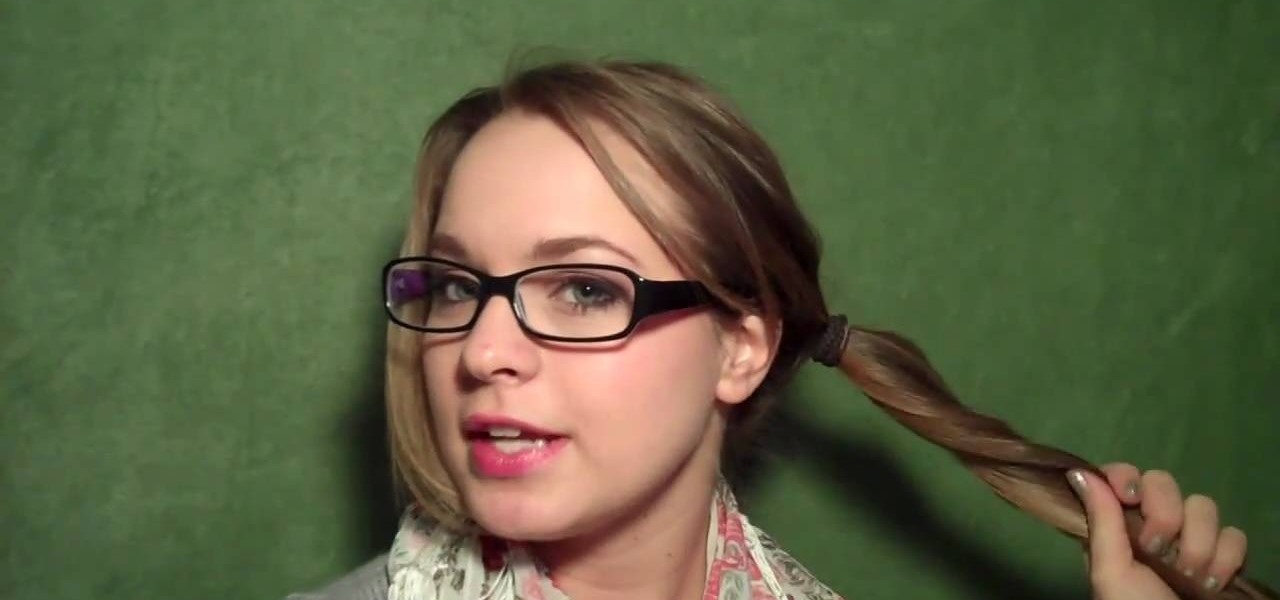The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.
Your data is your most important asset on your computer. Learn how to keep your data safe using Carbonite.com

Learn how to use Avid Interplay Window to access remote assets with working in Avid editing applications. This tutorial covers finding and using remote assets, checking in media, and capturing. Use Avid Interplay Window.

