One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.
The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

Another entrant — Aryzon — has joined the competition to be crowned as the "Cardboard of AR." The Netherlands-based startup launched their Kickstarter campaign Monday (May 29) and the campaign has already surpassed its funding goal. The company expects to ship units to backers in September.

Everyone feels a little safer with Android's security updates, which are welcome and often necessary protective measures. But what happens when the update that's supposed to safeguard your phone actually ends up wreaking havoc with its security system?

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...
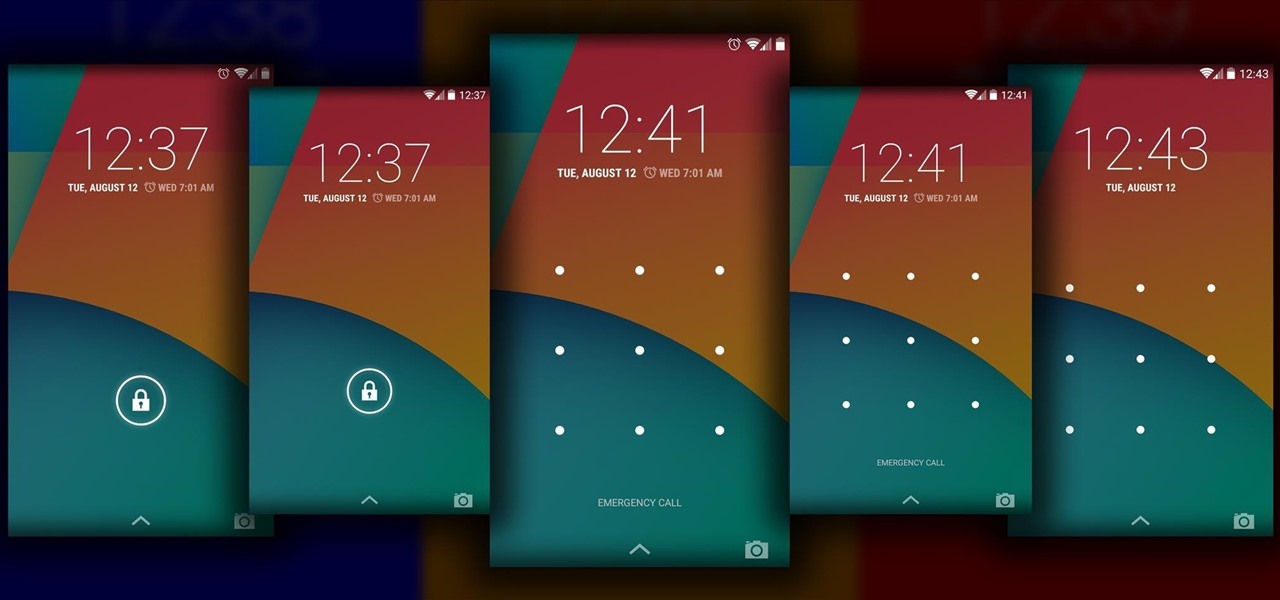
The Android lock screen interface is an integral part of our everyday use. For those of us who use lock screen security, it functions as a barrier between the sensitive data contained within our smartphones and potential outside access. Even if you don't use a pattern or PIN to secure your phone, you still interact with the lock screen every time you go to use it.

Welcome back, my greenhorn hackers!

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on.

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

Got some valuables that need to be protected in your Minecraft world? Watch this video to learn how to build a seriously secure, heavy duty, combination lock. This video will show you what materials to use to make this combination lock.

This is a great, sophisticated hairstyle you can achieve without using any heat (which can often damage your hair). It's an easy and useful secret - just braid your wet hair in the evening, secure in place and then undo it all in the morning!

Deadbolts are a security lock which are usually put on exterior doors. Many saftey experts recommend increasing the strength of your home deadbolt lock. This quick tutorial teaches you how to make your deadbolt extra secure and increase the safety of your house.

Need some help figuring out how to put a password on your wireless router? This home-computing how-to from the folks at CNET TV will teach you everything you'll need to know to do just that. For detailed information, and to get started protecting your own wireless network helpful video guide.

