Check out this instructional video to learn how to use hotel room safety tips. Make your vacation or business trip uneventful when it comes to staying safe in your hotel. Check out these tips for keeping you, and your stuff, safe when you're sleeping away from home. Hotel Room Safety - Stay Safe and Secure in Hotels Video.

Welcome to the Rudi Latka's Soccer School. The basic dive is best done at speed so the referee can't see what's happened. As you approach your opponent, flick the ball past them, and then as you pass the player dive upwards and then turn in the air slightly before landing. As you land look towards the ref with puppy dog eyes in order to secure the free kick. Dive while playing soccer.
Facebook is at it again. First they invaded your privacy with Instant Personalization, now they plan to take it a step further with their controversial plans to share users' home addresses and mobile phone numbers with third-party developers and websites.
You know it's crazy out there when governments start blocking social websites like Facebook, Twitter and even YouTube. But that's what happened in Egypt, when tens of thousands of anti-government protesters took to the streets on Tuesday (January 25th) in hopes of ending President Hosni Mubarak's 30 years of authoritarian power.

As useful as VPNs are for securing your browsing experience and bypassing frustrating barriers online, it's hard to find the right one among the horde of choices. VPN.asia: 10-Year Subscription is a great choice for a VPN that keeps your browsing safe and smooth, and right now, it's only $79.99.
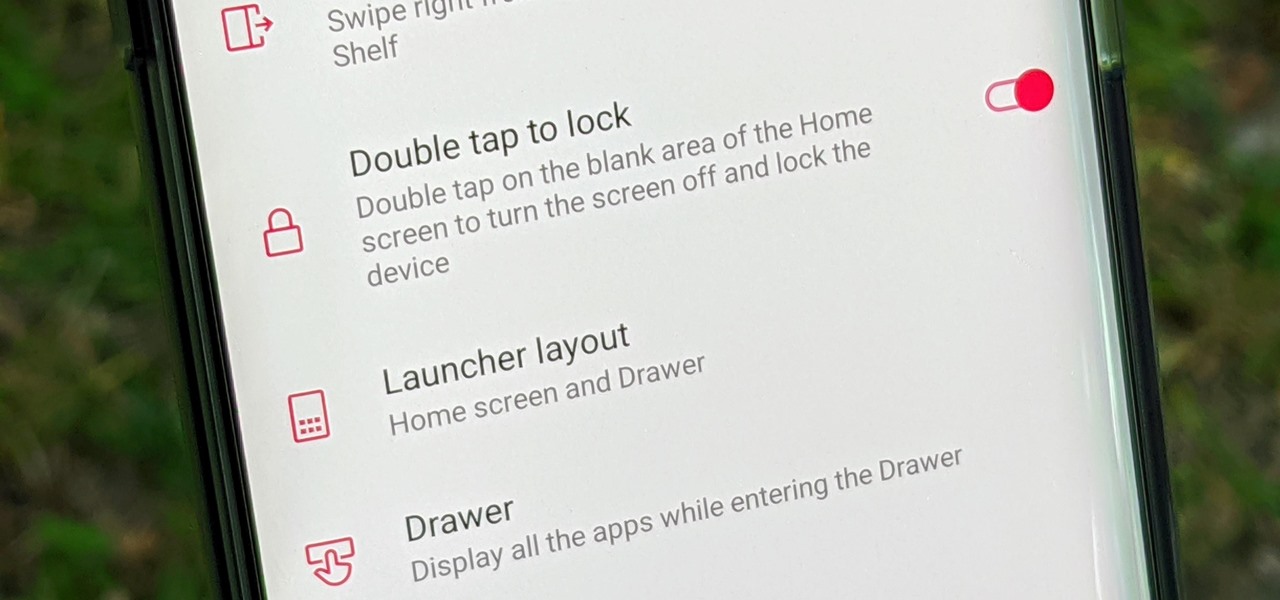
By default, most Android phones will instantly lock once you turn the screen off with the power button. Doing so is a surefire way to secure your device when you walk away, but what if there was another way to accomplish this even faster? If you're using the OnePlus Launcher on your OnePlus phone, there's something you can do to lock your phone instantly without pressing the power button.

