete a user account on Windows 7. Go to the start menu, the control panel, then user accounts. Click add or remove user accounts. Select the account you want to remove. Choose the option to delete the selected account. Windows will ask if you want to delete everything on the account or keep the information on your desktop while still deleting the account. This will be your choice. The narrator chooses to delete the full account.

This video describes how to create a new account on Windows 7. In this video it is shown the whole procedure and all you need to know to crate new user account.

This video demonstrates how users of the FileMaker Pro 10 software can easily start using this software from the quick start menu. It is demonstrated to users how to create a database or open an existing database from this quick start page. Also demonstrated is how users might be able to find further information using the "Learn More" option at the bottom of the menu. This option shows users the basics via videos, tours, and tutorials. A must see for those new to this software.

Microsoft Word 2010 prevails with new advancements. New options such as Backstage view allows the user to work efficiently and utilize new abilities when managing documents. It succeeds with new abilities that will allow the user to complete tasks quicker than before. Working with the newly enhanced ribbon allows the user to navigate with an easy, more personal customized environment. Now with more options and commands at your fingertips, it is evidently shown that Microsoft is gifting users ...

Is Windows XP just not customizable enough for you? Well, it was made that way so you don't eff up any of the settings to the point of no return. However, if you are confident in your computer expertise then modifying user accounts may be something of interest to you.

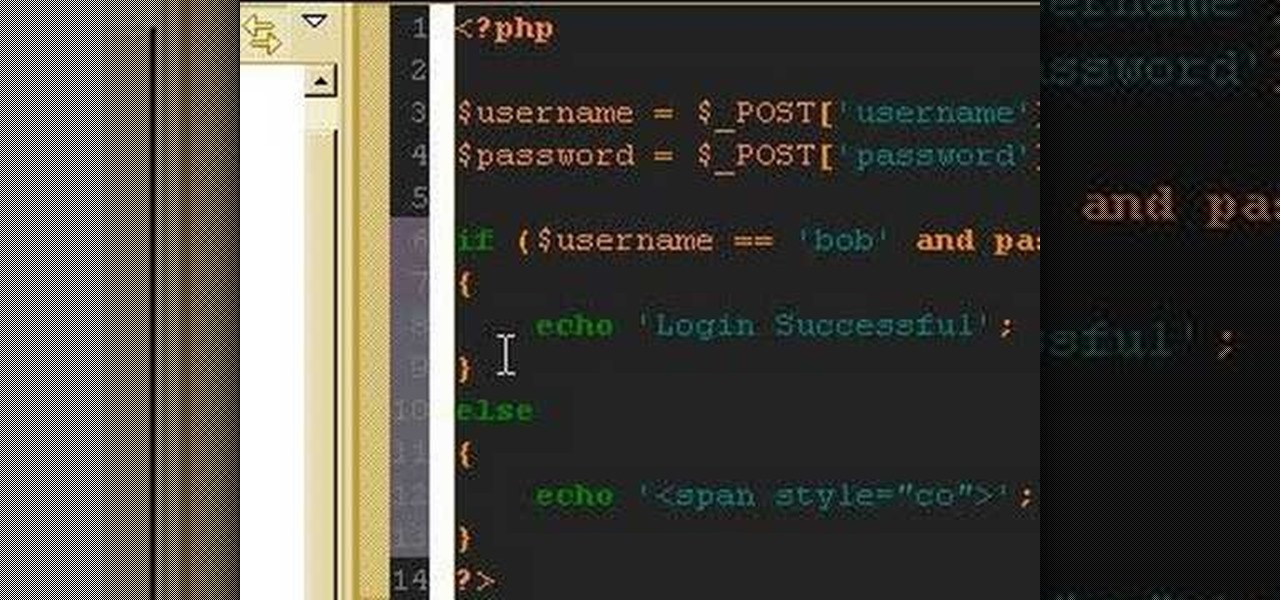
Using PHP & HTML to generate a user login form and authenticate the user.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

In these video tutorials, viewers learn how to tie the ribbon on ballet shoes. Make sure that the elastic and ribbon are adequately secured on the shoe. Begin by flexing your foot. Take the inside ribbon and loop it across the top of your foot. The outer side ribbon will go over the inner ribbon. Pull the ribbons tight enough so there is no gaping or sagging. Then, wrap the ribbons around the ankle and tie them together. Now, tuck the tie under the flat part of the ribbon. These videos will b...

Washington State has a history of large earthquakes, as does California. More than 1,000 earthquakes are registered in Washington State each year. More than 10,000 are recorded in California each year. In an earthquake, non-structural elements, which is anything that does not actually hold the building up, may become unhooked, dislodged, thrown about, and tipped over. this can cause extensive damage, interruption of operation, injury and even death.

Not every nurse can get an IV every time, that's why it's important to stay in practice for the proper technique used for inserting a peripheral IV. This is a common medical procedure that all fields related to medicine should know. Even the soldiers in the military are taught how to insert an IV — every soldiers, not just the medics.