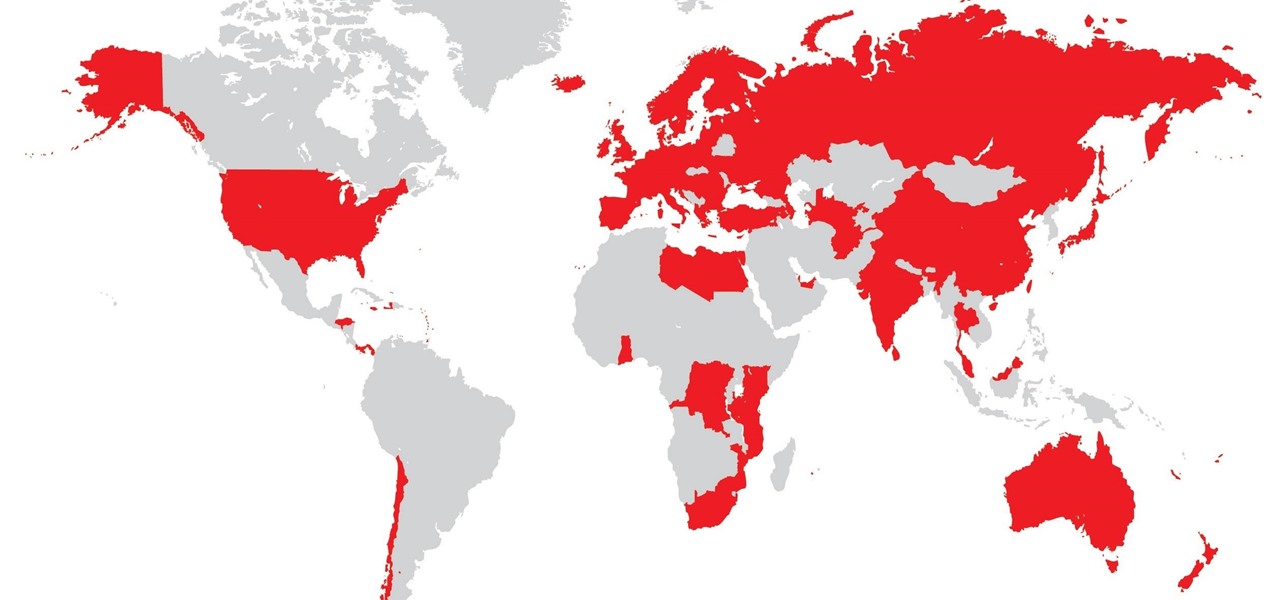
Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.
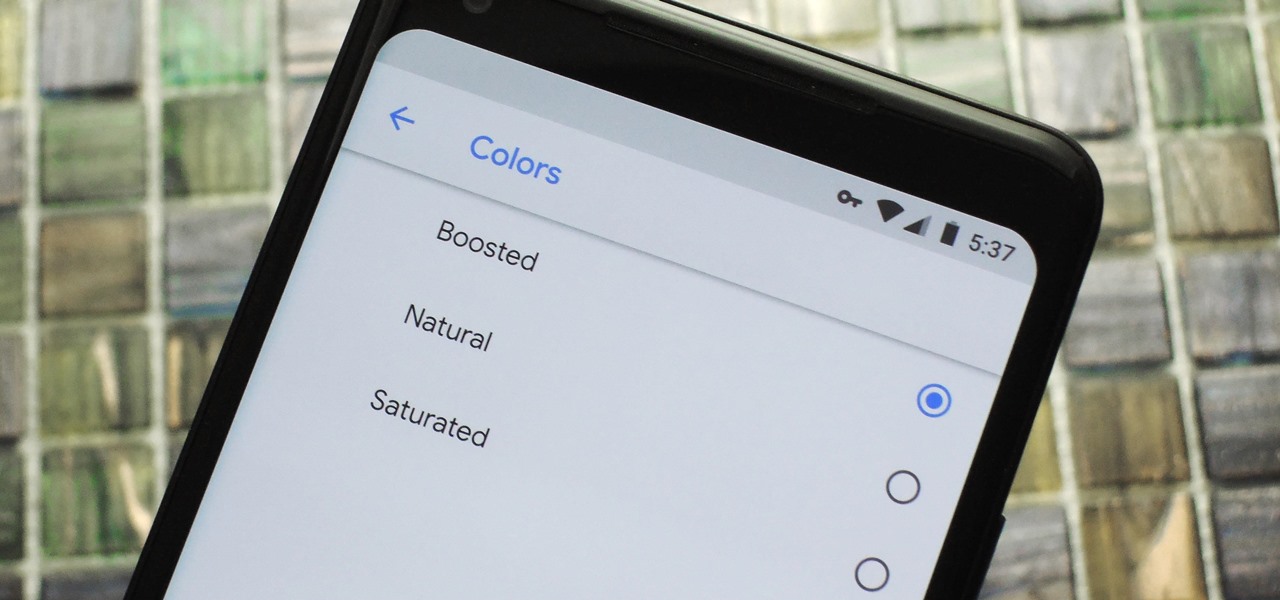
Google caught a lot of flak for the Pixel 2 XL's POLED display issues, regardless of whether the problems were real or perceived. It's too late to contract another screen manufacturer at this point, but Google is doing the next-best thing: Fixing as many user complaints as possible with software updates.
