In this video tutorial, viewers learn how to make funnel cakes. Users will need some cream puff dough. Place the dough into a disposable plastic bag and snip off one of the corners of the bag. This will allow the user to squeeze the dough out. Then heat some oil at medium heat for 3-4 minutes. Now pipe the dough into the boiling oil in a circular motion. The dough should sizzle in the oil. Cook the dough for 2-3 minutes on each side. Finish by draining the dough and add some powdered sugar. T...

In this video tutorial, viewers learn how to completely uninstall a program on a Mac computer. There are 2 ways to uninstall applications. The first way is to drag the application into the trash bin. With this method, users will also have to drag the related, numerous preference and supported files. The second ways is to download an application called App Zapper. With this program, users just need to simply drag the application into the App Zapper program to completely uninstall it. This vide...

In this video tutorial, viewers learn how to get their music heard. To get their music heard, users should create a mix tape of their best songs. They need to have connections with a music producer or have friends that have connections with a music producer. This will allow the friend to introduce you to the music producer. Users also need to put out their records on their own in public places such as clubs or parties to allow any nearby music producers to listen. This video will benefit thos...

In this video from Dr. Carlson, users are shown how to witness the effects of the relationship between temperature and matter firsthand, using light-sticks. For the experiment, users need 3 beakers (or vessels of the sort,) and 3 light-sticks of the same color, shape, and light. To test the range, each beaker must correspond to one of the following states: room temperature, ice-water, or boiling water. Deposit a stick in each of them and observe for two minutes. Thus, one will see how the ato...

In this video tutorial, viewers learn how to improve the control and shooting of iron golf clubs. Most people when they hit a golf ball go short of the green. Users are advised to use one more club (instead of 8, use 7). This will allows users to swing easier, allowing more control. When hitting with an iron, make sure it leaves a divot. It gives a better chance of contact and backspin. Find out where your swing hits the bottom. This video will benefit those viewers who enjoy playing golf and...

In this video from diethealth, viewers are shown how to perform a bridge with an exercise ball. The process begins with the user lying flat on their back, and having their legs positioned on the ball so that their knees are bent. Then, they must lift their hips so that their spine is in a neutral position, and then lowering it back to its previous position. Along with the lifting, they must inhale with the lifting and exhale with the descent, while tightening their gluts and shifting the weig...

The tutorial focuses on using Cheat Engine 5.5 to cheat (or hack) Epic Battle Fantasy 2, an online RPG game. The user will need to choose the "Epic Mode" under difficulty setting. The tutorial maker's mouse also shows where the user is clicking for the menu to come up. This tutorial is directly recorded from the tutorial maker's desktop, rather than using a video camera, therefore, the graphics are clear and just like what you would normally see on your desktop when you're playing. If you fol...

