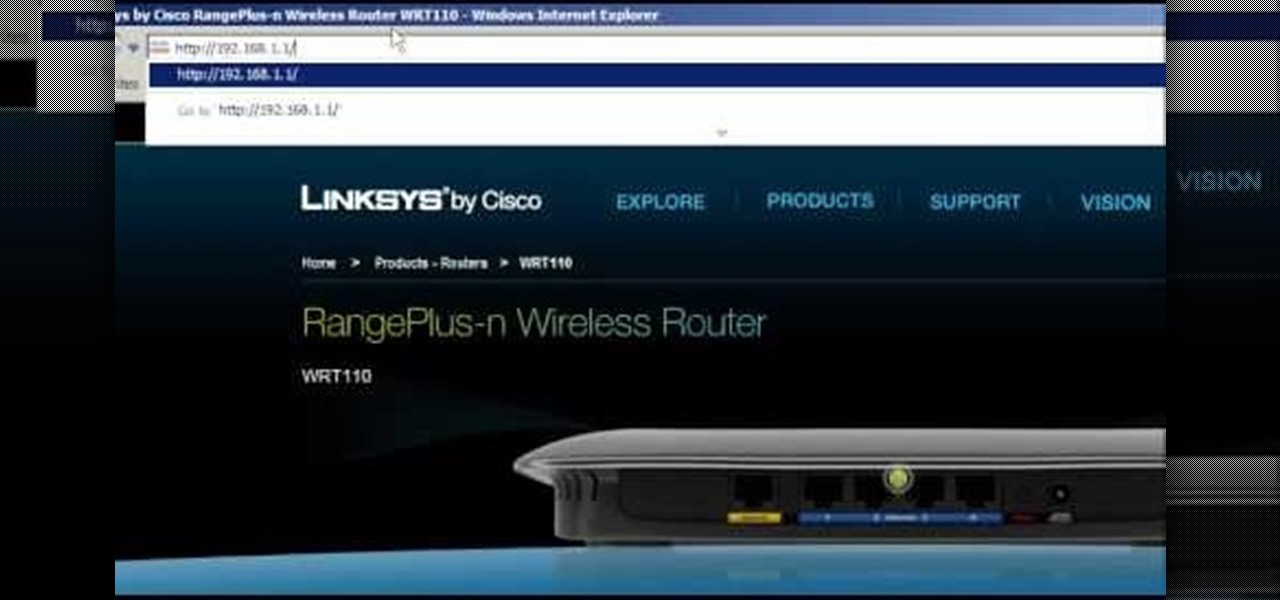
How To: Secure the WRT54G and a default password list
This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.


This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.

Check out this video to learn what kinds of tools to use to secure your furniture during an earthquake. You may want to use straps and stud finders.

Ori Livney shows you how to secure your newly inflated balloon with a simple knot at the tip.

Are you a Gmail user? Listen up, cause here's a snazzy tip from Tekzilla to help protect your emails.

Install acoustical wall panels using adhesive to secure the panel to the wall.

Check out this video to learn how to install acoustical wall panels using pins to secure the panel to the wall.

Check out this video to learn how to install acoustical wall panels using impale clips to secure the panels to the wall.

Motorcycle expert Chris Kelly is here to show you how to transport a motorcycle. As long as your bike fits, the vehicle won't matter but pay attention to how to tie down and secure the bike.

First of all the tutor advises that this is a good idea to do it regularly. It is advisable to drain it out otherwise it shall stop the boiler from working. Before starting your work you have to switch off your boiler. Now allow the water to cool down because it is very hot. First find out the radiator and the drain valve attached to it. Now take a hose pipe which is long enough to drain the water from the radiator to your backyard. Slide the pipe over the inlet and then secure it the link. S...

