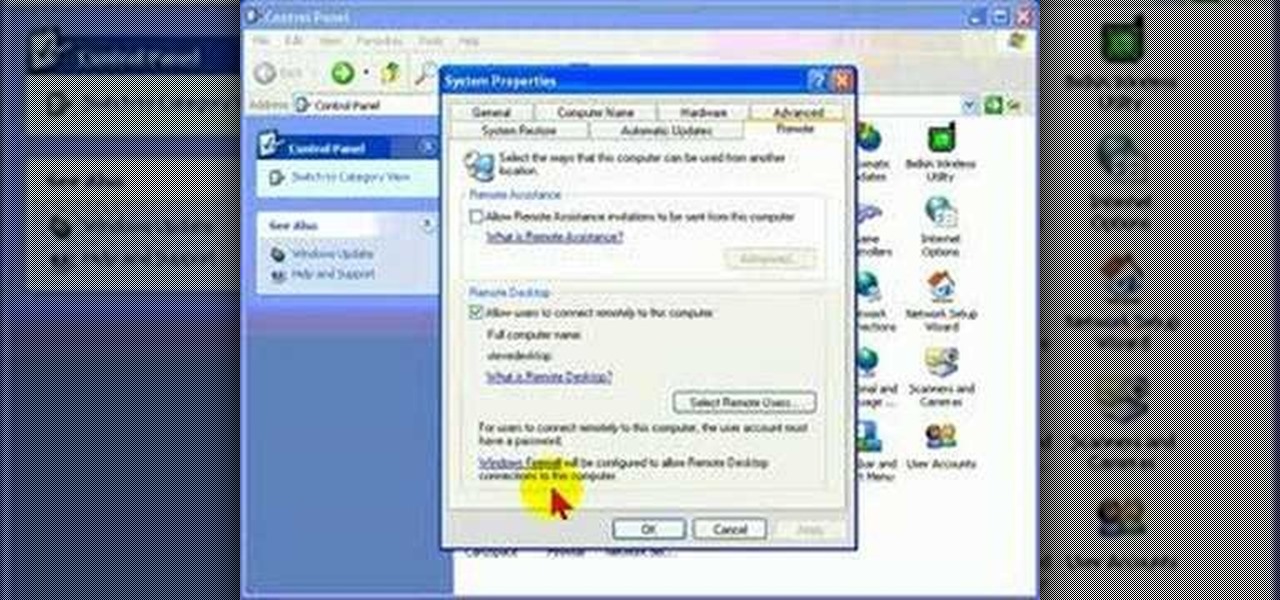
How To: Protect your PC by disabling Remote Desktop
Remote Desktop is a feature of Microsoft Windows, that allows you to access your PC from anywhere in the world, and use it as if you were sat right in front of it.


Remote Desktop is a feature of Microsoft Windows, that allows you to access your PC from anywhere in the world, and use it as if you were sat right in front of it.

Patti, the Garden Girl, host of the national PBS show Farmers Almanac TV shows how to brighten up your home and keep it secure with climbing roses.

The half blood knot with a tuck is similar to the improved clinch knot. The half blood knot with a tuck is a multi purpose fishing knot. The half blood knot with a tuck provides one good method of securing fishing line to hooks, lures, or swivels.

The improved clinch knot (overhand knot variation) is as the other clinch knots a multi purpose fishing knot. The improved clinch knot provides one good method of securing fishing line to hooks, lures, or swivels.

Protecting a new or young tree by staking it enables it to grow the strong root system it needs to secure itself in the ground. We will showyou how to stake a tree.

Materials: Scrap fabric, elastic thread, cardboard, scissors, cellophane tape, and other bits and bobs ie feathers, buttons

There are tons of quick pop up tents available nowadays, but the classic A-Frame tent still remains one of the most popular. A-Frames are those classic tents with the spikes in the ground that hold it up. They take a little more effort to erect but they are perfect for backpacking or short camping trips.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

Need to secure your track to the road bed for your model railroad? Well, this video tutorial will show you how to do it, not to mention show you how to weather your flex track.

