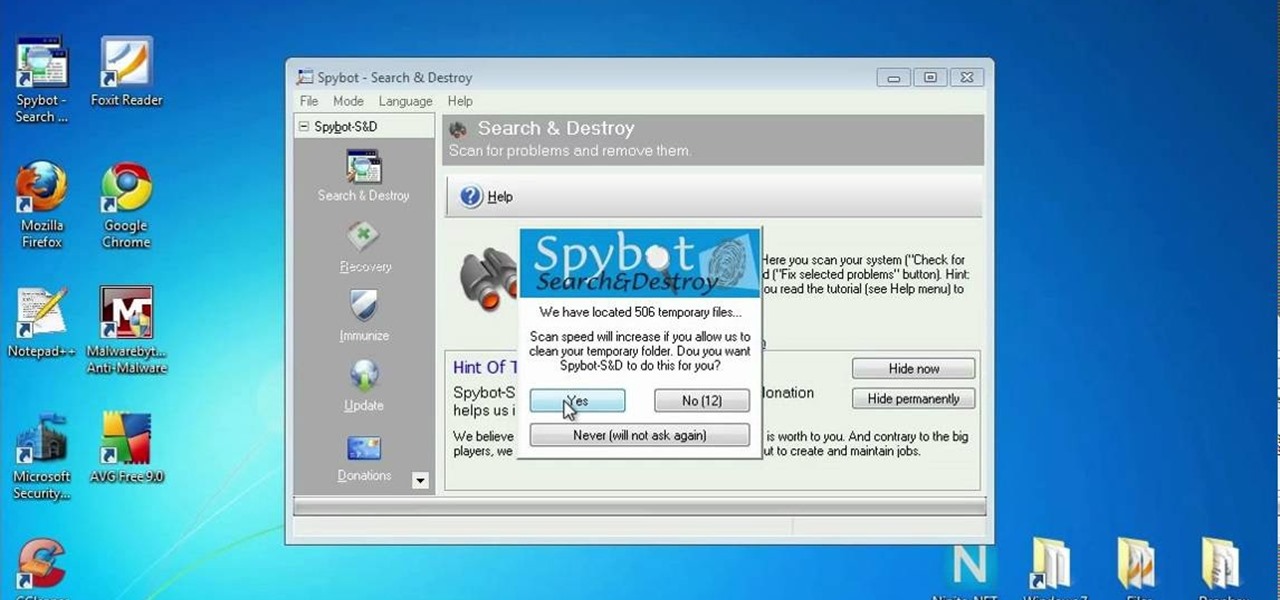
Picking a secure password is not only important for protecting your privacy, it's also very easy. Provided, that is, that you know how to go about it. This free video lesson from CNET TV will walk you through the process. For more information, and to get started creating and using high-security passwords yourself, watch this video tutorial.

Kandee, a makeup, artist demonstrates a Gwen Stefani up do that was from an Elle magazine cover. Rub hair paste into your hands and smooth it through your hair. Then section crown to forehead and twist it counterclockwise until it starts curling up. Keep twisting and wrap it around into a tight knot. Use a bobby pin to secure it at the base. Then take another section of hair and repeat. Split the bottom section of hair that is left asymmetrically and twist each of those sections halfway and t...

