Last week, the internet was ablaze with talk about the Galaxy S8's home button, because it subtly changes positions without the phone alerting you. This feature was included to stop burn-in issues with the screen, and the general consensus from tech sites was the screens would not experience any burn-in at all.

Bose Corp is the latest company trying to make another dollar off of you without your permission. Bose Connect, the companion app to the swag $350 Bose headphones, is not the Jane to your Jack that maybe we all hoped it to be.

The first augmented reality hardware and software functional requirements guidelines have been released today by UI LABS and the Augmented Reality for Enterprise Alliance (AREA).

Pinterest, a worldwide catalog of ideas shared by over 175 million users every month, is dominated by Android users, who are now the app's fastest growing group. Pinterest has since taken notice, and has started to incorporate handy home screen shortcuts for users with Android 7.1 or higher.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

Bitmoji has experienced explosive success this year thanks to Snapchat. The app allows users to create their own personal emoji and send responses to other friends, and even though it's only two and a half years old, this customizable emoji app is growing at an impressive pace.

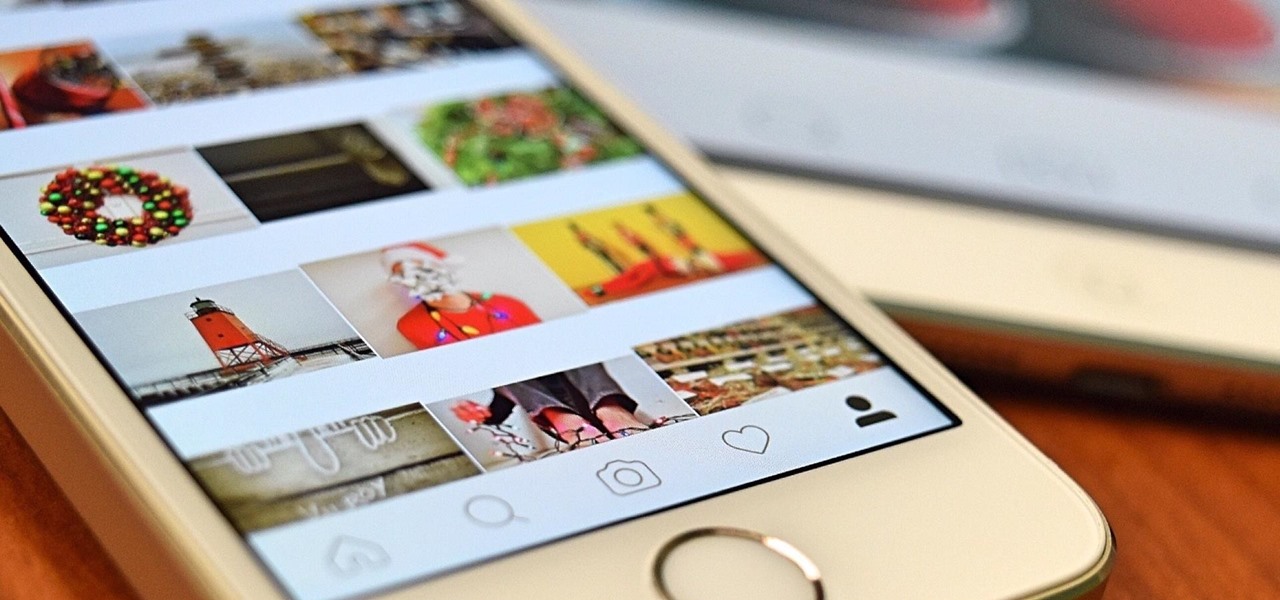
Starting today, you'll have the opportunity to save all your live Instagram videos to your phone at the end of each broadcast session. The latest update to the Instagram app now allows you to rewatch already-played broadcasts and gives you the ability to share them later on.

A new app called Roadie now makes life a little easier by connecting users to people who can transport their stuff. The app allows users to transport anything from dogs to getting rid of your ex's things. Furthermore, anyone can register as a sender, or become a driver to make an extra buck. The app is very easy to use: simply download (the app is available on both iOS and Android) and register using an email address or with Facebook. Using the profile you've created, users then select whethe...

Google Assistant has introduced tappable shortcuts on the Google app for Android, iOS, and Google.com this week.

A development team in Silicon Valley is nearing early access release of a new hardware-independent augmented reality platform called Phantom AR.

We live in a marvelous age, a time where technology is driving us forward as a species at a rapid pace, and tech-driven miracles are becoming more and more commonplace. While the human race may not be focused on building the largest wonders of the world, as it once was in history, the current order of wonders are much smaller in scale—even internal.

An interesting new use-case for the Microsoft HoloLens appeared in a YouTube video from Washington-based DataMesh last month. In it, you can see the HoloLens working in conjunction with the Microsoft Surface Studio, Surface Dial, and Surface Pen for 3D model detailing and visualization in real time.