This tutorial shows you how to improve your digital asset management. Once you have recorded your digital audio and video footage, you'll want to import it and edit it as efficiently and quickly as possible. This video shows you the most efficient workflow set up to use.
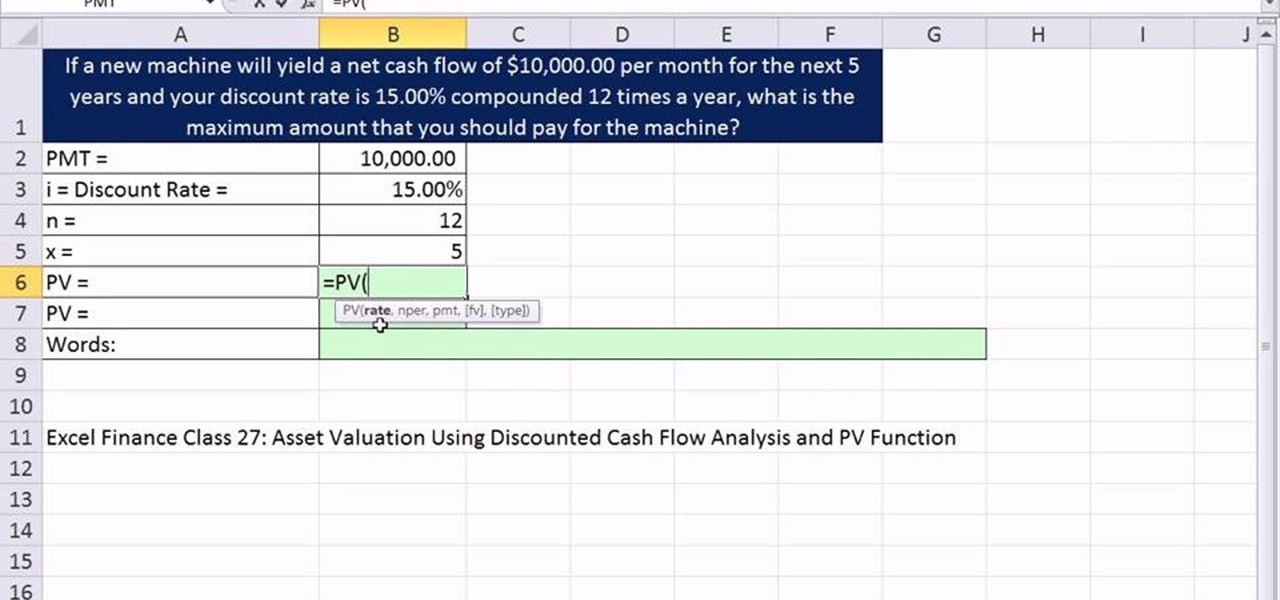
As you might guess, one of the domains in which Microsoft Excel really excels is finance math. Brush up on the stuff for your next or current job with this how-to. In this tutorial from everyone's favorite digital spreadsheet guru, YouTube's ExcelIsFun, the 34th installment in his "Excel Finance Class" series of free video lessons, you'll learn how to calculate the present value of annuity in Excel.

Techno-pop-starlet Ke$ha's hair is one of her greatest assets. It looks great all the time, and is pretty much always this curvy-wavy long style. This video will show you how to do that on yourself with only some simple hair care products.

If you live in a hurricane prone area, it is a good idea to protect your windows with security film. This video will teach you how to install hurricane security window film on your own and protect your home and assets.

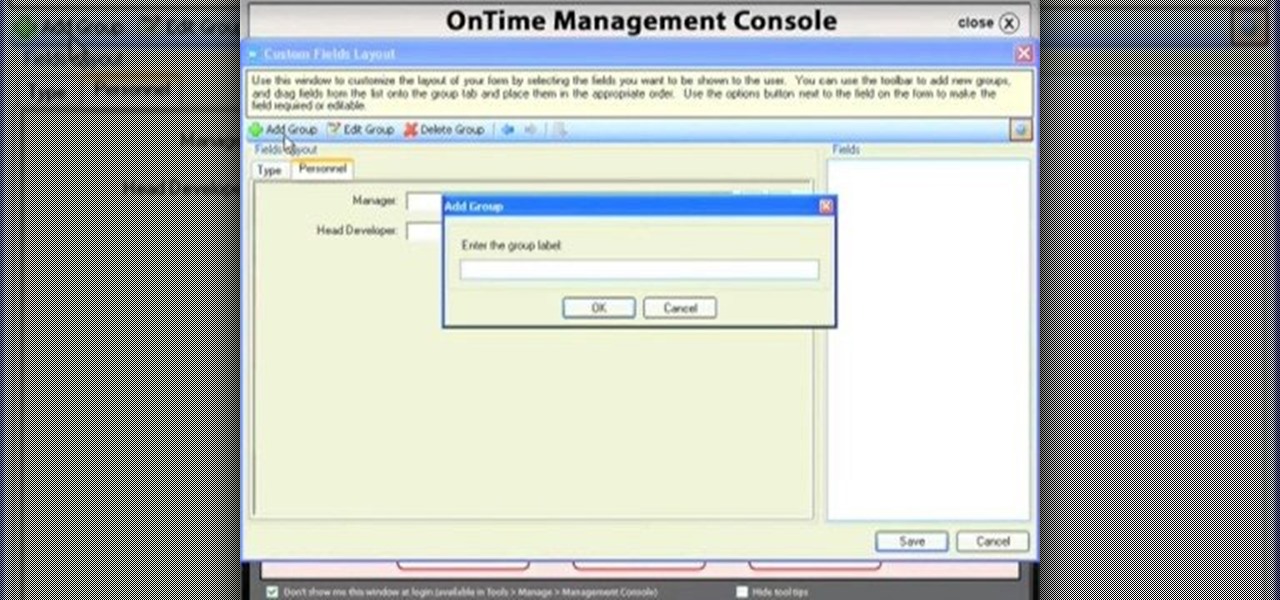
Custom fields are a great asset to OnTime, and there are several different ways that you can use them. This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite covers creating and using custom data inside projects. Take a look.