Before you go out to protest, understand what you are facing. Sometimes these demonstrations become infected with looters and rioters, which could mean interaction with law enforcement and potentially arrest. And if your phone is on you, it can be used as a tool against you.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.
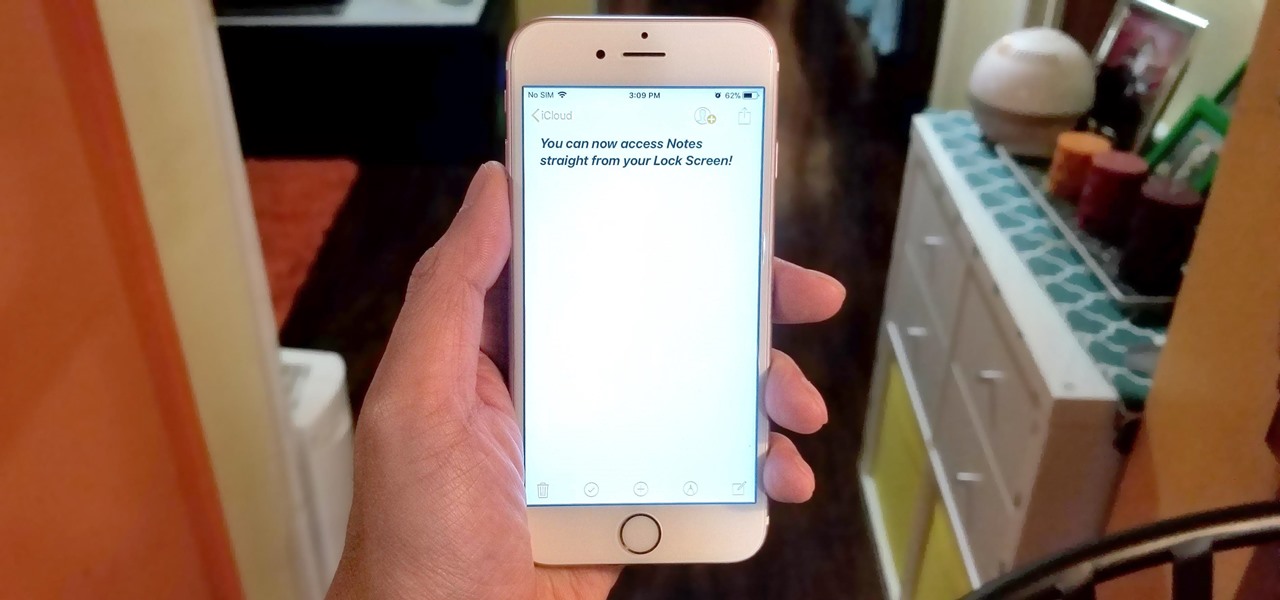
All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.
The Pixel and Pixel XL come with an awesome data-saving feature called Wi-Fi Assistant that automatically connects to open internet hotspots, then creates a secure VPN on your device to keep your data safe.

Take a look at this new and contemporary Prom Bun Hair Style which is super cool and exclusive to adorn. Its over the top style has a unique and sophisticated appearance which appends a ritzy accent to your urbane persona. Try out this style following this simple tutorial. Step 1: Comb Your Hair to Make Them Smooth and Tangle Free. Once Done Gather All Your Hair in a

Mermaid Braid Hair Style Tutorial For Beginners!!!!

We share links on an almost daily basis, usually not even thinking twice about it. Whether you're sending a funny cat video to your sister, or letting your coworker know where to go to download relevant files, there are plenty of reasons you might be giving someone a URL.

Today I would like to share a few data about painting on silk with all the creative readers. The knowledge comes in handy if you want to give a homemade gift or even try to sell a few of your masterpieces.
The Pixel 4 and 4 XL are the first Android phones released in the US to support secure facial recognition. You no longer have to hate on your Apple's friends because you now have "Face ID" as well. So I assume you want to set it up right away — here's how.