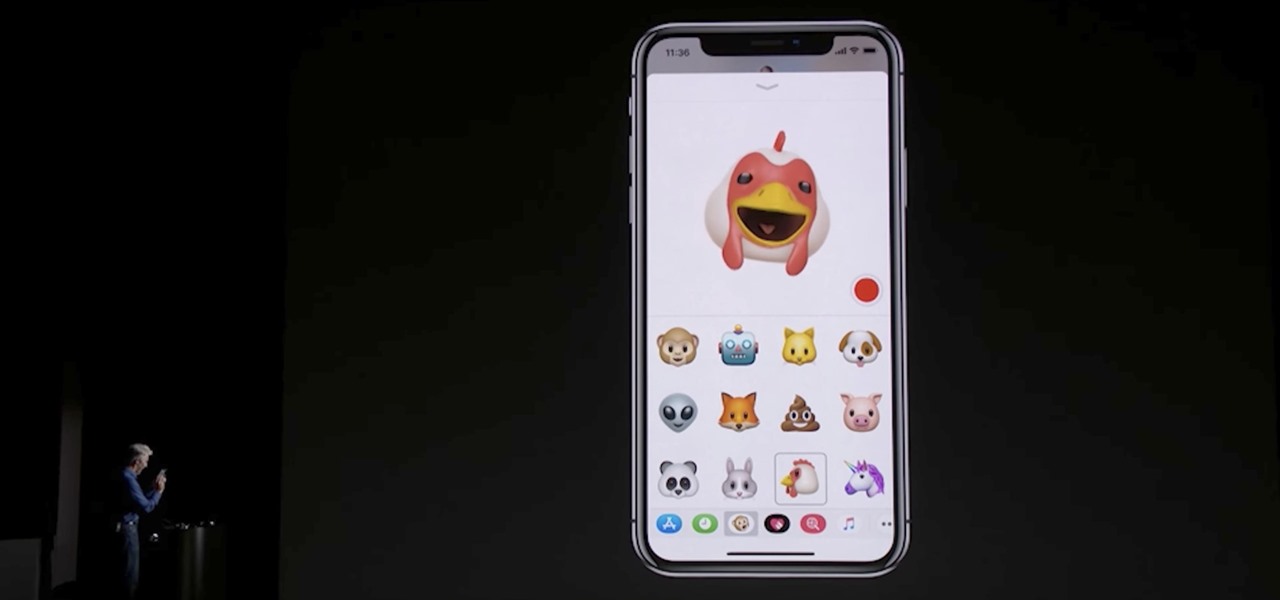
Animoji, short for animated emoji, was a focal point of the iPhone X presentation at the Sept. 12 Apple event. The reactions were split, to be sure, as some considered the attention to this feature on a $1,000+ smartphone to be a bit, well ... too much. As goofy as Animojis may seem at first, the tech behind them is undeniably impressive. In fact, it's possibly the most technically advanced feature of the iPhone X.