Protect your email account from would-be hackers and crackers with this free video tutorial from the folks at MacMost. If you have a Gmail, HotMail, Yahoo! Mail or other web-based email account, this video is much recommended. For more information, and to secure your own online free email account, watch this helpful guide.

Board Games With Scott presents the boardgame Settlers of Catan. Scott talks about how to play the popular board game and covers some strategy for securing the win.

Learn how to tie a Tack Knot - a secure way of attaching a rope to a fixed object such that it won't come undone even if shaken and flogged. This is a fine knot for camping, climbing, sailing or Boy Scout training.

Learn how to tie an Anchor Hitch (also known as a Bucket Hitch) - A very secure means of attaching a rope to an anchor or any other object that you can't afford to loose (like a bucket down a well, I suppose - thus the alternate name). I actually do use this hitch for temporary anchor attachment (preferring to permanently splice instead) as well as for my bucket lanyards when washing down my boat's deck.

Learn how to tie a Draw or Thief Hitch - a means of securing a rope with two standing ends - one end is load bearing, and the other can be pulled to release the knot. I used this knot extensively for raising the mast on my first trailor-sailor - Tie this above the spreaders, stand the mast up, then pull on the release line to untie it without having to climb aloft. This knot can be used in sailing, boating, general use, camping and bondage.

This video shows you how to tie a Thief Knot. This knot looks a Reef Knot to the casual observer and so can be used to determine if a thief is tampering with your belongings bag - secure it with a Thief Knot, and if you find it re-tied with a Reef Knot, you know someone has been messing with your stuff. This is used in sailing, boating, general use, camping and bondage.

Jared of the TechCentric crew gives you the lowdown on the basics of keeping your VoIP conversations secure and, on the other side of things, how to use the Cain VoIP sniffing application. For detailed instructions on keeping your VoIP conversations private, watch this hacking how-to.

Mike Lively of Northern Kentucky Universtiy demonstrates how to grab a website's resources for reconstruction in Flex using HTTRACK and Wireshark. This tutorial is especially helpful for sites you want to grab that think they are very locked down and secure. All with the free softwares HTTRACK and Wireshark.

Battlestations: Midway for the XBox 360 takes place at the very start of America's involvement in World War II, beginning with Pearl Harbor. Take a look at this instructional video and learn how to win the Battle of Tulagi and secure the strategic islands with these tips from G4TV.

Watch this quick instructional cinematography video that shows how to balance a Canon XL2 professional HD digital camera on a GlideCam 4000 Pro. Learn how to secure the camera using this handheld camcorder stabilizer to prevent unwanted swaying, shoot fluid traveling shots, and produce professional works.

If you can find people who speak English in China, you'll probably get where you want to go faster. Memorize this basic Chinese phrase and feel a lot more secure once you get to China!

This knot is common in the climbing world. We use it to secure two ropes together. Often used to form a loop on a prussik (cordalette) to construct an anchor. Can also be used to connect two ropes to rappel. This knot has many applications in the real world not just climbing.

Materials: Scrap fabric, elastic thread, cardboard, scissors, cellophane tape, and other bits and bobs ie feathers, buttons

Check out this informative video tutorial from Apple on how to organize your Mail in Mac OS X's Mail. See how to sort messages with rules, create smart mailboxes, and comlpletely organize your mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of Mac OS X Mail. See how to set up mail with your email accounts, compose messages, add attachments, view attachments with Quick Look, and search through Mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

Need to secure your track to the road bed for your model railroad? Well, this video tutorial will show you how to do it, not to mention show you how to weather your flex track.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Thanks to its encrypted messaging, WhatsApp can be a platform for secure communication with friends and family. One drawback, however, is that the app would let anyone add you to a group chat, regardless of if you approved it or not. This lack of control over your own account is over, as WhatsApp now lets you decide who can add you to a group chat.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Talk about rapid-fire. Apple released the sixth beta for iOS 11.4 on Thursday, May 17. The update comes just three days after the release of iOS 11.4 beta 5, indicating that Apple is readily approaching the official release of the software. Apple has not issued an official iOS update since 11.3.1, which found its way to users over three weeks ago.

Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.