The first time a friend or family member asks if they can borrow your phone or tablet, you probably just hand it over without a second thought. But the second, third, and fourth times? Now it's starting to become a habit, and something probably needs to be done about it.

Five Phases of Hacking:- The five phases of Hacking are as follow:

A few lines of code in the iOS 9.1 library cache found by Chase Fromm (@uloshe) indicate that Apple could be working on making iPhones that are Li-Fi compatible.
For reasons unknown, Microsoft decided to change the way the Guest account feature in the new Windows 10 operating system works. In previous versions, the Guest account feature allowed you to set up a limited account for other users so they don't have access to your important documents and settings. Now, the process requires assigning an email to a new account and configuring share settings.
Since the release of Windows 8, Microsoft has been heavily encouraging users to use Windows with a Microsoft account. According to Microsoft, the main benefit of using a Microsoft account is the ability to sign in and sync your information across various Microsoft devices and services. Furthermore, you have access to a singular cloud storage solution which can contain documents, pictures, settings, and more on whatever system you're using with the Microsoft account.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Before phones became mobile-gaming, music-playing, app-downloading devices, they were used simply to make convenient, cordless phone calls. There's so much on phones these days that a passcode is needed to keep everything secure, and making calls is now more complicated.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.

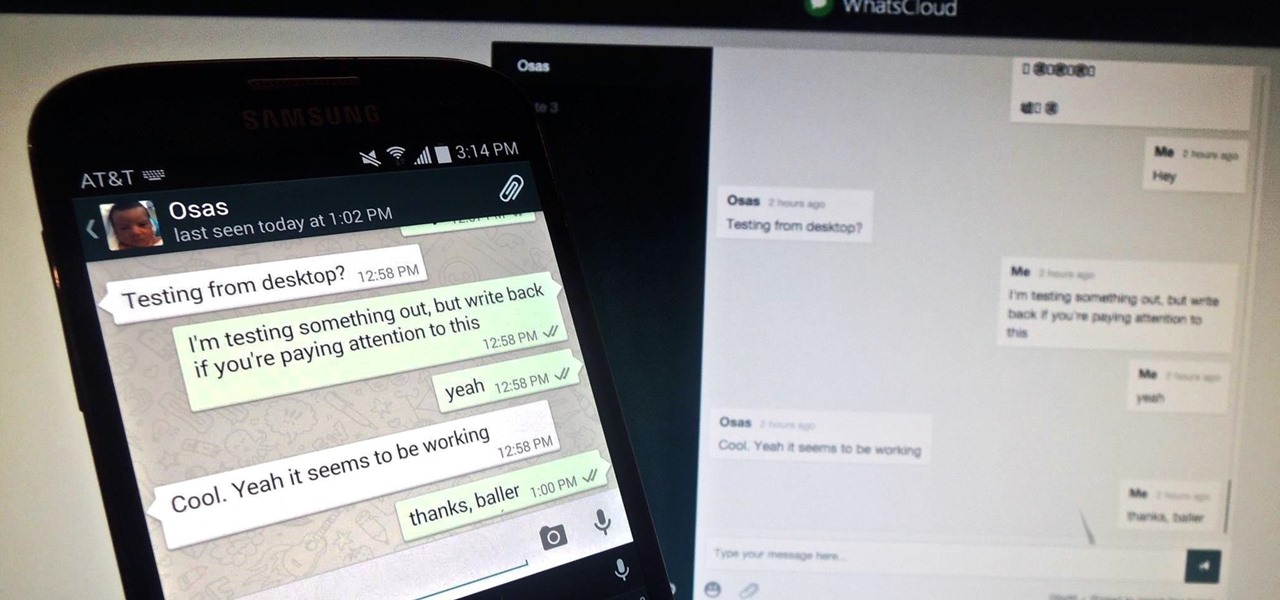
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.

When Google released Android 4.2, a new feature was introduced for tablets that allowed for multiple accounts to be used on a single device. In order to create a unique experience for each user, apps and personal data were kept separate, and switching between users became as simple as tapping your profile photo from the lock screen.

