If you're in the market for a new lawn mower, there are plenty of options, and it might be hard making a decision on which one is right for you. This video breaks down what you need to consider before buying a lawn mower and how to find one that best fits your needs.

Xteeener wants to show you how to make the cool easy Updo Bun. Materials required:

If you just got some banging new subs for the trunk of your car, then you're just about ready for the ultimate car stereo. But what kind of amp are you going to get to power those subwoofer speakers? Learn about the basics of car amplifiers in this video from Sonic Electronix, where they discusses the purpose of a car amplifier, as well as the parts of the amplifier. This includes the terminals, adjustments, types of amplifiers, and amplifier channels. Before putting together your first after...

Even if you're a master at the grill, dealing with the tank can be a little intimidating if you've never done it before. But there's really not much to worry about. Exchanging or refilling your gas grill tank is easy to do.

Watch this quick RV tutorial video to find out how to maintain or repair your furnace. All of the items shown are simple steps you can do yourself. Some motor homes have two furnaces and some have one. They should be located on one of the sides of the unit. In the shape of a medium sized rectangle. This compartment will also have a grill and it does stay hot. In order to open it up, remove the screws, remove the first door, and then there will be another one that just comes down as well. Then...

Two locks are used for truck trailers to prevent someone from taking the trailer. Secure a truck trailer by using locks with tips from a custom car repairman in this free auto maintenance video.

We know our Null Byte readers would like to see some iPhone-hacking scenarios on the site soon, but until we get some of those up, we understand that some of you actually use an iPhone as your primary phone. If that's you, and you would like an easier way to get information from point A (your iPhone) to point B (your computer) and vice versa, there's an all-in-one tool that can help.

For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level.

Smartphones have so much sensitive information attached to them. If you share your home with others, then you know the pains of trying to keep anything private. Photos are surely among the things you'd prefer to keep to yourself, so OnePlus has you covered.

Despite the recent gut punch of staff layoffs, Canada-based smartglasses startup North and its Focals are likely to be in the game for a while longer.

Thanks to its encrypted messaging, WhatsApp can be a platform for secure communication with friends and family. One drawback, however, is that the app would let anyone add you to a group chat, regardless of if you approved it or not. This lack of control over your own account is over, as WhatsApp now lets you decide who can add you to a group chat.

With plans to compete with Niantic and other augmented reality game developers, game developer WarDucks has closed a $3.8 million funding round.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

Less than a week after debuting its AR Cloud platform in public with a multi-user installation of more than 100 participants, Ubiquity6 announced on Tuesday that it has closed a Series B round of funding totaling $27 million.

Snapchat is enjoying a high field goal percentage when it comes to securing movie studio business with its sponsored augmented reality experiences, the latest coming through the basketball movie Uncle Drew.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

The business of enabling the development of augmented reality experiences appears to be as lucrative as AR app development itself.

Google's AI investment arm, Gradient Ventures, has joined a $10.5 million round of funding for Ubiquity6 and its platform for shared augmented reality experiences, just weeks after Google's GV fund backed a competing AR cloud platform.

One of the best-received features of the OnePlus 5T was the relatively secure face unlock, which made it quick and easy to get into the phone. Unfortunately, this feature wasn't included with the slightly older OnePlus 5 at first, but now, face unlocking is finally out of beta and available to everyone with a 2017 OnePlus.

Just nine days after the official release of iOS 11.2, Apple has released iOS 11.2.1. The update initially seems to have been seeded to only a handful of users and is intended to fix bugs in 11.2.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