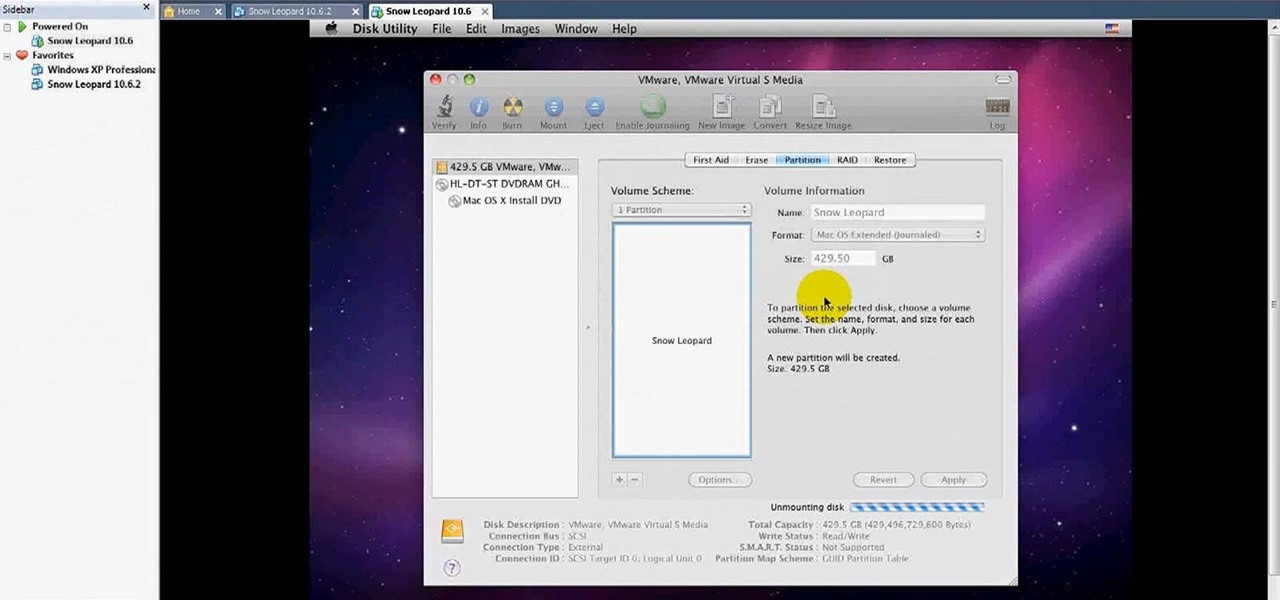
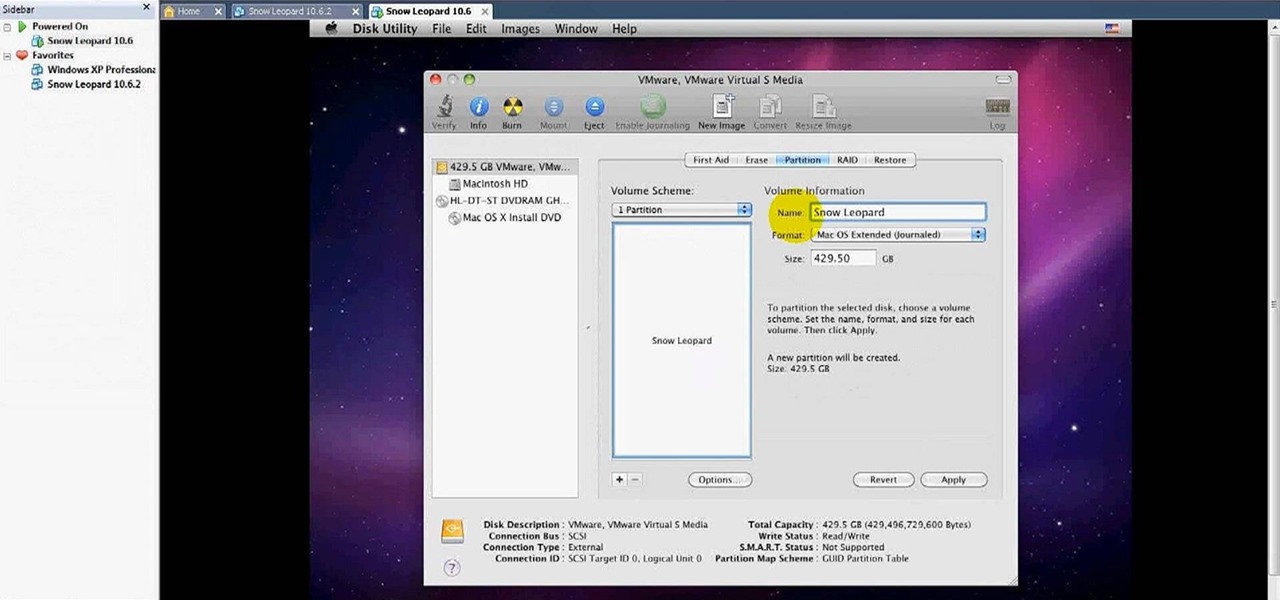
In this video tutorial, viewers learn how to install Mac OS X Snow Leopard in Windows PC using VMware Workstation as virtual machine. Begin by downloading the program from the link provided in the video description. ISO image is made especially for Windows PC users. Mac users can download the DMG file from there too. This video is a complete tutorial for installing Snow Leopard in Windows 7, XP, or Vista.