Do you have a file (or many files) that, in the wrong hands, may cause you trouble? Don't worry about it, because I'll show you how to wipe it (or them) from your computer in order to leave no trace behind.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.
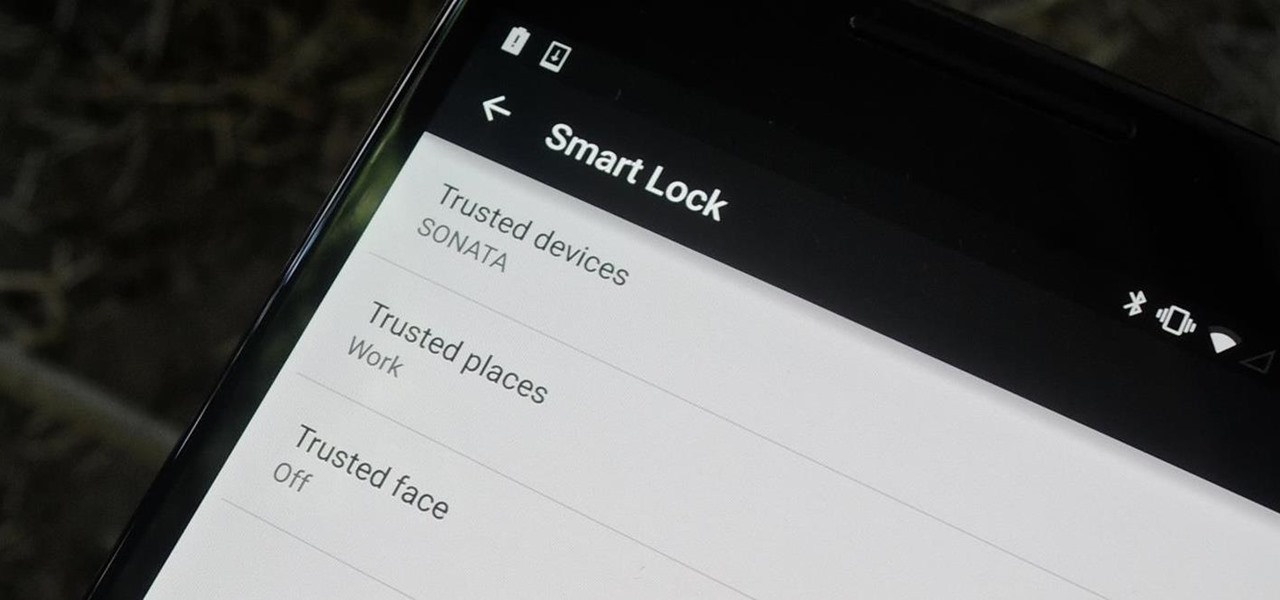
Keeping expensive mobile devices safe and secure is a priority for most of us, but the process of repeatedly unlocking a phone or tablet can seem like a pointless task. This leads to disabling the lock screen altogether, especially when in a safe place (e.g., home, office, car, etc.).