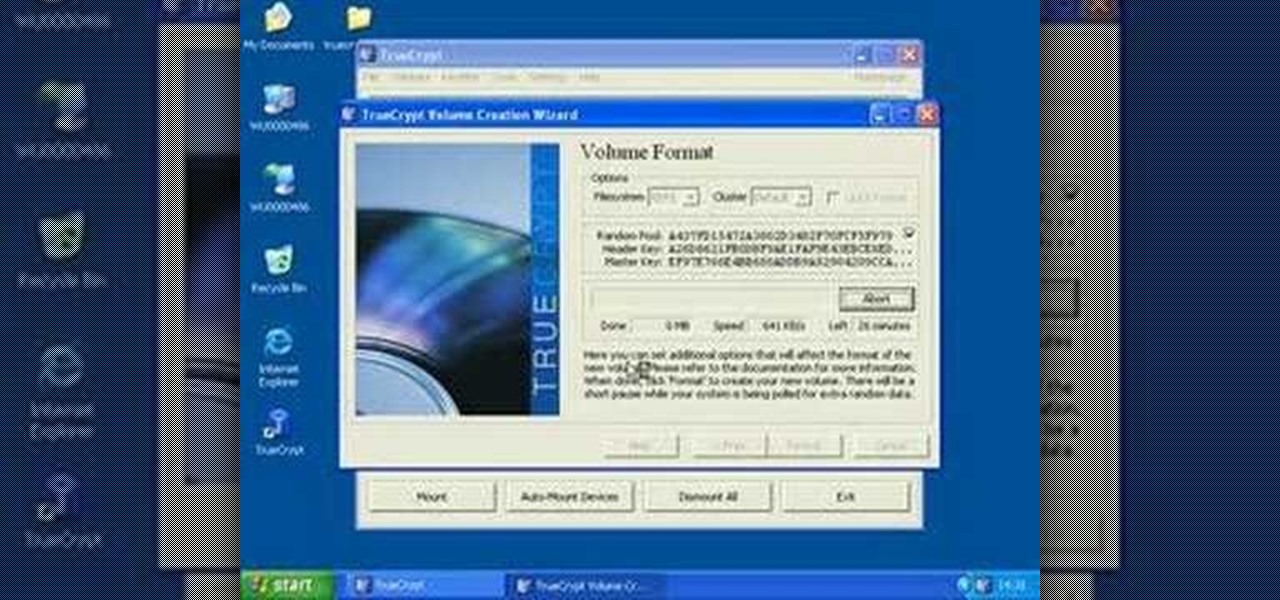
TrueCrypt is a free application that lets you encrypt designated programs on your Ubuntu system to prevent unwanted access. Provided you select a strong password, intruders will not be able to open your personal files and documents. This instructional video walks you through the process of installing TrueCrypt on your Ubuntu operated machine and demonstrates an example on how to create an encrypted volume within a select partition.

The Clinch Knot is used to secure your fishing line to your fishing lure. In this video, learn how to tie a secure clinch knot, step by step. You can't fish without a sturdy lure, so watch the video and practice until you master the knot on your own. Once you've got it, attach your bait and you are on your way! Happy fishing!

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Don’t play Russian roulette when it comes to your wheels. Keep your bike secure with these precautions.

A formal occasion calls for a classic look. You Will Need

Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

A little precaution can go a long way to securing your online banking experience. Use these tips from Tekzilla.

Secure a square knot with tips from this video.

Studies have shown that if you eat cereal regularly you will have a significant lower BMI (body mass index). You will want to eat whole grain cereals, but you will definitely want to watch out for the labels on which ones you buy to make sure you have the kind that will actually help you shed pounds.