In this video tutorial, viewers learn how to install Mac OS X Snow Leopard in Windows PC using VMware Workstation as virtual machine. Begin by downloading the program from the link provided in the video description. ISO image is made especially for Windows PC users. Mac users can download the DMG file from there too. This is a full video guide on how to install Snow Leopard in Windows 7, XP, Vista using VMware Workstation and download all the software (VMware workstation, Mac OS X Snow Leopar...

In this video tutorial, viewers learn how to cheat on the flash game Dead Frontier Outbreak. Dead Frontier Outbreak is a new promotional game released on multiple game sites by AdminPwn. It is a text-based zombie adventure game, complete with voice acting. It was created mainly to promote Dead Frontier among gamers who may not have heard of it. To perform this cheat, users simply right-click and select "forward until it reaches the end of the game." Users only need to do this three times. Thi...

Veteran video walkthrough provider Tasselfoot shows users how to beat all 30 levels of the browser based game Factory Balls 3, step-by-step. Gameplay revolves around dropping balls over tools in the correct order, in order to recreate the ball pictured on the box. The game features 30 levels, with later levels more challenging. The game is the third in the "Factory Balls" series, a creation from none other than Bart Bonte, of "The Bonte Room" fame; users who enjoy his brand of eccentric puzzl...

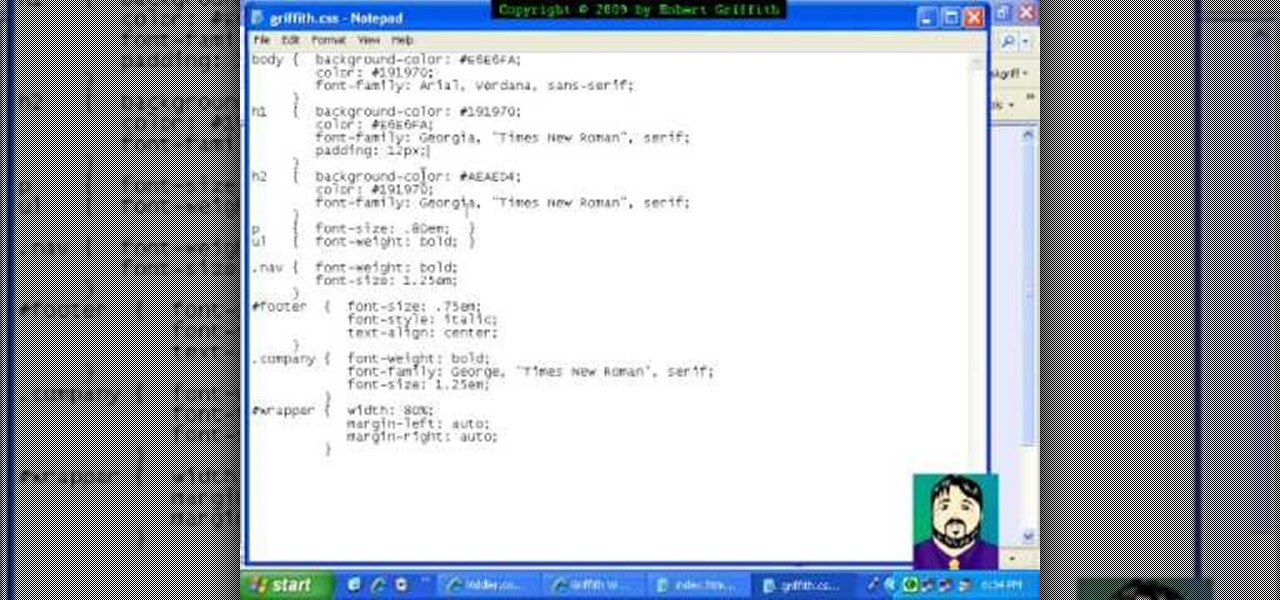
Have you seen extravagant graphics on web pages or in the GUI (Graphical User Interface) of a commercially published program? Do you wish you could create graphics comparable to published works? Now you can! This tutorial will take you step by step in creating visual elements in CSS. Cascading Style sheets are the present and future of web pages and this tutorial will make sure you are not left behind. The visual aspect of web pages are of utmost importance and the major determinant of a user...