Microsoft's latest move to further secure its hold on the emerging mixed reality space comes in the form of two new Mixed Reality Capture Studios in San Francisco (the flagship studio) and London.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

A Russian augmented reality startup wants the next frontier in real estate to be augmented reality estate.

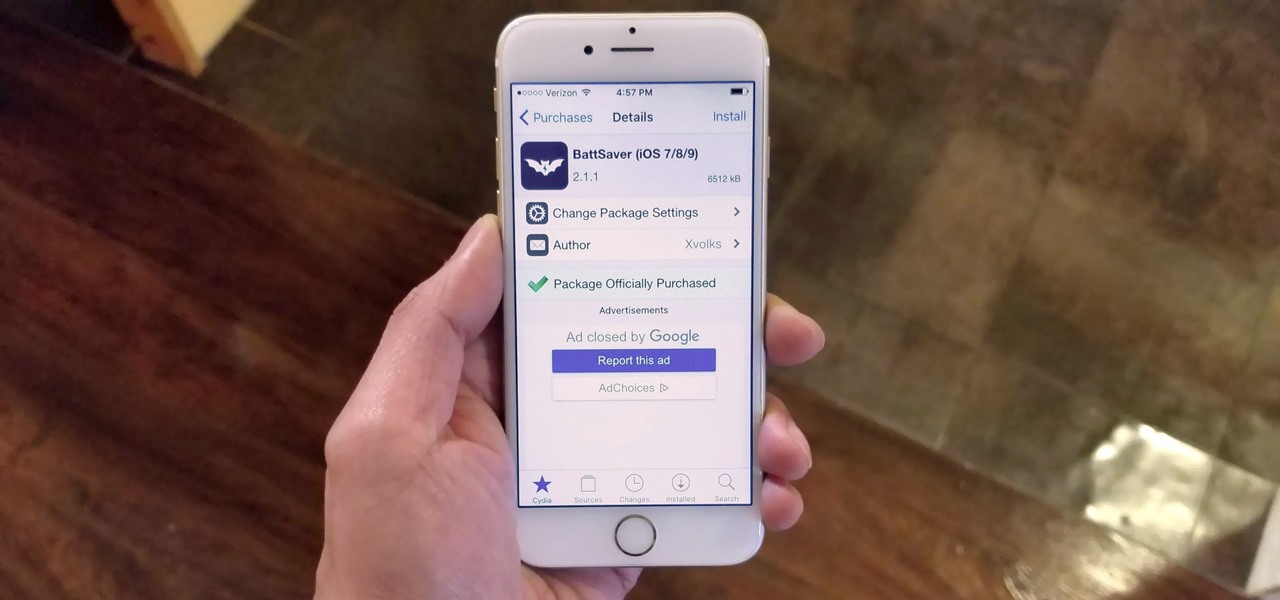
While widely known for its massive collection of free apps and tweaks that let you fully personalize your jailbroken iPhone, Cydia also comes laden with packages that can be purchased to take customization to a whole 'nother level. Similar in function to the iOS App Store, buying an app in Cydia is simple and relatively safe.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

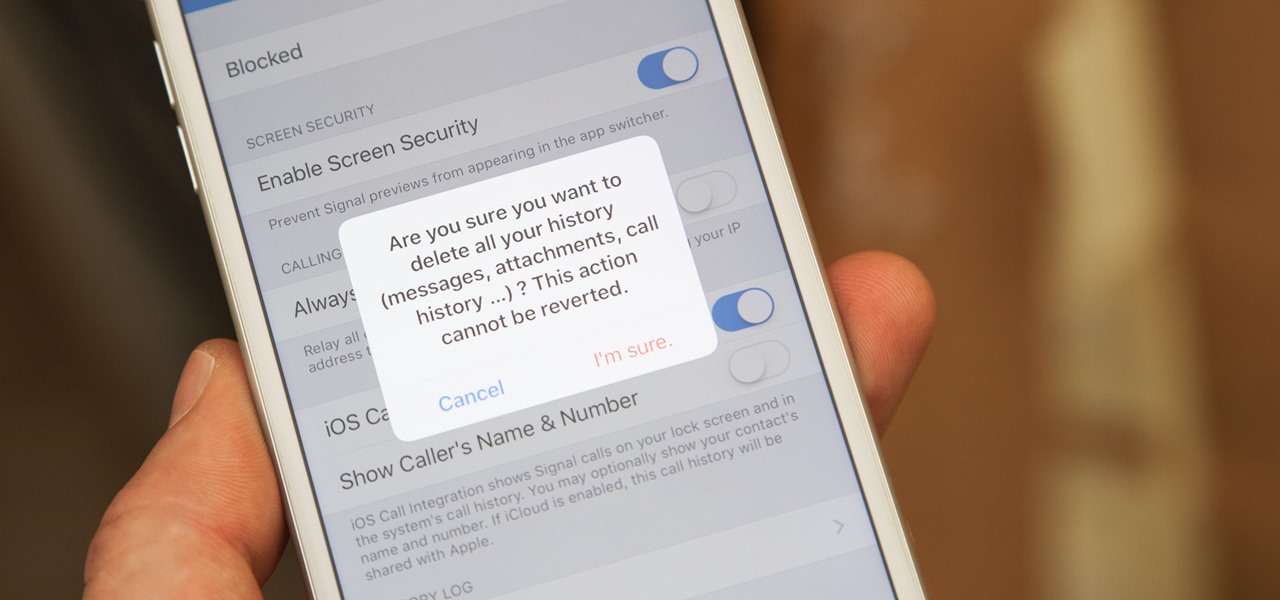
If thieves, hackers, law enforcement, or other would-be enemies should ever gain entry to your smartphone, they could also access conversations you've had in Signal Private Messenger. To better secure your encrypted communications, you can password-protect the whole app and its contents — but only on Android. Even then, it's necessary to perform data deletion on a periodic basis, if not immediately.