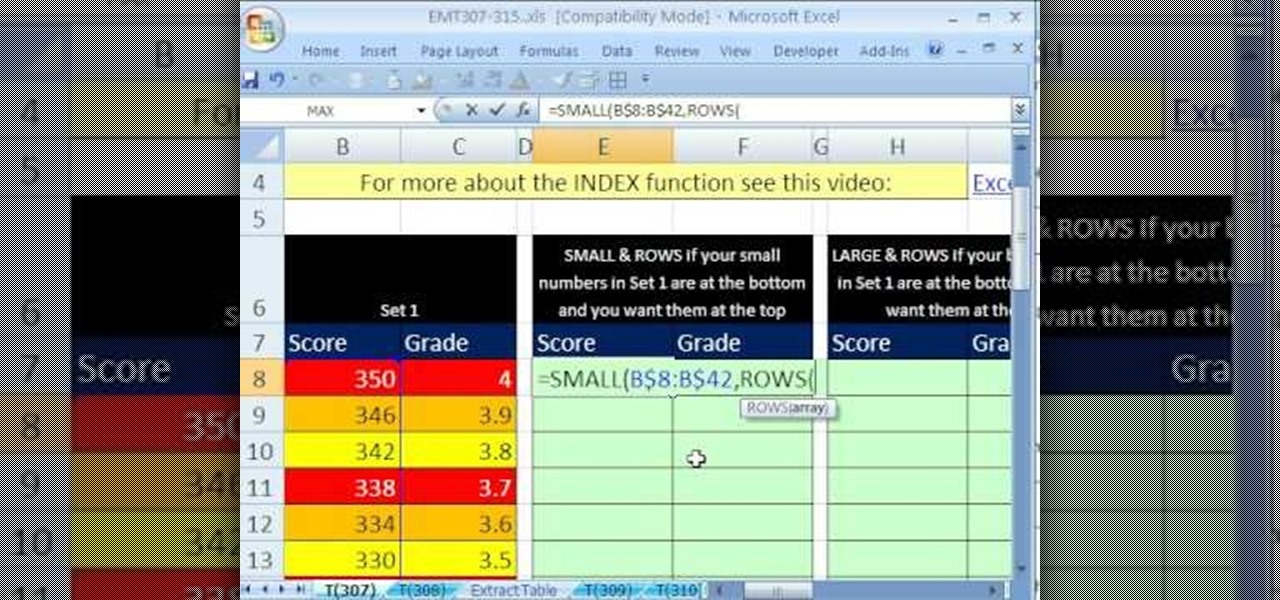
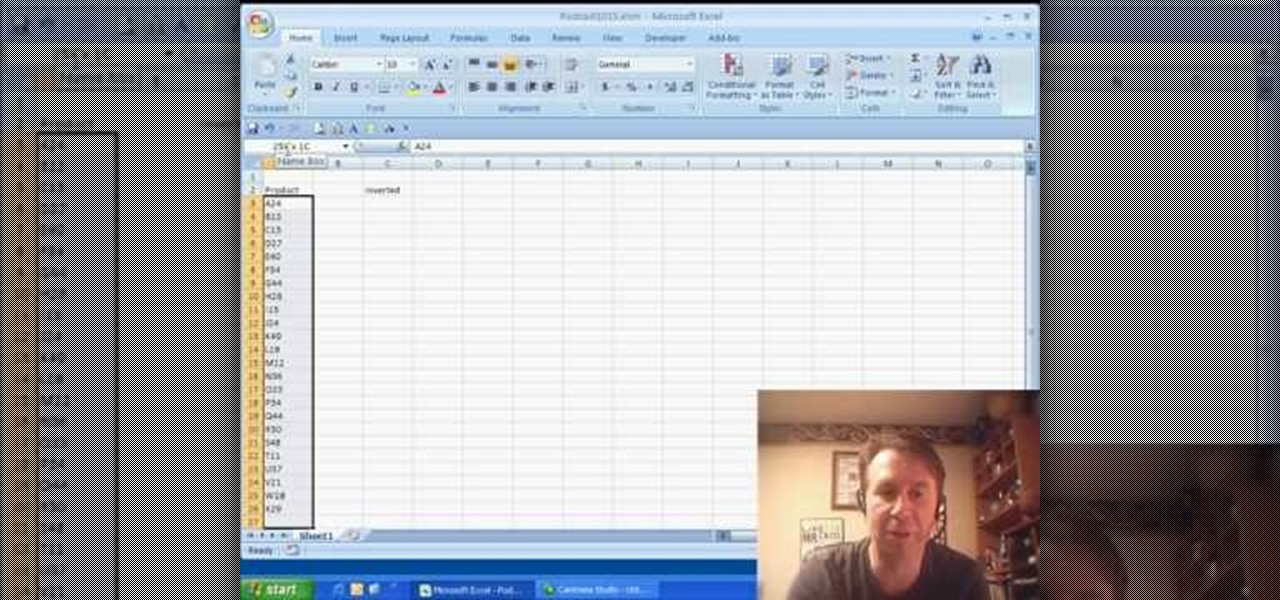
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 307th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the INDEX, ROWS, COLUMNS, LARGE, SMALL functions to create 4 different formulas that will invert a range of values.