On this YouTube video the user Vvistacomphelp shows you how to print screen and crop pictures. The first thing that the user shows is where the Print Screen button is located at on most keyboards so that you can press it on yours. The second thing is go to the start menu in Windows Vista and type in "paint" in the search box on the bottom left then open Paint under Programs. The third thing that is shown is how to make an image appear inside of the paint program so you can crop it. After foll...

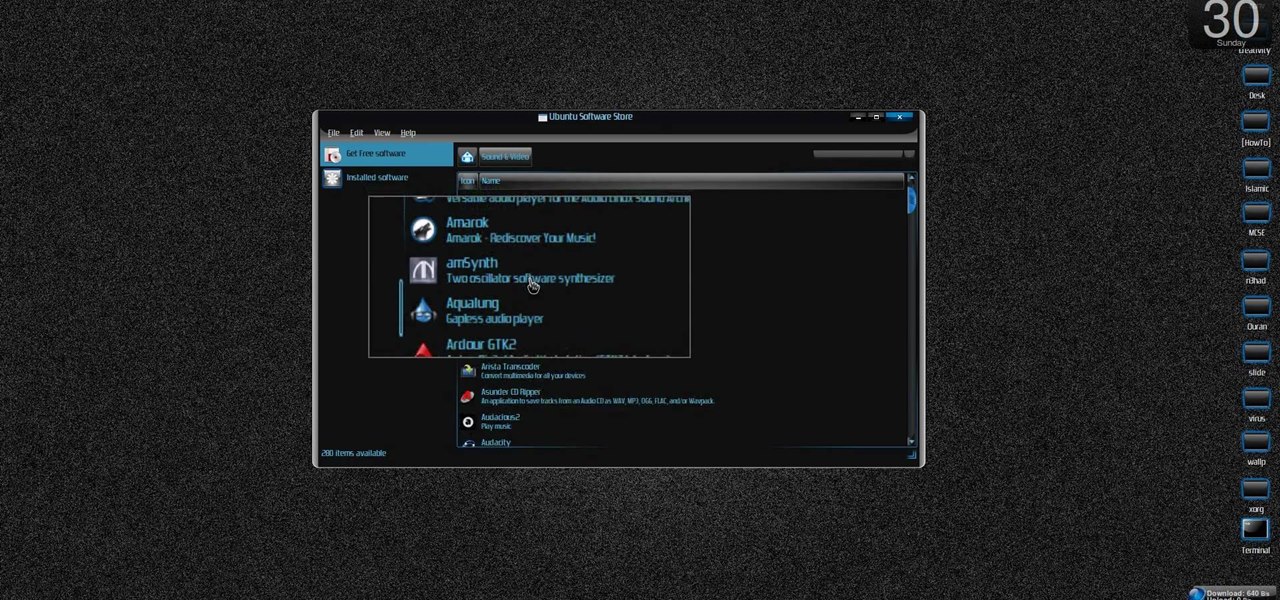
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install the Ubuntu Software Store on Ubuntu Linux.

This innovative handset makes user convenience its priority. Created with the aim of overcoming the limitations of existing mobile phones, every function is available through a flexible layout of navigation keys. Fixed keypads are a thing of the past with the LG KF600 Venus cell phone.

This tutorial goes over how to edit the text document that controls the hot key (shortcut key) commands. It doesn't go into the advanced commands or even begin to describe the various commands that you can invoke by changing the text document, but most of the users who will be editing this are ADVANCED USERS. NEVER. NEVER change the shortcut settings on a machine that is not yours and ALWAYS. ALWAYS make a backup copy of the document before you start to work on it.