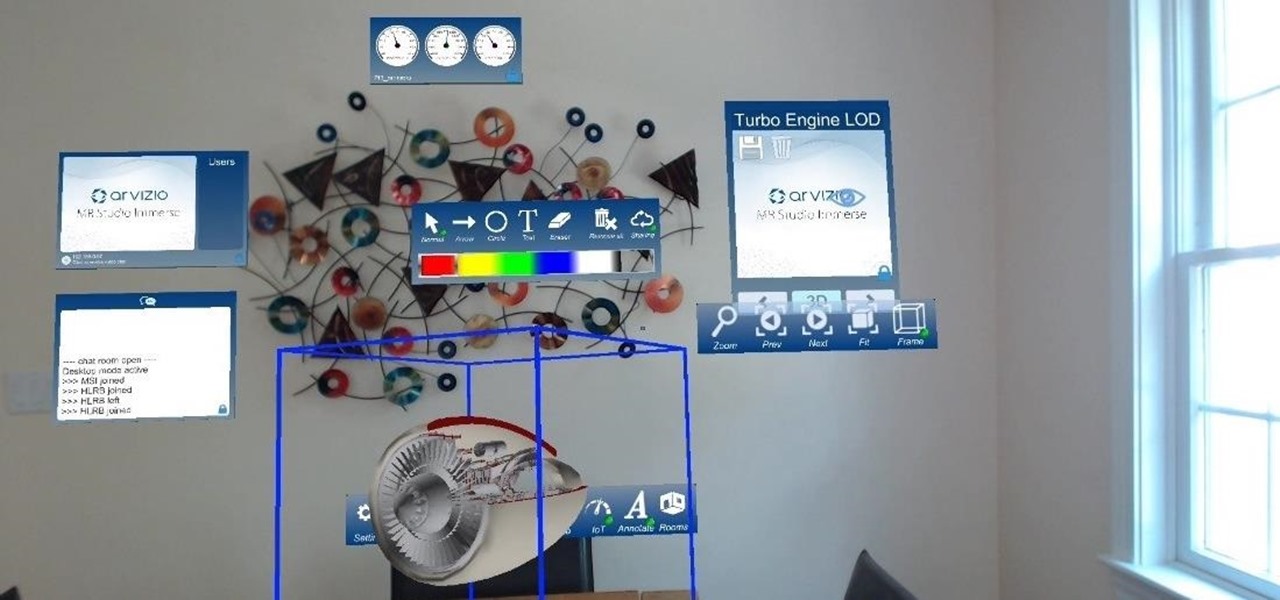
HoloLens developer Arvizio has expanded its collaboration suite of tools for enterprises with a device that can stream and record mixed reality experiences in high-definition for local and remote audiences.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

Augmented and virtual reality motion tracking leader Leap Motion, Inc. announced that it has secured $50 million in Series C funding to fund expansion into new territories and industries.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

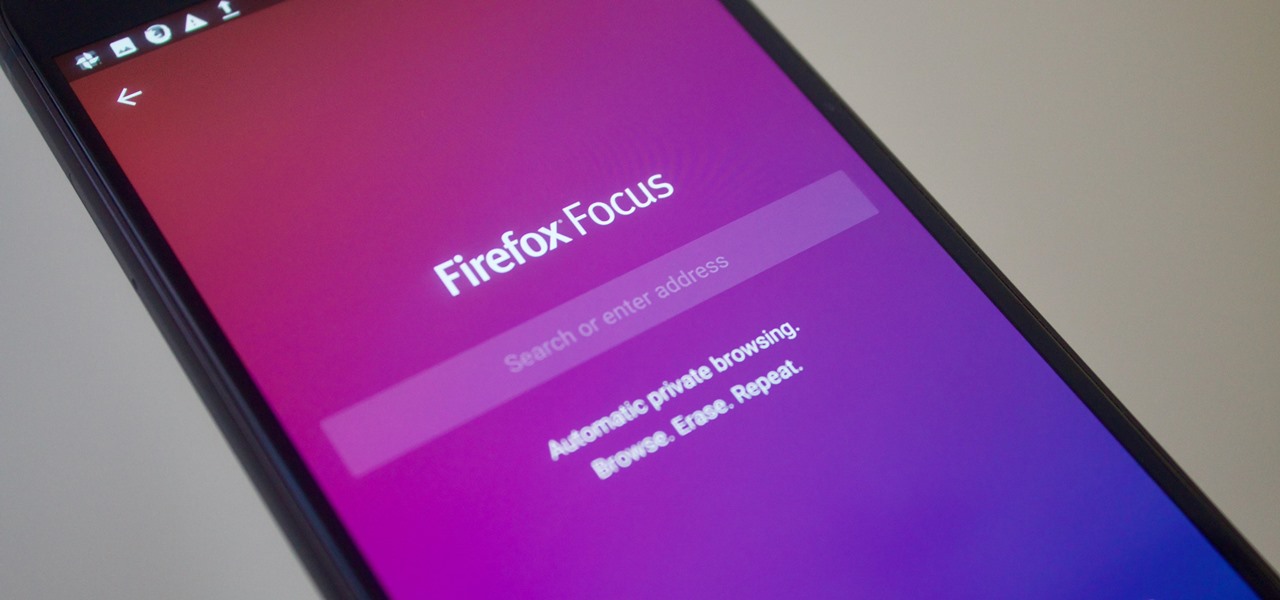
Firefox Focus is Mozilla's effort to make your internet experience a little more secure. Originally released in November 2016 for iOS, Focus blocks internet trackers, search history, anything that gets in the way of a clean, private browsing experience.

