
In this tutorial, we learn how to change the engine oil in a Chevy truck. To start, you will want to place your car up on a secure jack so you can get underneath it with ease. Next, find the oil can and drain plug underneath the truck and use a wrench to remove the bolts around them. Now, place an oil pan underneath the drain plug and let the oil leak out into this until there is no more left. Next, clean off the bolt that is used for the drain plug and remove the filter from the underneath o...

Paula Dean shows us how to make Filet Mignon for a romantic dinner for two in this video. Marinate your steak meat in the refrigerator using a plain Italian salad dressing. You can use a bottled dressing or make your own, if you prefer. Marinate for about 4 hours, 2 hours on each side.

First of all you need a handkerchief or a cloth napkin. Make sure that it is clean for use. Now start by folding the two opposite corners together. This shall make a triangle. Now you have top fold the two middle bits so that they overlap at the center. Now start rolling them together upwards. It is very important that you are rolling them very tightly. This shall make the body of the mouse solid otherwise it may fall apart. When you have made a solid roll then fold the two ends upwards as sh...

This video by repairs universe shows viewers how to replace the battery in the 2nd Generation iPod Touch. The tools you will need for this project include safe-open pry tools and a small phillips head screwdriver. To begin, remove the screen by releasing several clips that hold it to the frame using the safe-open pry tool. Run the tool between the case and the glass along all edges. Gently pull glass off and pry off the digitizer. Next, remove the small screw in the upper corner, lift up the ...
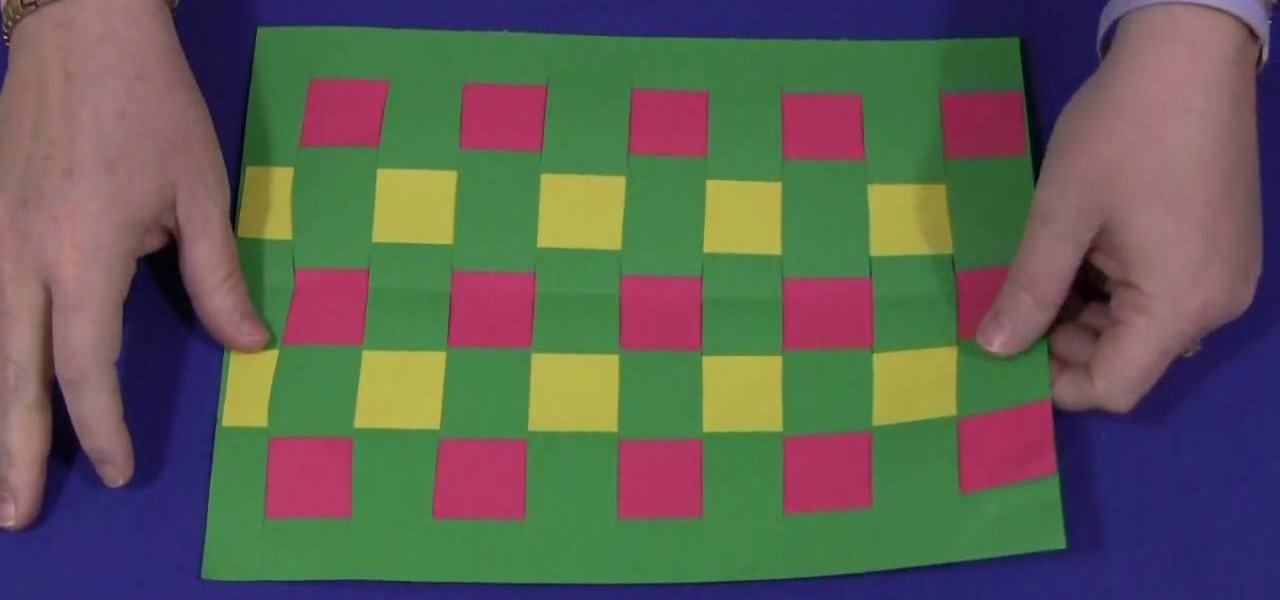
This is a project to keep your kids entertained. It is also a great way to practice hand eye coordination and motor skills. The materials that you are going to need are; construction paper and something to cut the paper with.Depending on the age of the child you can use 3 colors or more for older children and 2 colors for the younger children. Color choice is left up to what the child wants.To get started take a full size sheet of construction paper. Fold this paper in half length-wise. Take ...

The Mac OS's Disc Utility allows for the encryption of files. To open Disc Utility click on the magnifying glass (spot light) up in the top right hand corner, and search for Disc Utility. Click on the first result in the list. Once Disc Utility is open, click on "create a new image" in the top tool bar. A new window will drop down, where you choose what you want to save the new image as. Give it a name, and choose the size you want it to be. Moving down, choose the encryption you want to use ...

