
How To: Make an ant farm
Why buy an ant farm? It’s simple and fun to make one from a few items you have lying around the house.


Why buy an ant farm? It’s simple and fun to make one from a few items you have lying around the house.

Is your SD memory card getting a little too full? Is it not working? Try reformatting it. It's the first and sometimes last step to troubleshooting card problems. So, if your SD card has become too cluttered, this guide will restore it to a like-new condition with a simple format.

First of all the tutor advises that this is a good idea to do it regularly. It is advisable to drain it out otherwise it shall stop the boiler from working. Before starting your work you have to switch off your boiler. Now allow the water to cool down because it is very hot. First find out the radiator and the drain valve attached to it. Now take a hose pipe which is long enough to drain the water from the radiator to your backyard. Slide the pipe over the inlet and then secure it the link. S...

This video on typhoon preparedness comes from Andersen Air Force Base in Guam, where typhoons are common. The key to surviving a typhoon or other disaster is preparation. Stock up on enough food and supplies to last your family for about a week. Routinely check expiration dates on food, water and batteries and rotate your stock. Be sure window screens are in place and in good condition in the event the power is off for several days.
Wrestling with the whys are wherefores of WiFi? Can't figure out how to secure your network? Take heart: This remarkably thorough, seven-part home networking tutorial will get you up and running faster than you can say `Wireless G.'
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Despite the recent gut punch of staff layoffs, Canada-based smartglasses startup North and its Focals are likely to be in the game for a while longer.

As much funding as Magic Leap has secured, another round of funding will still catch headlines. However, the latest funding solidifies the company's strategy for succeeding in the consumer segment of AR.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.
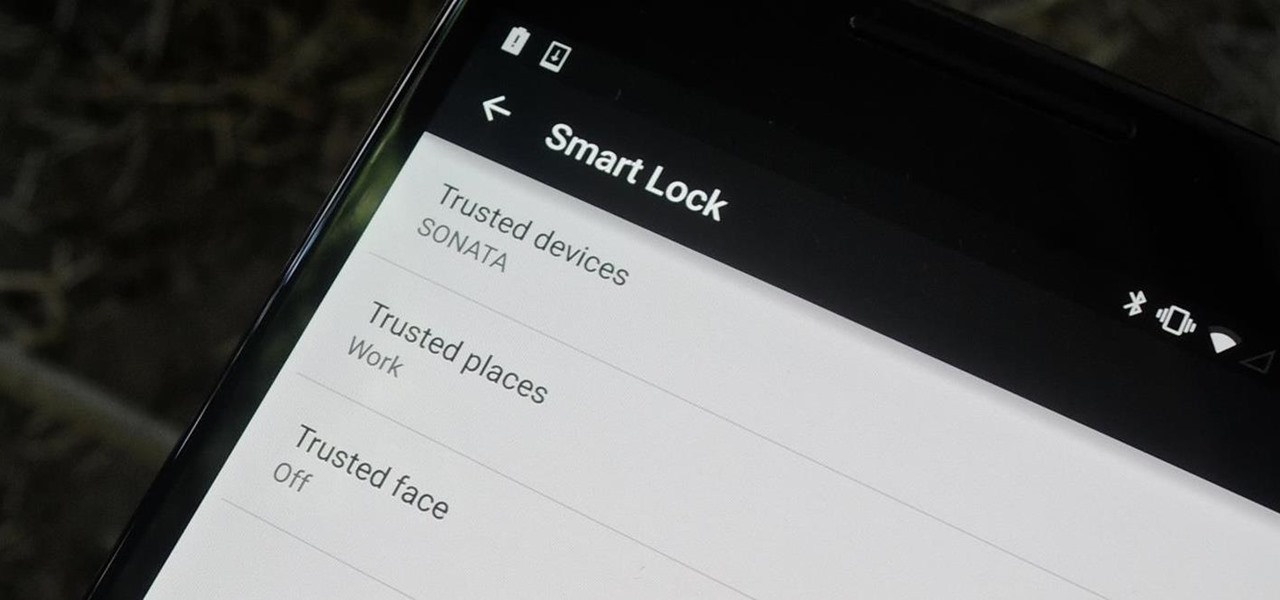
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

One thing that's always important to have in your home office is a bulletin board, because they let you quickly display papers that you need to see every day, such as schedules, notes and memos.