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.

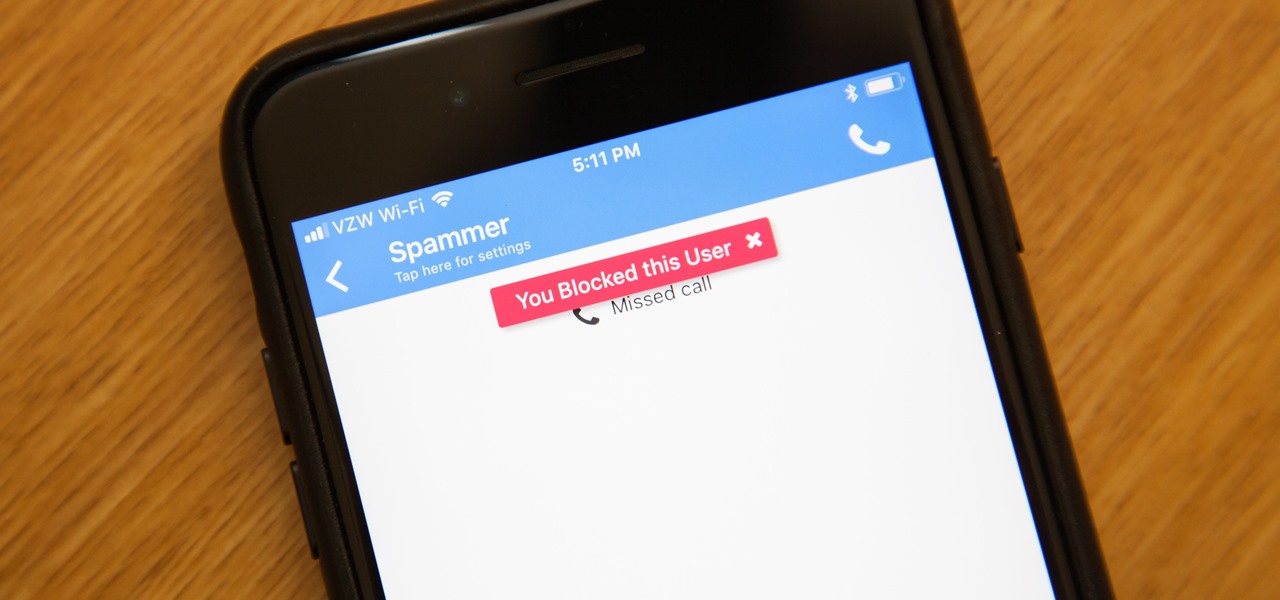
While it's a more secure platform for messages and calls, Signal's job isn't to prevent unknown users from contacting you, so you run into the same issues you would with a regular phone number. People you know that you don't want to talk to may try to strike up a conversation and you'll still get spam messages. Luckily, it's easy to block these suckers.

Drive.ai (a startup founded by Stanford University graduates), Waymo, General Motors, and serial entrepreneur and author Vivek Wadhwa are featured in today's top news.

If you've ever seen me glued to my iPhone, huddled on the corner of the 23rd St subway station fidgeting with my stupid hot pink nails trying to Instagram Story, then now you are about to find out exactly what I've been doing.