Apple's upcoming iOS 17 is expected to include many new features first seen on Android, but there are also some exciting, unique features that Android needs to steal pronto.

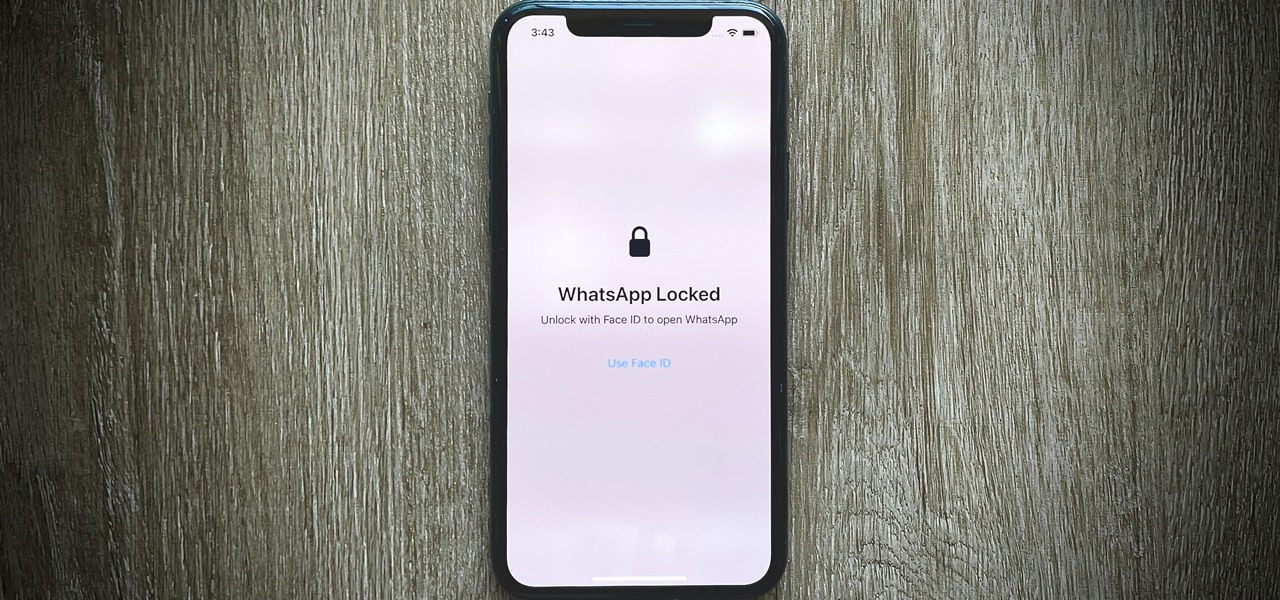
End-to-end encryption makes WhatsApp chats private and secure. However, if someone has access to your iPhone, they can easily open the app and browse through all of your personal conversations. Luckily, there's an easy way to block any would-be intruders at the gates — just lock the app behind Face ID or Touch ID.

It's time to make some more room at the augmented reality cosmetics counter. This week, social media giant Pinterest unveiled "Try On," a virtual make-up visualization tool running on its Lens visual search tool.

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

A century-old opera is getting a revamp in the UK after swapping dusty wigs and curtains for augmented reality overlays and Snapchat filters.