Well this law was passed... Our privacy is slowly being pulled away from us. But I'm certainly not going to let it stop me. We'll just have to take more secure measures. If You Use Tor Browser, The FBI Just Labeled You a Criminal.

In an effort to prevent drones from being hacked, DARPA has been developing an "unhackable system," and seems to think they're almost there. The development team "proved" mathematically that their kernel was unhackable, and they hope to use it for more than just drones (power grids, cars, phones, pacemakers, etc.).

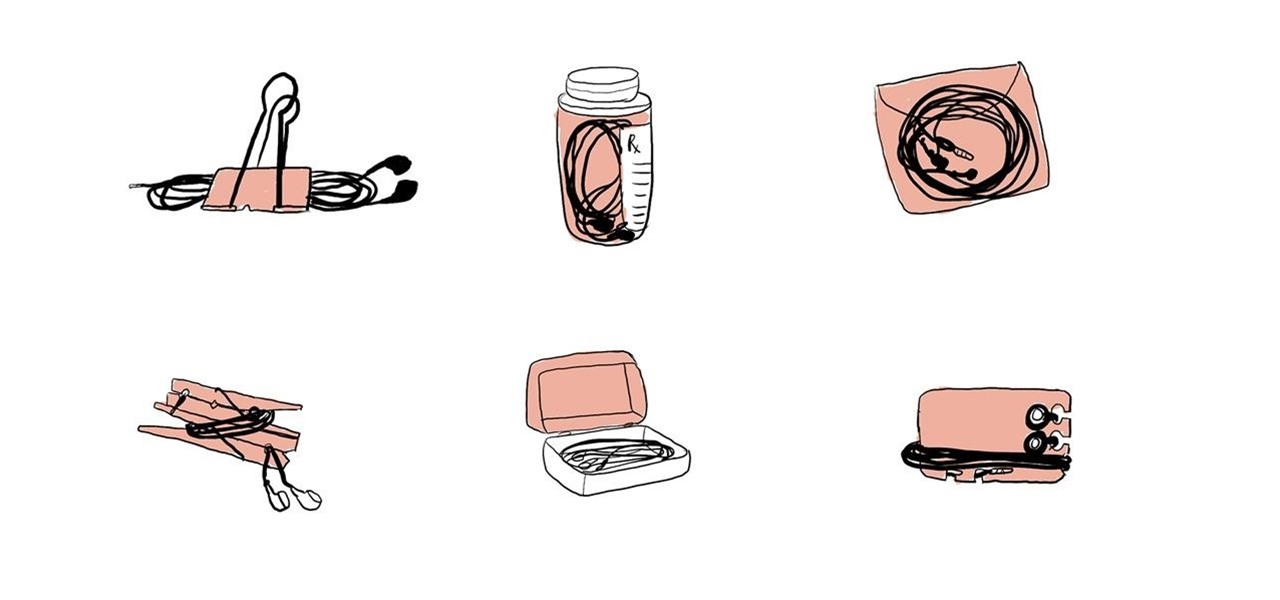
If you always carry earbuds with you in your purse or backpack, you can use simple household objects to prevent the cords from tangling up into knots.

Lorrie Faith Cranor: What’s wrong with your pa$$w0rd? | Talk Video | TED.com.