With Mac OS X, you can have all of your crucial business assets, like photos and logos, ready at your fingertips when creating marketing materials. In this video tutorial, you'll learn how to use the OS X Media Browser to keep important media at the ready. To learn more, watch this video tutorial.

Learn how to breakdown a game level for assets for you maps in Gears of War using the Unreal Engine 3. This example will show you how to create rain.

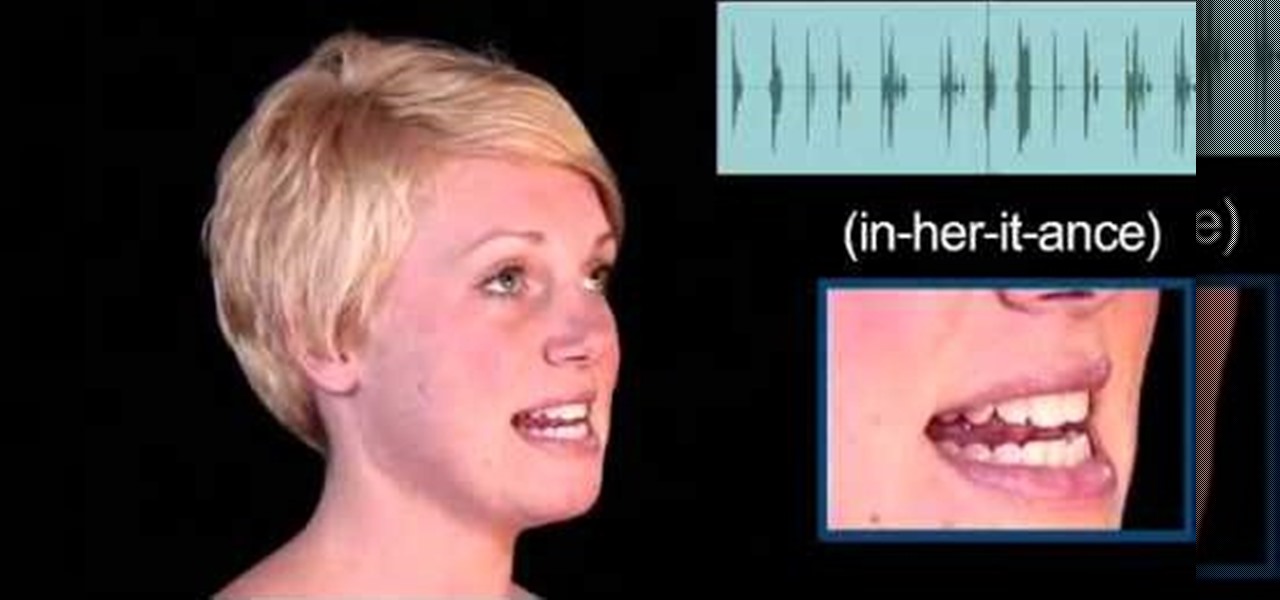
Today's word is "inheritance". This is a noun which means an asset such as money received from someone, often one's parents or relatives, after their death.