A spokesperson from the Nissan and Renault Alliance told Driverless the group is testing self-driving electric "robo-vehicles" for future mobility services and is "not ruling out anything" for future services the group might offer, as the alliance widens its driverless business model to include both fleets and private sales.

While two augmented reality companies were recently recognized for their innovative technologies, other companies have turned to augmented reality to innovate in their respective fields. Over the past week, use cases have ranged from selling snacks and video games to raising awareness for public health issues.

Reports of Samsung's Galaxy Note 8 having an in-display fingerprint scanner have been circulating for the past few days. Fans have been excitedly discussing the potential of the phablet possessing this technology, as it would be the first phone released with these capabilities. Unfortunately, a Samsung official revealed today to Naver — a South-Korean web portal — that Samsung has decided to forgo incorporating the feature into the Galaxy Note 8 due to technical limitations and time constraints.

Replacing your iPhone fingerprint sensor has been one of Apple's most cruel tortures. It's a slow and painful process made worse last year when Error 53 messages started appearing on the phones of users who had tried to repair their sensors outside of Apple. The error rendered the phones essentially useless. Since then, Apple has provided fixes but is now finally making it much easier to replace your iPhone fingerprint sensor with the releasing of "Horizon Machines" to official repair locations.

Another entrant — Aryzon — has joined the competition to be crowned as the "Cardboard of AR." The Netherlands-based startup launched their Kickstarter campaign Monday (May 29) and the campaign has already surpassed its funding goal. The company expects to ship units to backers in September.

Malware attacks on mobile phones are reaching an all-time high and it looks like companies like Samsung are doing all that they can to prevent any unwanted hackers from accessing its sensitive user data.

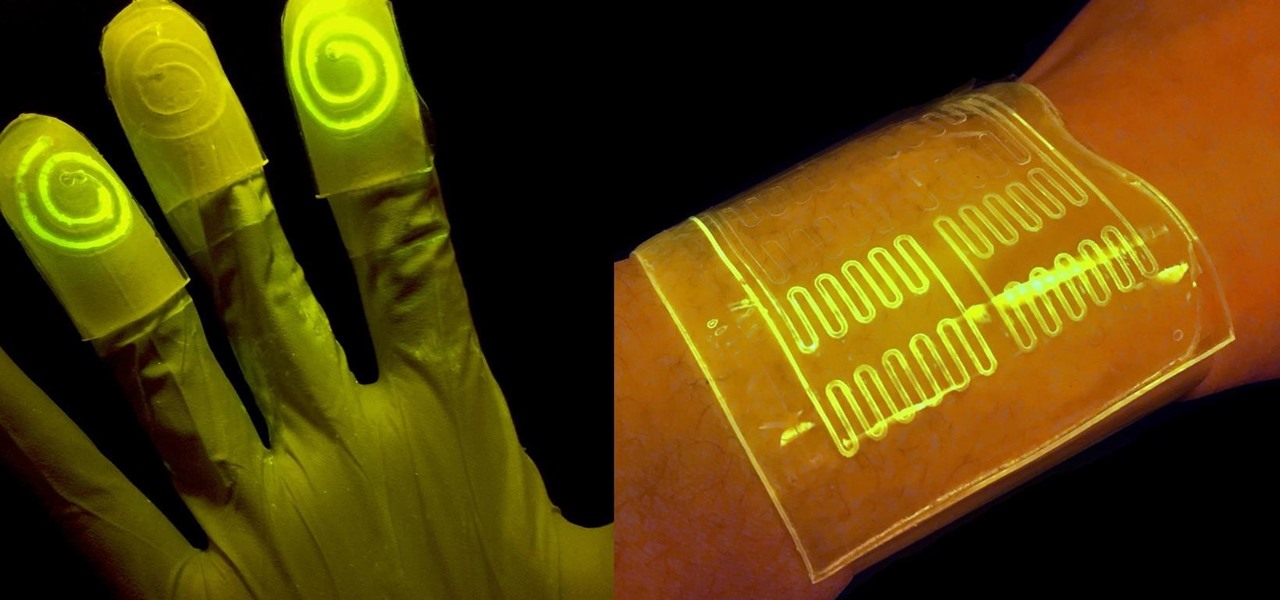
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are becoming a reality as researchers move forward with technology to use living bacteria in cloth to detect pathogens, pollutants, and particulates that endanger our lives.