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.
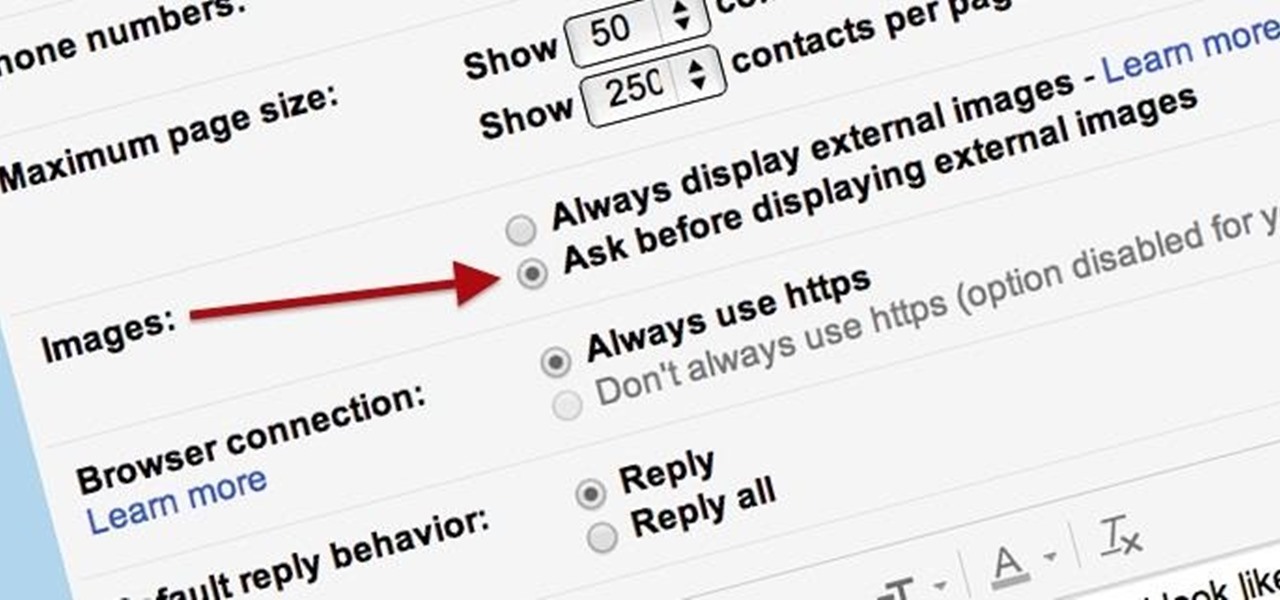
Securing your email address is one of the most important things you can do on the internet. Hackers, spammers, and overly aggressive marketers can turn your Gmail inbox into a heap trash if you're not careful.

One thing that's always important to have in your home office is a bulletin board, because they let you quickly display papers that you need to see every day, such as schedules, notes and memos.

This video demonstrates how to install trailer lights on your boat's trailer. In order to determine what size replacement kit you will need, you must figure out the width of the trailier at the widest point. First, remove the old lights. Use a large slotted screwdriver to remove the cover. Don't forget to wear eye protection. Next, use vice grips and a wrench to remove the exposed stud. Using a wire brush, remove the salt and loose corrossion. Then grease the threads of the studs. You are now...

Why buy an ant farm? It’s simple and fun to make one from a few items you have lying around the house.

If you're paranoid about the security on your web-browsing activities, fear not. This Firefox add-on, called HTTPS Everywhere, was created by the Electronic Frontier Foundation (EFF) to help you protect you from curious sites. Installing this add-on will make most websites default to the more secure version.

In this video, you'll learn about some great and alternative uses for clear nail polish. Did you know that you can use clear nail polish to stop tarnish or seal an envelope? It's true. You can also use clear nail polish to secure a screen or smooth a wooden hanger. Try these out yourself!