This video on typhoon preparedness comes from Andersen Air Force Base in Guam, where typhoons are common. The key to surviving a typhoon or other disaster is preparation. Stock up on enough food and supplies to last your family for about a week. Routinely check expiration dates on food, water and batteries and rotate your stock. Be sure window screens are in place and in good condition in the event the power is off for several days.
Wrestling with the whys are wherefores of WiFi? Can't figure out how to secure your network? Take heart: This remarkably thorough, seven-part home networking tutorial will get you up and running faster than you can say `Wireless G.'
How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.
This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.
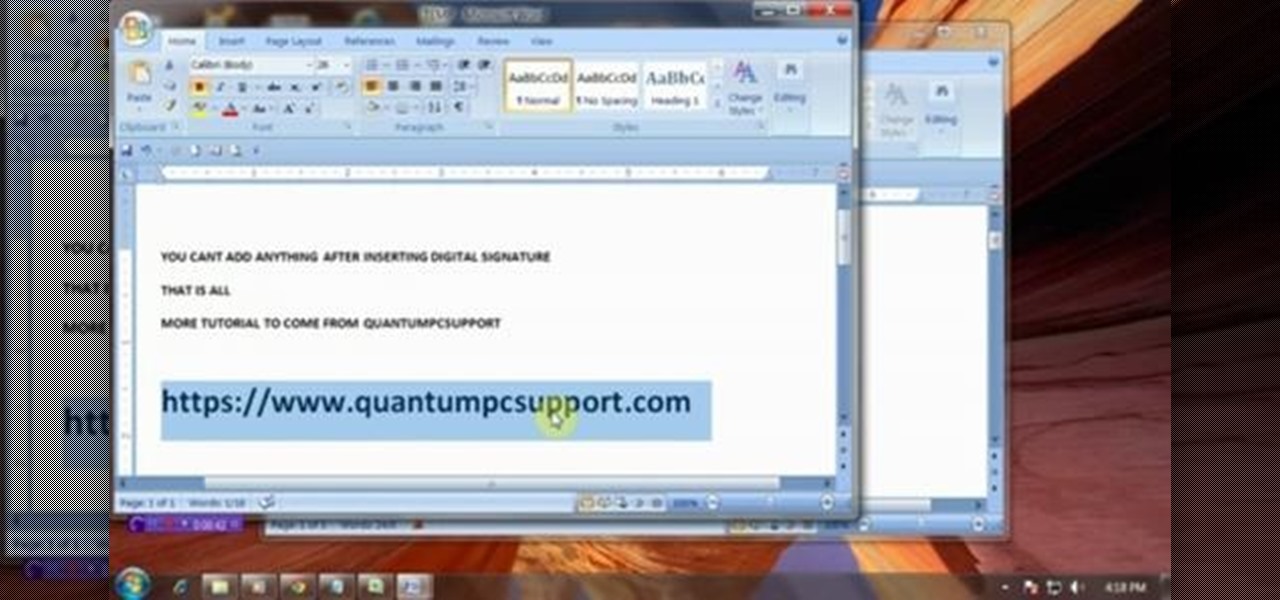
This video will guide you how to make digital signature in MS Word. The digital signature will allow to secure your document from tampering. When you set digital signature in your word text then you can't insert anything in the document anymore. You could add your image of signature with text.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.
If you want to protect your word doc from other, you can give it a password. When anybody wants to open, it will ask a password. This way your valuable document will be secured from unauthorized access.

Make sure your private documents are completely secure. This episode by Tinkernut deals with not only encrypting your files, but also hiding them in a hidden volume.

Stay secure on public wireless networks by making your own FREE virtual private network (VPN). This tutorial shows you how to set up an OpenVPN server and connect to it from your laptop.