This video shows you how to create a continuous, daisy-chain necklace. The materials used include: size 11 rock eyes in yellow, red and purple, a toggle clasp , 9mm thread and a size 10 beading needle. Start by sewing on one half of the clasp, tying a knot to hold it in place. Be sure to leave the tail ends long enough to be able to re-thread it later with a needle to sew the tail ends. The video then shows the precise order in which the various beads are threaded through to produce a chain i...

Cute Girl Hairstyles shows you how to create a French braid hairstyle for your hairstyle. Firstly, divide the long hair into two parts with a zig-zag parting on the top of the head. Keep one half of the hair in a ponytail to keep it out of the way. Wet the hair down, and take a small section of the hair. Section that part into three and repeat. Cross the first piece with the second piece, and then cross the third piece over (braiding). Pick up hair and add it to the left lock and repeat. You ...

The Trilene knot is a multi-purpose knot that can be used in fishing to attach hooks, swivels and lures. This is a great knot because it resists slips and failures.

This video describes how to solder a wire. The first thing you have to remember is that the wires should be cleaned, shiny, and bright. Then trim about 1/2-inch of the insulation of the wires and then make a secure mechanical connection. Next, put some soldering pencil clean and shiny 60/40 rosin core solder. Do not use 50/50 core solder. Start by making sure that the soldering iron is tint. Put the soldering iron underneath the joint. Heat tends to rise and then touch the solder to the joint...

Clean out the empty bottle that you are going to use. You can use a white dish-washing soap bottle or a cleaning agent bottle. Just make sure it is empty and clean. Use the pen to draw a wide rectangle that measures 3 inches long by 1/4 inch wide onto the bottle. The teeth you are making are going to stretch from either side of your canine teeth above and over your two front teeth. This will help them be more secure. Draw this onto a part of the bottle where it is curved. Draw two vampire tee...

See how to make a very tall, simple, yet elegant centerpiece for weddings and other events. You first need a tube and a base that it will fit into. Placing the tube in the base, use a hot glue gun to secure the tube into the base. You can then fill up the balloons with air using an air pump and tie pairs of balloons together. Twisting together four balloons, place the cluster of balloons around the base of the tube. Repeat with an additional 8 balloons and place this cluster at the top of the...

This video shows you how to remove and replace a sink basket. It's real quick and very efficient if you have a new sink and an old basket. Here are the steps on doing this.

Learn how to make a sword out of cardboard with this video. Materials:

This video tutorial shows you how to install a glass vessel sink or countertop. First you need to make sure that the glass vessel sink or countertop has all of the pieces needed and that none of the pieces are scratched or broken. You then need to place the mouthing ring on the countertop where the sink is going to go. Make sure that the rubber side is facing down. Then carefully set the sink on the mouthing ring. You must then take off the tail piece of the pop up drain. Take off the ridge a...

Learn how to polish shoes. You don't have to know how to get them Army-regulation shiny, but you should have some basic training.

Digidesign has transitioned all of their plug-in software copy protection from floppy drive based key disks to copy protection authorizations that reside on the iLok technology provide by PACE. The following is some information about iLok technology.

This instructional pet video shows a good way to introduce your pet rats to water. However, it's important to understand that some pet rats will just not like water. Your success will vary depending on your individual critter(s). Watch this tutorial video to learn the best methods of approach.

Whether you're using your phone's map to navigate or entrusting your passenger with the responsibilities of the mobile DJ, your phone needs a secure place in your car. And if it could charge while it's there, that's great too. The Naztech Smart Grip Wireless Charging Car Mount is exactly what you're looking for if you need a place to keep your phone secure, charging, and able to be used when it's safe to do so. Right now, this adjustable phone mount is on sale for $39.99, an 11% discount.

If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

As much funding as Magic Leap has secured, another round of funding will still catch headlines. However, the latest funding solidifies the company's strategy for succeeding in the consumer segment of AR.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

We know Android 9.0 will have the formal designation of Pie, following Google's age-old tradition of naming their OS after items you'd normally find on a dessert menu. And thanks to a slew of new features that centers around your overall security, P could also stand for Privacy.

When a photo or video is just too sensitive to leave laying around in your Photos app, you'll want to either delete it for good or hide it away in safe, secure location on your iPhone. As for the latter, Apple actually has a few tools available to make photos and videos hidden — even password-protected — on your iPhone.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

BlackBerry's focus on secure software and their new partnership with manufacturer TCL are two of the biggest factors in their recent resurgence. Last year, the company announced two new devices — the KEYone and the BlackBerry Motion. The KEYone has been available for a while, but after months of waiting, BlackBerry announced the Motion will hit US shores in a few days.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.









































