While Apple and Google have paved the way for developers to create web-based AR experiences through their respective mobile toolkits, an open source option has entered the space.

Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round.

Mobile augmented reality pioneer Blippar has now completed its fall from hopeful AR startup to the immersive computing history books.

In a previous tutorial, we were able to place the Mona Lisa on vertical surfaces such as walls, books, and monitors using ARKit 1.5. By combining the power of Scene Kit and Sprite Kit (Apple's 2D graphics engine), we can play a video on a flat surface in ARKit.

Toyota is testing blockchain and distributed ledger technology (BC/DL) for data sharing for driverless cars and other applications. This could eventually reassure buyers of its upcoming high-end cars by making sure their sensitive data is secure.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

In this video, we learn how to do wrapped pigtails on your American Girl doll. First, separate the hair from side to side. Then, take a small section from the front of the hair and put it aside. After this, you will need to comb the hair back into a ponytail and secure with a rubber band. Secure the other side into a ponytail as well, but put all the hair back into it. After this, you will take the front from the other side and wrap it around the ponytail. Clip it into place and then you will...

In this video, we learn how to tie a Palomar knot to secure a fishing line. This knot is pretty easy to tie, it won't take long. First, you will take the fishing line and make it into a loop. After this, insert it through the eye on the hook. Next, bring it back over and then tie an overhand knot, leaving it a little loose when you tie it. You should be able to see the working end hanging down. Now, take the loop and put it over the hook. Now when you tighten it up, you will have the complete...

In this video, we learn how to do the triple nifty knots hairstyle on your AG doll. First, comb the doll's hair back and then take the hair from the crown of the head. Put this into a ponytail and then secure with a rubber band. After this, section the tail off into two parts and twist them individually. Then, bring these around each other and create a bun at the top of the doll's head. Secure this with a rubber band. Do this with two other sections of the hair on the left and the right. When...

In this tutorial we learn how to fix an RV awning that will not retract. If you find yourself in the situation where the awning on your RV just won't retract, then this is the video for you! To secure the awning you will first need to go to the roof of the RV. When you get on top, you will need to look at the awning and see if something is stuck and causing it to stick. Manually secure the awning when you go to the roof so that it will stay in place for when you need it. If this doesn't help,...

In this tutorial, we learn how to install a cold air intake for a 96-04 Mustang. First, you will need to lift up the hood and locate/disconnect all wiring harnesses. Then remove the bolt around the air filter housing and set aside. Separate the intake and the housing, then pull out the air filter housing. Reinstall rubber grommets that may have come out, then disconnect all hoses from the engine. Put the intake and the pieces together, then you will start to place it back into the car the way...

In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

In this video, we learn how to make a box. First, fold the piece of paper into a triangle, then another triangle. Now, unfold the paper and fold all the sides into each other, making a square. After this, fold in the sides once more, making sharp creases on the edges. Now, open up the paper and do this again on the other sides, opening up again when finished. Now, fold the sides of the paper and turn it upside down. Follow the creases that you just made to fold the box up into a secure box. M...

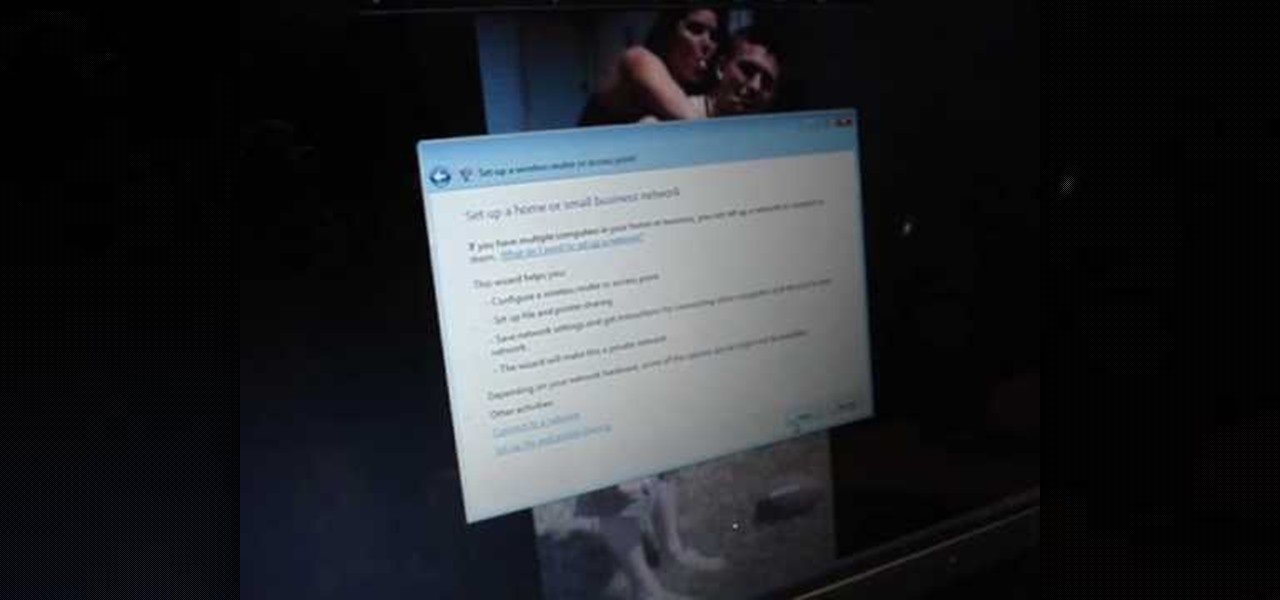
In this tutorial, we learn how to set up and secure a wireless router. First, take your cable and plug it into your modem from your computer. After this, plug in an Ethernet cable into your modem to a wireless router. Now, plug the wireless router and modem into the wall. Now, look for the icon on your computer that says you have connected a new device to it. Go through the set up wizard to make a new wireless network, once it doesn't find one, connect a USB to the computer. Now, click on the...