With the British exit from the European Union looming, the UK is looking to the auto industry to help boost their economy and secure jobs through the upcoming years. Today, Business Secretary Greg Clark and Transport Minister John Hayes announced the government investment of $136.7 million (£109.7 million) across 38 different automobile projects, as a part of the Plan for Britain.

Independent game developer PlayFusion announced today a partnership with NEXON Korea Corporation, resulting in a Series A preferred share round to fund development of their entertainment platform. PlayFusion's platform applies augmented reality, Internet of Things (IoT), and audio recognition to Lightseekers, an original property that combines mobile gaming with smart action figures, trading card games, and other media.

Facebook Messenger is getting ready to roll out a Snapchat-esque feature that will let users send messages that self-destruct after a certain amount of time, so you'll have an extra level of security when you need to send sensitive financial information or, more likely, risqué texts or images.

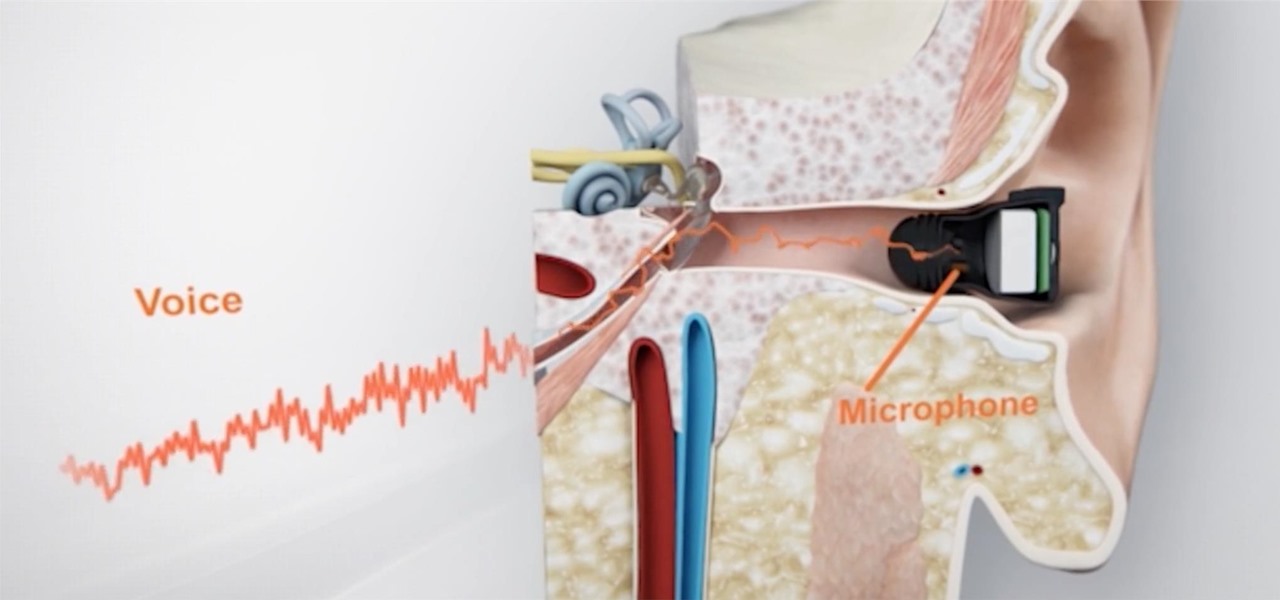
What's better than wireless in-ear headphones with noise-canceling technology? Giving them a microphone to hear you talk from inside your head. And that's exactly what you get with RippleBuds; its inside-facing mic helps keep your voice crystal clear over phone calls, and makes sure Siri, Cortana, and Google Now will always get the right command.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Recently the newly famous ProtonMail service was under attack by DDoS attack. This attack was believed to be the hacking group Armada Collective.

In this tutorial I am going to show you how to change some file metadata, this could be very useful if you want to edit or access a file and remove any evidence of your changes.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/)

This is a really tasty "scary" snack as it incorporates a lot of the flavours you'd usually put together (along with the almonds)

Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.