You may wish to block websites from being accessed on your computer for any number of reasons. Maybe you're a concerned parent who wants their kids to browse the internet safely. Maybe you're an employer who wants to secure office computers or blacklist innapropriate websites.
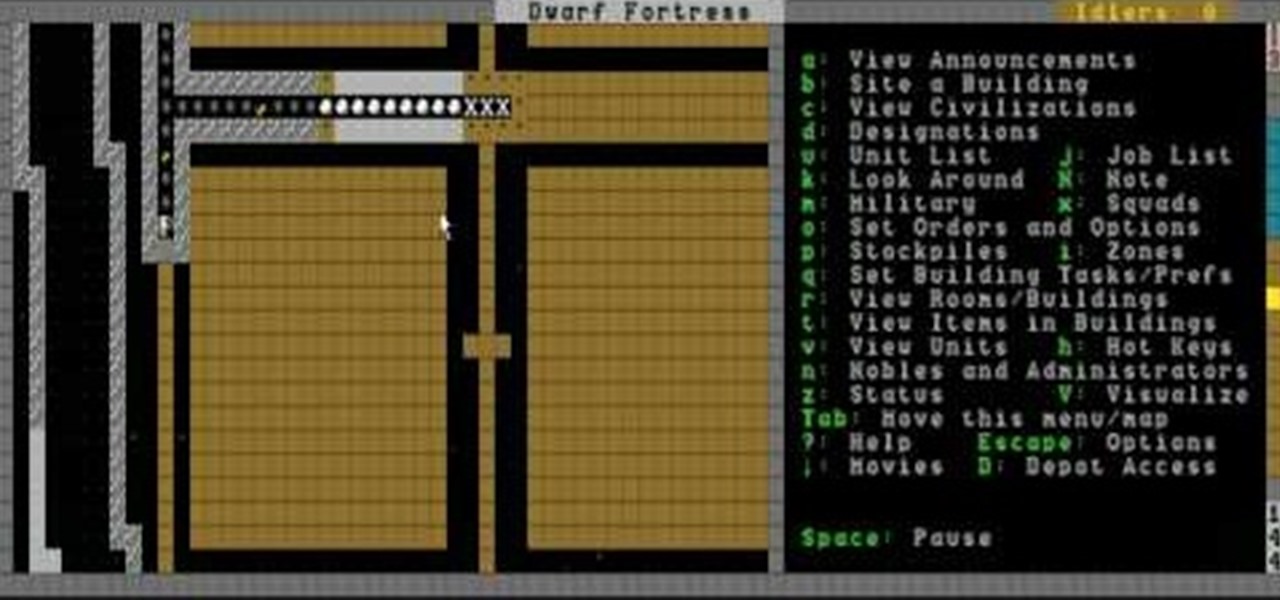
In this video, you'll learn how to use military patrols to repel invaders, make secure entrances to your fortress, and create bins in Dwarf Fortress.

The padlocks that secure most of America's high-school lockers are one of the easiest types of locks to open in the world for thieves and other miscreants. The easiest, cheapest way to do so is using a shim. These can be bought online, but why both when you can make one yourself out of an old soda or beer can? This video features a professional lockpicker at a conference explaining exactly how to make your own can shim and use it to open any padlock. You little devil you.

In this video, we learn how to pack a suitcase like a professional concierge. First, you want to tuck in the edge of the case and pack the shoes at the very bottom. After this, tuck shoes or underwear into boots and shoes to help save room. Next, lie the jeans over the luggage and then fold shirts up to where you are rolling them from the bottom up and place them on the pants. Add in any more shirts, then place the waist band and bottom of the pants over the shirts. Use tissue paper on the to...

Eddie shows us how to remove a boat from the water in this video tutorial. First, take down the canvases and wrap them up. Now, put the antennas down and drive the boat to the loading dock. Next you will need a large truck that has a hitch and trailer attached to it, and secure everything so the boat stays on and doesn't come off of the trailer. Take the drain plug out of the boat before you transport it, to make it lighter. Transport the boat to your house, and place bricks over the front so...

Know your knots! With this free video tutorial, you'll learn how to tie a multiple scaffold knot. The multiple scaffold knot has a couple more loops in it to make it stronger and more secure than the regular scaffold knot. The knot is easy to tie provided, of course, you know how to go about making it. For an easy-to-follow, step-by-step overview of how to tie this useful fisherman's knot in a minute's time or less, watch this free video knot tyer's guide.