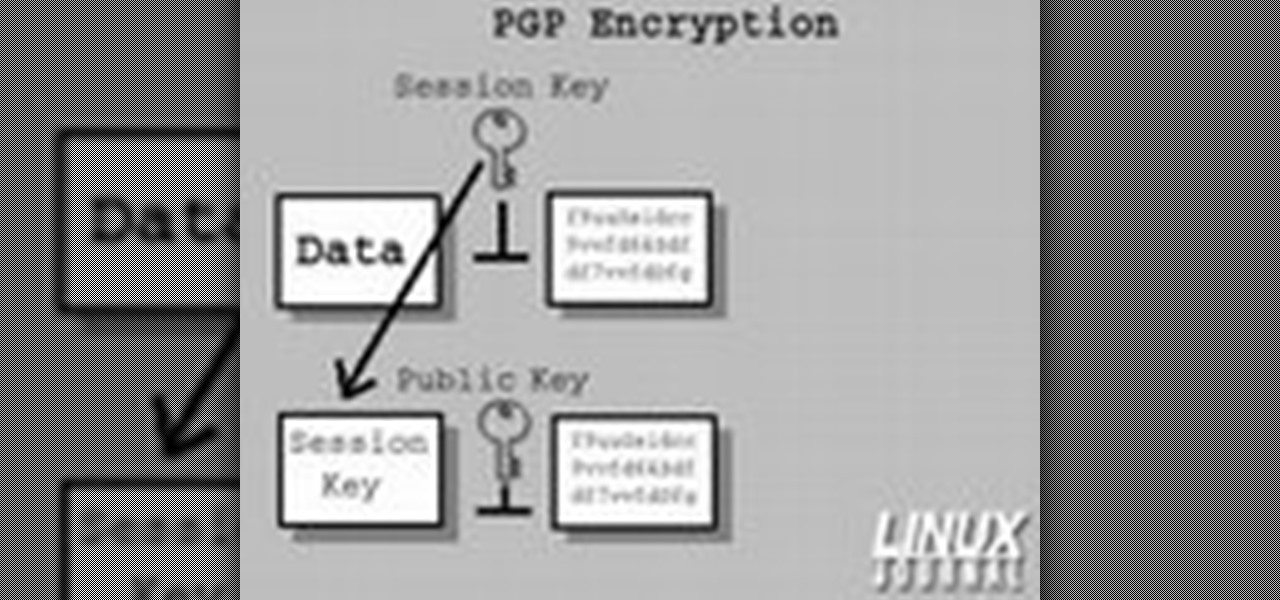
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

While the tech industry is hot in pursuit of mainstream smartglasses for consumers, another early maker of enterprise-focused AR hardware has apparently met its end.

After entering the UK's version of bankruptcy last month, Blippar's assets are up for sale, and bidding ended today.

Despite the hype and potential of immersive computing, the augmented reality industry is showing that it is not invincible, as another AR hardware maker, this time Osterhout Design Group (ODG), is reportedly going out of business.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.

In case you thought the long and unfortunate story of ODG was over, hold on, there's one last chapter to tell.

The last time we heard from Meta, the makers of the Meta 2 augmented reality headset, things looked pretty bleak. Now, as several new facts have come to light, we have confirmation regarding the beleaguered company's fate: Meta is done.