In this tutorial, we learn how to replace the spark plugs on a 2008 Kawasaki Ninja 250. First look underneath your bike to find out exactly where the spark plugs are at. Next, use wrenches and ratchets to loosen the parts around the spark plugs, then remove the spark plugs completely. After you have pulled them out, replace them with the new one and secure them into place. When finished, replace all the casing around the plugs and make sure you secure them tightly. Add on all bolts when you a...

In this tutorial, we learn how to make a floating illusion style necklace. You will need: beading wire, crimping pliers, wire cutters, beads (your choice), crimp beads, crimp covers (3mm), and a clasp (barrel clasp). First, cut your beading wire to the length you want your necklace, add 3-4 extra inches. Next, space your beads out on a beading board evenly, 1 1/2" apart. Now string a crimp bead onto your wire and take the end of the wire and string it through the crimp bead on the opposite si...

In this video, we learn how to properly pack glass for moving. Make sure you have a table or work area that has a furniture pad on it. Now, place packing paper onto the bottom of a box carton for glasses and china. Glass should be on the top of the box while plates should be placed at the bottom. Put the glasses into a rolled piece of paper until secured, then place upside down into the box. When finished, add crushed paper to the top of the first layer to avoid any glass from breaking. Make ...

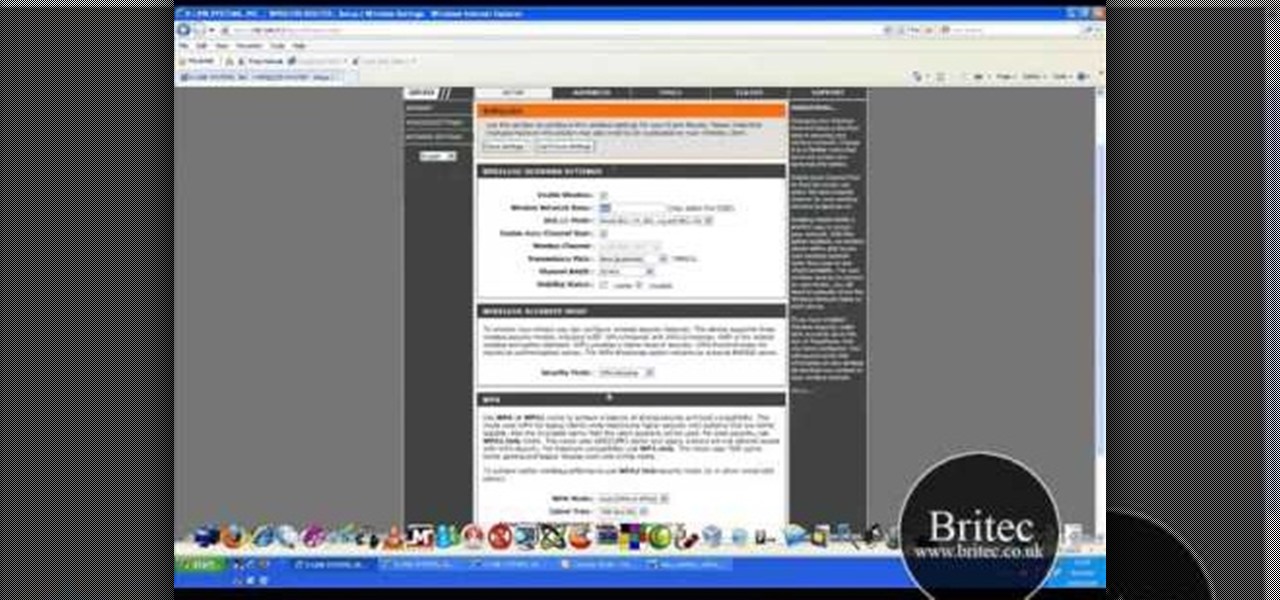
This video shows how to secure a wirelees internet connection on your Zyxel P-660hw-t1. For this, first click on Start button and open Internet Explorer(or any other browser). On the address bar of the browser, type in the IP address of your router. On the next page, enter your password and on the next page, either change the password or ignore. On the next webpage, under Advance setup, click on Wireless LAN. On the next page, click on 8021xWPA. Select authentication required and then click a...

