This week in Market Reality, we see two companies capitalizing on technologies that contribute to augmented reality platforms. In addition, industry mainstays Vuzix and DAQRI have business news of their own to report.

The Pixel is now rumored to be the next phone up in line to be getting a curved display. ET News just reported that Google is in talks to invest $875 million (KRW 1 trillion) in LG Display to give their next-generation Pixel 2 smartphone some curves around the edges.

The ride-sharing company Lyft has managed to secure $500 million in funding, which will certainly help its ongoing competition with Uber. According to recent reports, the cab firm is currently valued somewhere between $6.9 billion and $7.5 billion, but this still pales in comparison to Uber's estimated $70 billion valuation.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

No one is safe anymore, it seems. Google's Project Zero has just uncovered how easy it is for attackers to target your phone's Wi-Fi chip, which is essentially a mini processor for Wi-Fi that detects and processes networks.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Starting with version 6.0 Marshmallow, Android now supports fingerprint scanners natively. This change has effectively opened the floodgates, and now almost every flagship Android device includes a fingerprint scanner out of the box.

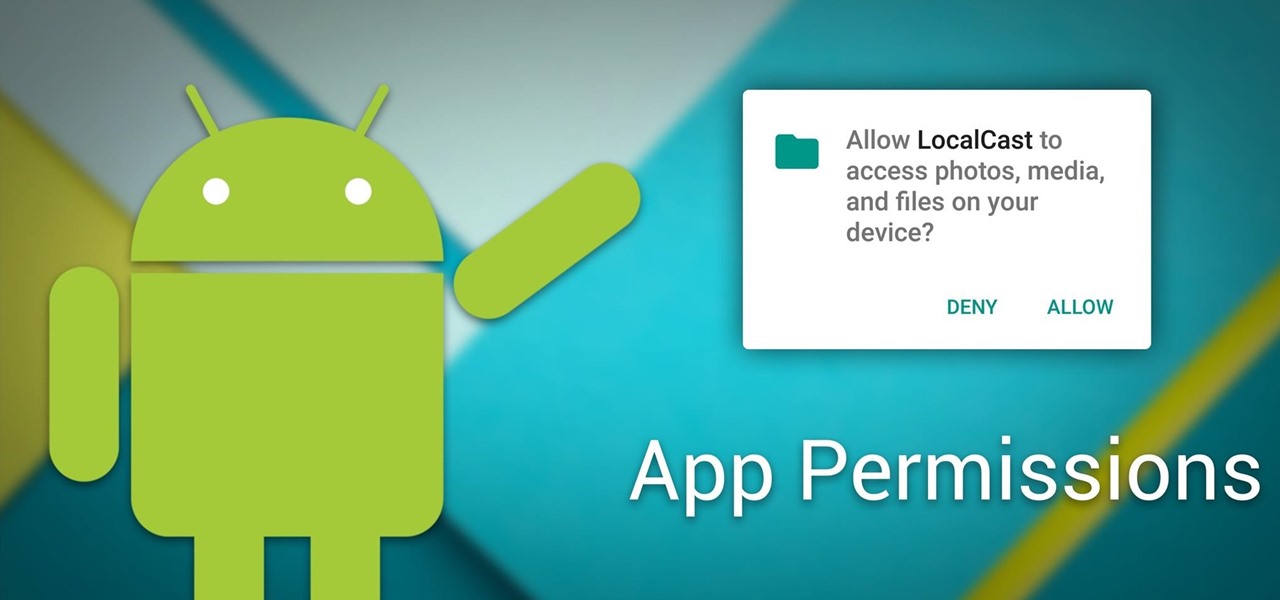
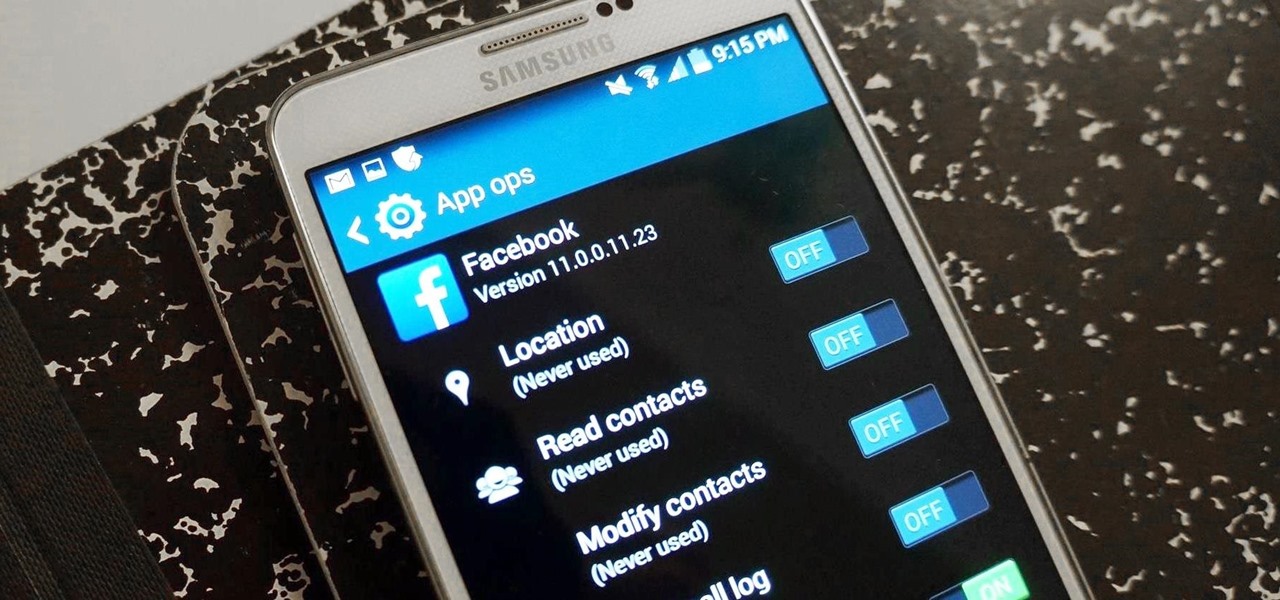
Android 6.0 Marshmallow added a new permissions system that can make your digital life much more secure. Unlike previous versions, apps now have to ask for your consent before they can access certain data, which puts you firmly in the driver's seat.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Welcome to another C tutorial. We will be looking at arrays, discussing what they are, when they are used and their special relationship with the char variable. Let's begin.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Want the next level security? Well then take a read here because this is some next level stuff. Heard of It?