The May 2017 security update has begun rolling out to Nexus and Pixel devices, which is usually great news. It means that your device is now being updated to protect you from the latest exploits and vulnerabilities found in Android. At other times, though, security updates patch root methods like Dirty COW, which is extremely frustrating for users and developers alike. Especially since most OEMs don't condone rooting or even unlocking the bootloader on their devices.

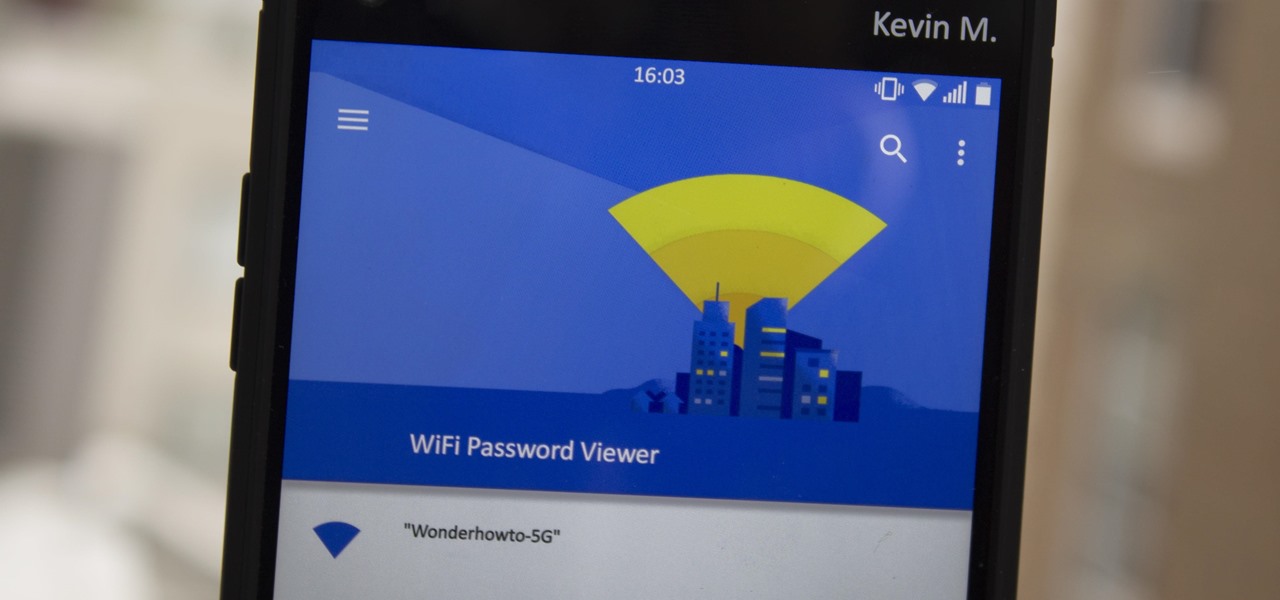
Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you have a nice and secure password with uppercase and lowercase letters, numbers, and symbols.

Everyone feels a little safer with Android's security updates, which are welcome and often necessary protective measures. But what happens when the update that's supposed to safeguard your phone actually ends up wreaking havoc with its security system?

It looks like Samsung was thinking about slapping a little nub of a home button on the Galaxy S8 and S8 Plus. This is according to a patent published by the European Trade Mark and Design Network, uncovered by Android Headlines. Despite having a nearly bezel-less display on their latest flagships, the South Korean manufacturer apparently considered modeling the design after last year's Galaxy S7 and S7 Edge.

When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo.

Despite a round of updates to Pokémon GO that patched and eliminated location spoofing, the game still has a difficult time dealing with the most hardcore cheaters. Like weeds on a grassy lawn, third-party bot makers still remain the biggest thorn in Niantic's side and continue to thrive despite the developer's best efforts to root them out. While the latest updates have blocked users from running modded versions of the game, like Pokemon GO++, that feature built-in joysticks to move your pla...

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Hackers are good at what they do—some can even use the way you move your phone to guess a 4-digit PIN in five attempts or less. That's why most of us with compatible hones use the fingerprint scanner. It's just much more secure. Or is it?