Abigail Goss demonstrates a traditional Apostolic hairstyle, the vertical roll with pin curls. She starts by creating a poof, back combing the roots from the crown to the forehead. Then she creates a section of hair above the ears. She rolls this hair several times in one direction and then puts all of the hair into a ponytail at the base of the neck. At this point the style looks like a french twist with a ponytail at the bottom. She then coats the hair with gel. To make the curls, she takes...

This video illustrate us how to make a piano bracelet on a loom. Here are the following steps: Step 1: First of all secure the piano tabs to the loom and criss cross the string on the tabs.

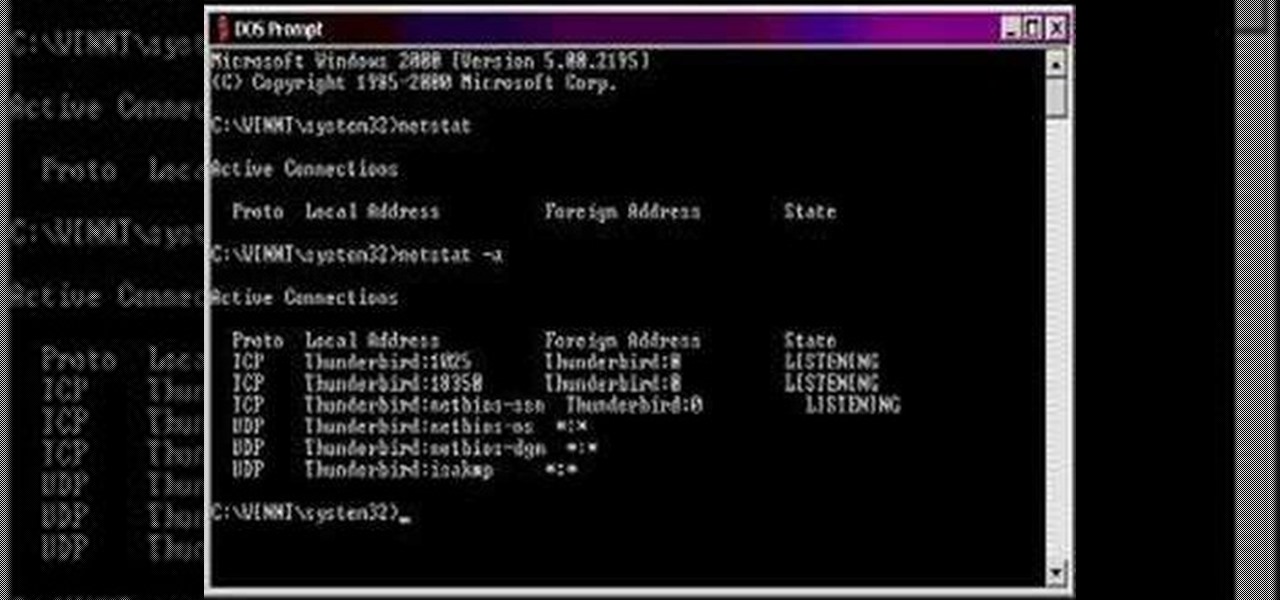
In this how to video, you will learn how to keep your Windows operating system secure by look for and closing open ports. First, you will need to run the program called Net State. Once this is open, type in netstat -a. This will list main connections. Next, type in netstat -an. This will give you the numbers of ports that are open. Some may be used for file sharing and anti-virus programs. If you want it completely secured, you should only have one running. This video shows you how easy it is...

