
How To: Play Rock-Paper-Scissors
Rock-paper-scissors is a great way to alleviate boredom or make decisions, such as figuring out who gets to go first in the next game you play.


Rock-paper-scissors is a great way to alleviate boredom or make decisions, such as figuring out who gets to go first in the next game you play.
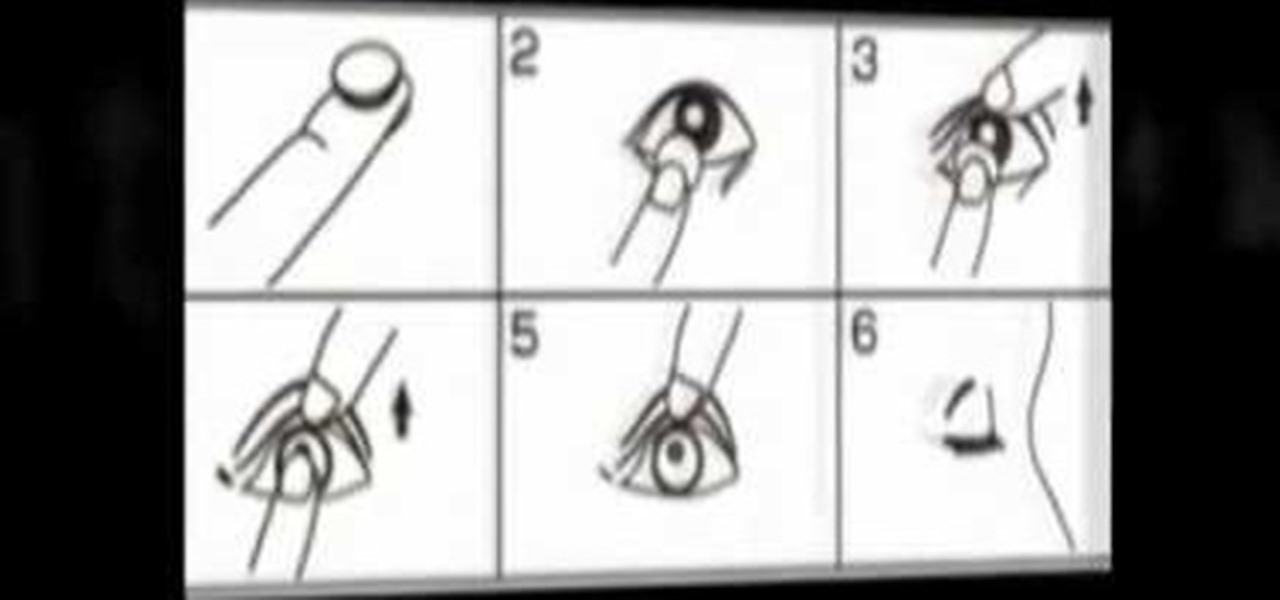
Watch this video tutorial from QQContacts.com to learn how to insert and wear contact lenses in six easy steps.

Learn how to relieve insomnia with acupressure. Get to sleep fast with a massage technique from the ancient Chinese healing art acupressure.

Learn how to relieve a stuffy nose with acupressure. Got a cold? Breathe easier with a move from the ancient Chinese medicinal technique, acupressure.

Learn how to stop a cough with acupressure. The next time you're hacking up a lung, try stopping it with the ancient Chinese healing art acupressure.

Learn how to sew a button by hand. Not wearing your favorite shirt because it’s missing a button? Don’t worry—sewing on a new one is simple and fast.

Learn how to shuffle a deck of cards. Impress your poker buddies by learning how to shuffle and deal like you do it for a living.

The human body contains nine units of blood—but in matters of a traumatic cut or injury, it's always better to be safe than sorry. If you're unsure whether you're in an emergency situation, get to an emergency room and let them decide.

Check out the Pulse Trick illusion from Brian Brushwood and Scam School. As a conversation starter, Brian shows you how to use two toothpicks to detect a pulse.
If you need some sound effects for your upcoming film, you better watch this video! After principle photography in production, you have to get into the editing process in post-porduction, which leads to sound department for ADR, Foley, Sound Effects and Sound Design. If you can't afford a professional sound designer for your movie, you can do it yourself, and this video will help you find sound effects on the Internet for your film.

Check out this instructional legal video sequence that shows you how to file a motion in family court. This video contains important information on preparing and serving a motion in family court. The most common reasons for filing a motion are to request a court order affecting child custody, parenting time, or child support. The court has forms and instructions for the most common problems. Please remember the court is a very formal place with a set of language and rules. This is the video i...

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

In this video tutorial, viewers learn how to do an Ollie on a fingerboard/Tech Deck. Users will only be using two fingers, the middle and index finger. Place the middle finger on the tail and the index finger near the bolts of the board. Now pull the board back, pop the tail down and throw it up forward. Users will need to do this in a fast motion. The fingerboard will almost seem like it is stuck to your 2 fingers. This video will benefit those viewers who enjoy playing with fingerboards and...

Start by putting the loop of the wrap on the thumb of the hand you are going to wrap. Wrap the wrist moving about half way up the forearm. Then run the wrap back down the arm and when you get to the hand wrap between the thumb and the first finger wrapping over the knuckles five times. Then wrap around the thumb and then begin running the wrap in between each of the fingers starting with pinky and ring finger. After you wrap through the ring finger and middle finger then wrap around the wrist...

In this video tutorial Slipperypiggy5 shows an easy way to make a hot air balloon with a rubber band. Take a rubber band put one end on the thumb and the other on the little finger of left hand. With the right hand's finger (index finger) make a twist in the middle and put it on the middle finger of left. Take one part of the loop from the little finger and put it on the thumb and do vice versa. Hold the middle part with right hands index finger and release all loops of thumb and little finge...

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

Welcome back, my hacker novitiates!

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

With the sheer amount of photos, videos, and miscellaneous files we place on our computers, proper organization becomes necessary. Not only so that we can quickly get to a file when it's needed, but also to declutter folders and keep them from looking like random file dumps.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

I have an embarrassing habit: I type with six fingers. Just as your grandma pecks at the keyboard with her two index fingers, I rely solely on my index, middle, and thumb fingers only. But it's not as slow as you think, and I'm not the only one out there that does it.

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

In Obstetrics and Gynecology (OB/GYN), doctors deal specifically with the female reproductive organs, which means a lot of visual inspection of the vaginal area. Whether you're a doctor, surgeon, nurse, or nursing assistant, knowing how to properly drape a patient is detrimental to the patient feeling protected and secure with the hospital staff, along with having some privacy. This video will cover different types of draping techniques.
It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

Use the Excel Vlookup function in Microsoft Excel 2007 to look up data in a table. This tutorial looks up the level and value of a product from a stock list using the Vlookup function in Excel.

This video tutorial is in the Software category which will show you how to create a website in Dreamweaver and Photoshop. Open Dreamweaver and make sure you have the view on table mode. In the table mode, draw layout table and draw layout cells tools are alive. To define a new site, go to file > new folder and give the folder a name. then go to site > new site. On the site definition window that comes up now, give a name to your site and click next. Finally save this page into the ROOT folder...

Yo-yo's are not just for kids anymore. Check out this funky tutorial and learn how to yo-yo like a pro. You can do way more than just pull your yo-yo up and down, with a little practice you will soon be performing tricks and spinning your yo-yo all over the place!

Everyone loves a magic trick, especially when you wow them with a seemingly normal object. In this trick, take a regular coin and make it disappear and move around magically! Soon, you will be the hit of every party!