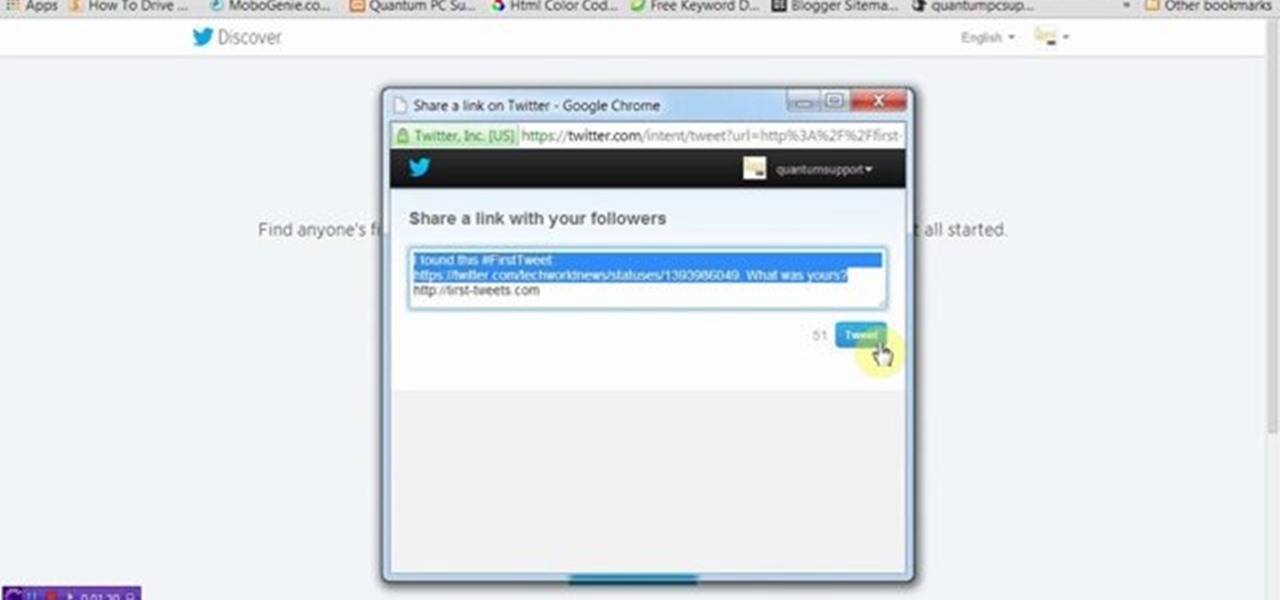
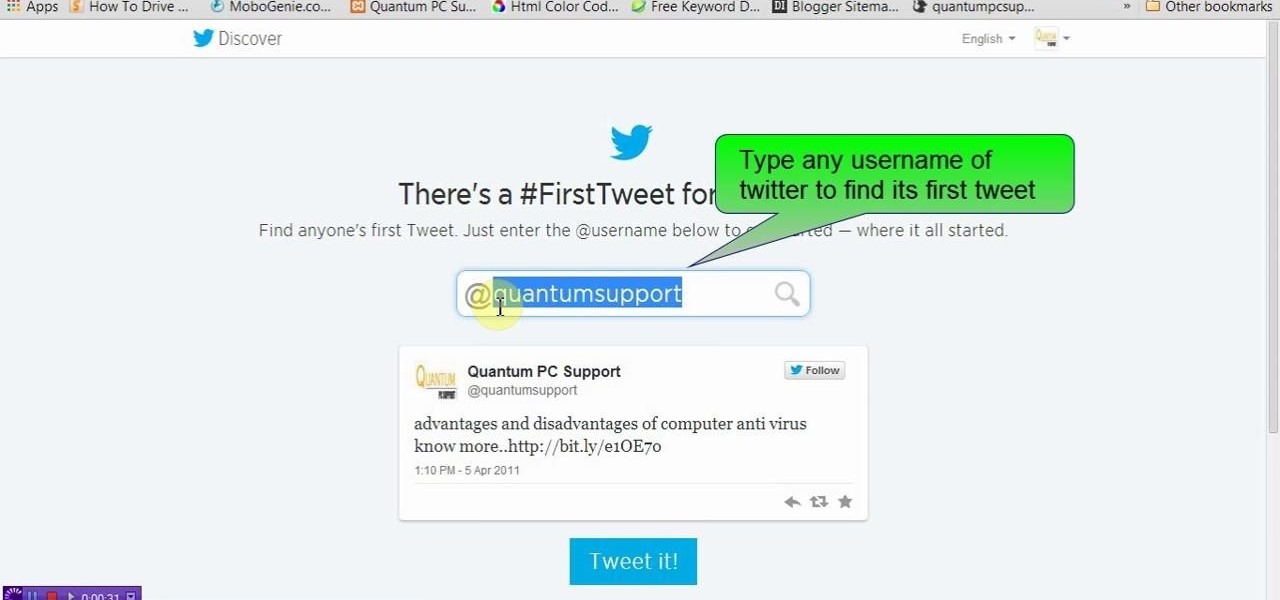
This tutorial video will show you how to find first tweet of any user in Twitter. You have to type first-tweets.com in address bar of your browser. The site will be redirected to discover.twitter.com/first-tweet page. Just type any user name and twitter will show the first twit of that user. Watch the video and try it yourself.