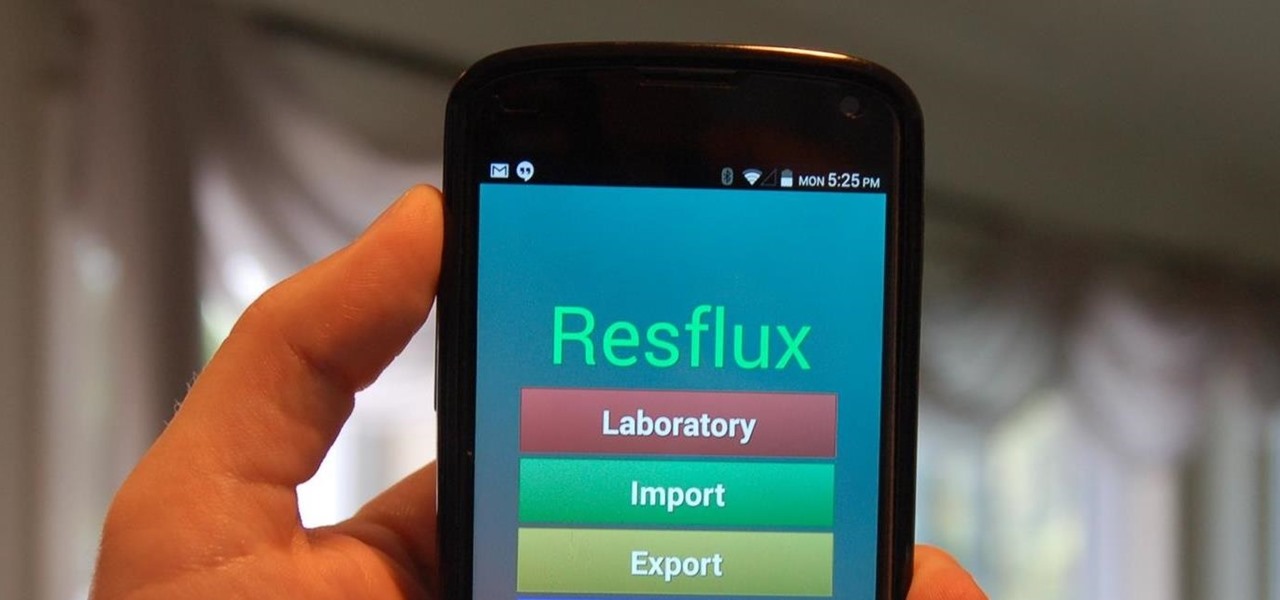
Resflux is an Xposed mod developed by Julian Paolo Dayag, aka WisdomSky, that provides users with a straightforward and functional way to customize and theme almost every aspect of the packages (apps and system components) installed on their Android device.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

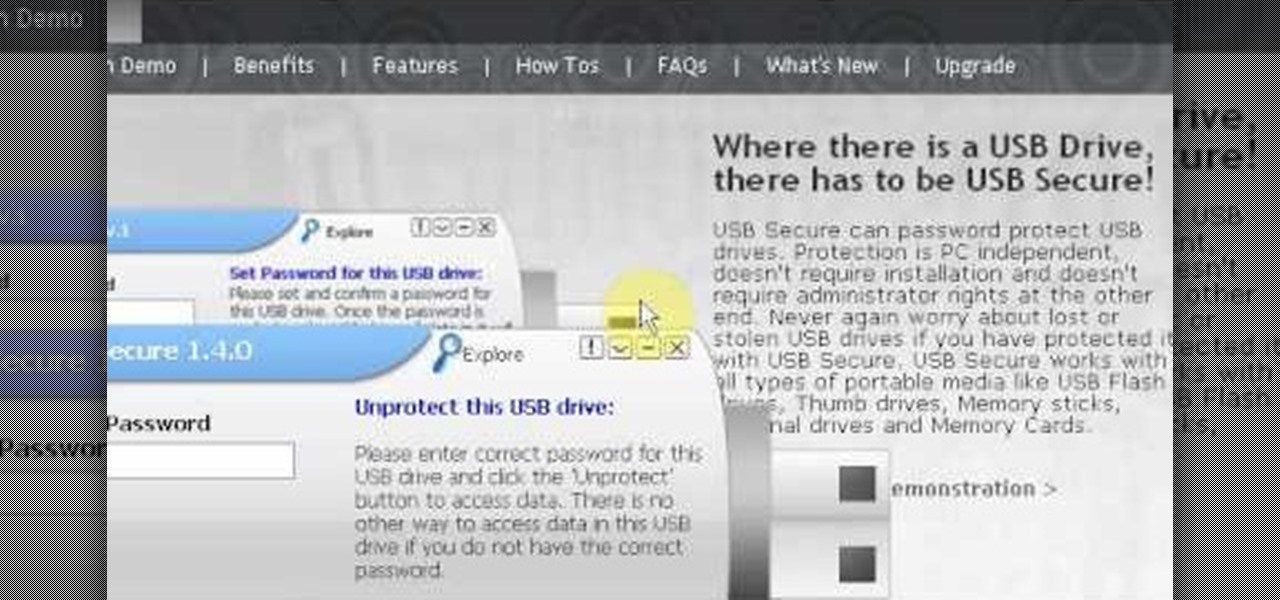
Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

Use three tools to create a simple ponytail. Use a hairbrush, a bobby pin, and a bungee band holder for this look. Using a bungee band instead of a standard ponytail holder eliminates some of the issues typically caused by pulling hair through ponytail holders. Start by using a bristled brush to brush the hair to one location on the head. Secure one hook of the bungee band in the ponytail and wrap the tail around the rest of the hair. Wrap it around again, and secure the other bungee band hoo...