You may wish to block websites from being accessed on your computer for any number of reasons. Maybe you're a concerned parent who wants their kids to browse the internet safely. Maybe you're an employer who wants to secure office computers or blacklist innapropriate websites.
In this video, you'll learn how to use military patrols to repel invaders, make secure entrances to your fortress, and create bins in Dwarf Fortress.

The padlocks that secure most of America's high-school lockers are one of the easiest types of locks to open in the world for thieves and other miscreants. The easiest, cheapest way to do so is using a shim. These can be bought online, but why both when you can make one yourself out of an old soda or beer can? This video features a professional lockpicker at a conference explaining exactly how to make your own can shim and use it to open any padlock. You little devil you.

In this video, we learn how to pack a suitcase like a professional concierge. First, you want to tuck in the edge of the case and pack the shoes at the very bottom. After this, tuck shoes or underwear into boots and shoes to help save room. Next, lie the jeans over the luggage and then fold shirts up to where you are rolling them from the bottom up and place them on the pants. Add in any more shirts, then place the waist band and bottom of the pants over the shirts. Use tissue paper on the to...

Eddie shows us how to remove a boat from the water in this video tutorial. First, take down the canvases and wrap them up. Now, put the antennas down and drive the boat to the loading dock. Next you will need a large truck that has a hitch and trailer attached to it, and secure everything so the boat stays on and doesn't come off of the trailer. Take the drain plug out of the boat before you transport it, to make it lighter. Transport the boat to your house, and place bricks over the front so...

Know your knots! With this free video tutorial, you'll learn how to tie a multiple scaffold knot. The multiple scaffold knot has a couple more loops in it to make it stronger and more secure than the regular scaffold knot. The knot is easy to tie provided, of course, you know how to go about making it. For an easy-to-follow, step-by-step overview of how to tie this useful fisherman's knot in a minute's time or less, watch this free video knot tyer's guide.

In this how to video, you will learn how to open a 6th generation Ipod Classic. First, make sure to turn it off and make sure the hold button is on. Take a prying tool to undo the clips inside the device by sliding it in between the cover and back. Once the clips are undone, place thumb tacks on the sides and tops while popping the base out. Be careful, as there are cables inside that you do not want to break. The orange part is the battery while the blue object is the hard drive. Once you ma...

This video illustrate us how to preform a simple interrupted suture in surgery. Here are the following steps:

This video shows the viewer how to make a UNA box from pieces of hardwood, and 2 pieces of dowel. The box is made by building the normal box from the wood. The lid is then secured using a large piece of dowel so that it can pivot. Additionally to the first large dowel another smaller piece of dowel is secretly added to stop the box opening this has to be removed for it to open so makes it harder for intruders to open. The box can then be sanded, painted and used to hide small objects!
Check out this informative video tutorial from Apple on how to get familiar with a Mac in comparison to a PC. If you're used to working on a PC, this video will show you some of the basic differences between using a PC and a Mac. Once you get to know the fundamentals, you'll find that it doesn't take long to get familiar with the Mac.

Check out this informative video tutorial from Apple on how to stream music wirelessly with AirPort Express and a Mac. If you have a Mac or a PC and iTunes, it's easy to stream music wirelessly. It's called AirTunes. All you need is an AirPort Express and a set of powered speakers, or stereo, or AppleTV, and the room you want to hear music in.

Ever wanted to learn how to make a rekey a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... key making. Just watch this video tutorial to see how to properly make a replacement key for a lock.

Don't know the combination to your lock securing all of your important gym socks? Maybe you just want to impress all of your friends by hacking a combo lock? Whatever the reason, this instructional hacking video will show you how to open a lock with a soda can shim the easy way.

If you're paranoid about the security on your web-browsing activities, fear not. This Firefox add-on, called HTTPS Everywhere, was created by the Electronic Frontier Foundation (EFF) to help you protect you from curious sites. Installing this add-on will make most websites default to the more secure version.

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.

In this video, you'll learn about some great and alternative uses for clear nail polish. Did you know that you can use clear nail polish to stop tarnish or seal an envelope? It's true. You can also use clear nail polish to secure a screen or smooth a wooden hanger. Try these out yourself!

For roasted chicken, you would expect it to have a nice, brown crispy skin. You would expect it to be moist inside with great flavors throughout. By using the rotisserie function (very common in France) on the Cuisinart Brick Oven. Check out the recipe for this delicious herb-roasted chicken from Chef Hubert Keller.