This video will show you how to see first twit of any user in twitter. You could type https://www.first-tweets.com in address bar and the site will be redirected to another place https://www.discover.twitter.com/first -tweet page. You have to enter the user name and twitter will fetch the first twit of that user. Watch the video and employ it yourself.

In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

If you're as bad at locking your Nexus up as I am, you have the "slide" option set for your screen lock. It may not be the most secure option, but it's definitely the easiest way to unlock your device while being able to utilize lock screen widgets.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

Jake von Slatt of The Steampunk Workshop kept breaking the rear glass panel on his iPhone. So, he ended up making his own gorgeous replacement out of brass to replace the standard Apple logo ones who kept getting. The only problem was that it made his signal strength super weak, so he figured out how to transfer the etching onto a glass back. Here's the basic rundown of how he accomplished this feat...

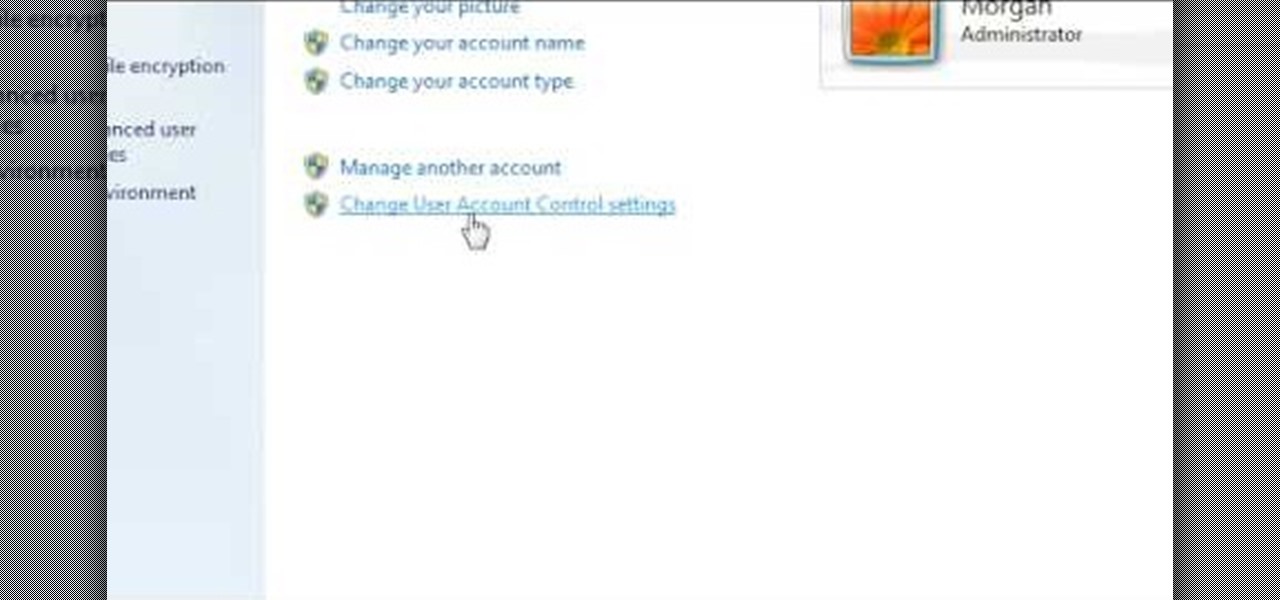
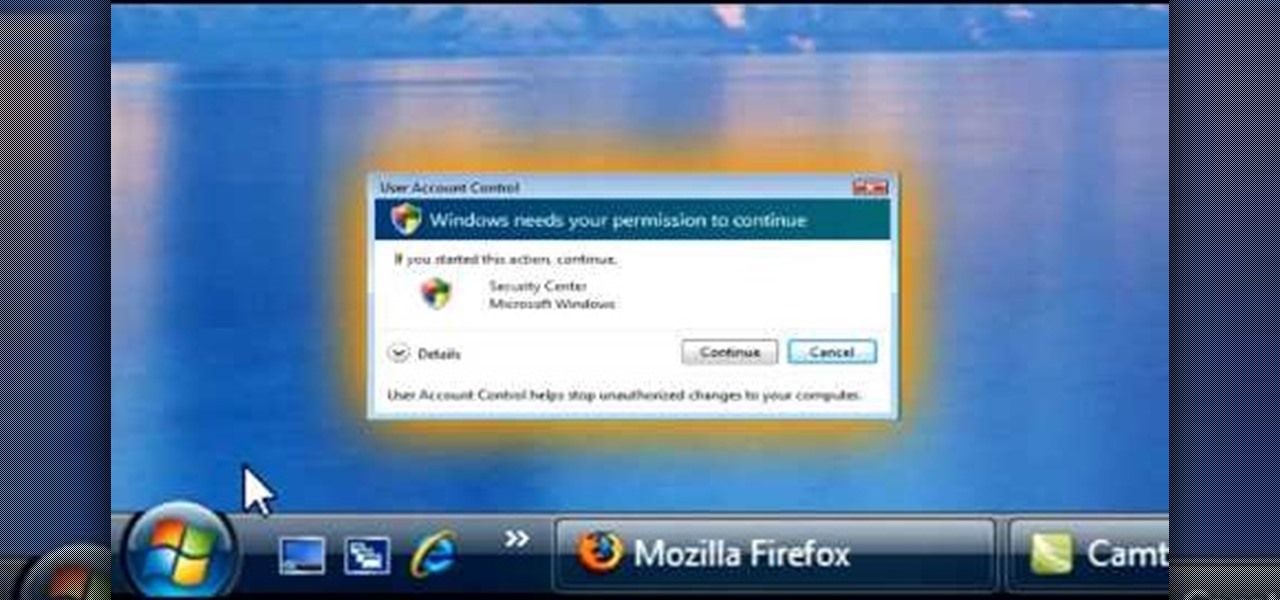
In this video, we learn how to turn off user account control (UAC) in Windows 7. First, go to your desktop and then the start menu. From here, go to the control menu and then user accounts. After this, go to change your user account control settings and a new window will pop up. From here, change the bar from the top to the bottom where it does not notify you, or wherever you want it to be that suits you the best. To finish, you will save this and then exit out of all the windows and your set...