Using ASP.NET Secure Services and Applications Services

Need to know how to tie a Bowline with a few ways of securing it? This way shows you how to secure it with a seizing so that it won't accidentally come undone. Included is a little variation of the bowline with a built-in seizing. If you don't have electrical tape to secure the bowline feed the bitter end back through the hole. It also makes it so you don't have a tail line dangling if you're towing something.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

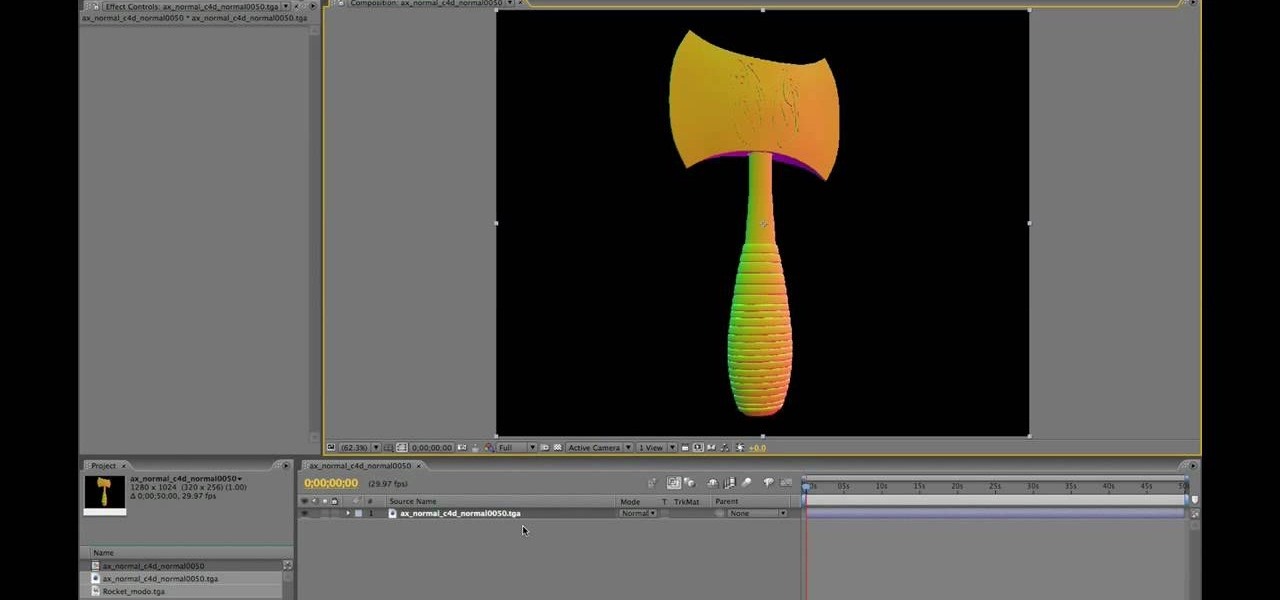
After Effects allows you to do all sorts of amazing things to your videos and images, but it cannot do it all alone. This video will show you how to use an After Effects plugin called Normality 3 to make lighting adjustments to 3D assets on the fly, having already rendered out a normal pass using either Cinema 4D or Modo (you can use other 3D software too, but those two are both shown as examples in the video). It will also demonstrate how to render out the normal passes.