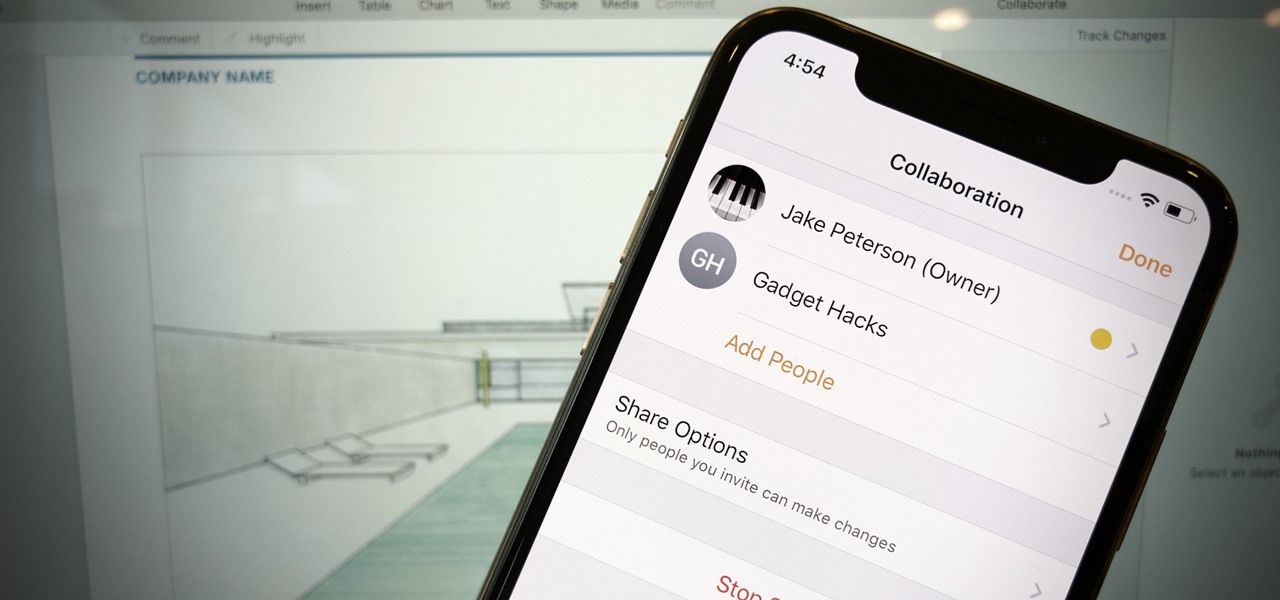
Google Docs is made for teamwork and collaboration, but Apple's iWork suite also comes with the same functionality. If you're working on a Pages document on your iPhone, and you want input from other members of your team, you can easily invite them to view, comment, edit, and more right alongside you.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

In recent years, augmented reality has increasingly helped to take art off museum walls and bring it (virtually) into people's homes and communities, offering new perspectives on classic pieces and modern creations alike.

While Magic Leap has remained mostly silent regarding its plans for its Magic Leap One successor, the software team continues to makes strides with improvements to the device's Lumin OS and SDK.

Now that we've officially seen the HoloLens 2 and Microsoft has shown off the improvements and new superpowers of the augmented reality headset, what about the specs?

Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

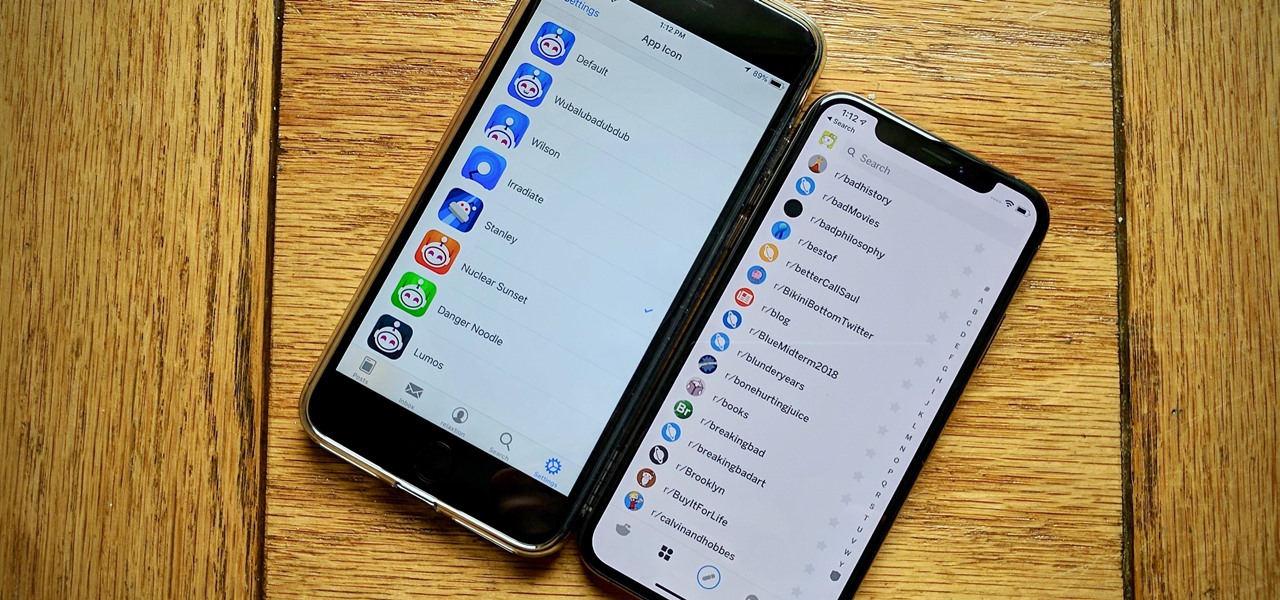
These days, using Reddit on your iPhone is just as good, if not better, than Redditing on a desktop browser. While there's an official Reddit app for iOS, there are plenty of third-party clients that have similar features as well as custom perks to enhance the experience. But figuring out which Reddit client is best for your daily use can be a lot of work — work that we can make easier on you.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

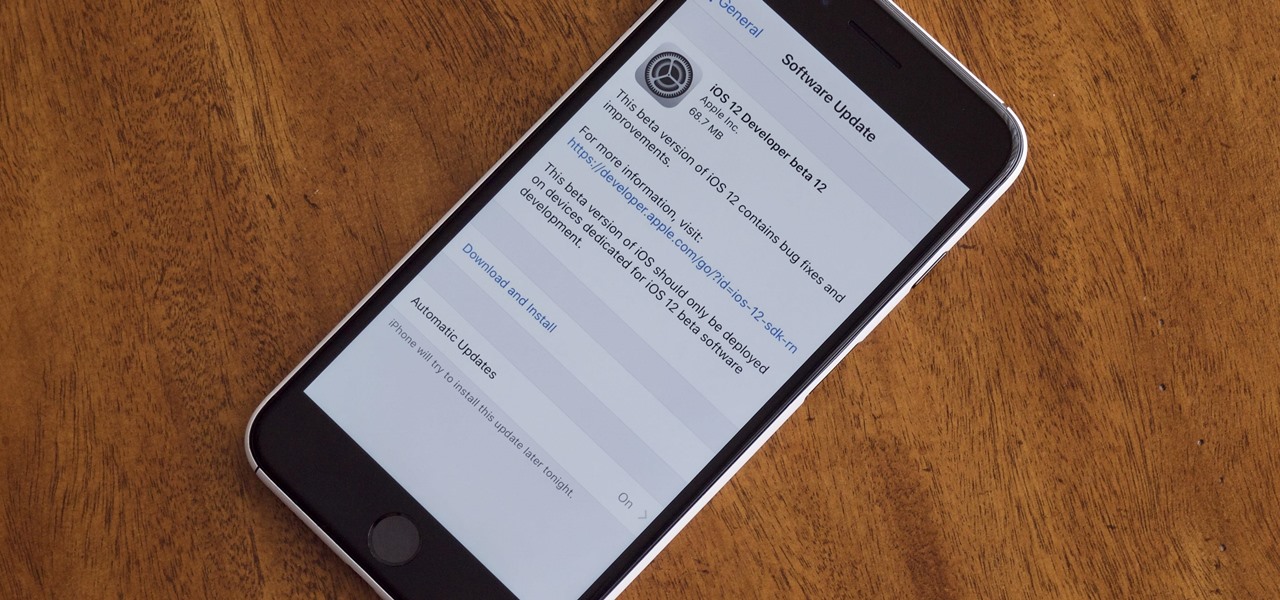
Right before the Labor Day weekend, Apple issued iOS 12 developer beta 12, which comes four days after dev beta 11 and public beta 9, and just one day after announcing the Sept. 12 event. This update primarily fixes a bug where you would be continuously prompted to install a new iOS update even when none existed.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Can't say we didn't see this coming — Apple released iOS 12 public beta 7 on Monday, August 20, the same day it seeded the ninth version of the beta to developers. While the two betas may have different names, public beta 7 and dev beta 9 are virtually identical, so public testers shouldn't feel as though they are missing out.