Just because you are using Linux, doesn't mean you have to be cut off from file sharing with those using a regular Windows PC. In this tutorial, learn how to share files between Ubuntu and Windows using a Samba local network. Samba is simple to use and can be obtained through your Synaptic package manager.
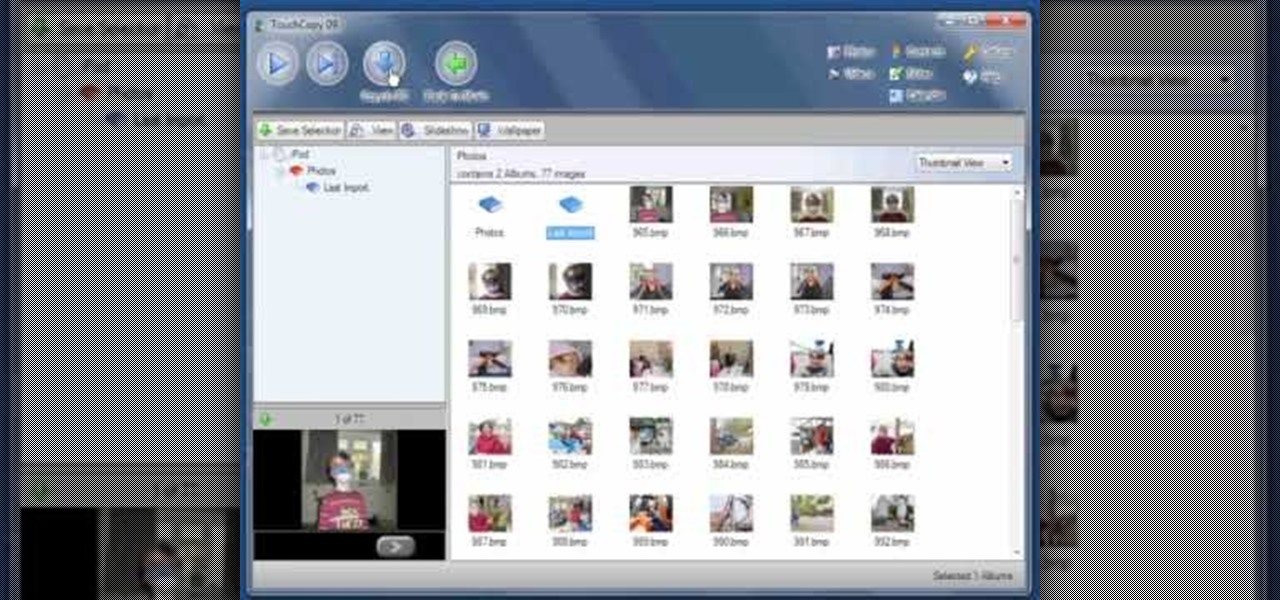
What if your computer just crashed and you've suddenly lost of your personal photos? Those are memories you can never get back in the digital world, unless...

This video is some real basic stuff about boat tying and anchoring. Watch to see the right way to tie and anchor your boat.

The Double Bowline has the same strength as a figure eight knot but is simpler to tie. As the rope wraps around twice, the double bowline knot is more secure than a regular bowline knot. Watch this video knot-tying tutorial and learn how to tie a double bowline knot.

As the clove hitch knot is adjustable and slipper, it can be useful attached to a carabiner, allowing the load to move fluidly up and down the rope. However, the clove hitch is not particularly useful or advisable as a securing knot. Watch this video survival training tutorial and learn how to tie a clove hitch knot on a carabiner.

With this how-to, you'll learn how to mount an SSH server on your Mac as part of the file system. The key is a third-party program called MacFuse, which is available, free of charge, through Google Code. To get started running SSHFS, or the secure shell filesystem, on your own Mac, take a look!

While the clove hitch is not a particularly secure knot, it's useful in situations when the knot requires a little bit of give. The steps to tying this knot are demonstrated in this how-to video, and are shown at a fast pace so you can see how quick and easy it is to do. Watch this video knot-tying tutorial and learn how to tie a clove hitch knot quickly.

The Improved Half Blood Knot is basically a half blood knot with a little improvement. To make the knot more secure the end tag is locked in the final step when tying the knot. The Improved Half Blood Knot is a popular knot for attaching hooks, swivels and lures to the the fishing line. Watch this video fishing tutorial and learn how to tie and improved half blood knot on a fishing line.

RC Car Action Magazine Editor Matt Higgins explains how to modify your antenna cap for better wire protection. Make sure that antenna cap doesn't go flying off. Watch this video tutorial and learn how to secure the antenna cap on an RC vehicle.

In this roofing video Bob Schmidt shows you how to use the foam padding from a sofa cushion to say secure and not fall while doing roof repairs.