In this clip, you'll learn how to get started using Secure Computing's Secure Web Protection proxy service. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

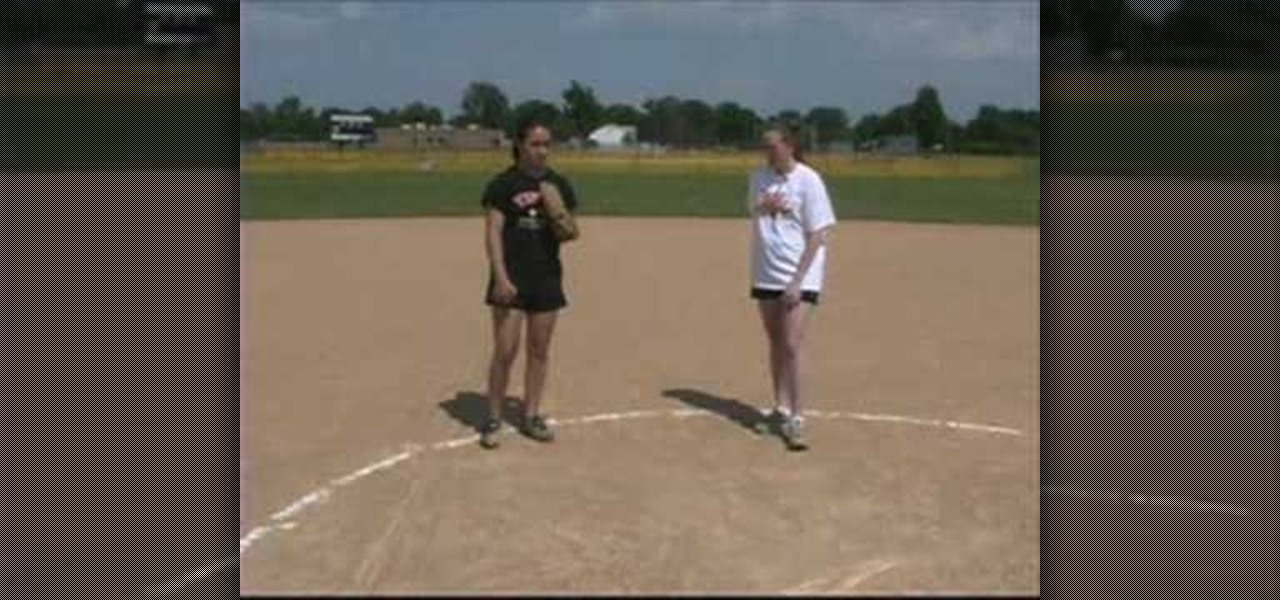
An important part of pitching for softball games should always include properly warming up the legs. Legs are an important asset to doing the fast paced motion in pitching. In this sports how-to video, Farmington (MN) HS assistant softball coach Melissa Langer demonstrates a leg warmup drill for pitchers.

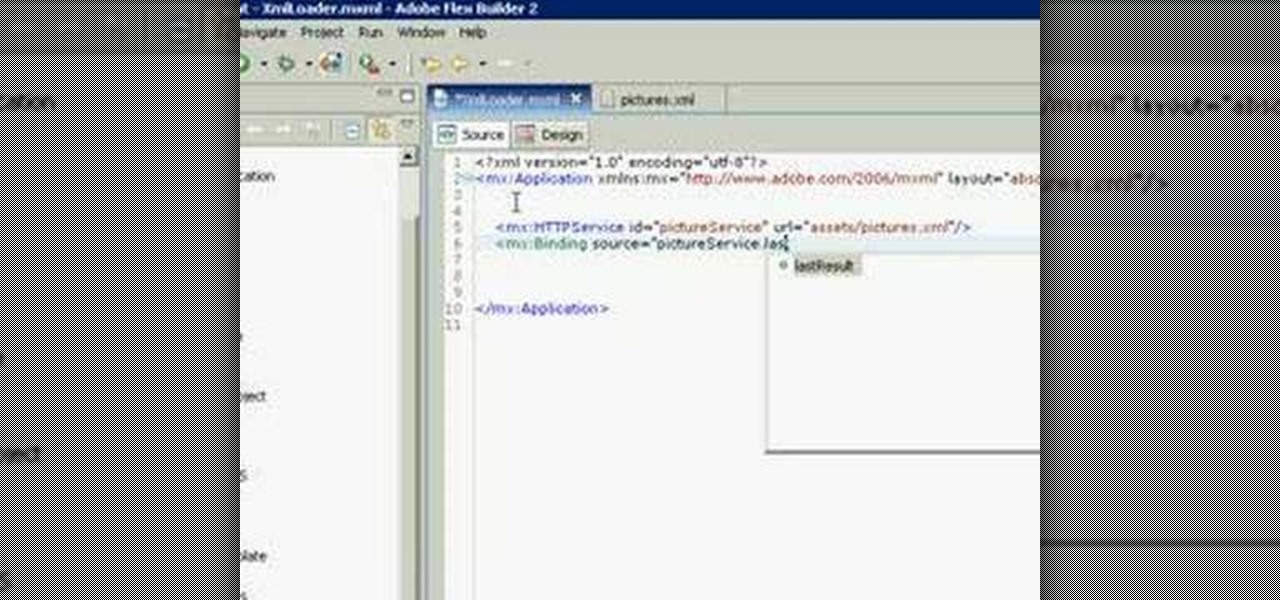
This XML video tutorial will show you how to bind an XML file in MXML in about ten lines. First you'll want to create a Flex project in Adobe Macromedia Flex Builder 2, then create an assets folder and a new XML file in MXML. Coding doesn't get any easier than this. Just watch and learn.