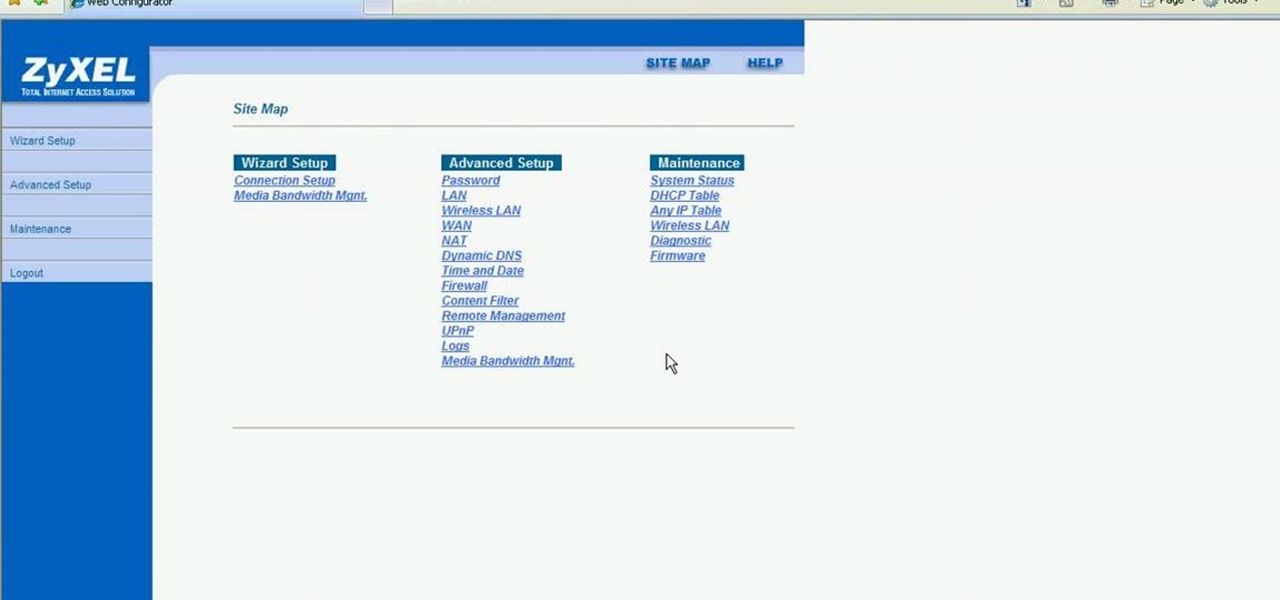
Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

How to build a high tunnel to protect your plants

This is a video using Swarovski Crystals to make jewelry. This video shows how to make one with a gold bow. You need a pendant with 2 hoops (in this case it is a gold bow), a pendant holder, a crystal, a bill, and pliers. You take the bill and hook the crystal on it. Then you hook the bow on it and secure it using the pliers. You take the pendant holder onto the top of the bow pendant, and press it down to secure it, and you’re finished. You can also make rings, earrings, necklaces, and many ...

This video shows the viewer how to secure crimp beads using both crimping pliers and chain-nose pliers for the purpose of jewelry making. The video uses two millimeter crimp beads, beading wire, and both sets of pliers to demonstrate the technique. To crimp using the crimping pliers, the viewer will utilize both notches of the pliers to crimp the bead onto the wire. In order to crimp using the chain-nose pliers, one must simply flatten the bead onto the wire. Crimping is a good method to secu...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

Do you need to lock the door but don't have the keys? This may happen if you are sharing your keys with someone else, staying at a friend's house, or for a variety of other reasons. Check out this video for a sneaky way to secure that door tight without even sticking a key in the lock.

In this video tutorial you will learn all about using Adobe Bridge. Adobe Bridge is a powerful, easy-to-use media manager for visual people, letting you easily organize, browse, locate, and view creative assets. It provides centralized access to project files, applications, and settings, as well as XMP metadata tagging and searching capabilities. Get started with Adobe Bridge.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Welcome back to this series on making physical objects come to life on HoloLens with Vuforia. Now that we've set up Vuforia and readied our ImageTarget and camera system, we can see our work come to life. Because in the end, is that not one of the main driving forces when developing—that Frankenstein-like sensation of bringing something to life that was not there before?

Because of Android's massive array of supported smartphones that carry vastly different display sizes and resolutions, the operating system uses a value known as DPI to determine the size of icons and visual assets that will best suit a given screen.