In this how to video, you will learn how to open a 6th generation Ipod Classic. First, make sure to turn it off and make sure the hold button is on. Take a prying tool to undo the clips inside the device by sliding it in between the cover and back. Once the clips are undone, place thumb tacks on the sides and tops while popping the base out. Be careful, as there are cables inside that you do not want to break. The orange part is the battery while the blue object is the hard drive. Once you ma...

This video illustrate us how to preform a simple interrupted suture in surgery. Here are the following steps:

This video shows the viewer how to make a UNA box from pieces of hardwood, and 2 pieces of dowel. The box is made by building the normal box from the wood. The lid is then secured using a large piece of dowel so that it can pivot. Additionally to the first large dowel another smaller piece of dowel is secretly added to stop the box opening this has to be removed for it to open so makes it harder for intruders to open. The box can then be sanded, painted and used to hide small objects!
Check out this informative video tutorial from Apple on how to get familiar with a Mac in comparison to a PC. If you're used to working on a PC, this video will show you some of the basic differences between using a PC and a Mac. Once you get to know the fundamentals, you'll find that it doesn't take long to get familiar with the Mac.

Check out this informative video tutorial from Apple on how to stream music wirelessly with AirPort Express and a Mac. If you have a Mac or a PC and iTunes, it's easy to stream music wirelessly. It's called AirTunes. All you need is an AirPort Express and a set of powered speakers, or stereo, or AppleTV, and the room you want to hear music in.
Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.
Check out this informative video tutorial from Apple on how to use the basics of Mac OS X Mail. See how to set up mail with your email accounts, compose messages, add attachments, view attachments with Quick Look, and search through Mail. Mac OS X. It's what makes a Mac a Mac.

Ever wanted to learn how to make a rekey a lock? Well, there's no better time than now to start learning the craft of so many locksmiths out there... key making. Just watch this video tutorial to see how to properly make a replacement key for a lock.

Don't know the combination to your lock securing all of your important gym socks? Maybe you just want to impress all of your friends by hacking a combo lock? Whatever the reason, this instructional hacking video will show you how to open a lock with a soda can shim the easy way.

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.