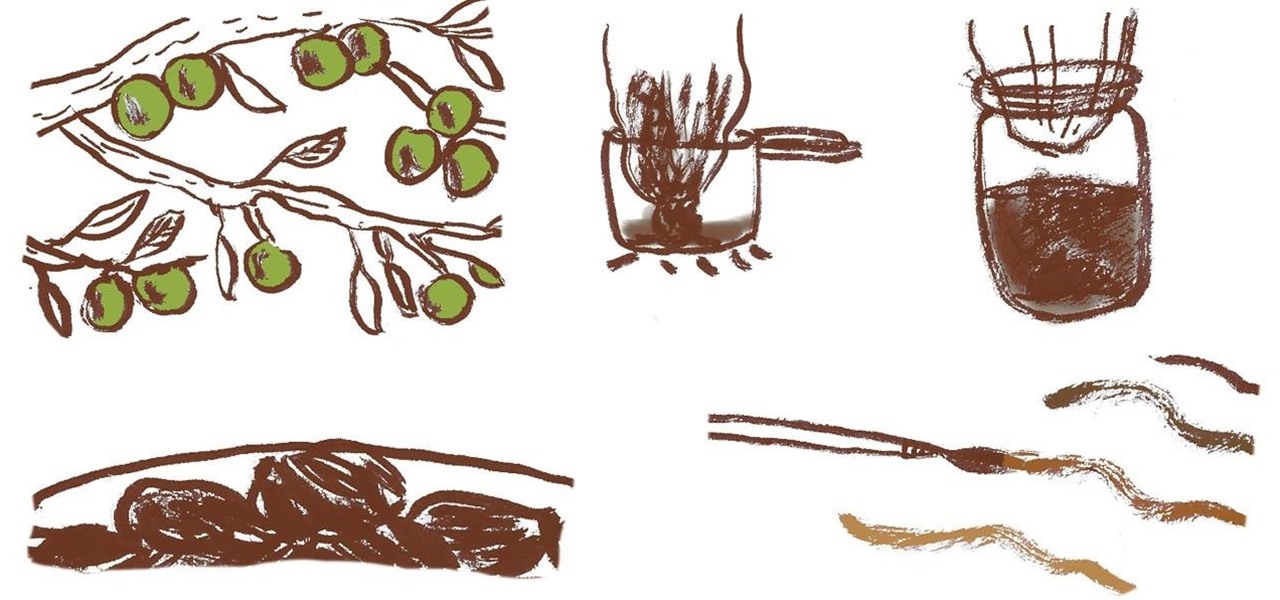
Using black walnuts, boiling water and a lot of time, you can make your own beautiful shades of deep dark brown to black ink for your next drawing, calligraphy, or wood craft project.

Bobby pins are great for pinning down flyaway bangs, but they're also great for pushing up the unused gel in a tube of toothpaste, marking the end of a transparent tape roll, opening the plastic seal in food jars, and even removing the pits from ripe cherries or olives.

When you really think about it, registering for any website is a little scary. Not only do they now have your name, email address, and a username/password combination you might've used elsewhere, but certain sites and services ask for quite a bit more private information. From phone numbers to addresses to birth dates and more, that company now has all of your information stored.

Now that you have learned how to knit ribbing, you will have to know how to bind off ribbing. If you have knitted something that needs to have a stretch to it, such as socks or a neck, this is a very important technique to know.

Tom Green shows how to make your life easier using these Fireworks productivity tips. This tutorial includes things like sharing layers between pages and creating dummy text.

Rosemarie Fiore is badass. She makes art with pyrotechnics, amusement park rides, Atari, guns, and pinball machines. Though all of her work is cool, I have to say my favorite piece is Fiore's larger than life spirograph, made from an amusement park ride, entitled "Good Time Mix Machine".

Got a screw loose? Don't worry. We all do. This handy tutorial will keep any screw secured to any screwdriver.

In this Rhino / Grasshopper 3D software tutorial we rebuild the shift tutorial provided by David Rutten.

Want to learn how to make a grape magically disappear? Let Ryan Oakes show you how in this mystical Mouth Magic trick! You will need two grapes. Sometimes we use materials that require adult supervision... like scissors so make sure you have friends and family around whenever you do magic tricks.

This week, California, like a growing portion of America is now 'handsfree'. As of July 1st, mobile phone use in cars became prohibited without the use of a headset.

Watch this video from This Old House to learn how to replace your exterior columns. Steps:

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

General Tips for Exercising in the Heat -Schedule workouts for the cooler times of the day.

Today, we are going to combine what we learned from the Introduction to Cryptography article with our Java programming skills. If you are new to Java, check out Matthew's Learn Java: Part One for a quick beginner's lesson, or check out some of the Java tutorials directly on Oracle.