As with any new smartphone (but especially with Apple), the iPhone 8 is generating rumor after rumor. This newest rumor, however, rocks the boat a bit, as BGR reports that the iPhone 8 may release at Apple's standard time in the fall, but the 3D camera will be pushed to the 8s.

Dreaded are the days when you're working on a masterpiece, then all of a sudden, your Windows computer crashes, loses power, or an app just gets up and quits. Well, now there's an app for that.

Vodafone India has merged with telecom company Idea Cellular to become India's largest mobile player this week.

Overweight kids often become overweight adults. New research suggests a couple reasons why and suggested that there may be ways to intercept that fate.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Blue light (like that from our smartphone) tricks the human brain into thinking it's still daytime, even if it's coming from something as small as a screen. So while you're playing around with your new Pixel or Pixel XL after dark, subconscious signals to be awake are preventing you from getting to sleep as early as you should.

Passwords are everywhere. We use them to unlock phones, computers, websites, encrypted disks, encrypted files... the list just goes on and on. Savvy users will already have a password manager of some sort that can generate a very strong password on a per site basis. However, these password managers also require a password. Not only that, it has to be something memorable.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

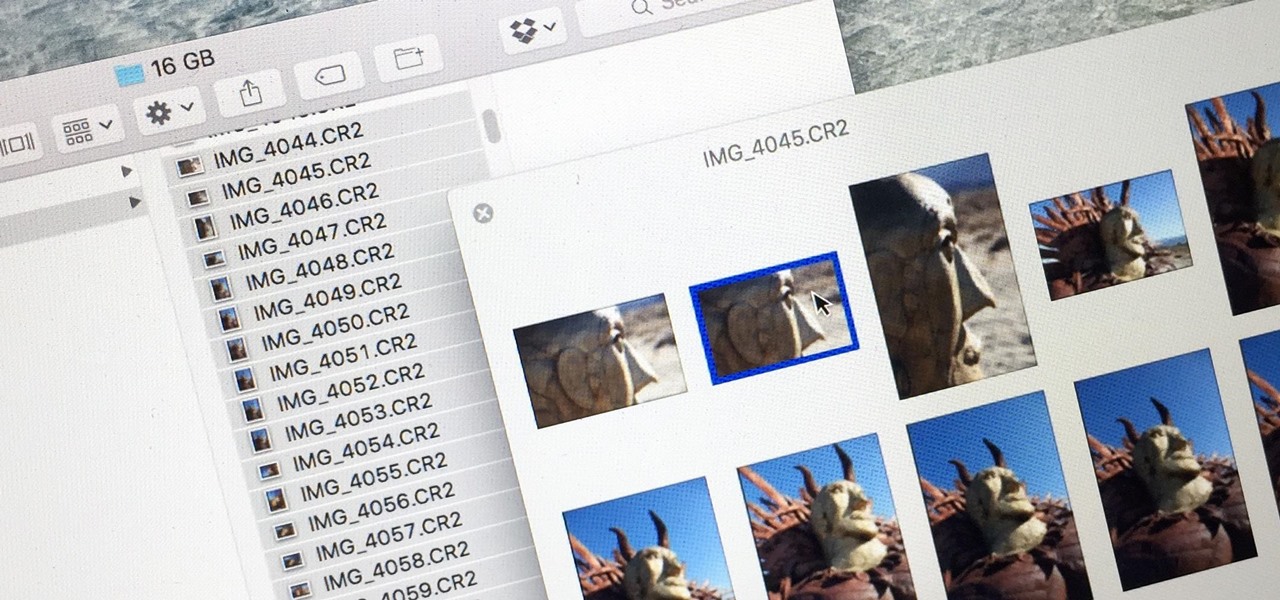
Quick Look, first introduced in 2007, is an instant preview feature on the Mac operating system that lets you view files and folders without opening them up. Just highlight a file, like a picture or text document, then press the spacebar on your keyboard to get a speedy preview of it.

There may be no other crustacean with as many names as the crawfish: crayfish, crawdad, crawdaddy, mudbug, Florida lobster, spiny lobster, rock lobster, and freshwater lobster (to name a few). But no matter what you call it, there's no denying that it's a popular delicacy in the South and beyond.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

The most genius summertime snack hack that we've come across recently is, without a doubt, the campfire cone. Astounding in its simplicity and ease of preparation, yet brilliant in its execution, the campfire cone has something for everyone: parents and children, expert and novice campers, backyard barbecuers, and oven lovers alike.