Notthecoolmom gives a craft lesson on how to make a diaper wreath for a baby shower. To make the wreath you will need the following materials: a package of 56 size 1 diapers (preferably with a design of some kind), a Styrofoam wreath, a spool of ribbon, and rubber bands (optional). Start by laying your diapers around the wreath to get an idea of spacing. Be careful not to make your wreath too full. You don't have to use all of the diapers it depends on the size of your wreath. To put the diap...

This video shows you how to use an exercise band to do bicep curls, triceps extensions and shoulder raises along with some fun extensions of these basic exercises. When doing the bicep curl with the band it is very important to ensure that the band is firmly secured under your shoe, so that it does not slip forwards and snap. Once the band is secure you must curl the arms up towards the shoulders, keeping your elbows bent and close to your sides. The arms are still working in a negative resis...

Ever had a spoke break on your bike wheel? Don't throw the wheel away! Repairing a spoke only takes a few tools and some patience. You will need, at a minimum: a freewheel tool (used to remove the part of the wheel that engages the bike chain), a wrench, and a screwdriver. First, remove the tire and inner tube from the wheel. Next, remove any parts of the broken spoke that are accessible from the underside of the wheel rim. If the spoke is attached to the side of the wheel where the freewheel...

The Prusik knot is a great versatile outdoor knot, boating knot, or paddling knot, and is used widely throughout each. Mountain climbing is a big user of this knot. You can use this knot to secure a loop to a tight line. Also great for hitching boats.

One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. It's like having a safe built right into your smartphone, and it couldn't be easier to set up.

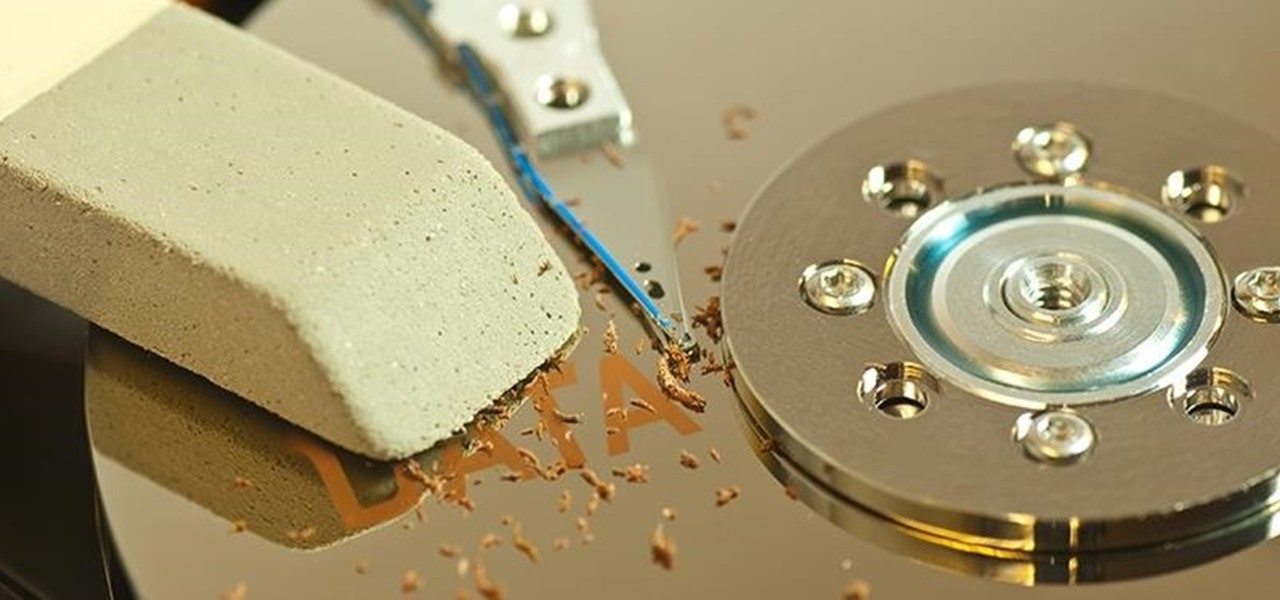
When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

Like its predecessor—and probably every device in the future—the Samsung Galaxy S6 comes with a fingerprint scanner that allows for a more secure lock screen, web sign-ins, and account verification. But unlike its brethren, the sensor on the S6 has been vastly improved. No longer does it require a clumsy swipe—all you have to do is place your finger on it for less than a second, much like Touch ID on iPhones.

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.