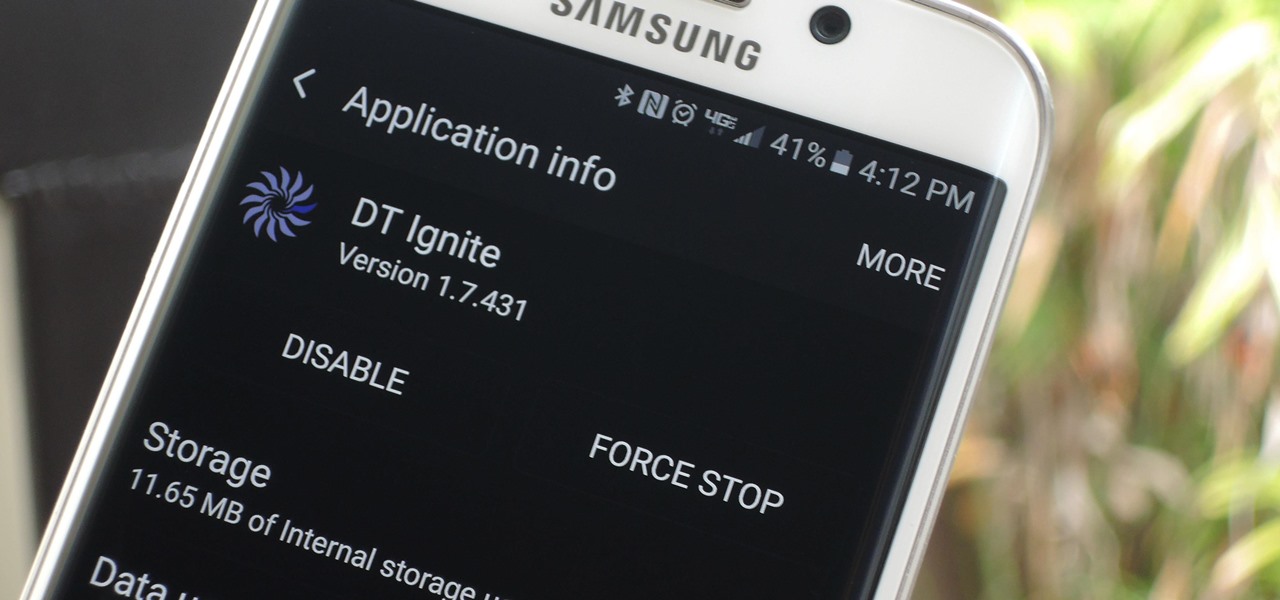
A few months ago, it was discovered that Verizon was installing an extremely shady app called "DT Ignite" on some of its smartphones—most notably, the Galaxy S7 and S7 Edge. The app, created by Digital Turbine, monitors your smartphone usage, then uses the data it collects to silently install "recommended" apps without notifying you.

Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.

According to multiple users on Reddit, the Pixel and Pixel XL's camera can have some serious auto-focus issues if you're using a certain type of case with Google's new flagships. When the problem occurs, your camera app will refuse to settle on a focus point, making almost everything in the frame blurry. Redditor HeshoMike uploaded a video of the phenomenon, and you can see it in action here:

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

We're so used to seeing things in particular ways that anything different just doesn't make sense to our brains. Culturally, we like to read things from left to right, and from top to bottom. Change that and our brains struggle to adjust.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and instead, will only be offering 1 TB of storage.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.
Welcome back Hackers\Newbies!

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

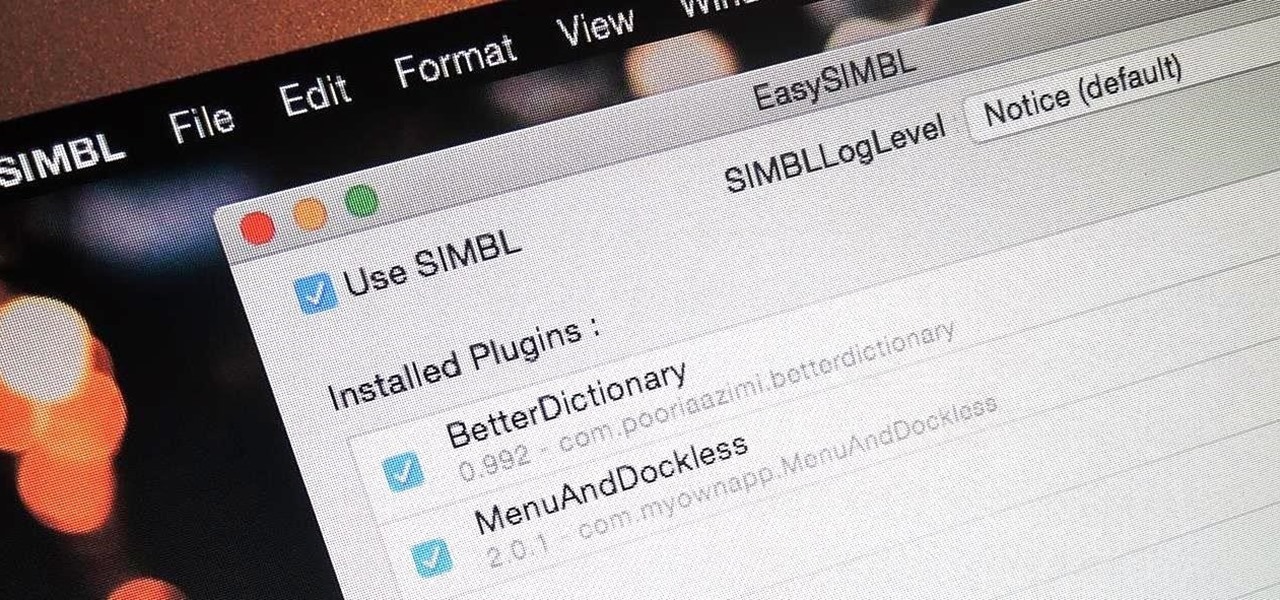
When you buy a Mac, you accept that you're giving up the customization found on Windows or Linux systems for a more fluid and secure machine. This is great for most consumers, but for those of us who'd rather opt for a tailor-made experience, there are always developers that can combine functionality with stability.