This video describes how to create a new user account on an Apple Mac OS X 10.6 (Snow Leopard) computer to tell whether your Pro Tools problem is user-specific or global. Whether you're new to Digidesign's Pro Tools 8 or simply looking to pick up a few new tips and tricks, you are certain to benefit from this free software video tutorial. For complete instructions, take a look.

Want to keep other users from accessing certain applications, files or folders? This video tutorial will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in just over a minute's time. For more information, including detailed, step-by-step instructions, watch this Win 7 user's guide.

This Blender user's tutorial covers camera movement from camera view, the render panel, and the ambient occlusion panel. Whether you're new to the Blender Foundation's popular 3D modeling program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look.

Microsoft has released its latest rendition of the Windows operating system, Windows 7. Windows 7 succeeds Windows Vista and comes with many improvements and useful updates. To install the update one a personal computer running Windows, a backup of the user's personal files and data onto a detachable hard drive is recommended to prevent data loss during the update process. The ISO image of the Windows 7 OS is burned onto a DVD. A partition is optionally created on the user's computer to allow...

Revision3 Internet Television and Tekzilla Daily with Veronica Belmont demonstrate how to unlock Vista's super user mode. First, open the start menu and type CMD. Right click the command prompt and select the run as administrator option. Type the code net user administrator / active:yes. Hit enter. Your system should reply with the command completed successfully message. Then, the next time you restart your system, you'll see the administrator as an option in the welcome screen. If you use th...