This is a simple approach to everyday makeup that focuses on enhancing your natural beauty, and making those assets you already have look great.

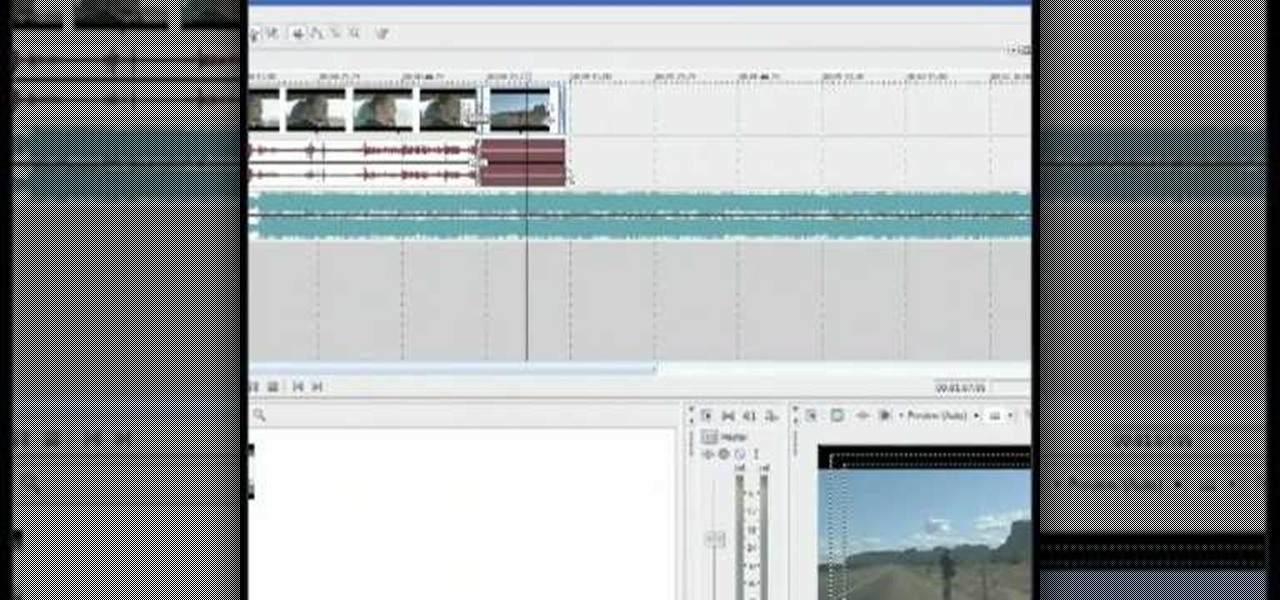
This tutorial shows you how to add an additional track for background music, voice over or any other audio assets when you already have existing audio in Sony Vegas 7.

Augmented and virtual reality motion tracking leader Leap Motion, Inc. announced that it has secured $50 million in Series C funding to fund expansion into new territories and industries.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

Buns and updos are gorgeous hairstyles, with one caveat: If they're not pinned perfectly and securely in place, all your hard work braiding and curling will go to waste as your hair slowly unravels.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!