There are many places where you can get help. If you are under 18 you will need your parents to take you, if anything the counselor will need to talk to your parents to see what is your home situation. Remember the counselor will not say anything to your parents or anyone else unless you want to harm yourself or anyone else. If you are 18 and older you could sing up for yourself to receive help. You could get help from places like HOPICS, (For Teens) and People Who are.

It is not that they do crazy things they do not know how to deal with stress. It is more likely for a teen to make a “bad” decision when they are under stress. Teens' brains are not yet developed; your brain is fully develop around the age of 25. That is why an adult will response better under stress than a teen.

Last Friday's mission was to accomplish solving HackThisSite, realistic 3. The third mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend restore a defaced website about posting peaceful poetry.

Originally made as portable convenience locks, padlocks are known for their cheap, simplistic and relatively secure design. Their construction is made up of a body, shackle and locking mechanism, with the shackle typically assuming a "U" shape to be easily linked to things like fences and chains.

Scrabble Bingo of the Day: CABRESTA [n/pl.] A cabresta (also cabestro or cabresto) is simply a lasso, a rope formed with a running noose that's used on ranches and Western plains for catching horse and cattle. Cabresta comes from the Spanish word halter, which refers to the headgear used for leading or tying up livestock and other animals. But halter also used to mean to hang someone by roped noose, which could be how it became popular as a term for a noosed lasso.

Cheers to another completed Community Byte project! Things went well regarding timeliness and being friendly to the other coders and students. If you've got ideas for our next mission, or an idea for a tutorial, submit them to me. Friday, our mission was to take out HackThisSite, basic mission 5. This mission focused on JavaScript, again. This time there is a little bit more security in place.

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

Welcome to Pizza Perfect. I'm a novice pizza maker with one goal: to master the art of the homemade crust. The cheese (fresh mozzarella), the sauce (endless options or super basic), and the toppings (the sky is the limit) are all easy. But the crust I've found to be somewhat elusive.
EL Wire is a bit tricky if all you want to do is glow. But there's a lot to know about the technology, as well as helpful information to get you addicted to it. EL Wire is a thin copper wire that gives off a beautiful glow when an electric charge is applied. There are 10 colors of EL Wire, and each wire has it's own unique characteristics. Typically EL Wire is used for safety as well as costuming. It has such a low power point that it can run off as little as watch batteries to make it glow!

Well, maybe not a real invisibility cloak—sorry Harry Potter fans—but a team of scientists at MIT's SMART Centre are on their way to producing materials that mimic actual invisibility.

Hello readers again! Sorry about the long wait (scary computer problems). Today I am going to talk to you about security problems on Wizard101. I have recently encountered many security flaws on Wizard101, including hacking, frauding and other crazy things. Wizard101 is the target for many online predators, many of who are fully-grown adults aged 60 or 70. Here is the link to an article I found about it: Wizard101 Internet Predators

"ASTON-2"-WINDOWS SHELL REPLACEMENT USER INTERFACE, I HAVE BEEN USING IT NOW FOR A WEEK OR SO AND I FIND IT NOT ONLY FASTER, YET MORE INTUITIVE, AND MORE FEATURE RICH THAN WINDOWS EXPLORER.EXE EVER THOUGHT OF BEING...! IT DOES HAVE IT'S LITTLE QUIRKS OR EVEN BUGS HOWEVER...LIKE EARLIER TODAY THE TASK-BAR FOR ASTON-2 WOULD NOT RAISE UP OUT OF AUTOHIDE FOR ANYTHING, I REBOOTED THEN IT WAS FINE AGAIN, THIS COULD BE A WEB BASED BUG THAT INTERFERED, OR LOCAL BAD CODE WITHIN ASTON-2 BUT I DOUBT IT,...

Here at WonderHowTo, we are often presented with morally questionable HowTo's. When it comes to stocking our library, we have to weigh in the community value of indexing tutorials with potentially negative repercussions. Where is the line when it comes to areas like weapons, sex, and drugs?