This video shows the proper way to hold a knife and the proper technique for slicing and dicing. Watch and learn how simple it is. Make the knife an extension of your arm by pinching the blade with your thumb and index finger, proceed by placing your other three fingers on the handle of the knife.

The traditional six yards is undoubtedly among the most gorgeous outfits a woman can adorn. Here we tell you how you can wear it with a new twist for a modern look.

There's so much you can do with packing tape (besides packing). You can use it to seal art designs, turn everyday objects into sculptures, and even transfer photos. Or, if you have some index cards, you can turn them into a DIY dry-erase board that folds up and fits in your pocket like Redditor robertgfthomas did.

If you want to play 'Tell Me Why' by Neil Young on acoustic guitar you should first tune your guitar down a whole step for every string. First, the chords are in a Key of G. The chords you will play with are G, D, C, Am7, Gmaj7 and a Bm. Also on certain parts of the song you should lift up your index finger on the C. The verse will be C, D, Am7 and G. This is a boom-chucka rhythm which means you play the root note and go down up on the chord. You can throw in licks by lifting up your index fi...

Like everyone, you're on Facebook. And, also like everyone, you'd like to control the access your Facebook apps have BEFORE you even install them. Well, you can, with a sweet little Firefox add-on called FB-Secure. Take control of Facebook app privileges before they read your secret diary.

In this clip, you'll learn how to secure a new Microsoft Windows desktop or laptop computer. For more information, including a complete demonstration, and detailed, step-by-step instructions, as well as to get started protecting your own new Microsoft Windows PC, take a look.

If your home has a garage with a fairly standard garage door opener, that garage door is probably the easiest way for a burglar to gain entrance to your house. If you want to secure your home against such breakins, watch this video. It offers tips for securing your garage door so that thieves cannot gain access to your property and your family.

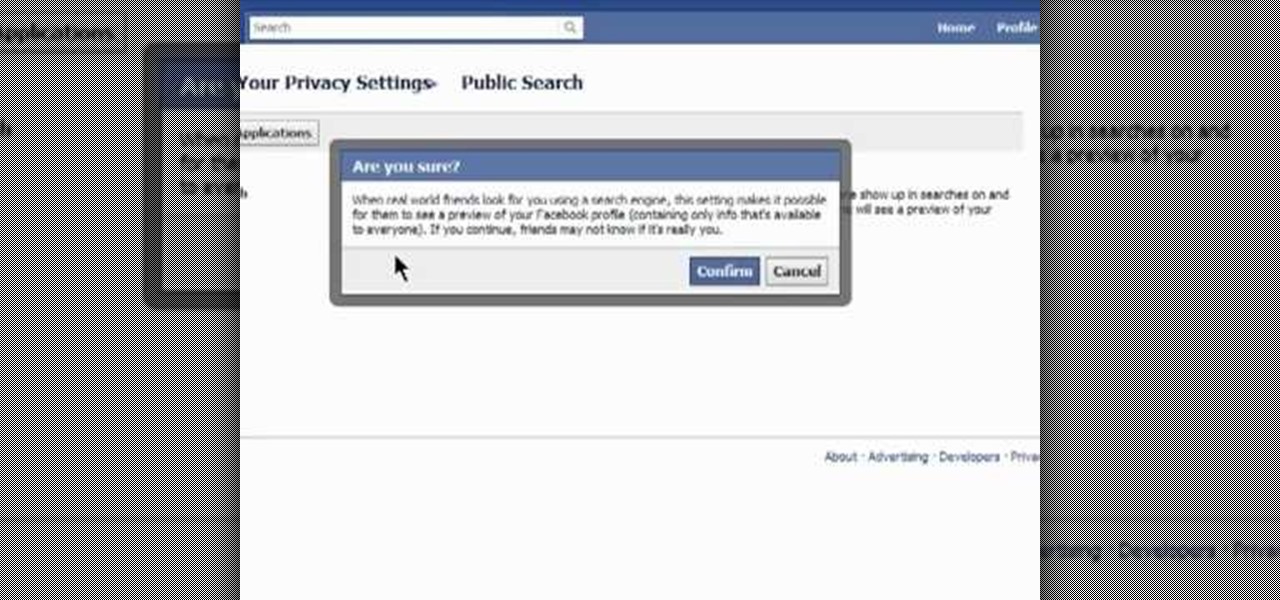
Looking for a guide on how to secure your public Facebook profile? This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