For this hijab style, start with hair completely covered and a large rectangular pashmina scarf. Pull the scarf over the head with one side hanging longer than the other. Pull the scarf tightly over the forehead to the nape of the neck and pin it together at the nape. Take the shorter end of the scarf and tuck it back toward the nape of the neck. Then pull the long end under the chin and up around the head until it is tight. Secure the end with a pin. Earrings can be worn through the scarf as...
When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.
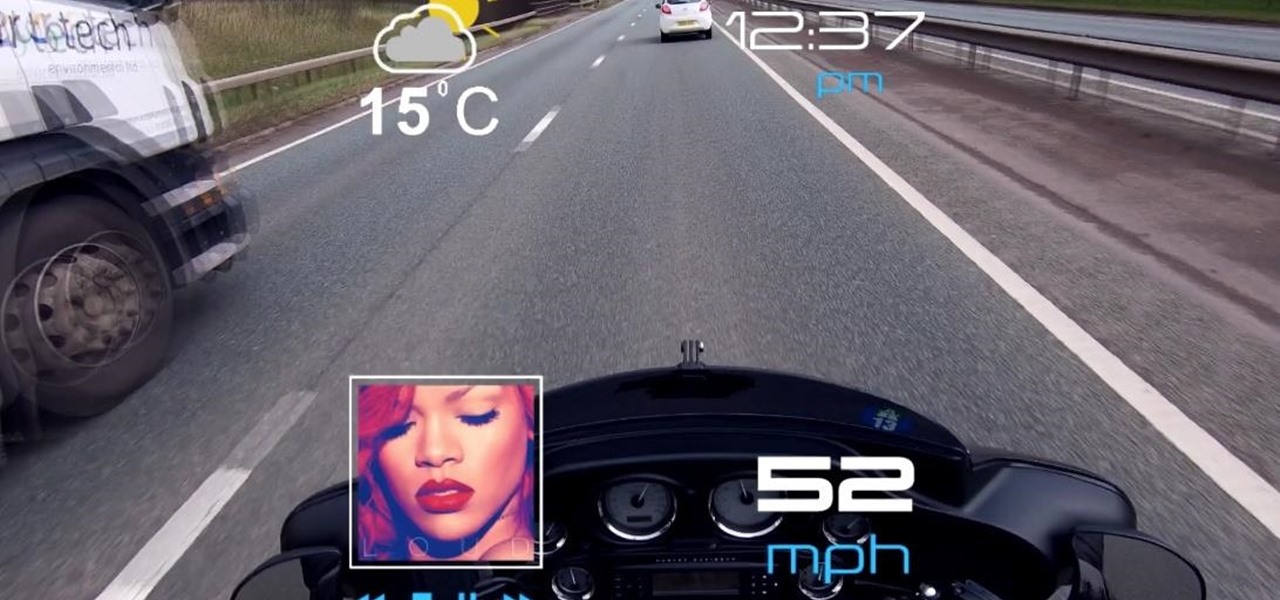
Less than a week after securing a $25 million Series C funding round for automotive HUDs, DigiLens has introduced a new waveguide display for motorcycle helmets that's thinner, lighter, brighter, and manufactured at a lower cost.
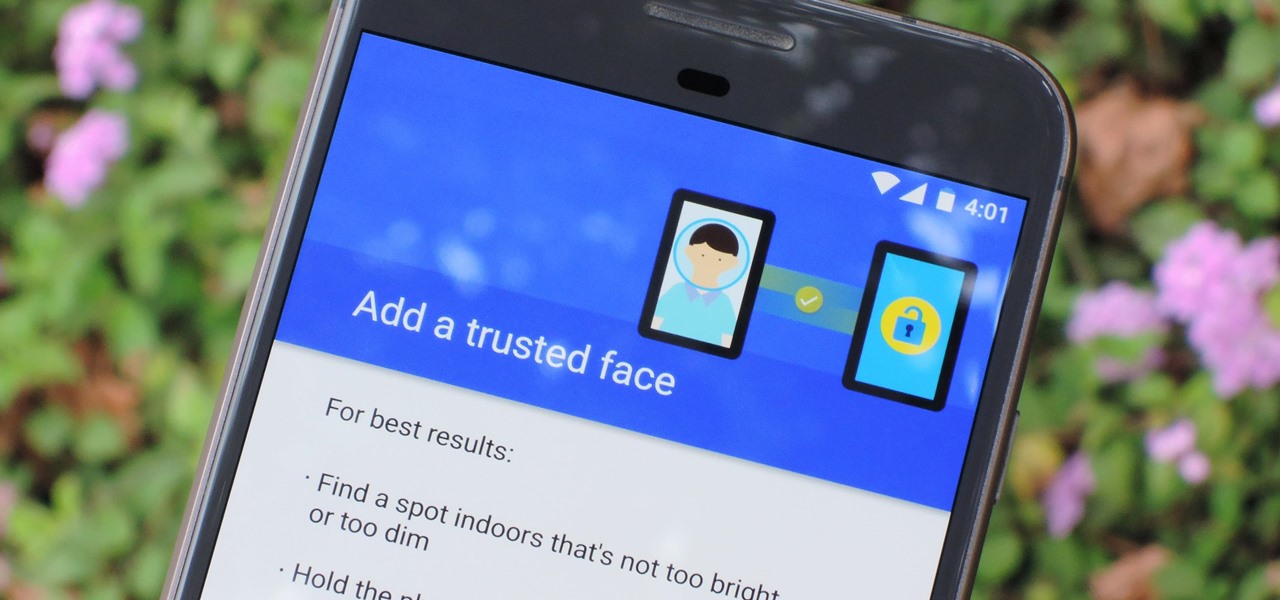
The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?