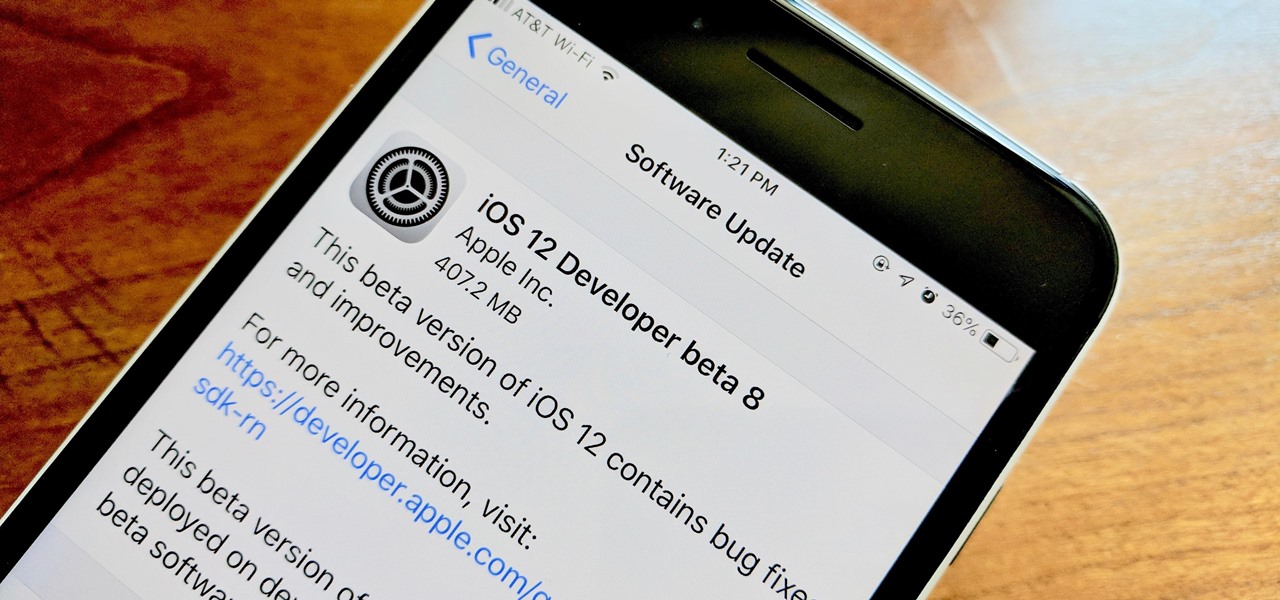
Apple developers, check your iPhones — Apple released the eighth developer beta for iOS 12 on Wednesday, August 15. This update arrives just two days after the release of dev beta 7, which Apple quickly pulled after complaints of unusual performance and stability issues.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Project Fi, Google's MVNO, is running a new promotion on the latest and greatest from LG. From July 16 until the 29th, whenever you order and activate the LG G7 ThinQ or LG V35 ThinQ, you will receive a $300 service credit. When you do the numbers, that equals a minimum of three free months of service.

Not all threats to our privacy come from hackers thousands of miles away. Often, we just want to keep our data safe from those around us, who may snoop in our phones or demand we reveal our secrets. That's where BlackBerry Locker comes in.