In this video, we learn how to wear a beret securely. This is used to keep the beret on your head so it doesn't fly away. To do this, you will need the beret and bobby pins. First, place the beret onto your head and style your hair around it so it looks how you prefer. Next, grab your pins and place then inside the beret holes onto your hair. Use a couple of the pins to make sure the hat and hair are connected and secured tightly. When finished, move the hat slightly to make sure it is secure...

Learn how to create & secure applications with BIG-IP v10. Whether you're new to F5 Networks' popular network appliance or are a seasoned administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

In this video tutorial, viewers learn how to secure a Mac Book Pro. Begin by opening the System Preferences and select Security under Personal. In the General tab, users are able to put on a password when the computer goes to sleep or screen-saver, disable automatic log in and log out after a certain amount of minutes. To set a password, go back to System Preferences and select Accounts under System. Then click on Change Password and input your password. This video will benefit those viewers ...

This video is a tutorial on how to make a baby diaper cake. To begin, you will need to roll all your baby diapers from the waist down and secure them with rubber bands. Your top tier will have 8 diapers, the middle tier will have 19 diapers, and the bottom tier will have 40 diapers. Use rubber bands to secure all your tiers together. Next, glue thick ribbon around the tiers over your rubber bands. Follow up with decorations such as bows and extra ribbons. Use a cake stick to secure the tiers ...

Need to know how to tie a Double Sheet Bend? This is a more secure version of the standard sheet bend, and an excellent way of joining two ropes of equal or different diameter. He's using flex rope, but it's a generally good way of securing two lines together.

Studying to be a nurse? Then one important part of nursing involves making your patient comfortable. This nursing how-to video demonstrates how to attach Foley catheter tubing to the leg to avoid pulling. Our nurse uses a catheter securement device to secure the catheter in place. Follow along and learn how easy it is to use this device to secure the Foley catheter to avoid pulling.

Learn how to secure a web site using the new Membership and Roles features of ASP.NET 2.0. In this ASP.Net video tutorial, the topics include user registration, password recovery, and restricting access to content with roles.

From email to online banking, you never want someone poking around in your personal information. Learn what to avoid when creating passwords, and try these tips to keep your passwords safe and secure.

Google Sites makes it easy for anyone to create and manage simple, secure group websites. You can create and publish new pages with the click of a button, edit web pages like documents, and move content and pages around as you please. Information is stored securely online, and you decide who can edit or view the site. Google Sites is powerful enough for a company intranet, yet simple enough for a family website.

This video tutorial will explain you how to secure a USB thumbdrive (or flashdrive) using the free, open-source encryption software TrueCrypt.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 10th installment in their joint series of digital spreadsheet magic tricks, you'll learn how to invert a range (turn a range of cells upside down) with two different INDEX formulas.

Mr. G teaches you how to balance a penny on a bent hanger and then spin the hanger with the penny still balanced around your index finger.