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

The guide will walk you through a power switch replacement on a bObsweep Standard or Pethair. It includes:

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

As far as wallets go, mine is as full as they come; think something like George Castanza's overstuffed wallet on Seinfeld. I've got receipts, pictures, and tickets jammed inside, but what takes up the bulk of the space are all of the cards—credit, debit, gift, rewards, customer loyalty... I've got pretty much any card you can think of squeezed in. While it is a strain on my rear end, there's nothing I can do besides keep some of the cards elsewhere. However, looking for them when I need them ...

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

It's a modern day nightmare to accidentally reveal too much information on Facebook. I've inadvertently told the world my location more times than I can laugh off, and my friends haven't fared too well either. Just take a look at the requested app permissions next time you're about to click install and you'll quickly realize how much that app can reveal about you.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

The dryer’s idler pulley provides tension to the dryer’s drum belt so the belt won’t slip when the drum is turning. It can become faulty over time due to increased friction. If your dryer is making a squeaking or squealing nose then the idler is probably faulty. Replacing this pulley is a simple project. Repair your noisy dryer with this step-by-step tutorial!

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

A common problem on bumper covers is that the tabs that attach the bumper to the car get broken. This is critical, as this is what secures and aligns the bumper cover. Many times, a broken tab is all that is wrong with the bumper cover. With the cost of these plastic parts $200 to $700, the replacement cost can break the bank.

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

Here is how you can build a frame for your MEGA SOLAR SCORCHER in under an hour, and for less than $8!! This is effectively a 4 foot magnifying lens that concentrates insane amounts of heat from the sun. What would you do with all this free solar power? My design for this custom "Scorcher Frame" is easy to use, and incredibly cheap to make, as you can see in this step-by-step video.

Spices are a necessary ingredient in any kitchen. It doesn't matter how good of chef you are—without proper spices, your food will always fall flat.

In this tutorial, we learn how to make a ribbon bow with the help of toothpicks. Start with a full twist on your ribbon, then place it behind the toothpick and hold it in place with another toothpick. Next, make another loop and then do a front loop with a half of a twist. Now, secure those in place with toothpicks and do three side loops with half twists. Secure them with toothpicks, then continue with larger loops made with half twists. When finished, hold the ribbon in the middle with your...

Selling isn't easy. And it isn't any easier online, at least, until you get set up. It sure beats the streets. But how do you get ready to sell online?

Is your SD memory card getting a little too full? Is it not working? Try reformatting it. It's the first and sometimes last step to troubleshooting card problems. So, if your SD card has become too cluttered, this guide will restore it to a like-new condition with a simple format.

A whole is drilled into the cap of a barrel with a 3 1/4 inch bit and another one an inch or more below the top and one of 3 inches width on the next side. Spreaded adapters ends are wrapped with plumbers tape; to prevent water leaks. The ends are then screwed together and placed into the top hole in the barrel. The spiget is held into the side hole with a piece of pvc pipe and a garden hose is attached. A funnel is made with a piece of window screen mesh slightly bigger than a pvc pipe it co...

If you have just purchased a new Ford Taurus, you may have noticed the new SYNC feature. SYNC is a GPS built right into your dashboard. If this is your first time using a global positioning system, you may need a few pointers. Check out this video and learn how to access step by step directions and get where you need to go.

Everyone wants to have a pretty young thing on their arm, but not everyone can get it. To secure perfect trophy wife of your dreams, you need to meet a few criteria. Check out this tutorial and learn the do's and don'ts of dating younger ladies.

All of these four videos are excellent. You will notice that while all the videos and articles have slightly different design dimensions, they are fundamentally very similar. I urge you to view and read everything I am serving up. Then, my final words of advice are simply....choose between a barbeque switch and a taser gun. (Hint: there is a right choice, and there is a wrong choice.)