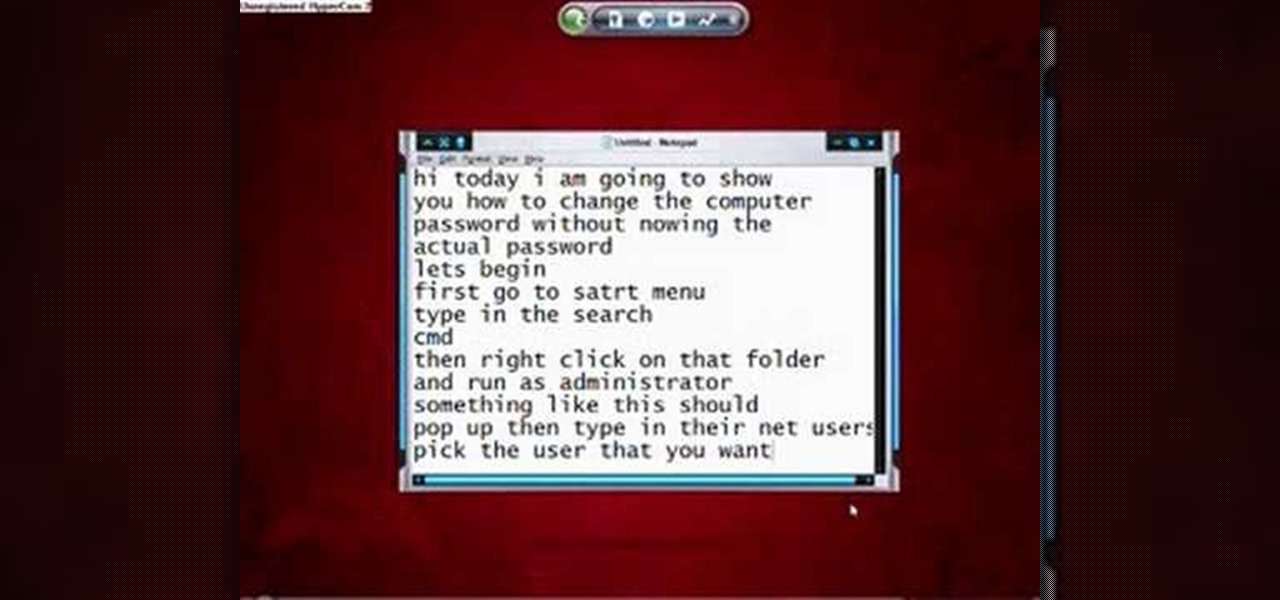
This video shows how to hack the computer password for Vista. We can change the computer password without knowing the actual password. First go to Start menu. Type in the Search "cmd". Then right click on that folder and run as administrator. Then we get a pop up. Type in their net users. Pick the user that we want to hack into. After picking the user type in net user the username and then * . After typing this hit enter key and it should say the command completed successfully and we have to ...

In this video tutorial, viewers learn how to negotiate with a credit card company. There are 3 main items that users can negotiate. The first item is the date of payment. Users are able arrange a more convenient date for payment. The second item is the annual fee. Users are able to work out a way to not have to pay an annual fee for using a credit card, which will help save money. The third item is the interest rate. Users can negotiate and try to lower the interest rate that they must pay. T...

In this video tutorial, viewers learn how to block certain users from seeing their Facebook account. Begin by logging into your account and go to your home page. Click on the Setting tab and select Privacy Settings. At the bottom of the page, under Block List, there will be a space for users to type in a persons name to block and click Block. Select the person from the list of people and click Block. This video will benefit those viewers who use Facebook, and would like to learn how to block ...

In this video Jesse Liberty demonstrates how to create user controls dynamically (at run time) and how these user controls can raise events to interact with the page that creates them. This is a step by step, extensive tutorial on exactly what you'll need to know when using Microsoft's Silverlight. This is a detailed, easy to follow video, to help you use the program, and all it entails.

In this video tutorial, viewers learn how to clean the rear LCD on a camera. Begin by dry cleaning using Giottos Rocket Blower and nylon fine brush. Users will also need a isopropyl rubbing alcohol and microfiber cloth. Users may also need gloves to protect their hands from the alcohol. Begin by blowing off any dust and brush it with the brush. Now users will be wet cleaning using the isopropyl alcohol and microfiber cloth. Users are advised to clean weekly. This video will benefit those view...

1. To disable the UAC (User Account Controls), first click start button and type "msconfig" into the start search text box.

In this video tutorial, viewers learn how to use Skype. Skype is a software application that allows users to make voice calls over the Internet. It is very similar to MSN messenger. It allows users to communicate through instant messaging, voice chat or have a video conference. Users are able to communicate with others anywhere in the world who also have Skype. It is a free program. Users will need to make an account and download the program. This video is very descriptive and clearly explain...

This video was made to help users with disabilities use Windows XP more efficiently in their lives. Starting with entering the control panel the and clicking on the accessibility options the user will have an array of options to help customize their settings to their needs. The demonstrator showed that sticky keys are for those who have a difficult time holding down buttons at once for functions. The filter key eliminates double strokes for certain keys so you would need to hold down a key to...