In iOS 13, Apple introduced HomeKit Secure Video, which allows smart home devices with cameras to give iPhone users a private and secure way to store recorded videos. Plus, it has benefits such as object detection and activity notifications. Logitech is the first to add support for HomeKit Secure Video with its Circle 2 cameras, and all it takes is a quick firmware update to get started.

Video: . This video will show you how to secure your kayak to a J bar roof rack carrier.

In the last iteration of how to train your python, we covered if/else and conditional statements. We're going to diverge a little today and cover lists. Lists are simply that, lists. It is a set of values located under one variable. Now that we know the definition of a list, let's learn about them! List Basics

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

You can run Android 2.3 Gingerbread on your Sprint HTC Hero. Watch this video to learn how to use CyanogenMod to install Android 2.3 Gingerbread on your HTC Hero. Here is the link for the described in the video.

The Desire Z's People widget gives you an easy-to-navigate visual index of all of your friends and contacts. Learn how to use it with this quick, official tutorial from HTC.

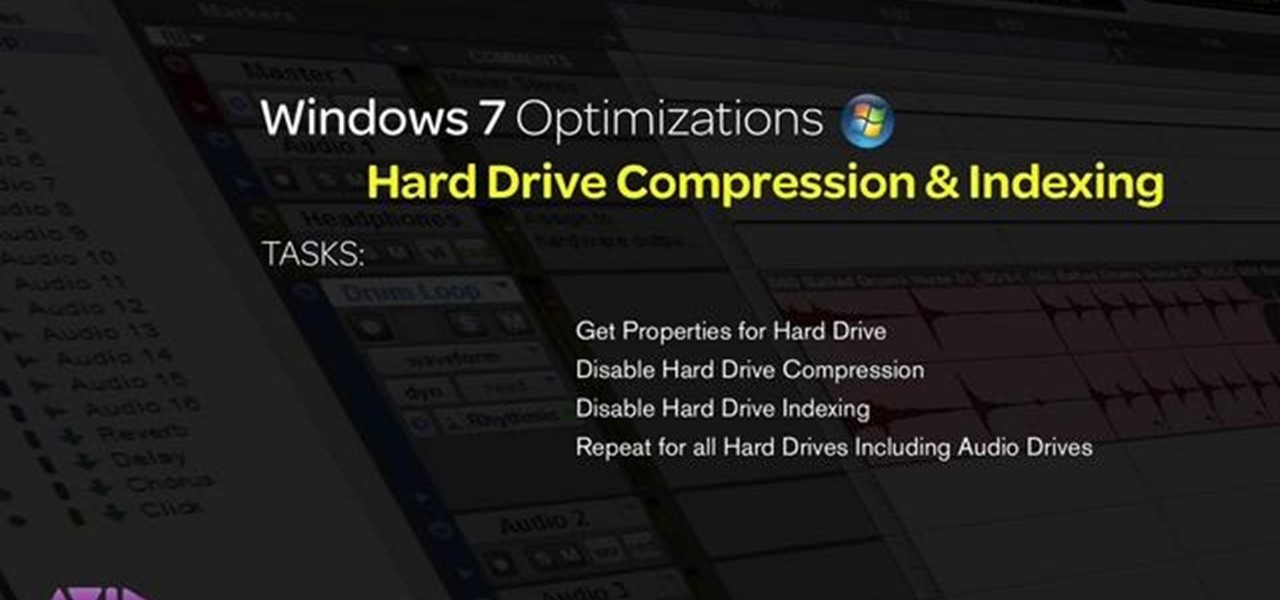
Want to get better results when you run Pro Tools on your PC? This tutorial shows you the easy step of disabling disk compression and indexing, two steps you can use to get the maximum efficiency out of real time applications like Pro Tools.

In this webmaster's guide, you'll learn how to use the Google PageRank tool to track a page's rank in the Google Search index. Whether you're new to the world of search engine optimization (SEO) or are merely looking to pick up a few new tips and tricks, you're unlikely to find a better source than this official video guide from Google. Take a look.