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

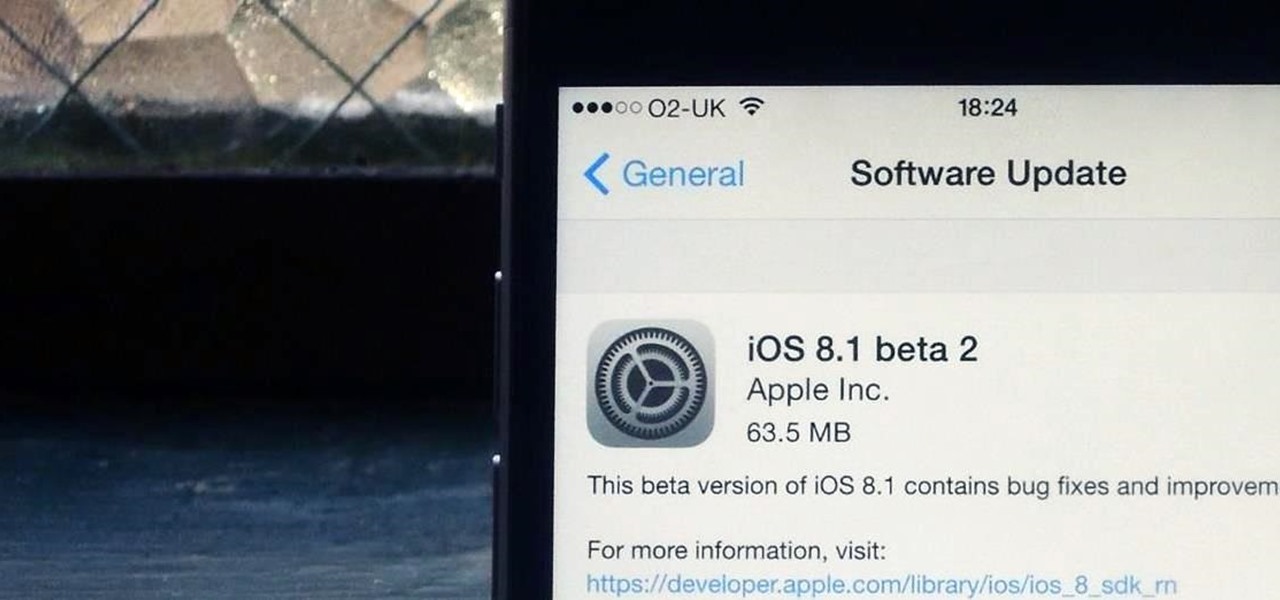
Shortly after Apple's iOS 8.0.1 update fiasco ruined many iPhone users' cellular reception (which was fixed with iOS 8.0.2), developers were treated to the first beta release of iOS 8.1, which will be the next big update for iPad, iPhone, and iPod touch.

Accessing your favorite and most recent contacts on your iPhone is now faster than ever before, thanks to the iOS 8 update. Just double-click your Home button, select your contact above the app switcher menu, then choose how you want to contact them.

It's been a long-rumored feature, but today, VoIP calling has finally started rolling out to users of Google's Hangouts service. Essentially integrating Google Voice into the popular messaging platform, Google has given Android (as well as iOS) users an easy way to make calls without eating up their plan's minutes.

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

The Galaxy S5 is a flagship-level device with some pretty advanced features, like its 4K video recording capability, water-resistant casing, fingerprint sensor, and KitKat running out of the gate.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

Most hardcore Android fans loathe carrier or manufacturer additions to the Android operating system. Whether it's bloatware or changes to the user interface, many enthusiasts prefer the clean look of stock Android.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Nearly two years ago, Peter Chou, CEO of HTC, confirmed that the company would no longer be locking bootloaders. Whether or not they've actually lived up to this claim is debatable. Any phone bought from a wireless carrier comes locked. Only the new HTC One Developer Edition ships with an unlocked bootloader, and it does not have any carrier add-on software installed.