In this video tutorial, viewers will learn how to make homemade beef jerky. Users will need meat in freezer for 20 minutes and a knife. It’s important to cut off the fat. Cut the meat into thin strips (like beef jerky). Users can press down on meat to make it thinner. Users may decide to add some flavoring and spices. Put the meat strips into a smoker grill. Users may also choose flavor of smoker wood to enhance flavor. Start the smoker and wait for 3-4 hours. This video will benefit those vi...

TheCondowit shows you how to put an SNES emulator on your R4/M3 card. The user says that the first thing you want to do is goto SNEmulDS homepage then scroll down when you get there and goto the green text. Next the user tells you to click on the R4DS / M3 Simply. The user then walks you through some more steps then shows you a live demonstration of the emulator in action to confirm that it works. After following all the steps the user provides, you should be able to put an SNES emulator onto...

This video tutorial shows you how to turn off USER ACCOUNT CONTROL in Windows 7. Step 1 : Go to START and select CONTROL PANEL .

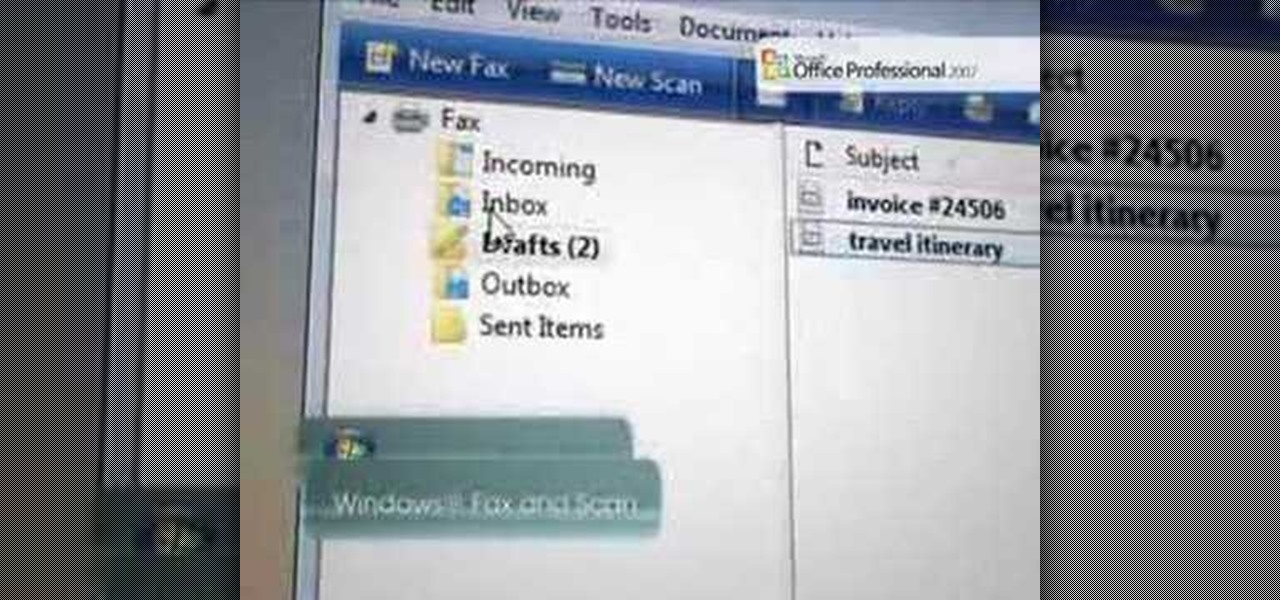
With Windows® Fax and Scan feature that works with the Windows Vista™ operating system makes it even easier to share fax and scanning capabilities with multiple users. Where previous fax and scanning programs allowed an individual user to send and receive faxes or scan documents with a locally-connected fax or scanner; Windows Fax and Scan provides a flexible system for multiple users to share local or network-connected scanners and fax devices. F

The User Dashboard in OnTime is a great way to look at items across types and edit them. See how to view and search through data regardless of its type (Defect, Feature, Task, Incident) by taking advantage of the User Dashboard. For detailed instructions on using the dashboard, watch this installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite.

Ever wish you could switch between users on your Mac without having to kill all of your applications (and losing all your data) in the process? In this tutorial, Molly Stanberry from MacMost.com Shows how to enable fast user switching in Mac OS X Leopard.